🚀 CloudSEK becomes first Indian origin cybersecurity company to receive investment from US state fund
Read more
Key Takeaways
Cybersecurity policies are documented rules that guide how an organization secures its digital assets and information systems. They define acceptable behavior, security requirements, and responsibilities for employees, contractors, and third parties.
These policies serve as the foundation of an organization’s information security governance framework. They translate high-level security objectives into enforceable rules that support consistent decision-making.
Cybersecurity policies are important because they establish a structured and consistent approach to managing digital risk.
Cybersecurity policies operate through governance oversight, technical enforcement, and daily employee compliance.
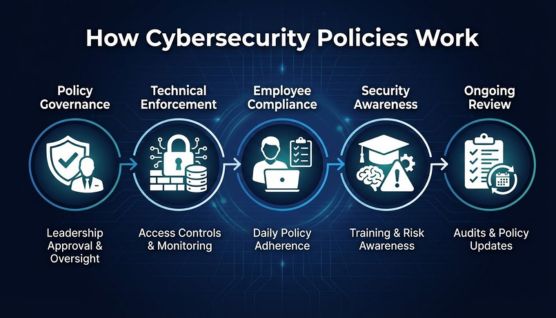
Organizations rely on multiple cybersecurity policies because risk does not exist in a single place. Each policy addresses a specific security exposure while reinforcing a shared governance model across systems, data, and users.
The Information Security Policy sits at the center of the security program and sets direction for all other policies. It connects security objectives with business risk, regulatory obligations, and recognized standards such as ISO 27001 and the NIST Cybersecurity Framework.
Security teams use this policy to guide decision-making rather than resolve individual issues in isolation. When written correctly, it keeps technical controls, audits, and operational priorities aligned.
The Acceptable Use Policy explains how systems, networks, and organizational data may be used during daily work. It draws a clear boundary between productive activity and behavior that introduces unnecessary risk.
Clear usage rules reduce accidental misuse and limit insider-related exposure. They also provide a consistent basis for response when violations occur.
Access Control Policy determines who is allowed to access systems and data, under what conditions, and at what level. It supports identity management, privilege assignment, authentication requirements, and periodic access reviews.
Restricting access limits the blast radius of compromised credentials. This policy remains one of the most effective safeguards against lateral movement during an attack.
The Data Protection and Privacy Policy governs how sensitive, regulated, and personal information is handled throughout its lifecycle. Teams rely on it when storing, sharing, retaining, or disposing of data.
Consistent handling supports privacy regulations and contractual obligations. It also reduces exposure caused by unmanaged data locations and excessive access.
The Incident Response Policy prepares the organization for security events before they occur. It defines reporting channels, response roles, investigation steps, and communication expectations.
Clear direction enables faster decisions under pressure. It also supports regulatory notification requirements and coordinated external communication.
Network and Endpoint Security Policy focuses on protecting servers, networks, and user devices from unauthorized access and exploitation. It guides decisions related to firewalls, endpoint protection, monitoring, and segmentation.
As remote work and cloud environments expand, centralized control becomes harder to maintain. This policy helps security teams enforce consistent protection across distributed systems.
The Email Security Policy addresses threats delivered through email, including phishing, malware, and social engineering. It sets expectations for user behavior and defines how suspicious messages are reported.
Because email remains a primary attack vector, clarity is critical. Strong habits significantly reduce the success rate of human-focused attacks.
BYOD policy allows personal devices to be used without weakening organizational security. It explains access conditions, required safeguards, and acceptable monitoring practices.
Flexibility does not have to increase risk. Clear boundaries protect organizational data even when devices are not company-owned.
When writing a cybersecurity policy, the goal is not to produce documentation for its own sake but to create something people can actually follow. The components below help ensure the policy is clear, enforceable, and relevant to real security risks.
Start by making it clear what the policy is meant to protect and why it exists. Clearly stating the scope helps readers understand which systems, users, and data the policy applies to.
Every policy should clearly state who is responsible for enforcing and maintaining it. This prevents confusion and ensures security tasks are not ignored or assumed to belong to someone else.
Security controls explain how policy expectations are applied in practice through technical and administrative measures. These controls guide how access is restricted, activity is monitored, and systems are configured.
Risk management connects the policy to real threats and business impact. It helps prioritize controls based on likelihood, severity, and organizational tolerance for risk.
Policies should reflect applicable regulations and industry standards. This alignment supports audits and reduces legal and regulatory exposure.
A policy must explain how compliance is monitored and what happens when rules are violated. Clear enforcement reinforces that the policy is operational and taken seriously.
Cybersecurity policies should be reviewed regularly to remain effective. Updates ensure the policy stays aligned with evolving threats, technologies, and business changes.
The policy should be easy to access and written in language employees can understand. Clear communication helps people apply the policy correctly in daily work.
Cybersecurity policies align with recognized frameworks to ensure structured risk management and audit readiness.
Effective cybersecurity policies are built through risk awareness, clear structure, and consistent enforcement.
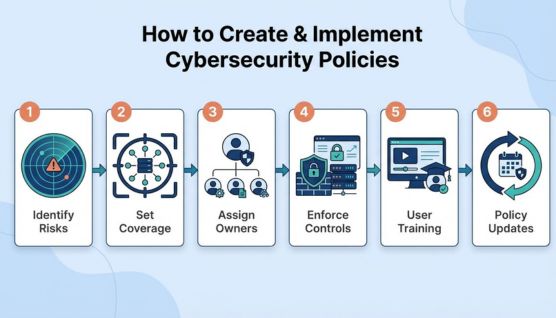
Identify critical assets, threat scenarios, and business impacts. This ensures policies address real organizational risks.
Clearly specify users, systems, and data covered by each policy. Well-defined scope prevents ambiguity.
Designate owners for approval, enforcement, and maintenance. Ownership ensures accountability throughout the policy lifecycle.
Support policies with access controls, monitoring, and security tooling. Technical enforcement strengthens compliance.
Provide ongoing security awareness training. Informed users reduce accidental violations.
Review policies annually or after major changes. Regular updates keep policies relevant.
Many organizations weaken cybersecurity policies through design and execution failures.
Cybersecurity policies define security rules, but enforcing them across cloud assets and external exposure remains challenging. Effective enforcement requires visibility into threats beyond internal networks.
CloudSEK supports policy enforcement by identifying exposed digital assets and real-time external threats. This intelligence helps align access control, data protection, and incident response policies with actual risk conditions.
By integrating CloudSEK insights into governance workflows, organizations can validate whether policies remain effective. This enables faster adjustments and stronger alignment between documented controls and real-world security posture.
