🚀 CloudSEK becomes first Indian origin cybersecurity company to receive investment from US state fund
Read more
Security analytics is the practice of analyzing security data to identify malicious activity and assess risk within digital and cloud environments. Related security events are examined together to understand their significance rather than as isolated alerts.
Security data is generated by networks, systems, applications, and user actions during normal operation. Viewing this information in combination makes abnormal or attack-related behavior easier to recognize.
A clear picture of ongoing security activity is formed through analysis of recorded evidence. That picture reflects what is occurring across the environment without describing specific tools, techniques, or response actions.
Security analytics works by collecting and examining security data as a whole to identify meaningful patterns and suspicious activity.
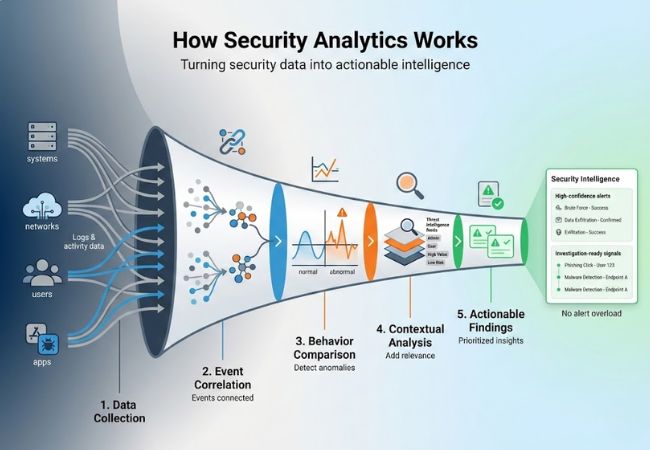
Security data analytics is the examination of security-related data to understand its structure, quality, and relevance within cybersecurity operations. The term refers to working with security data as data, before it is interpreted as threats or incidents.
Relevant data includes logs, records, and activity produced by systems, networks, applications, and identities. Analysis at this stage focuses on accuracy, consistency, and completeness rather than conclusions or response actions.
Within cybersecurity programs, this discipline forms the data foundation that higher-level security analytics relies on. The scope remains limited to preparing and understanding security information without extending into detection logic or threat interpretation.
Security analytics relies on multiple categories of data produced by digital systems and recorded user activity.
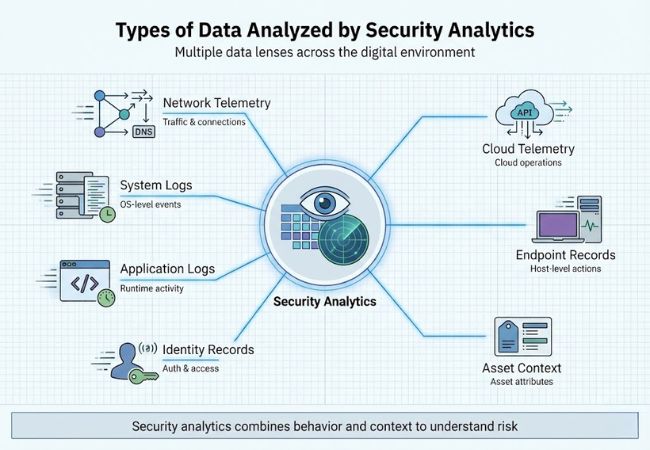
Network telemetry includes records describing connections, traffic flow, and communication paths between systems. Common examples include flow logs, DNS records, and connection metadata.
System logs record operating system events, service activity, and system-level changes. Time-stamped entries provide evidence of how systems function over time.
Application logs capture events generated during software execution. Typical entries include errors, transactions, and configuration-related records.
Identity records document authentication attempts, access approvals, and session activity. User and service account interactions with resources appear within these records.
Endpoint records describe activity occurring on servers, workstations, and virtual machines. Examples include process execution events and file-level changes.
Cloud telemetry originates from cloud platforms, APIs, and managed services. Recorded activity reflects workload operations and configuration states.
Asset context data describes characteristics such as system role, ownership, location, and sensitivity. Descriptive attributes define assets without expressing behavior or intent.
Security analytics interprets threat behavior by placing observed security activity into structured adversary and behavioral contexts.
Observed actions are aligned with known attacker techniques and tactics to determine intent. Frameworks such as MITRE ATT&CK provide a shared reference for categorizing adversary behavior.
Individual security events are connected into ordered activity chains. Sequence-level visibility reveals progression patterns that single events cannot show.
Normal user and system behavior is established from historical activity. Deviations from established baselines highlight potentially malicious behavior without relying on static rules.
Threat intelligence supplies external knowledge about active campaigns, tools, and techniques. Contextual alignment connects internal activity with real-world threat behavior.
Multiple signals are evaluated together to assess likelihood rather than certainty. Confidence scoring reduces misclassification and limits false escalation.
SIEM provides the centralized data management layer that supplies structured security data for security analytics.
Security analytics supplies validated, context-rich findings that drive incident response actions and automation workflows.
Cloud security analytics is the practice of analyzing security data generated within cloud computing environments. The term applies specifically to security visibility in cloud-based infrastructure and services.
Cloud computing environments include public, private, and hybrid platforms that deliver compute, storage, and applications through managed services. Security data in these environments originates from cloud-native systems rather than traditional on-premise infrastructure.
This scope remains limited to identifying and understanding security activity within cloud platforms. Differences from traditional security analytics are addressed separately without redefining the concept here.
Cloud security analytics and traditional security analytics differ primarily in the environments they monitor and the type of security data they analyze.
Security analytics plays a critical role in helping organizations understand security activity and risk across increasingly complex digital environments.
Correlated security data reveals malicious activity that isolated alerts often fail to expose. Visibility improves across networks, systems, users, and cloud resources.
Ongoing analysis highlights areas of exposure tied to assets, identities, and access paths. Risk becomes measurable through observed security activity rather than assumptions.
Contextual evaluation reduces unnecessary alerts generated by standalone events. Security teams gain clearer signals instead of high-volume noise.
Evidence-based insights support consistent and defensible security decisions. Actions rely on observed patterns rather than urgency or guesswork.
Automated analysis allows large volumes of security data to be handled efficiently. Scaling security operations no longer depends solely on additional personnel.
Modern environments span on-premise systems, cloud platforms, and hybrid infrastructure. Security analytics provides unified visibility across these fragmented surfaces.
Preparedness improves through continuous awareness of security conditions. Teams remain informed before incidents escalate into major disruptions.
Security analytics is applied across multiple security functions to examine activity, surface risk, and support informed security operations.
Security analytics identifies malicious activity by correlating signals across systems, users, and networks. Low-visibility attacks become detectable through combined activity rather than isolated alerts.
Unusual behavior by internal users or privileged accounts is examined for misuse or compromise. Activity context helps separate policy violations from legitimate access.
Security events are reconstructed into timelines to understand how incidents unfolded. Analysts gain clarity on entry points, movement, and affected assets.
Authentication and access data is analyzed to identify stolen or abused credentials. Abnormal login patterns and access paths reveal unauthorized account use.
Security activity within cloud services and workloads is examined for misuse and exposure. Analytics provides visibility into actions that are difficult to observe with traditional controls.
Observed security activity is used to evaluate exposure across assets and identities. Risk decisions rely on real operational data rather than static assumptions.
Security analytics provides a way to understand security activity based on actual data rather than isolated alerts or assumptions. Clear visibility into how systems, users, and environments behave allows security teams to reason about risk with accuracy.
As organizations operate across on-premise and cloud environments, consistent analysis of security data becomes essential. Security analytics remains a practical requirement for maintaining awareness of security conditions over time.
Security analytics is used to understand security activity and risk by analyzing security-related data. The goal is to identify meaningful signals within large volumes of recorded activity.
Traditional monitoring focuses on individual alerts and predefined rules. Security analytics examines related activity together to provide context and deeper understanding.
Threat detection is one application, but security analytics also supports investigation, risk assessment, and visibility across environments. Its scope extends beyond identifying attacks.
Security analytics applies to both on-premise and cloud environments. Cloud-specific data sources are analyzed using the same analytical principles.
Security analytics does not replace SIEM systems. SIEM provides data collection and management, while analytics focuses on interpretation and insight.
Machine learning can enhance security analytics but is not mandatory. Rule-based and statistical methods are also commonly used.
