🚀 CloudSEK becomes first Indian origin cybersecurity company to receive investment from US state fund
Read more
Crypto ransomware, also known as encryption ransomware, is malicious software that encrypts files and demands payment for a decryption key. Once the encryption process is complete, victims lose access to important data even though the operating system may still function normally.
The term “crypto” refers to cryptography, which is the method used to lock files, not cryptocurrency itself. However, attackers usually request ransom payments in digital currencies because they are harder to trace and difficult to reverse.
Unlike other forms of malware that focus on surveillance or disruption, crypto ransomware directly targets data availability. This approach makes recovery difficult and often forces victims to consider payment despite the lack of any guarantee that access will be restored.
Crypto ransomware follows a predictable attack sequence that begins with system infection, progresses through file encryption, and ends with a ransom demand for data recovery.
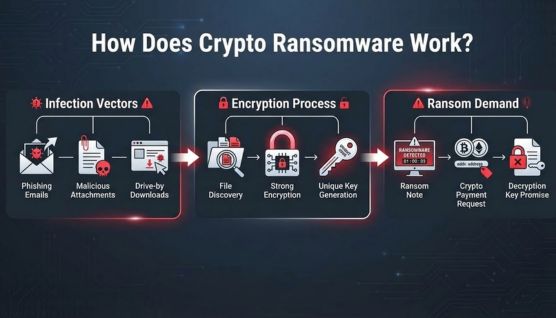
Crypto ransomware commonly enters systems through deceptive delivery methods that exploit user behavior or unpatched vulnerabilities.
After gaining access, the ransomware scans the system to identify files that will cause maximum disruption when encrypted.
Once files are encrypted, the ransomware informs the victim and outlines the conditions for data restoration.
Cryptocurrency is the primary payment method for crypto ransomware attacks because it enables fast, cross-border transactions outside traditional financial systems.
Digital currencies allow attackers to collect payments without relying on banks or regulated intermediaries. This enables ransomware operations to scale globally with minimal transaction friction.
Cryptocurrency transactions are difficult to directly link to real-world identities. Attackers exploit this gap to reduce attribution risk and complicate investigations.
Once confirmed, cryptocurrency payments cannot be reversed. This removes recovery options after funds are sent, regardless of whether decryption keys are provided.
Bitcoin remains the most commonly requested ransom currency due to its liquidity and widespread acceptance. Some attackers also favor privacy-focused cryptocurrencies to further reduce transaction visibility.
FinCEN data indicates that approximately 97% of reported ransomware transactions involved Bitcoin. The FBI has also observed a rise in Monero demands, with some groups adding 10%–20% payment premiums to reduce tracking risk.
Because ransom pressure depends on urgency, attackers carefully select which files to encrypt to maximize disruption.
Crypto ransomware targets files that are essential to personal use or business operations, as restricting access creates immediate leverage. The focus is on disruption rather than volume.
Documents, photos, and videos are frequently encrypted because they often contain irreplaceable personal information. Loss of access creates emotional pressure even when the system remains usable.
Databases, financial records, and internal documents are high-value targets in organizational environments. Encrypting this data can halt operations and quickly escalate financial impact.
Backup files are often encrypted to eliminate recovery options before victims can respond. Without usable backups, organizations face significantly fewer alternatives.
Attackers prioritize files based on how quickly their absence disrupts normal activity.
Crypto ransomware and locker ransomware differ in how they restrict access and apply pressure on victims. While both demand payment, the method used to deny access affects recovery options.
By targeting data rather than device access, crypto ransomware typically causes more lasting damage.
Crypto ransomware is dangerous because it removes access to essential data while systems remain online and usable. This prevents work from continuing without triggering immediate system failure.
Encrypted files stop personal tasks and business operations that depend on documents, databases, or records. The resulting downtime often leads to financial loss, compliance issues, and long recovery timelines.
Ransom payment does not guarantee data restoration. Victims must make decisions under pressure without reliable assurance that access will be restored.
File recovery after a crypto ransomware attack depends mainly on preparation rather than post-attack actions. Once encryption is complete, recovery options become limited and uncertain.
Attackers control the decryption keys from the moment files are encrypted. Access to those keys is never guaranteed, even after payment.
Some victims attempt payment to restore access to their files. Outcomes vary widely and often result in partial recovery or no response at all.
Offline backups provide the most reliable path to recovery. Systems can be restored without engaging with attackers when clean backups are available.
Public decryptors exist for a small number of older ransomware variants. Modern crypto ransomware relies on strong encryption that cannot be bypassed through tools alone.
Improper recovery attempts can permanently damage encrypted files. Rushed decisions often reduce recovery options instead of improving them.
Preparation and prevention determine recovery success far more than any action taken after encryption.
Preventing crypto ransomware depends on reducing exposure, limiting attack surfaces, and maintaining recovery options before an incident occurs.
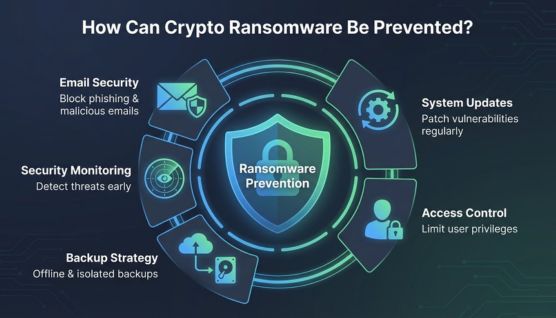
Phishing remains a primary delivery method for crypto ransomware. Filtering malicious emails and training users to recognize suspicious messages reduces initial infection risk.
Unpatched software provides common entry points for ransomware attacks. Regular updates close known vulnerabilities and limit exploit opportunities.
Reliable backups protect data from permanent loss after encryption. Offline and isolated backups prevent ransomware from encrypting recovery files.
Restricting user privileges limits how far ransomware can spread within a system. Reduced access prevents attackers from encrypting shared or critical resources.
Early detection helps contain ransomware before widespread encryption occurs. Monitoring unusual activity allows faster isolation and response.
Effective prevention lowers the likelihood of infection and reduces the impact of successful attacks.
Actions taken immediately after a crypto ransomware attack determine how much damage spreads and how much data can ultimately be preserved.
Disconnect infected devices from networks as soon as ransomware activity is detected. Isolation prevents further encryption and limits lateral movement across connected systems.
Avoid wiping systems or modifying files before assessing the scope of the attack. Preserving logs, ransom notes, and encrypted files supports investigation and recovery decisions.
Identify which systems, files, and backups are affected. Understanding the extent of encryption helps prioritize response and restoration efforts.
Paying the ransom does not guarantee file recovery and may encourage further attacks. Decisions should be based on recovery options rather than pressure from attackers.
Restore data only from clean, verified backups after removing the ransomware infection. Reconnecting systems too early can lead to reinfection or additional data loss.
Analyze how the attack occurred and address gaps in security controls. Strengthening defenses reduces the likelihood of future incidents.
Responding methodically limits damage and supports recovery, while rushed actions often increase long-term loss.
CloudSEK supports crypto ransomware prevention by identifying external risk signals before attacks reach the encryption stage. Its focus is on early detection of attacker intent, exposed assets, and infrastructure abuse rather than post-incident response.
Using its XVigil platform, CloudSEK monitors surface, deep, and dark web activity for indicators such as leaked credentials, ransomware group discussions, and phishing infrastructure. This visibility helps organizations detect targeting patterns and campaign preparation before systems are compromised.
CloudSEK also helps reduce attack entry points by identifying exposed services and misconfigurations commonly exploited for initial access. By delivering context-driven alerts, it enables security teams to act early and limit the conditions that allow crypto ransomware attacks to succeed.
