🚀 A CloudSEK se torna a primeira empresa de segurança cibernética de origem indiana a receber investimentos da Estado dos EUA fundo
Leia mais
Malware campaigns now deploy polymorphic code, fileless execution, and encrypted command channels to evade conventional defenses. Ransomware, trojans, and rootkits increasingly operate in memory, reducing visibility for traditional signature-based systems.
Evasion tactics such as zero-day exploitation and payload obfuscation weaken static detection models that rely solely on known patterns. Behavioral baselining, anomaly recognition, and Indicators of Compromise (IoCs) have therefore become essential for identifying malicious activity that does not match existing databases.
Modern malware detection techniques integrate static inspection, runtime analysis, endpoint telemetry, and threat intelligence into a layered security architecture. Mastering these techniques enables organizations to detect, contain, and neutralize sophisticated threats before operational damage escalates.
Malware detection is the process of identifying malicious software within systems before harmful actions are executed. Security controls continuously inspect files, processes, memory, and network traffic to uncover signs of unauthorized or deceptive behavior.
Identification does not rely solely on spotting known malicious code. Detection engines analyze patterns, compare activity against established baselines, and correlate suspicious signals to determine whether behavior indicates compromise.
These analytical methods extend across endpoints, servers, and cloud environments to maintain consistent visibility throughout the infrastructure. Early recognition of abnormal activity allows security teams to isolate threats before damage spreads across interconnected systems.
Malware detection works by analyzing digital activity through layered inspection and behavioral evaluation mechanisms.
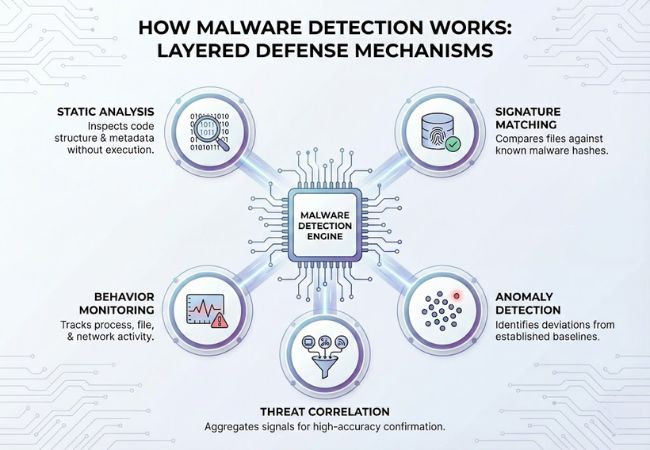
Malware detection relies on multiple analytical approaches that work together to identify known, unknown, and evasive threats.
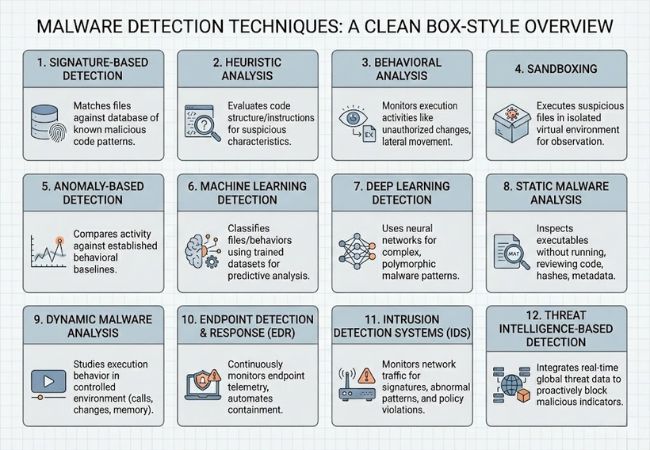
Signature-based detection identifies malware by matching files against a database of known malicious code patterns. Accuracy remains high for recognized threats, but new or modified malware can bypass this method until signatures are updated.
Heuristic analysis evaluates code structure and instruction sequences to detect suspicious characteristics. Variants of known malware can be flagged even when exact signatures are absent.
Behavioral analysis monitors how applications act during execution rather than how they are written. Activities such as unauthorized encryption, privilege escalation, or lateral movement trigger security alerts.
Sandboxing executes suspicious files inside an isolated virtual environment. Runtime behavior is observed safely without exposing the primary system to infection.
Anomaly-based detection compares current system activity against established behavioral baselines. Unusual deviations may indicate zero-day exploits or insider-driven compromise.
Machine learning models classify files and behaviors using trained datasets of malicious and benign samples. Predictive capabilities improve as models analyze larger volumes of threat data.
Deep learning systems use neural networks to detect complex and polymorphic malware patterns. Multi-layered models identify subtle correlations beyond rule-based logic.
Static malware analysis inspects executable files without running them. Code review, hash comparison, and metadata evaluation reveal embedded malicious intent.
Dynamic malware analysis studies malware behavior during execution in a controlled environment. Observed network calls, file changes, and memory usage expose hidden payloads.
Endpoint Detection and Response continuously monitors endpoint telemetry for suspicious activity. Automated containment actions such as device isolation reduce spread across networks.
Intrusion Detection Systems monitor network traffic for known attack signatures and abnormal patterns. Alerts are generated when policy violations or malicious activity is detected.
Threat intelligence-based detection integrates real-time global threat data into security platforms. Known malicious IP addresses, domains, and hashes can be blocked proactively.
Traditional and modern malware detection differ in methodology, analytical depth, and response capability.
Malware detection systems strengthen cybersecurity defenses, yet technical and operational constraints prevent absolute threat elimination.
Zero-day malware exploits vulnerabilities that have no existing signature or predefined behavioral profile. Detection engines may identify suspicious activity later, but initial compromise can occur before models adapt.
Legitimate applications or system processes may be incorrectly flagged as malicious. Excessive false alerts consume analyst time and reduce operational efficiency.
Advanced malware can disguise itself as normal system activity to evade detection logic. Encrypted payloads and memory-only execution techniques increase the likelihood of missed threats.
Continuous behavioral monitoring and AI-driven analysis require significant processing power and memory allocation. High resource consumption can impact endpoint performance in large-scale deployments.
Attackers use obfuscation, polymorphic code, and sandbox detection methods to bypass security analysis. Anti-debugging and delayed execution techniques further complicate runtime inspection.
Large volumes of security alerts can overwhelm analysts within Security Operations Centers (SOCs). Critical threats may be overlooked when high-priority signals blend with low-risk notifications.
No single malware detection technique provides complete protection, making layered implementation the most effective strategy.
Small businesses often rely on signature-based antivirus combined with basic behavioral monitoring due to budget and infrastructure constraints. Cloud-managed security platforms with automated updates reduce maintenance complexity and improve baseline protection.
Growing organizations benefit from integrating behavioral analysis with Endpoint Detection and Response (EDR) solutions. Centralized dashboards and automated alert prioritization improve visibility without overwhelming internal IT teams.
Large enterprises require multi-layered architectures that combine EDR, network-based intrusion detection, threat intelligence feeds, and anomaly detection systems. Security Operations Centers (SOCs) leverage telemetry correlation and automated response to reduce dwell time across complex infrastructures.
Financial institutions, healthcare providers, and critical infrastructure operators demand predictive detection models powered by machine learning and deep learning systems. Continuous monitoring, encryption inspection, and regulatory-aligned controls strengthen resilience against advanced persistent threats.
Selecting a malware detection solution requires evaluating technical capability, operational fit, and long-term scalability.
Choose solutions that combine signature-based scanning with behavioral and anomaly detection. Multi-layered analysis increases protection against both known and unknown threats.
Look for machine learning capabilities that continuously adapt to emerging attack patterns. Automated response features such as endpoint isolation reduce incident response time.
Ensure the solution supports endpoints, servers, cloud workloads, and hybrid environments. Seamless integration prevents visibility gaps across distributed systems.
Platforms that incorporate real-time threat intelligence feeds enhance proactive blocking. Correlated global data improves detection accuracy against emerging campaigns.
Evaluate CPU and memory consumption during deep scanning and real-time monitoring. Lightweight agents reduce operational disruption across business devices.
Organizations operating under regulatory frameworks should confirm alignment with standards such as ISO 27001 or NIST guidelines. Built-in reporting features simplify audit readiness and documentation.
Malware continues to evolve in complexity, stealth, and scale, demanding detection strategies that go beyond traditional signature scanning. Layered approaches that combine behavioral analysis, anomaly detection, machine learning, and threat intelligence provide stronger defense against modern attack techniques.
Organizations that invest in adaptive detection frameworks reduce breach impact, shorten response time, and strengthen overall cyber resilience. Clear understanding of malware detection techniques empowers security teams to build proactive, intelligence-driven protection in an increasingly hostile digital landscape.
