🚀 CloudSEK becomes first Indian origin cybersecurity company to receive investment from US state fund
Read more
Industrial Internet of Things (IIoT) security is the practice of protecting connected industrial devices, networks, and systems from cyber threats. Safety, availability, and operational continuity remain the primary objectives in industrial environments.
Operational technology (OT) environments include sensors, machines, and control systems connected to IT networks and cloud platforms. Increased connectivity improves efficiency while expanding exposure to cyber risks across industrial operations.
Unique IIoT security challenges include legacy systems, real-time operational constraints, and the physical safety impact of cyber incidents. A layered security approach combines device protection, network segmentation, continuous monitoring, and standards such as IEC 62443.
IIoT security in industrial environments means controlling how connected industrial systems operate, communicate, and respond to abnormal or unauthorized activity. The focus remains on keeping production processes stable while preventing manipulation of machines, networks, and control systems.
Industrial operations depend on continuous system availability and predictable process behavior. Security controls must function without interrupting production flow or affecting real-time operational requirements.
IIoT security therefore becomes part of how industrial systems are planned and managed. Network boundaries, access permissions, and monitoring practices are designed to protect operational integrity across connected industrial environments.
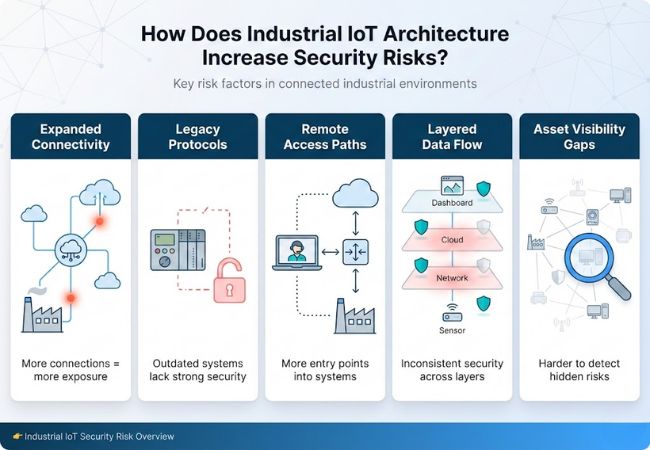
Industrial IoT architecture increases security risks by expanding connectivity across industrial devices, control systems, networks, and platforms.
Industrial IoT environments face security threats that target connected industrial systems, operational processes, and physical infrastructure.
Malware disrupts industrial operations by interfering with control logic, system communication, and machine behavior. Infected systems can trigger unexpected shutdowns or unsafe operating conditions.
Ransomware encrypts industrial systems and restricts access to operational controls and data. Production downtime occurs frequently because industrial environments cannot pause operations safely.
Unauthorized access results from weak credentials, exposed interfaces, or insecure remote connections. Attackers gaining access can modify control parameters or disable safety mechanisms.
Supply chain risks originate from compromised software, firmware, or third-party components. Malicious code introduced during updates or integrations can affect systems before deployment.
Insider misuse includes configuration errors or intentional actions by authorized personnel. Operational technology environments remain vulnerable due to broad access privileges.
Network-based attacks exploit unsecured industrial protocols and flat network structures. Lateral movement across connected systems enables attackers to reach critical control assets.
Denial-of-service events overwhelm industrial networks or devices with excessive traffic. System unavailability can disrupt monitoring, control, and safety functions.
Traditional IT security fails in IIoT systems because industrial operations impose constraints that standard enterprise security models are not designed to handle.
Industrial systems prioritize continuous operation and cannot tolerate frequent shutdowns for patching or maintenance. Security controls that interrupt availability can disrupt production and safety functions.
Operational technology systems depend on deterministic timing and low latency. Security tools that introduce delays or unpredictable processing can interfere with control logic and process stability.
Many industrial devices and control systems were designed before modern cybersecurity requirements existed. Limited processing power and outdated software prevent the deployment of traditional security agents.
Industrial systems directly control physical equipment and human safety mechanisms. Security actions that are acceptable in IT environments can create hazardous conditions in industrial settings.
Industrial networks often use flat architectures and specialized protocols rather than segmented enterprise designs. Standard IT security assumptions do not align with how operational technology networks function.
IIoT security works by applying controls across multiple layers of industrial systems to reduce risk without disrupting operations.
Device-level security focuses on protecting sensors, controllers, and industrial endpoints from unauthorized modification. Measures include authentication, firmware integrity checks, and controlled device access.
Network-level security limits how industrial systems communicate across operational environments. Segmentation, controlled traffic paths, and monitoring reduce unauthorized movement within industrial networks.
Platform-level security governs how industrial data is processed, stored, and accessed in centralized systems. Identity management and access controls restrict system interaction to approved users and services.
Application-level security protects industrial software interfaces and dashboards used for monitoring and control. Access permissions and activity logging prevent misuse of operational functions.
IIoT security is guided by a broad ecosystem of international, sector-specific, architectural, and threat-modeling frameworks designed specifically for industrial and operational technology environments.
IIoT security is applied across industries to protect connected operational systems that control physical processes, safety mechanisms, and service continuity.
Manufacturing environments apply IIoT security to protect production lines, industrial robots, and automated quality systems. Security controls focus on preventing downtime, unauthorized process changes, and intellectual property exposure.
Energy utilities use IIoT security to safeguard power generation, transmission, and distribution systems. Protection priorities include grid stability, continuous service delivery, and regulatory compliance.
Oil and gas operations rely on IIoT security to protect drilling systems, pipeline controls, and remote monitoring infrastructure. Cyber incidents in these environments can lead to environmental damage and operational shutdowns.
Transportation systems apply IIoT security to protect signaling, control systems, and industrial monitoring platforms. System availability and integrity remain critical due to real-time operational dependencies.
Water and wastewater facilities use IIoT security to secure treatment processes, monitoring sensors, and distribution controls. Unauthorized access can directly affect public health and service reliability.
Mining operations apply IIoT security to protect automated equipment, safety systems, and remote monitoring technologies. Operational disruption in mining environments can result in safety risks and production losses.
Chemical processing facilities rely on IIoT security to protect process control systems handling hazardous materials. Security failures can cause unsafe reactions, equipment damage, or regulatory violations.
Implementing IIoT security requires aligning protection measures with industrial operations, system limitations, and long-term risk management objectives.
Clear visibility into connected industrial devices, systems, and communication paths is essential for risk control. Unidentified assets create unmanaged exposure across industrial environments.
Network segmentation separates critical operational systems from IT networks and external connections. Restricted communication paths reduce lateral movement and contain potential incidents.
Access control governs how users, devices, and applications interact with industrial systems. Proper identity and permission management prevents unauthorized operational changes.
Continuous monitoring identifies abnormal behavior across industrial devices and networks in real time. Early detection supports faster response in environments where downtime is costly.
Legacy systems often lack modern security capabilities and cannot be easily modified. Compensating controls such as network protection and monitoring reduce associated risks.
Incident response planning defines how industrial organizations detect, contain, and recover from security events. Structured response processes help maintain operational stability during disruptions.
Industrial Internet of Things security has become essential as industrial systems continue to adopt connectivity across devices, networks, and platforms. Protection of availability, safety, and operational continuity now carries equal importance to data security.
A structured, layered security approach aligned with industrial constraints enables organizations to reduce risk without disrupting operations. Long-term IIoT security depends on visibility, disciplined architecture, and continuous adaptation as industrial environments evolve.
IIoT security concentrates on safeguarding industrial systems connected to IT networks and cloud platforms. OT security traditionally addresses isolated control systems, but IIoT security expands this scope due to increased connectivity.
Legacy industrial systems can be secured using compensating controls such as network segmentation and continuous monitoring. Direct modification is often limited, so protection is applied around the systems rather than inside them.
Poorly designed security controls can disrupt industrial performance. Proper IIoT security is designed to operate without introducing latency, downtime, or process instability.
Cloud connectivity can be secure when strong access controls, encryption, and monitoring are in place. Risk depends on architecture and configuration rather than cloud usage itself.
IIoT environments require continuous monitoring due to real-time operational constraints. Ongoing visibility helps detect abnormal behavior before operational impact occurs.
