🚀 أصبحت CloudSek أول شركة للأمن السيبراني من أصل هندي تتلقى استثمارات منها ولاية أمريكية صندوق
اقرأ المزيد
Modern enterprises operate in highly distributed, cloud-driven, and interconnected digital environments where security risks extend far beyond traditional network boundaries. As organisations scale, adopt cloud services, enable remote work, and integrate third-party ecosystems, security becomes a business-critical function rather than a purely technical concern. Enterprise security addresses this reality by providing a structured, organisation-wide approach to managing risk, protecting critical assets, and ensuring operational resilience.
This article explores how enterprise security works, why it is essential, what it protects, the core components and challenges involved, and how organisations build, govern, and evolve enterprise security programs to support secure and sustainable business operations.
Enterprise security is the comprehensive protection of an organisation’s data, systems, identities, networks, and operations across the entire enterprise environment.
It encompasses technology controls, operational processes, workforce practices, and governance frameworks to secure digital and organisational assets at scale.
The primary objective of enterprise security is risk reduction, operational resilience, and uninterrupted business continuity in complex and distributed environments.
Enterprise security works by applying layered controls across the organisation, integrating people, processes, and technology, and continuously adapting protections based on risk, visibility, and operational feedback.
Layered Security Across Enterprise Environments
Enterprise security applies multiple security layers across on-premise systems, cloud platforms, endpoints, applications, and networks. Each layer reduces exposure and limits attack progression when another control fails. This layered design strengthens resilience in hybrid and distributed enterprise environments.
Integration of People, Processes, and Technology
Enterprise security operates as an enterprise-wide operating model rather than a collection of tools. People establish accountability and decision ownership, processes define repeatable workflows and escalation paths, and technology enforces controls while generating visibility. This integration ensures security actions align with business priorities and scale consistently across the organisation.
Continuous, Risk-Driven Security Lifecycle
Enterprise security functions as a continuous lifecycle guided by risk and business impact:
This lifecycle ensures enterprise security evolves alongside threats, technology changes, and organisational growth.
Centralised Monitoring, Automation, and Policy-Driven Enforcement
Enterprise security relies on centralised monitoring to correlate signals across environments and support faster, informed decision-making. Automated workflows and orchestration reduce response time and operational friction, while policy-driven enforcement ensures access, data handling, and security controls remain consistent across on-premise, cloud, and hybrid environments.
Together, these mechanisms enable enterprise security to operate at scale, remain aligned with business risk, and support secure, resilient operations in complex digital environments.
Enterprise security is important because modern organisations operate large, distributed, and constantly evolving digital environments where security failures directly impact financial performance, regulatory standing, and executive accountability.
Enterprise security protects the business by reducing risk across critical operational and strategic areas:
Protection of Sensitive Assets
Enterprises manage customer data, intellectual property, financial records, and regulated information that require continuous protection to prevent financial loss and legal exposure.
Operational Continuity
Cyber incidents cause downtime, service disruption, and productivity loss across business units and geographies, directly affecting revenue and service delivery.
Regulatory and Legal Compliance
Enterprises must comply with regulations such as GDPR, HIPAA, PCI DSS, and industry-specific mandates, where non-compliance results in fines, penalties, and regulatory scrutiny.
Reputation and Customer Trust
Data breaches and service outages reduce customer confidence, damage brand credibility, and create long-term market impact.
Support for Digital Transformation
Cloud adoption, remote work, and third-party integrations expand the attack surface and increase security complexity, making enterprise security essential for safe innovation and growth.
Enterprise security reduces organisational risk by safeguarding financial stability, supporting executive and board-level accountability, and enabling resilient, compliant, and secure business operations at scale.
Enterprise security protects the full range of assets that enable an organisation to operate securely, remain compliant, and maintain continuity across complex and interconnected digital ecosystems.
Data Assets
Customer information, intellectual property, financial records, employee data, and regulated information stored across enterprise systems, cloud platforms, and third-party services.
IT Infrastructure
Networks, servers, endpoints, data centres, cloud workloads, and externally connected environments that support day-to-day enterprise operations.
Applications and Digital Services
Web applications, APIs, enterprise software, SaaS platforms, and internally developed systems used by employees, partners, vendors, and customers.
Identities and Access
Employees, contractors, partners, service accounts, and privileged users accessing enterprise and extended-enterprise resources.
Business Operations
System availability, service uptime, workforce productivity, and continuity of critical business processes across regions and business units.
External Enterprise Footprint
Public-facing digital assets, domains, integrations, and partner-connected systems that represent the organisation’s extended attack surface and brand presence.
By protecting these areas collectively, enterprise security reduces risk across internal and external environments, limits disruption, and supports reliable, trusted operations at organisational scale.
Enterprise security is built on a set of interconnected technical, operational, and governance components that collectively protect the organisation across systems, users, data, and environments. Each component addresses a distinct risk area while supporting enterprise-wide visibility, control, and resilience.
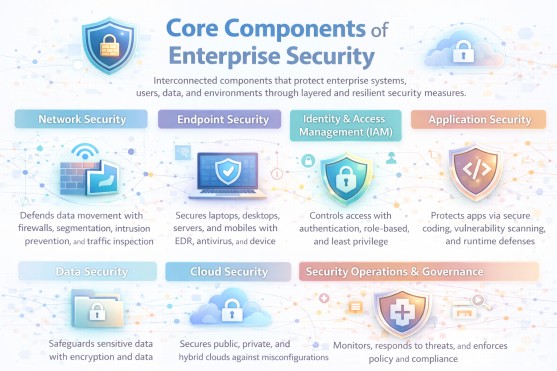
Together, these components form a layered and operational enterprise security framework that reduces exposure, limits breach impact, and supports secure, resilient business operations at scale.
Enterprise security must address a wide range of persistent and evolving threats that target systems, data, users, and operations. These threats are frequent, sophisticated, and capable of causing significant operational and financial impact.
The threat landscape remains intense: IBM surveys show that 40 % of C-suite leaders reported a recent cyberattack, and 76 % of security leaders are concerned about increasing threat sophistication.
The 2025 Global Cybersecurity Readiness Report states that despite defensive investments, many organisations face multiple events annually, and fewer than 37 % consider themselves fully prepared for cyberattacks.
Enterprise security provides a holistic, scalable approach that addresses modern organisational risk, while traditional IT security is limited in managing today’s distributed and identity-driven environments.
Enterprise security architecture defines how security controls, technologies, and processes are designed, prioritised, and integrated across the organisation to manage risk consistently and at scale.
It provides a unified framework that aligns security decisions with business objectives and IT architecture by embedding protection across users, systems, data, and networks.
Enterprise security architecture enables organisations to scale securely, adapt to evolving threats, and maintain consistent, business-aligned protection across complex and distributed environments.
Governance, Risk, and Compliance (GRC) provides the structural foundation that makes enterprise security measurable, accountable, and aligned with business objectives and regulatory obligations.
GRC ensures security decisions are guided by risk awareness, executive oversight, and consistent policy enforcement across the organisation.
Security Governance
Defines policies, standards, roles, and accountability models that guide how security is implemented, monitored, and enforced across the enterprise, ensuring leadership visibility and ownership.
Risk Management
Identifies, assesses, and prioritises cyber risks based on business impact, asset criticality, and threat exposure, enabling informed investment decisions and continuous risk adjustment.
Regulatory Compliance
Ensures alignment with legal, industry, and contractual requirements such as data protection, privacy, and audit obligations, reducing regulatory exposure and enforcement risk.
Policy Enforcement and Oversight
Translates governance policies into operational controls and continuously verifies adherence across systems, environments, and teams to maintain consistent security posture.
Audit, Reporting, and Assurance
Provides evidence of security posture, control effectiveness, and compliance status through structured reporting to executives, boards, regulators, and auditors.
By embedding accountability, continuous risk evaluation, and oversight into security operations, GRC enables enterprise security programs to operate consistently, adapt to change, and demonstrate trustworthiness in regulated and high-risk environments.
Enterprise security faces persistent challenges driven by expanding digital environments, increasing threat sophistication, and the need to align security outcomes with business priorities. These challenges impact visibility, control, operational efficiency, and executive decision-making.
These challenges require enterprises to adopt integrated security architectures, improve risk context and visibility, leverage automation, and prioritise controls based on business impact to maintain effective protection at scale.
Enterprise security requires continuous visibility into external risk, intelligence-led prioritisation, and strong alignment between security operations, governance, and business impact.
CloudSEK supports these requirements by extending enterprise security beyond internal controls into the external digital environment where many modern threats emerge. Capabilities such as External Attack Surface Management (EASM) help organisations identify exposed assets, misconfigurations, and shadow IT across cloud and third-party environments.
Threat intelligence and digital risk monitoring improve early awareness by tracking credential leaks, phishing infrastructure, brand abuse, and threat actor activity across the open, deep, and dark web.
By correlating external exposure with risk prioritisation based on exploitability and business impact, security teams can reduce alert noise and focus on the most critical risks. Integration with SOC and GRC workflows strengthens response coordination, reporting, and governance, aligning external risk intelligence with enterprise security programs and long-term resilience objectives.
