🚀 A CloudSEK se torna a primeira empresa de segurança cibernética de origem indiana a receber investimentos da Estado dos EUA fundo
Leia mais
Key Takeaways:
The MITRE ATT&CK Framework applies across a wide range of computing environments, including enterprise IT systems, cloud platforms, mobile devices, and industrial control systems. This cross-environment coverage allows a single reference structure to be used regardless of where attacker activity occurs.
By using one unified framework, organizations can analyze threats that move between technologies without switching models or terminology. This consistency is especially important in modern attacks that cross on-premises, cloud, and operational environments.
Ongoing research by MITRE Corporation ensures the framework continues to reflect emerging attacker activity across different industries and platforms. As coverage expands, the framework remains applicable to both traditional and modern infrastructure.
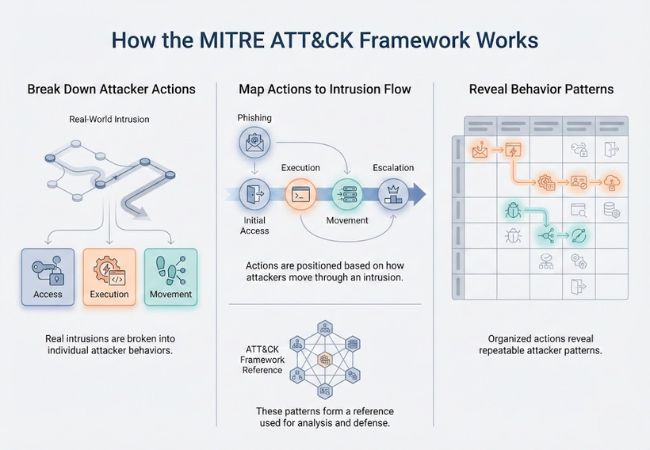
MITRE ATT&CK works by breaking real intrusion incidents into discrete attacker actions that can be studied independently. Each action is documented using a consistent structure so similar behavior can be recognized across unrelated attacks.
Those actions are then positioned relative to one another based on how attackers progress during an intrusion. This ordering reveals patterns in attacker movement, decision-making, and escalation over time.
Once organized, these behavior patterns form a reference system that supports deeper analysis in later stages of security operations. Subsequent sections build on this structure to explain classification, visualization, and practical use.
The MITRE ATT&CK Framework uses multiple matrices to organize attacker behavior by environment, allowing techniques to be analyzed in the context where they are actually used.
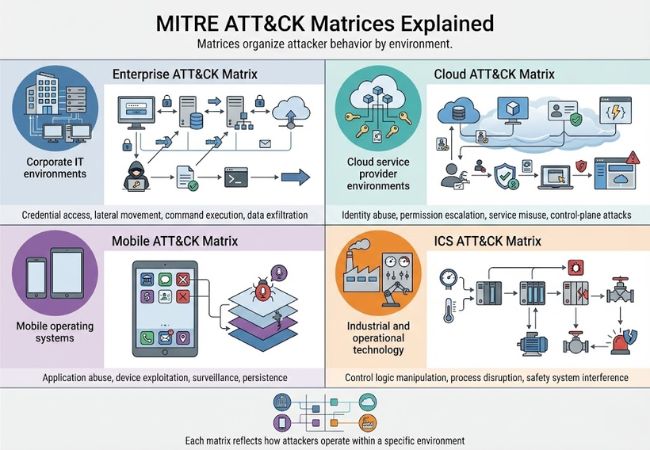
Enterprise ATT&CK Matrix includes techniques attackers use against corporate IT environments, such as credential access, lateral movement, command execution, and data exfiltration. These behaviors commonly target operating systems, identity services, email systems, and enterprise applications.
Cloud ATT&CK Matrix documents techniques that exploit cloud-specific architectures, including abuse of cloud identities, permission escalation, service misuse, and control-plane manipulation. Activity here reflects how attackers operate within cloud service providers rather than traditional networks.
Mobile ATT&CK Matrix captures techniques used to compromise smartphones and tablets, including application-based attacks, device exploitation, surveillance activity, and persistence on mobile operating systems. These behaviors account for the security constraints and sandboxing models unique to mobile platforms.
ICS ATT&CK Matrix contains techniques associated with industrial and operational technology environments, such as manipulation of control logic, disruption of physical processes, and interference with safety systems. Behaviors in this matrix focus on reliability, availability, and physical impact rather than data theft.
Within the MITRE ATT&CK Framework, tactics define the technical objectives adversaries pursue as an intrusion progresses, explaining why specific attacker behavior appears at each stage.
ATT&CK techniques show how attackers carry out actions inside an environment after deciding what they want to achieve.
ATT&CK sub-techniques exist to show how the same attacker behavior changes in execution depending on access, environment, and technical constraints.
MITRE ATT&CK Technique T1595 refers to attackers actively sending network traffic to target systems to identify exposed hosts, services, and applications before attempting access. This activity falls under the Reconnaissance phase, where adversaries reduce uncertainty and identify viable entry points.
T1595 includes Scanning IP Blocks (T1595.001), Vulnerability Scanning (T1595.002), and Wordlist Scanning (T1595.003), which collectively reveal live infrastructure, reachable services, and potential weaknesses. Responses from these probes often expose service banners, software versions, misconfigurations, or hidden paths that inform later exploitation decisions.
Active scanning generates direct interaction with target systems and frequently appears in firewall logs, IDS/IPS alerts, WAF telemetry, and cloud flow logs. In a large-scale cloud traffic study, 64% of scanning IP addresses were observed only once over a four-month period, highlighting how quickly scanning infrastructure rotates and why detection must rely on behavioral patterns rather than static IP reputation.
The MITRE ATT&CK Navigator is a visualization tool designed to work directly with the MITRE ATT&CK Framework and its matrices. It enables teams to represent attacker behavior, defensive coverage, and analysis results in the same structure used by ATT&CK.
Security data such as detections, adversary activity, or simulated attacks can be overlaid onto ATT&CK tactics, techniques, and sub-techniques. Visual representation helps teams identify coverage gaps, overlaps, and priorities more effectively than reviewing raw logs or tables.
Navigator is widely used during threat modeling, purple team exercises, and security reviews. Layered views support clear communication of security posture to both technical teams and leadership using attacker behavior as the reference point.
The MITRE ATT&CK Framework is important because it helps organizations understand attacks through attacker behavior rather than isolated tools or alerts.
Attack tools and infrastructure change frequently, but attacker actions remain consistent across campaigns. Focusing on behavior allows threats to be identified even when malware or indicators rotate.
Many attacks succeed after initial access without being immediately detected. ATT&CK improves visibility into what happens inside an environment once an attacker is already present.
Security controls often exist without clarity on what they actually protect against. Mapping defenses to ATT&CK highlights which attacker behaviors are monitored and which remain exposed.
Security maturity is difficult to assess without a shared reference. ATT&CK provides a structured way to measure detection depth and response capability over time.
Different teams often describe the same threat activity in different ways. ATT&CK creates a common vocabulary that aligns analysts, engineers, and leadership around the same behaviors.
Security teams use the MITRE ATT&CK Framework to apply attacker behavior knowledge across detection, response, testing, and strategic security planning.
Logs and alerts are aligned to ATT&CK techniques to show which attacker actions are visible in the environment. Coverage becomes measurable when detections are tied to behaviors instead of individual tools.
ATT&CK guides the creation of new detection logic by highlighting common attacker behaviors that should be observable. Engineers use it to prioritize detections that cover multiple threats with minimal overlap.
Hunters use ATT&CK to search for attacker behavior that may exist without triggering alerts. This approach focuses investigations on behavior patterns rather than known indicators.
ATT&CK provides structure for tracking attacker progress during an investigation. Responders use tactics and techniques to understand where an attacker has been and what may come next.
Security controls are compared against ATT&CK to identify behavioral blind spots. Gaps become clear when common attacker actions lack monitoring or response capability.
Offensive and defensive teams use ATT&CK as a shared reference during simulated attacks. Exercises focus on validating detection and response against realistic attacker behavior.
Red teams model real-world threats by replaying ATT&CK techniques associated with known adversaries. Defensive readiness improves when testing mirrors actual attack behavior.
ATT&CK helps verify whether security tools detect the behaviors they claim to cover. Validation focuses on outcomes rather than vendor feature lists.
ATT&CK translates technical findings into attacker-centric language that leadership can understand. Security posture discussions shift from tool metrics to behavioral risk.
The MITRE ATT&CK Framework is used by a wide range of roles that need to understand, detect, or communicate attacker behavior.
Security operations analysts use ATT&CK to interpret alerts and investigations through attacker behavior. Tactics and techniques provide context that helps prioritize response actions.
Hunters rely on ATT&CK to guide proactive searches for malicious behavior that may not trigger alerts. Behavior-focused hunting reduces dependence on indicators and signatures.
Detection engineers use ATT&CK to design and validate detection logic tied to real attacker actions. Coverage can be expanded systematically instead of adding isolated alerts.
Responders use ATT&CK to track attacker progression during an active incident. Understanding likely next steps helps contain threats faster.
Offensive teams reference ATT&CK to simulate realistic attacker behavior during testing. Exercises become more valuable when aligned with real-world techniques.
Managers and executives use ATT&CK to understand risk in behavioral terms. Security posture becomes easier to communicate without relying on tool-specific metrics.
Both the Cyber Kill Chain and the MITRE ATT&CK Framework are used to understand how cyberattacks unfold, but they differ fundamentally in structure, depth, and defensive purpose.
The MITRE ATT&CK Framework matters because it explains cyber threats through attacker behavior rather than tools, malware, or alerts. This perspective helps organizations understand how attacks actually unfold in real environments.
Using ATT&CK allows security teams to improve detection, response, testing, and communication using a shared behavioral reference. As threats continue to evolve, behavior-based understanding remains one of the most reliable ways to assess and strengthen cybersecurity defenses.
