🚀 CloudSEK becomes first Indian origin cybersecurity company to receive investment from US state fund
Read more




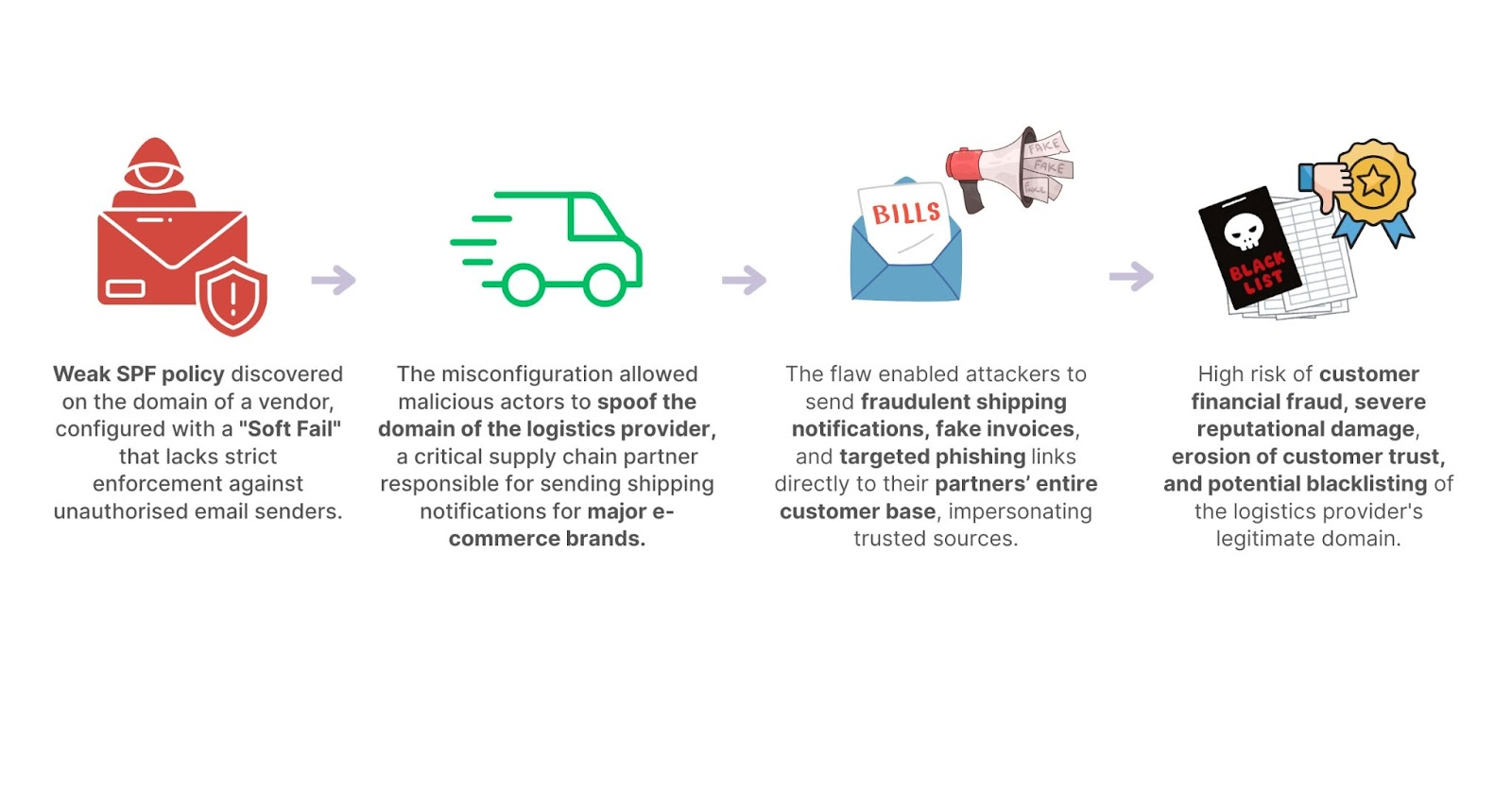
During a routine supply chain security assessment, CloudSEK’s Digital Supply Chain Security platform SVigil uncovered a misconfigured SPF (Sender Policy Framework) record on a vendor’s primary domain. The vendor, a logistics SaaS provider, powers global supply chain operations—serving e-commerce platforms, manufacturers, and enterprises by acting as the digital bridge between suppliers, transporters, and end clients.
For a provider at the heart of so many supply chains, trusted communication is non-negotiable. Each day, their domain delivers thousands of mission-critical emails—covering shipment updates, invoices, delivery schedules, and client communications. Yet, a seemingly minor misconfiguration in their email security posture quietly undermined this trust, leaving their brand exposed to exploitation.
That single oversight transformed a legitimate business domain into a potential launchpad for phishing attacks, business email compromise, and large-scale fraud.
CloudSEK's SVigil platform, while monitoring a customer’s supply chain infrastructure, flagged a seemingly minor issue where the Sender Policy Framework (SPF) record was set to ~all (a "Soft Fail") on a vendor’s primary domain.
SPF is an email authentication mechanism designed to prevent spoofing by listing the servers authorised to send emails on behalf of a domain. An SPF record typically ends with either:
This "soft fail" policy was an open invitation for attackers. It allowed any malicious actor on the internet to send emails that looked exactly like they came from the logistics company, and most receiving mail servers would still deliver them to the recipient's inbox.
The ability for an attacker to perfectly spoof an email from a trusted logistics provider is a critical threat. It would enable a wide range of devastating attacks:
This incident underscores the value of continuous vendor and third-party risk monitoring. SVigil flagged and contained a high-impact vulnerability that could have affected thousands of transactions across multiple brands and industries.
By discovering the vulnerability before malicious actors did, SVigil prevented real-time data manipulation, financial fraud, and broader system abuse.
In the world of digital trust, prevention isn’t just better — it’s priceless.
About CloudSEK
CloudSEK is a unified digital risk management platform that leverages AI and machine learning to deliver real-time threat intelligence, attack surface monitoring, and supply chain security across enterprises globally.