🚀 A CloudSEK se torna a primeira empresa de segurança cibernética de origem indiana a receber investimentos da Estado dos EUA fundo
Leia mais
Key Takeaways
IoT security is the protection of connected devices and the data they exchange from unauthorized access or disruption. It ensures that everything from small sensors to industrial IoT systems can function safely within a network.
Many IoT devices run simple software and use lightweight communication methods that make them easier targets for attackers. Security measures such as authentication, encryption, and device monitoring help reinforce these weaker points.
As IoT expands into homes, hospitals, factories, and supply chains, the impact of a single compromised device grows significantly. Effective IoT security keeps devices trustworthy, prevents data manipulation, and reduces the risk of network-wide disruption.
OT security protects the industrial systems that run physical processes such as manufacturing lines, power grids, and water treatment operations. It focuses on keeping these environments safe, reliable, and continuously available because any disruption can impact real-world operations.
Unlike IT environments that primarily protect data, OT systems rely on equipment like PLCs, SCADA platforms, and ICS controllers that must operate without interruption. Securing systems requires approaches tailored to legacy hardware, deterministic communication, and strict uptime requirements.
Modern OT security also addresses new risks created as OT networks connect with IT and cloud systems. This convergence exposes critical infrastructure to cyberattacks, making segmentation, strict access control, and continuous monitoring essential.
The difference between IoT and OT security comes from what each environment protects and how risks impact their operations. IoT deals with connected devices and data flows, while OT focuses on safeguarding physical processes that must run without interruption.
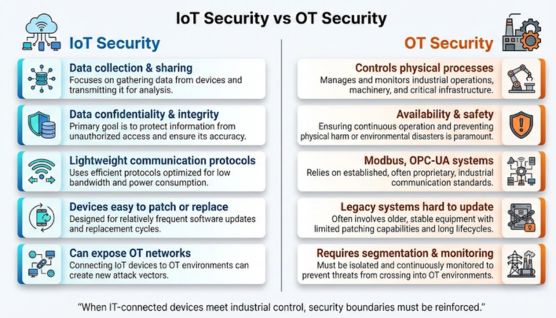
IoT is designed to collect, share, and process data across connected environments. OT is designed to control physical processes where uptime and precision are critical.
IoT security focuses on confidentiality and data integrity because breaches often expose or alter information. OT security prioritizes availability and safety since disruptions can stop production or damage equipment.
IoT uses lightweight protocols optimized for communication speed and device simplicity. OT relies on industrial protocols like Modbus and OPC-UA that were not originally built with cybersecurity in mind.
IoT devices can usually be patched or replaced without major impact. OT systems often run on legacy hardware that cannot be taken offline, making updates more difficult.
As IoT connects with OT networks, vulnerabilities in IoT can become entry points into critical infrastructure. This increases the need for strong segmentation and monitoring across both environments.
IoT plays a growing role in OT environments by adding real-time data, remote visibility, and smarter automation to industrial operations. Connected sensors and devices help OT systems make faster decisions and improve efficiency without interrupting physical processes.
IoT sensors capture continuous data on equipment performance, environmental conditions, and workflow activity. This visibility helps OT teams detect issues early and optimize operations.
Condition data from IoT devices supports models that forecast equipment failures before they occur. Early warnings reduce downtime and extend the life of industrial assets.
IoT connectivity allows operators to monitor and adjust OT systems from remote locations. This capability increases operational flexibility and reduces the need for on-site interventions.
Automation enabled by IoT streamlines processes such as energy management, material flow, and production timing. These improvements enhance throughput and lower operational costs.
IoT acts as a bridge between IT and OT by connecting digital platforms with physical equipment. This integration supports analytics, optimization tools, and centralized management.
IoT systems face significant security risks because they rely on large numbers of simple, connected devices that often operate with minimal protection.
Many IoT devices still rely on default usernames or simple passwords, making them effortless targets for attackers. Once compromised, devices can be used to steal data, disrupt services, or gain deeper network access.
IoT products often remain unpatched for long periods because updates are slow, manual, or unsupported. This leaves known vulnerabilities open and exploitable long after fixes exist.
Lightweight communication protocols in IoT are designed for speed, not security. Without encryption or authentication, attackers can intercept commands or alter data in transit.
IoT ecosystems spread across homes, hospitals, fleets, and factories, creating an enormous attack surface. A single weak device can become a stepping stone to compromise an entire network.
Once infected, IoT devices can be combined into massive botnets capable of overwhelming websites and applications. These coordinated attacks can disable services and cause widespread disruption.
OT systems face high-impact security risks because they run physical operations that cannot tolerate disruption. Any breach has the potential to stop production, damage equipment, or put safety at risk.
Many OT environments still rely on decades-old hardware that lacks built-in security features. Replacing or updating this equipment is difficult, leaving long-term vulnerability gaps.
OT networks often operate without internal segmentation, allowing an attacker to move freely once inside. A single entry point can expose multiple critical systems.
Industrial protocols such as Modbus and BACnet were designed for reliability, not cybersecurity. Commands and data often transfer without authentication or encryption.
Essential OT systems cannot pause for frequent patches or maintenance. Delayed updates increase the chance that known vulnerabilities remain exploitable.
Cyberattacks in OT environments can cause physical outcomes, including equipment failure or operational hazards. The real-world consequences make OT an increasingly attractive target for attackers.
The connection between IoT and OT systems introduces new security challenges because digital devices now interact directly with physical operations. This blending expands the attack surface and makes it easier for threats to move across environments that were once separate.
IoT devices often become entry points that lead attackers into OT networks. A single vulnerable sensor can create a route to critical industrial systems.
Connected environments combine the scale of IoT with the sensitivity of OT. This creates more access points while also raising the potential impact of a breach.
IoT uses lightweight communication methods, while OT depends on industrial protocols built for reliability. The mix of both introduces compatibility and security gaps that attackers can exploit.
IT, IoT, and OT systems frequently share data and infrastructure, reducing isolation. Less separation increases the chances of lateral movement during an attack.
A compromise that begins in IoT can escalate into disruptions that affect production, safety, or critical infrastructure. Convergence turns routine cyber threats into operational risks.
Securing IoT and OT systems requires a layered approach because each environment has different risks and operational needs. The goal is to reduce exposure while keeping devices and industrial processes running safely.
Separating IoT, OT, and IT networks limits lateral movement during an attack. Clear boundaries ensure that a compromise in one area cannot easily spread to another.
Every device and user must prove identity before gaining access, even inside the network. Continuous verification prevents unauthorized commands or lateral expansion.
Limiting permissions reduces the chance of misuse or accidental changes to critical systems. Strong credential management protects both devices and operational equipment.
Behavioral monitoring helps detect unusual activity early, whether it comes from a compromised IoT sensor or an OT controller. Faster detection reduces the chance of operational impact.
A structured update plan helps secure IoT and OT systems without disrupting essential operations. Prioritized patching focuses on the most critical vulnerabilities first.
IoT and OT are becoming more connected every year, bringing new opportunities for efficiency as well as new challenges for security. Understanding how both environments operate helps organizations protect their devices, safeguard critical processes, and reduce operational risk.
A strong security strategy must account for the scale of IoT, the sensitivity of OT, and the growing interdependence between the two. With clear visibility, structured protection, and proactive monitoring, teams can maintain safer and more resilient digital–physical operations.
IoT security protects connected devices and their data, while OT security protects industrial systems that control physical processes. OT incidents carry higher stakes because they can cause real-world disruption or equipment damage.
OT systems rely on legacy hardware that cannot be easily updated. Interrupting these systems for maintenance can impact production and safety.
Yes, interconnected networks allow attackers to move from IoT devices into OT systems if segmentation is weak. A single compromised device can become an entry point.
Manufacturing, energy, utilities, and transportation depend heavily on OT security. These sectors use critical control systems that must operate without interruption.
IoT devices often use weak authentication and rarely receive timely updates. Attackers exploit these gaps to gain access or build large botnets.
IoT provides real-time data and visibility that help OT teams make faster, more informed decisions. This improves efficiency and supports early detection of issues.
Segmentation creates clear boundaries between network zones to limit lateral movement. Compromises in one area are contained before reaching critical systems.
Zero Trust access control, continuous monitoring, strong credential policies, and structured patching enhance protection across both environments. These practices help maintain stability and reduce risk.
