🚀 CloudSEK becomes first Indian origin cybersecurity company to receive investment from US state fund
Read more
Key Takeaways:
Quishing, or QR phishing, is a form of digital fraud where attackers embed an encoded URL inside a QR code to redirect users to a deceptive online destination. It adapts traditional phishing into a format that looks familiar and blends seamlessly into everyday settings like menus, service labels, and delivery notices.
This method is growing because QR codes conceal their destination, giving users no visual way to evaluate the link before scanning. By combining convenience, routine scanning behavior, and a hidden redirect path, quishing introduces a subtle entry point for unauthorized access and credential harvesting.
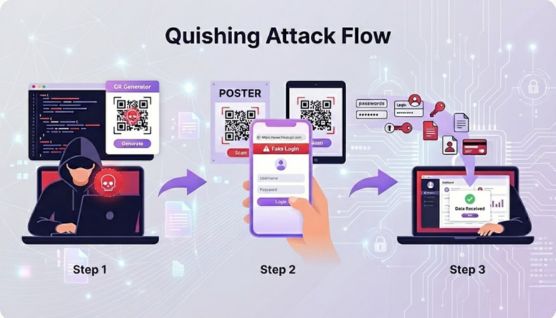
A quishing attack begins when an attacker generates a QR code linked to a controlled webpage that imitates a legitimate service. The code is placed where users naturally expect it, creating a believable context that lowers suspicion before the scan.
When the victim scans the QR code, their mobile browser immediately loads the encoded URL, presenting a spoofed interface designed to look authentic. This environment allows attackers to prompt the user for information while masking the fraudulent nature of the page.
If the victim submits credentials, financial data, or personal details, the attacker captures the information through a harvesting mechanism built into the site. The data is then used for unauthorized access, financial manipulation, or escalation into broader compromise.
QRLJacking is a session-hijacking technique where attackers exploit QR-based login systems to take over a user’s active account session.
Quishing is considered a serious threat because it transforms phishing into an image-based payload that is harder for security tools, filters, and users to evaluate before interaction.
Quishing creates practical obstacles for both users and organizations because QR interactions often fall outside normal security workflows. These limitations make it harder to apply consistent inspection, control, and verification across the environments where QR codes are used.
Attackers can replace authentic QR codes with deceptive stickers in public spaces, making it difficult to validate whether a code is genuine. Since the physical placement appears normal, users have no clear reference point to tell the difference.
Most QR interactions happen on personal smartphones that are not managed by corporate security tools. This reduces visibility for organizations and leaves mobile browsers more exposed to harmful redirections.
Security systems are primarily designed to scan text-based URLs rather than extract encoded data from images. This gap limits the ability of email filters and automated defenses to identify dangerous QR code destinations before users scan them.
Quishing attacks appear in places where QR codes are used for quick access, payments, or service interactions. Attackers target environments that feel routine so the malicious QR code blends into everyday activity.
Attackers send QR codes in emails under the pretext of verifying accounts, retrieving documents, or completing security checks. These codes look legitimate because users are accustomed to receiving service-related reminders through email.
Fake QR stickers are placed on posters, parking meters, menus, or event banners to lure people into scanning them in passing. The setting feels ordinary, so victims rarely notice that the original code has been replaced.
Scammers attach QR codes to delivery notices, payment updates, customer support messages, or cryptocurrency prompts. These contexts create urgency, increasing the likelihood that someone will scan the fraudulent code without evaluating it.
Detecting quishing requires paying attention to both the physical appearance of the QR code and the behavior of the website it leads to. Small inconsistencies can reveal whether the code belongs to a legitimate source.
A QR code that looks like a recent sticker, appears misaligned, or covers another printed element may indicate tampering. Any QR code placed in an unexpected location should be approached with caution.
If scanning the code reveals a domain with misspellings, unusual extensions, or unrelated branding, it is likely malicious. Legitimate services maintain consistent and recognizable domains.
A website that immediately asks for login credentials, personal details, or payment information is a strong warning sign. Reputable platforms do not request sensitive data without clear context and authentication.
Falling for a quishing attack can expose sensitive information and lead to significant financial or account-related harm. The consequences extend beyond the initial interaction and may affect both individuals and organizations.
Attackers can capture usernames, passwords, and multi-factor authentication details through deceptive login pages. Stolen credentials are often used for unauthorized account access or sold on criminal marketplaces.
Malicious QR codes may lead to fraudulent payment pages or account verification forms designed to harvest banking information. This data enables unauthorized transactions, payment redirection, or direct account compromise.
Some quishing sites deploy malware or remote access tools that infiltrate the victim’s device. This foothold can be used to monitor activity, steal additional data, or move laterally into business environments.
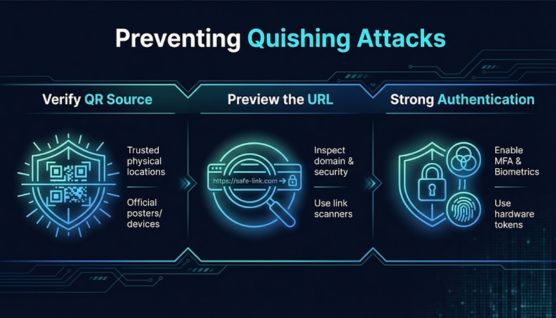
Preventing quishing requires combining cautious scanning habits with security tools that limit the risk of interacting with untrusted QR codes. Both individual users and organizations benefit from reinforcing safe scanning behavior.
Scan only QR codes from known and reputable origins, especially when dealing with payments or account access. Avoid scanning codes placed in public spaces unless their authenticity is clear.
Enable features or apps that display the destination URL before opening it in a browser. Previewing the link helps identify mismatched brands, altered domains, or unsafe redirections.
Use multi-factor authentication and secure login practices to reduce the damage from stolen credentials. Even if attackers obtain a password, additional authentication barriers limit their ability to access accounts.
Quishing has quickly evolved into a mainstream cyber threat because QR codes now sit at the center of everyday interactions, making it easier for attackers to disguise harmful destinations. Staying aware of how these scams operate helps users recognize situations where a QR code may not be as trustworthy as it appears.
By combining cautious scanning habits with basic security tools and stronger authentication practices, both individuals and organizations can significantly reduce their exposure. Consistent vigilance and informed decision-making remain the most effective ways to avoid falling victim to QR-based deception.
