🚀 CloudSEK becomes first Indian origin cybersecurity company to receive investment from US state fund
Read more
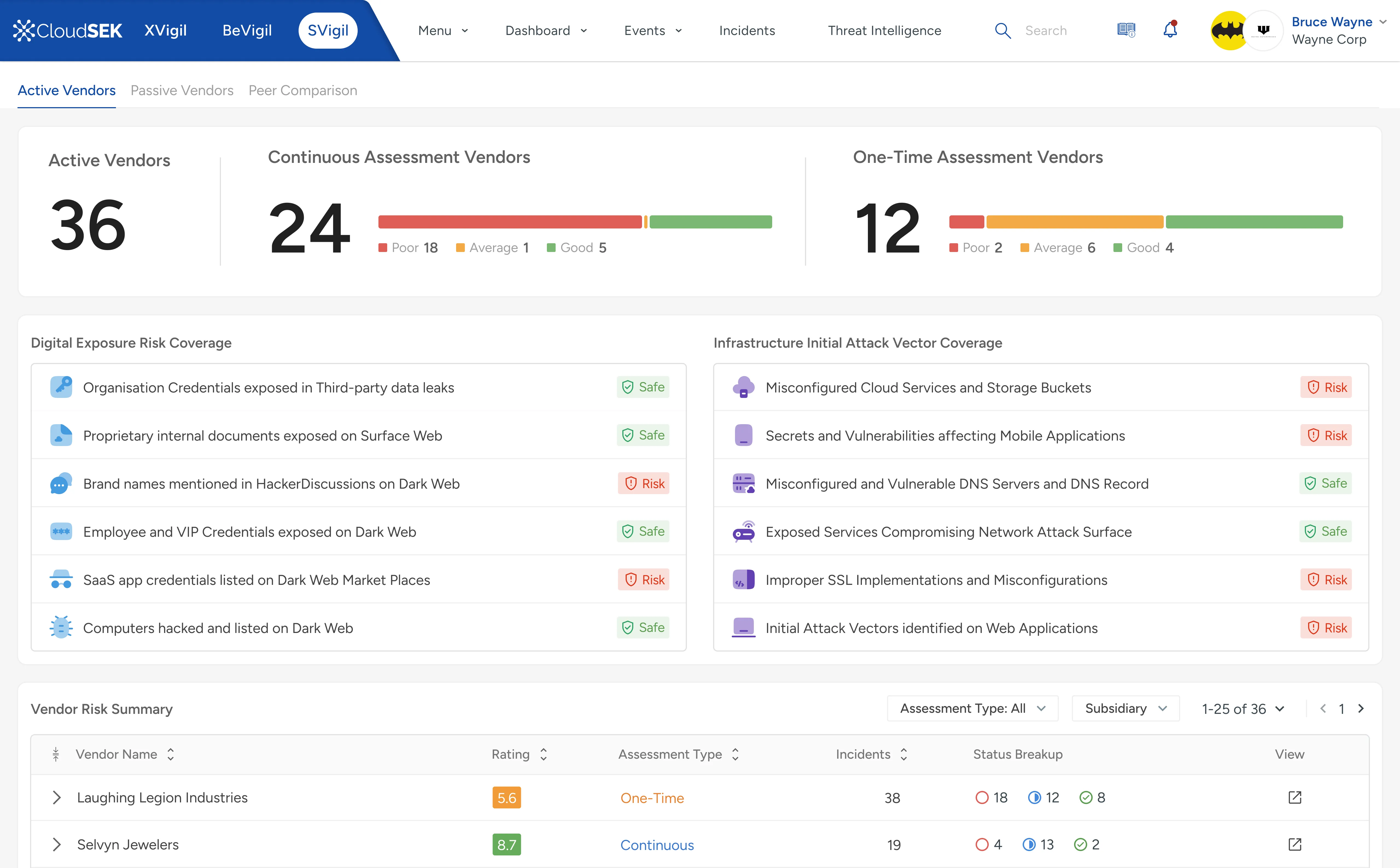
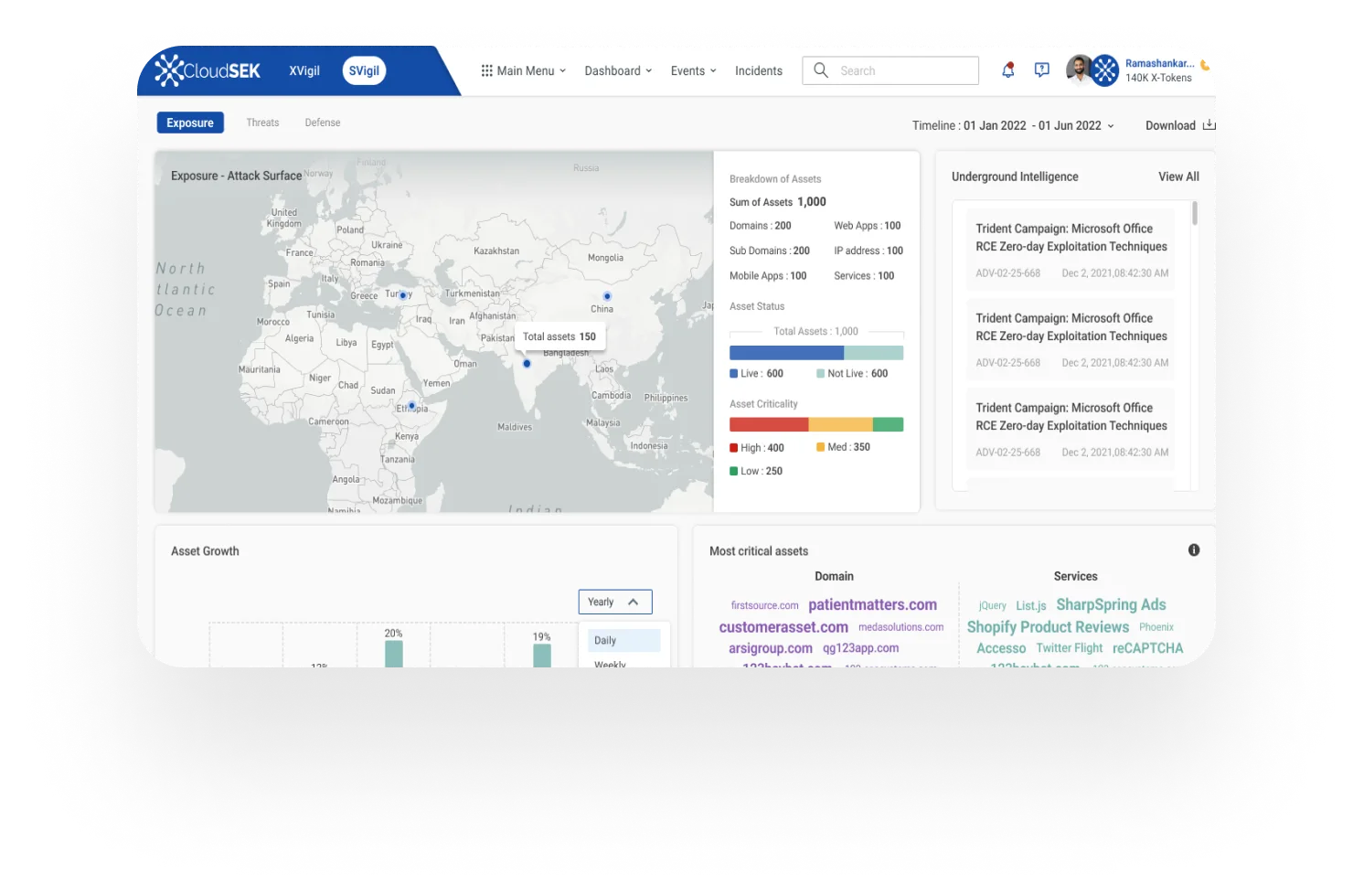
CloudSEK SVigil assesses the risks and vulnerabilities introduced by third-party suppliers and vendors that may impact the security of an organization's products or services.
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)

.png)
.png)
.png)
.png)
.png)

Global Enterprises and Fortune 500 companies trust CloudSEK to fortify their cybersecurity posture.





Stay updated with the Latest resources.
The latest helpful guides from CloudSEK.
Integrations
Integrate CloudSEK’s IAV intelligence via APIs and automate threat resolution across 50+ applications in your security ecosystem.
Integrations
Integrate CloudSEK’s IAV intelligence via APIs and automate threat resolution across 50+ applications in your security ecosystem.
Unlock the power of data-driven insights with our team of research experts who will delve in to the On-Demand Research service
Gain insight into potential risks to your digital infrastructure and take proactive measures to strengthen your security posture.
CloudSEK IOA (IAV) Platform Assists Customers in their Prevention Strategies
Traditional Cyber Intelligence Companies
CloudSEK IOA (IAV) Platform
Integrations