.webp)
Threat Actor Directory
Know Your Adversaries
Access comprehensive profiles of known threat actors, including APT groups and cybercriminal collectives. Gain a strategic advantage by understanding threat actors, their tactics, past activities, and potential nation-state affiliations.

Adversary Intelligence
Know Your Enemy Before They Strike
Gain deep insights into attack methodologies, and malicious infrastructures. Our system blends exclusive intelligence from HUMINT, OSINT, and incident RFIs to help you anticipate and neutralise adversaries.

Vulnerability Intelligence
Prioritise Threats, Patch Smarter
Track and prioritise vulnerabilities that are actively exploited in the wild. CloudSEK identifies and alerts you to the most pressing CVEs, helping you patch smarter and reduce exposure to costly breaches.

Malware Intelligence
Detect Malware Threats Faster
Stay ahead of malware campaigns with intelligence from malware logs and deep/dark web investigations. Get critical incident reports and actionable insights on malware threats that may impact your business.

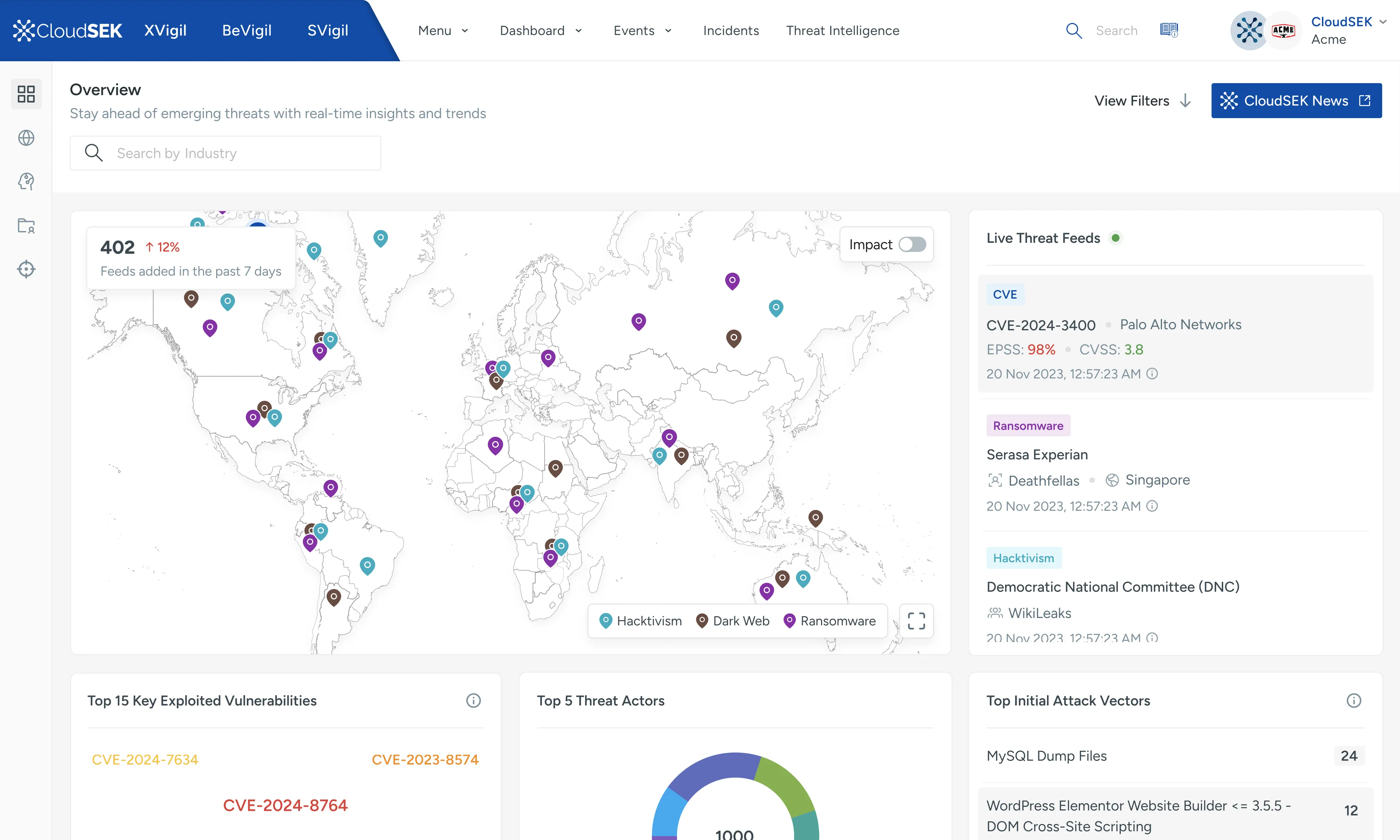
Cyber News Feeds
Stay Updated with AI-Driven Insights
Quickly digest the critical information by filtering through the noise with AI-curated summaries from credible sources, highlighting key threats and trends relevant to your industry, region or any other area of interest.

Dark Web Feeds
See Threats Others Miss
Gain visibility into hidden cybercriminal activity on the dark web. Identify stolen credentials, illegal marketplaces, hacking tool sales and other criminal operations before they surface on mainstream platforms.

CVE Feeds
Monitor Emerging Vulnerabilities
Be the first one to know of emerging and actively exploited vulnerabilities. CloudSEK provides timelines, exploitation trends, and dark web insights, ensuring ready to act before threat actors exploit them.

Ransomware Feeds
Proactive Defence Against Ransomware
Monitor global ransomware activity with live alerts and impact assessments. Identify targeted sectors and vulnerabilities to strengthen your defenses against one of the most disruptive cyber threats.

Hacktivism Feeds
Monitor Ideologically Driven Threats
Track hacktivist campaigns, their targets, and their methods. Real-time activity alerts and in-depth analysis of tactics (TTPs) and motivations help you prepare for ideologically motivated cyber attacks.
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)

.png)
.png)
.png)
.png)
.png)

.webp)
.webp)







