🚀 CloudSEK becomes first Indian origin cybersecurity company to receive investment from US state fund
Read more
Key Takeaways:
A Distributed Denial of Service (DDoS) attack is a cyberattack in which a website, server, or network receives traffic beyond its handling capacity from multiple distributed sources. This excess traffic prevents the system from processing legitimate requests.
DDoS attacks commonly use botnets made up of compromised devices to generate traffic at scale. By exhausting bandwidth, CPU, or memory resources, the attack causes service disruption and downtime.
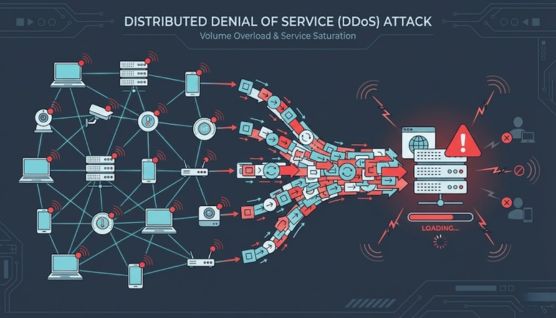
A DDoS attack works by sending a high volume of network or application requests to a target system from multiple distributed sources at the same time. When request volume exceeds what the system can process, legitimate traffic is delayed or dropped.
These requests are typically generated by a botnet composed of compromised computers, servers, or IoT devices. Each device sends traffic simultaneously, creating a load that appears legitimate at the network level.
As bandwidth, CPU, memory, or connection limits are consumed, the service becomes unstable or unavailable. This failure occurs even when the underlying system is not breached or technically compromised.
DDoS attack types are defined by the layer of infrastructure that experiences resource exhaustion. Each type disrupts availability by stressing a different operational boundary.
Volumetric DDoS attacks impact network capacity by saturating inbound and outbound bandwidth. The failure point occurs upstream, often before traffic reaches the application or server.
Protocol-level DDoS attacks target connection-handling mechanisms within network and transport layers. These attacks cause service disruption by exhausting session tables or processing limits in intermediary devices.
Application-layer DDoS attacks affect how web applications process requests rather than how traffic is routed. Disruption occurs when backend logic, databases, or APIs are unable to sustain request load.
Multi-vector DDoS attacks apply pressure across multiple infrastructure layers simultaneously. This forces defenders to respond at several control points at once, increasing mitigation complexity.
DDoS attack tools and methods rely on automated and distributed systems to generate coordinated traffic that consumes network or server resources.
This section explains the attack flow at a conceptual level to support detection and defense, not execution.
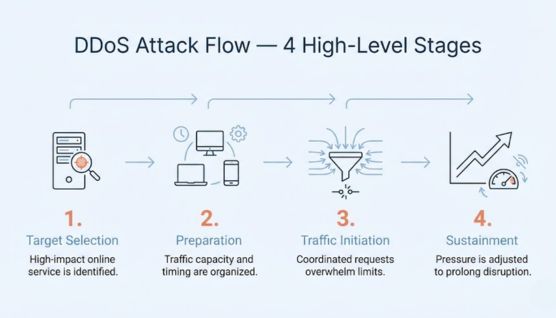
Attackers begin by choosing an online service where downtime would cause disruption or visibility. Selection is usually based on accessibility and dependency rather than technical complexity.
Before activity begins, attackers ensure they have sufficient capacity to generate abnormal traffic levels. This phase focuses on readiness and timing rather than exploiting software flaws.
The attack starts when traffic is directed toward the target in a coordinated manner. The intent is to exceed normal handling limits so legitimate requests are delayed or dropped.
Attackers monitor availability and adjust pressure to prolong disruption. Changes are made to maintain impact until defenses absorb or block the activity.
Websites depend on a continuous ability to receive and respond to user requests, which makes availability their most critical requirement. DDoS attacks exploit this dependency by pushing request volume beyond what the site can reasonably handle.
As traffic pressure increases, normal user interactions are delayed or dropped altogether. Pages fail to load, sessions break, and interactive functions become unreliable or unusable.
Unlike isolated system failures, these disruptions affect every visitor at the same time. The result is a visible outage that directly impacts user trust and service continuity.
Digital services have become deeply embedded in everyday operations, making continuous availability a baseline expectation rather than a competitive advantage. When services go offline, even briefly, the impact is immediate and visible to users.
DDoS attacks exploit this dependency by turning availability into a point of failure. Downtime interrupts transactions, affects customer confidence, and can halt critical online operations without warning.
As online exposure increases, even short disruptions carry long-term consequences. This makes resilience against service disruption a core concern rather than a secondary security issue.
Organizations detect an ongoing DDoS attack by identifying abnormal behavior that deviates from established traffic and performance baselines. Detection focuses on early signals that indicate service availability is being stressed rather than system compromise.
Sudden spikes in request volume, packet rates, or connection attempts are common indicators of a DDoS event. These patterns often appear inconsistent with normal user behavior or historical traffic trends.
Increased response times, timeout errors, or intermittent service failures signal resource exhaustion. Monitoring tools flag these symptoms when infrastructure components begin to operate outside acceptable thresholds.
Logs reveal repeated requests, incomplete connections, or abnormal request distribution across endpoints. Correlating logs across systems helps confirm whether the behavior is coordinated rather than incidental.
Automated monitoring systems trigger alerts when predefined limits for bandwidth, connections, or request rates are exceeded. Behavioral analysis further distinguishes malicious traffic from legitimate usage spikes.
User reports, uptime monitors, and third-party observability services often surface issues before internal systems fully register impact. These external signals help validate and scope the incident in real time.
Effective DDoS protection solutions combine cloud-based infrastructure with layered defenses to maintain availability during abnormal traffic conditions.
Cloud-based DDoS protection absorbs and filters attack traffic before it reaches on-premise or origin infrastructure. Its scalability allows systems to withstand large traffic surges without local resource exhaustion.
Network layer protection focuses on controlling traffic volume and connection behavior before requests reach applications. This prevents bandwidth saturation and reduces pressure on downstream systems.
Application layer protection analyzes request behavior to identify abnormal or malicious patterns. It prevents resource-intensive requests from overwhelming backend logic or services.
Automated mitigation systems detect traffic anomalies and respond in real time without manual intervention. Faster response minimizes downtime during high-intensity or multi-vector attacks.
Choosing the right DDoS protection strategy depends on how well it aligns with traffic patterns, risk exposure, and operational requirements.
The strategy should handle sudden traffic spikes without degrading performance. Scalability ensures protection remains effective as attack volume increases.
Clear visibility into traffic behavior helps teams identify abnormal patterns early. Continuous monitoring supports faster detection and response.
The ability to react immediately to traffic anomalies is critical during active attacks. Faster response reduces downtime and limits service disruption.
The protection approach should integrate smoothly with existing infrastructure and security tools. Seamless integration reduces complexity and operational overhead.
Access to reliable support and incident guidance is important during prolonged or complex attacks. Strong operational backing improves recovery and resilience.
CloudSEK’s platform is centered on proactive cyber risk intelligence rather than direct traffic mitigation. Its capabilities support DDoS readiness by strengthening visibility, anticipation, and preparedness across exposed digital assets.
Through attack surface monitoring tools such as XVigil and BeVigil, CloudSEK helps organizations identify exposed infrastructure, misconfigurations, and initial attack vectors. Addressing these issues reduces the ease with which attackers can target critical systems during a DDoS event.
CloudSEK also delivers actionable threat intelligence from open, deep, and dark web sources, including early indicators of coordinated campaigns and DDoS-for-hire activity. This intelligence is typically paired with specialized mitigation platforms such as Cloudflare, AWS Shield, or Akamai for large-scale traffic filtering and response.
