🚀 A CloudSEK se torna a primeira empresa de segurança cibernética de origem indiana a receber investimentos da Estado dos EUA fundo
Leia mais
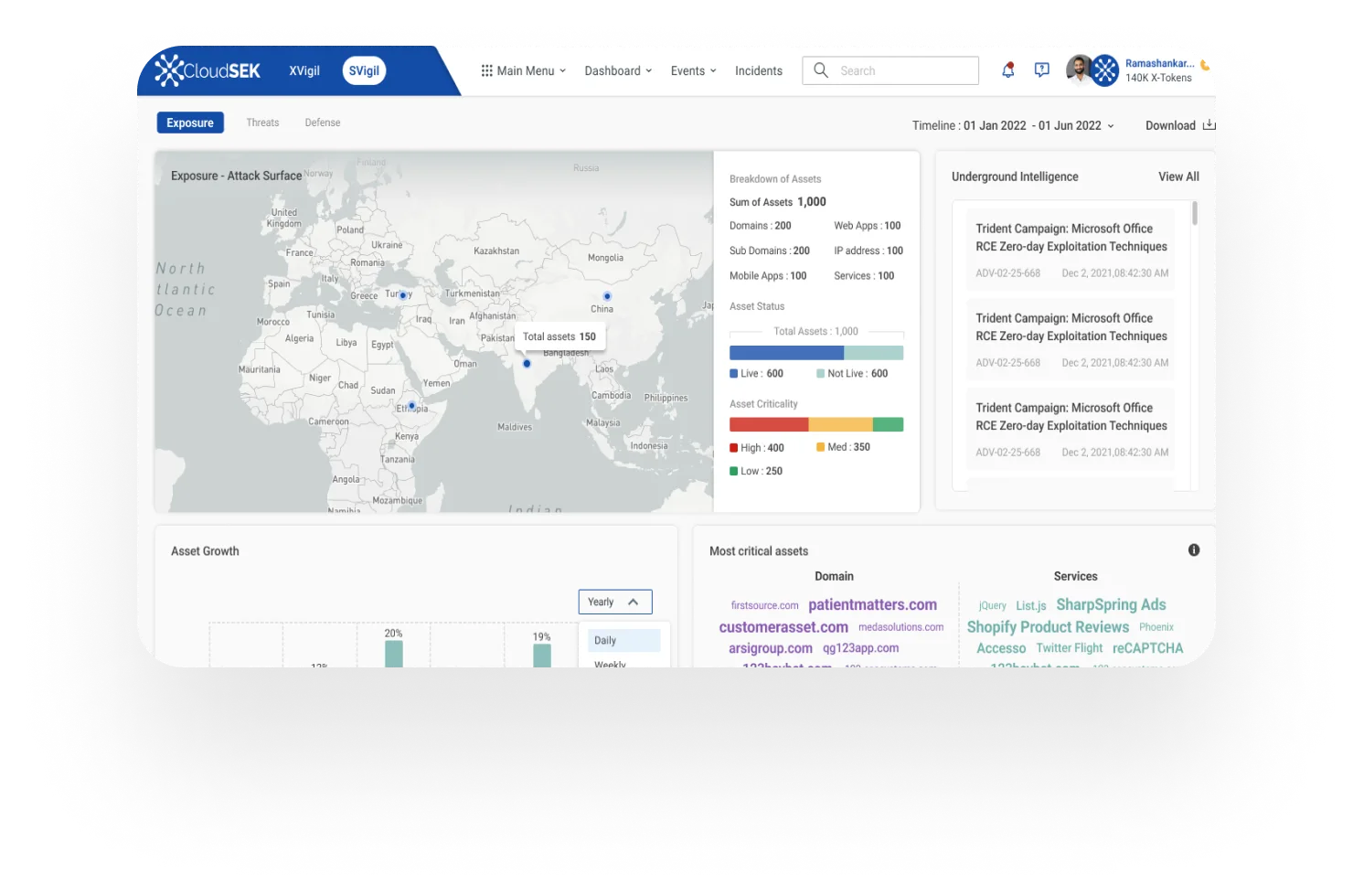
CloudSEK BeVigil creates a blueprint of an organization's external attack surface including the core infrastructure and the software components. This is then scanned for any misconfigurations, vulnerabilities etc thereby preventing potential exploits or cyber attacks targeted at the organization.

.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)

.png)
.png)
.png)
.png)
.png)

Empresas globais e empresas da Fortune 500 confiam no CloudSEK para fortalecer sua postura de segurança cibernética.

Identify security vulnerabilities in web applications with ease. BeVigil Enterprise Web App Scanner conducts thorough scans to detect issues such as SQL injection, cross-site scripting (XSS), and other common web app vulnerabilities, ensuring robust security for web applications.
Ensure the security of a website and its associated systems with BeVigil Enterprise SSL Scanner. It scans SSL configurations to detect potential risks such as weak encryption, expired certificates, and improper implementations, helping maintain secure communication channels.
Strengthen your network security with BeVigil Enterprise DNS Scanner. It detects misconfigurations in DNS settings, including SPF and DMARC records, subdomain takeovers, and private IP disclosures, safeguarding against various web security threats.
Identify potential security risks in mobile applications effortlessly. BeVigil Enterprise Mobile App Scanner detects OWASP Mobile Top 10 vulnerabilities, misconfigurations, malware, and hard-coded secrets, ensuring comprehensive security for mobile apps.
Detect security flaws in API endpoints effectively with BeVigil Enterprise API Scanner. It maintains an inventory of all API services and identifies issues such as improper authentication, data exposure, and potential entry points for cyber-attacks.
Gain a comprehensive view of your network topology with BeVigil Enterprise Network Scanner. It automatically scans and identifies active hosts, open ports, and available services in the network, assessing potential security risks.
Evaluate the security of cloud-based assets seamlessly with BeVigil Enterprise Cloud Scanner. It scans cloud infrastructure for vulnerabilities, misconfigurations, and security risks, ensuring the safety of cloud environments.
Identify and track known vulnerabilities in software systems swiftly with BeVigil Enterprise CVE Scanner. It scans devices, applications, and systems against the CVE database to detect publicly disclosed vulnerabilities, ensuring timely remediation.


Stay updated with the Latest resources.
The latest helpful guides from CloudSEK.
CloudSEK IOA (IAV) Platform Assists Customers in their Prevention Strategies
Traditional Cyber Intelligence Companies
CloudSEK IOA (IAV) Platform
Integrações
Integre a inteligência de IAV do CloudSEK por meio de APIs e automatize a resolução de ameaças em mais de 50 aplicativos em seu ecossistema de segurança.
Integrações
Integre a inteligência de IAV do CloudSEK por meio de APIs e automatize a resolução de ameaças em mais de 50 aplicativos em seu ecossistema de segurança.
Unlock the power of data-driven insights with our team of research experts who will delve in to the On-Demand Research service
Gain insight into potential risks to your digital infrastructure and take proactive measures to strengthen your security posture.
Integrations