🚀 CloudSEK becomes first Indian origin cybersecurity company to receive investment from US state fund
Read more
A cyber attack is a malicious attempt to access, damage, or misuse computers, networks, or digital data without permission. Its purpose is usually to steal information, disrupt services, or gain control over systems.
As businesses, governments, and individuals depend more on cloud platforms, online services, and connected devices, cyber attacks have become more frequent and widespread. Digital environments now present larger attack surfaces that attract a wide range of threat actors.
Cyber attacks are no longer isolated technical incidents but part of an ongoing digital risk landscape. Understanding their nature, impact, and methods of control is essential for maintaining security and operational stability.
Cyber attacks have evolved from occasional security incidents into a continuous and large-scale digital threat. Financial fraud, ransomware, and data breaches now occur frequently and cause sustained damage rather than isolated disruption.
According to the FBI Internet Crime Complaint Center (IC3), Americans reported 859,532 cybercrime complaints in 2024, with total losses exceeding $16.6 billion. U.S. authorities warn that cybercrime activity and financial impact are expected to continue rising through coming years as attackers increasingly rely on automation and advanced techniques.
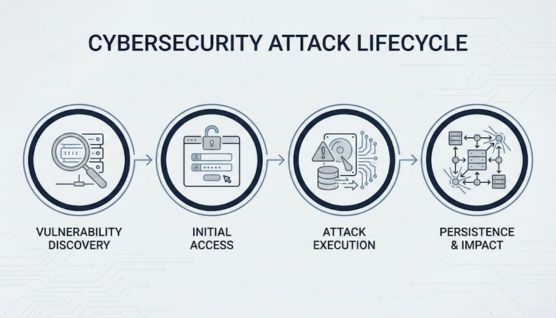
A cyber attack typically begins when an attacker identifies a weakness in a system, application, or user account that can be exploited. These attackers may be cybercriminals, organized groups, insiders, or state-sponsored actors, depending on the goal of the attack.
Once a weakness is found, attackers attempt to gain unauthorized access to networks, devices, or data. Common targets include user credentials, databases, cloud environments, and critical business systems.
After access is obtained, the attacker carries out actions such as stealing data, encrypting files, disrupting services, or moving laterally within the environment. Many attacks continue unnoticed for long periods, allowing greater damage before detection.
Cyber attacks use different techniques depending on the attacker’s goal and the weakness being exploited. Each type follows a distinct method and targets specific systems, data, or users, which is why understanding these categories is essential.
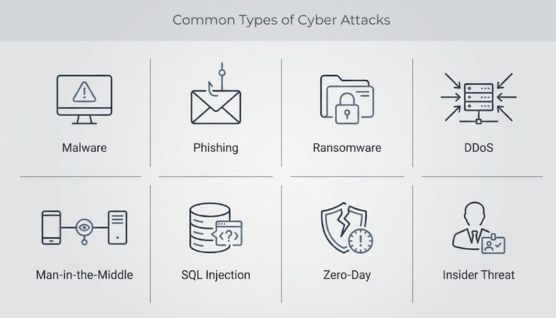
Malware attacks involve malicious software designed to infiltrate systems without user consent. These programs are often delivered through infected files, compromised websites, or malicious downloads.
Once installed, malware can spy on activity, steal data, or give attackers remote control of devices. It commonly targets endpoints such as computers and mobile devices, making it one of the most widespread attack methods.
Phishing attacks rely on deceptive messages that appear legitimate to trick users into revealing sensitive information. These messages are usually delivered through email, text messages, or fake websites.
The primary targets of phishing are user credentials, financial information, and personal data. Because phishing exploits human trust rather than technical flaws, it remains highly effective and difficult to eliminate.
Ransomware attacks encrypt files or lock systems to deny access to data. Attackers then demand payment in exchange for restoring access.
These attacks primarily target businesses and institutions that rely on continuous system availability. Ransomware can cause severe operational disruption and long recovery periods even after payment.
DDoS attacks attempt to overwhelm systems by flooding them with excessive traffic. This prevents legitimate users from accessing websites or online services.
The main target of a DDoS attack is system availability rather than data. Such attacks are often used to disrupt operations, damage reputation, or distract security teams from other intrusions.
Man-in-the-middle attacks occur when attackers secretly intercept communication between two parties. This usually happens on unsecured or poorly protected networks.
By capturing data in transit, attackers can steal credentials or alter information. These attacks commonly target login sessions, financial transactions, and private communications.
SQL injection attacks exploit vulnerabilities in applications that interact with databases. Attackers insert malicious queries through input fields to manipulate database operations.
This allows unauthorized access to sensitive records or administrative functions. Poor input validation and outdated applications are common enablers of this attack type.
Zero-day exploits target vulnerabilities that are unknown to software vendors at the time of attack. Because no patch exists, defenses are often unprepared.
Attackers use these exploits to gain early access before detection measures are available. Zero-day attacks are especially dangerous due to their stealth and high success rate.
Insider threats originate from individuals with legitimate access to systems or data. These may include employees, contractors, or partners.
Such threats can be intentional or accidental, but the impact is often severe due to existing permissions. Insider incidents commonly affect sensitive data and internal systems.
Real-world cyber attacks affect different targets in different ways, depending on the attacker’s objective and the systems involved.
The impact of a cyber attack can extend far beyond the initial breach, affecting finances, operations, data security, and long-term trust.
Detecting cyber attacks early helps reduce damage and prevents attackers from maintaining long-term access to systems. Most detection relies on identifying unusual activity rather than waiting for visible disruption.
Unusual spikes in traffic, unexpected connections, or abnormal data transfers can indicate an attack in progress. Monitoring network behavior helps identify intrusions before they escalate.
Unexpected crashes, slow performance, or unauthorized configuration changes may signal compromise. These signs often appear after malware execution or unauthorized access.
Security tools generate alerts when known threat patterns or anomalies are detected. Reviewing alerts and logs regularly improves response speed and accuracy.
Threat intelligence provides insight into emerging attack methods and indicators of compromise. External intelligence helps organizations recognize threats that internal monitoring may miss.
Mitigation focuses on limiting damage once a cyber attack has already occurred. Quick and coordinated action is critical to reduce further harm and shorten recovery time.
Affected systems should be disconnected immediately to stop the spread of the attack. Isolation prevents attackers from moving laterally across networks.
Compromised accounts and credentials must be disabled or reset as soon as possible. This reduces the attacker’s ability to maintain access.
Clean backups allow systems and data to be restored without negotiating with attackers. Regular backup testing ensures recovery can happen quickly.
Applying security patches closes the vulnerabilities used in the attack. This helps prevent repeat exploitation of the same weakness.
Preventing cyber attacks focuses on reducing the chances of an attack succeeding before any damage occurs. Strong security fundamentals and consistent practices play a critical role in lowering risk.
Strong authentication methods help ensure only authorized users can access systems and data. Multi-factor authentication significantly reduces the risk of account compromise.
Regular software updates fix known security vulnerabilities before attackers can exploit them. Unpatched systems remain one of the most common entry points for attacks.
User awareness training helps individuals recognize phishing attempts and suspicious activity. Informed users are less likely to fall victim to social engineering attacks.
Network security controls such as firewalls and intrusion prevention systems help filter malicious traffic. Segmentation limits the spread of attacks if a breach occurs.
Secure system configuration reduces unnecessary exposure and attack surfaces. Applying least-privilege access limits what attackers can do if access is gained.
Cyber attacks continue to evolve as technology, connectivity, and attacker capabilities advance. Future threats are expected to become more automated, targeted, and difficult to detect.
Attackers are increasingly using automation and artificial intelligence to scale phishing, malware creation, and vulnerability discovery. This allows attacks to adapt faster and target victims more efficiently.
Third-party vendors and software providers are becoming common attack entry points. A single compromised supplier can expose multiple organizations at once.
Misconfigured cloud services and exposed APIs are creating new attack surfaces. As more data moves to cloud environments, attackers are shifting focus away from traditional networks.
Ransomware operations are evolving into organized service-based models. This lowers the barrier to entry and increases the volume of attacks.
CloudSEK helps organizations identify external digital risks by monitoring exposed assets, threat actors, and emerging attack patterns in real time. This visibility allows security teams to understand potential threats before they are exploited.
By detecting early indicators of cyber threats, CloudSEK supports faster identification and response to attacks. Early awareness reduces dwell time and limits the impact of malicious activity.
Proactive threat intelligence also strengthens prevention and mitigation efforts by prioritizing risks based on real-world exposure. This enables organizations to focus resources on the most critical threats rather than reacting after damage occurs.
