🚀 A CloudSEK se torna a primeira empresa de segurança cibernética de origem indiana a receber investimentos da Estado dos EUA fundo
Leia mais
Key Takeaways:
Advanced Persistent Threat (APT) groups represent highly strategic cyber actors focused on long-term infiltration rather than quick attacks. Such groups slip into networks quietly and remain active for extended periods to gather intelligence or prepare disruption.
Nation-state backing gives APT operators deep resources and specialized tools that support targeted missions. Careful planning and tailored techniques allow sustained access without triggering alerts.
Once access is established, activity expands into reconnaissance, data collection, or controlled movement within the environment. Prolonged presence is what makes APT operations so difficult to detect and eliminate.
The review is based on publicly released government advisories, national CERT reports, and law-enforcement disclosures published during 2024–2025. Only incidents with confirmed attribution or high-confidence intelligence assessment were included.
Each attack was assessed using consistent criteria covering operational scope, target-sector relevance, and persistence observed during 2025. Focus was placed on repeat activity, infrastructure access, and campaigns demonstrating sustained intelligence value rather than isolated events.
Findings were cross-checked across multiple state sources to avoid single-source bias and exclude speculative reporting. Priority metrics included affected organizations, geographic reach, and officially reported impact to maintain accuracy and comparability.
Salt Typhoon has been tracked since at least 2019 as a PRC-aligned espionage actor focused on telecommunications infrastructure. Intelligence reporting associates the group with prolonged access inside carrier environments rather than short-duration intrusions.
Activity observed across 2025 concentrated on edge routing devices, configuration extraction, and covert traffic collection within telecom networks. Control of provider infrastructure enabled indirect visibility into government, political, and enterprise communications dependent on those carriers.
In February 2025, Canada’s Cyber Centre confirmed the compromise of three network devices at a Canadian telecommunications provider, including configuration exfiltration and tunnel creation for traffic monitoring. The incident was publicly attributed to PRC-linked activity targeting carrier infrastructure.
Active since at least 2021, Flax Typhoon is associated with PRC intelligence services conducting infrastructure-scale access operations. The group is distinguished by its use of large botnets as persistent espionage infrastructure.
Across the reporting period, operations leveraged compromised routers, IoT devices, and small office equipment to obscure command-and-control activity. This infrastructure allowed follow-on intrusions while blending traffic into routine consumer and enterprise network flows.
A joint U.S. government advisory reported Flax Typhoon control over more than 260,000 compromised devices worldwide, including over 385,000 unique U.S. devices identified during remediation efforts. Authorities stated the botnet was actively used to support cyber-espionage operations.
Mustang Panda has been active since at least 2012 and is widely tracked for targeted espionage against government and diplomatic institutions. Target selection consistently reflects PRC foreign policy and regional intelligence priorities.
Initial access commonly relied on spearphishing, followed by staged payload delivery and credential reuse to maintain persistence. Victim environments included public administration bodies, foreign ministries, and transport-adjacent organizations.
In its November 2025 public administration report, ENISA documented 586 publicly reported incidents, with state-linked intrusion sets confirmed in about 1.2% of cases. The agency highlighted credential-focused espionage as a persistent threat, noting increased use of phishing and session hijacking to bypass security controls.
Operating since at least 2007, APT17 is linked to PRC intelligence collection against government-adjacent targets. Historical reporting associates the group with credential theft and sustained email access rather than disruptive activity.
Mailbox compromise and identity harvesting defined observed activity during 2025, with continued access to systems supporting public-sector workflows. These techniques enabled long-term intelligence collection with limited operational visibility.
ENISA’s public-sector threat analysis again identified 77 state-linked incidents affecting public administration entities across EU member states. Credential-focused espionage activity was highlighted as a persistent risk pattern.
APT28 is attributed to Russia’s GRU Unit 26165 and has operated since at least 2004. The group is closely associated with military and strategic intelligence collection.
Targeting observed during 2025 centered on logistics providers, IT services, and organizations supporting aid flows into Ukraine. Intrusions relied on spearphishing, credential access, and lateral movement through trusted partner environments.
A U.S.-led joint advisory stated that APT28 targeted dozens of entities across transportation, logistics, and technology sectors. Authorities linked the campaign to intelligence collection supporting Russian military objectives.
APT29 has been linked to Russia’s Foreign Intelligence Service (SVR) since at least 2008. The group is known for long-dwell espionage operations targeting diplomatic and government institutions.
Identity-based access dominated observed campaigns, including credential theft and cloud account compromise. Persistence was maintained primarily within email and collaboration platforms rather than through endpoint-focused intrusion.
The UK National Cyber Security Centre reported handling 429 cyber incidents in its latest annual review, including 204 nationally significant cases. Russia-linked espionage against public institutions remained a recurring component.
Sandworm, also tracked as APT44, has been active since at least 2009 and is aligned with Russian military objectives. The group is distinguished by its integration of espionage and destructive cyber operations.
Operations continued to blend intelligence collection with disruption, particularly in energy and infrastructure environments. Targeted systems were selected for their potential to generate operational impact beyond individual victims.
In 2025, DPRK-linked Kimsuky used QR-code phishing to hijack cloud identities, and the FBI attributed a record $1.5 billion Bybit cryptocurrency theft to North Korea’s TraderTraitor cluster. Concurrently, Russia’s Sandworm (APT44) escalated cross-border attacks by deploying new wiper malware, including ZEROLOT, against energy and logistics infrastructure.
Lazarus Group has been active since at least 2009 and plays a central role in DPRK cyber operations for revenue generation. Financial theft remains a core mission under sustained sanctions pressure.
Cryptocurrency platforms formed the primary focus of operations, combining social engineering with transaction manipulation and rapid laundering workflows. Stolen assets were dispersed through complex blockchain networks.
The U.S. Federal Bureau of Investigation attributed the February 21, 2025 Bybit theft, valued at approximately $1.5 billion, to DPRK actors operating under the TraderTraitor activity cluster. Japanese authorities publicly corroborated the scale of the loss.
Kimsuky has been active since at least 2012 and is associated with DPRK intelligence collection targeting foreign policy and defense-related subjects. The group frequently targets researchers, analysts, and government-linked experts.
QR-code-based phishing became a defining technique, allowing operators to bypass email security controls and harvest credentials. Access to cloud identities and collaboration environments followed successful lure execution.
An FBI FLASH alert documented multiple Kimsuky QR-code phishing campaigns observed in May and June 2025, detailing four distinct lure scenarios. Authorities warned the technique was being actively reused.
APT42 has been active since at least 2015 and is linked to Iranian intelligence services. Operations are associated with surveillance-driven espionage targeting individuals rather than infrastructure.
Observed campaigns focused on phishing and account compromise aimed at diaspora members, journalists, academics, and policy professionals. Access to personal communications and research material remained the primary objective.
France’s national cybersecurity agency reported 162 incidents transmitted to state institutions in its latest annual assessment. Iranian-linked intrusion activity was cited among persistent threats affecting civil society and policy environments.
APT groups remain one of the most disruptive forces in modern cybersecurity due to their persistence, skill, and long-term objectives.
Intrusions unfold slowly, allowing attackers to blend into normal network activity without raising suspicion. Hidden movement creates long windows for intelligence gathering or infrastructure manipulation.
Nation-state support grants access to zero-days, specialized tools, and large operational teams. Such advantages overwhelm the defensive capabilities of most organizations.
Focus often falls on governments, telecom systems, critical infrastructure, and major enterprises. Compromise in any of these environments triggers widespread operational and geopolitical consequences.
APT attacks rely on layered techniques that enable silent entry, controlled expansion, and long-term persistence inside high-value environments.
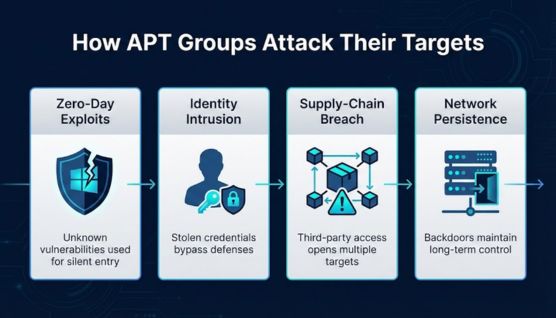
Unknown vulnerabilities offer direct access paths into systems before any patch or defense is available. Use of these flaws gives attackers immediate leverage over critical assets with minimal detection risk.
Compromised credentials allow adversaries to impersonate legitimate users and bypass perimeter controls. This approach becomes especially powerful when cloud platforms and authentication tokens are involved.
Vulnerabilities in third-party vendors or software updates provide indirect access to multiple organizations at once. This tactic expands the attack surface and magnifies system-wide impact.
Backdoors, hidden services, and scheduled tasks maintain control over compromised environments for extended periods. Such persistence supports ongoing espionage and sets the stage for future operations.
Strong detection and response strategies require visibility, context, and continuous analysis across every layer of the environment.
Unusual authentication patterns, process activity, or lateral movement often signal early stages of an intrusion. Continuous monitoring helps surface subtle deviations that traditional tools overlook.
Strict access policies limit exposure from stolen credentials and privilege escalation attempts. Cloud identity logs provide the context needed to trace unauthorized role changes or token misuse.
Proactive investigation uncovers hidden footholds that automated systems miss. Focused searches across endpoints, logs, and authentication events reveal long-term activity linked to APT operations.
Aligning observed behavior with MITRE ATT&CK techniques strengthens detection accuracy. Pattern recognition across tactics and procedures improves confidence in identifying persistent threats.
Clear playbooks ensure teams act quickly during confirmed intrusions. Containment, isolation, and forensic review reduce dwell time and limit operational impact.
Cyber operations in 2026 will evolve toward greater automation, deeper infrastructure targeting, and more complex identity exploitation.
Adversaries will use automated reconnaissance and decision-making to accelerate early intrusion stages. Faster adaptation inside networks will make manual detection increasingly difficult.
Cloud identity systems will face heightened pressure as attackers refine token theft and privilege abuse techniques. Expanded reliance on federated access models will widen the attack surface.
Energy grids, transportation systems, and water networks will remain high-priority targets. Increased digitization across these sectors creates new entry points for covert reconnaissance.
Manipulated audio and video content will make phishing attempts more convincing. Social engineering will become harder to verify as attackers mimic trusted voices and personas.
Vendors and managed service providers will continue to serve as indirect access points for high-value targets. Broader dependency on third-party integrations increases systemic exposure.
APT groups shaped 2025 through targeted espionage, infrastructure access, and identity-driven intrusions that left lasting operational impact. Their precision and persistence confirmed that nation-state cyber activity remains one of the most significant global security challenges.
Defenders now face a landscape where cloud compromise, supply-chain exposure, and AI-enhanced techniques demand faster detection and stronger identity controls. Entering 2026, organizations must refine visibility, response workflows, and intelligence alignment to stay ahead of evolving adversaries.
