🚀 CloudSEK becomes first Indian origin cybersecurity company to receive investment from US state fund
Read more
VPN protocols play a critical role in shaping how secure, fast, or stable a VPN connection feels during everyday use. They influence everything from connection reliability to how well a VPN handles streaming, remote work, or public Wi-Fi.
Because different protocols are built with different priorities, no single option fits every situation or device type. Knowing how these protocols differ helps users choose the right balance of speed, security, and compatibility.
Protocol behavior changes based on factors like signal conditions, encryption load, and network restrictions. As these conditions shift, the connection’s security and responsiveness can vary noticeably.
A VPN protocol is a set of rules that controls data encryption and transfer between your device and a VPN server. It defines the encrypted tunnel used to protect online activity as traffic moves across public and private networks.
Different VPN protocols use distinct encryption standards and connection designs, which explains why options such as WireGuard, OpenVPN, and IKEv2 behave differently across devices. Some focus on speed and efficiency, while others prioritize stronger protection or broader compatibility.
The protocol selected affects connection stability, loading times, and the level of privacy available on networks like public Wi-Fi. These outcomes shape the overall VPN experience during everyday browsing, streaming, and remote work.
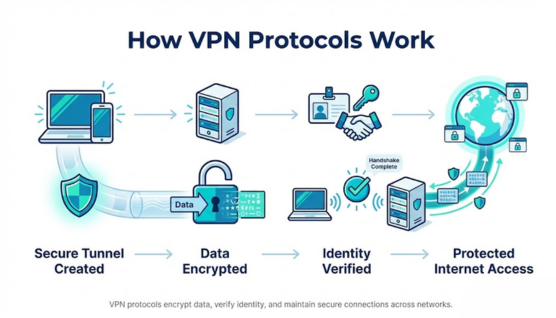
VPN protocols work by establishing a secure connection by creating an encrypted tunnel between a user’s device and a VPN server. All internet traffic passes through this tunnel, keeping data hidden from external networks and intermediaries.
Before transmission, data is encrypted using cryptographic algorithms so readable information becomes scrambled and unreadable. Authentication mechanisms confirm the identity of the device and server, preventing unauthorized access to the connection.
Once the tunnel is active, the protocol manages packet delivery, encryption maintenance, and reconnection during network changes. The efficiency of these processes determines speed, stability, and reliability across Wi-Fi, mobile data, or restricted networks.
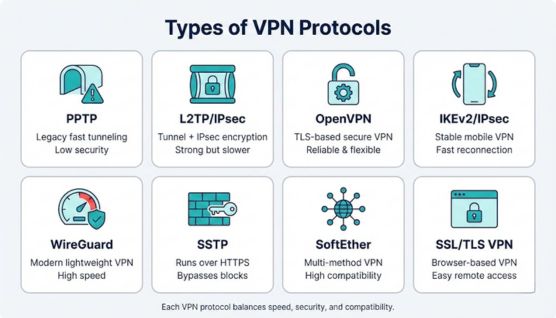
PPTP is a legacy VPN protocol designed for fast tunneling with minimal processing overhead on older systems. PPTP commonly carries traffic using GRE encapsulation and older authentication methods like MS CHAPv2, which do not meet modern privacy expectations.
A PPTP session builds a basic PPP tunnel and then pushes traffic through it with lightweight encryption. Speed stays decent, but weak protection is the defining limitation, especially on hostile networks.
PPTP fits only low risk use where legacy compatibility matters more than confidentiality. Quick setup and low overhead help, but privacy and account safety are the clear compromises.
L2TP IPsec pairs a tunneling layer with IPsec encryption to deliver a stronger baseline than PPTP. L2TP forms the tunnel while IPsec encrypts and authenticates the connection, typically using UDP 500 and UDP 4500 to support NAT friendly connectivity.
Extra encapsulation adds overhead, which can reduce speed on busy links. Some restrictive networks also block IPsec traffic more readily than HTTPS based tunnels.
L2TP IPsec works well for general remote access when built in OS support matters and setup needs to stay straightforward. Solid encryption and wide compatibility are the strengths, while speed loss and blocking risk remain the tradeoffs.
OpenVPN is an open source VPN protocol widely used for privacy and secure remote access across platforms. OpenVPN relies on TLS through OpenSSL for key exchange and encryption, then carries data over UDP for speed or TCP for reliability.
UDP mode often feels faster for streaming and everyday browsing because it avoids extra retransmission overhead. TCP mode can help on unstable links, but performance may drop when loss and congestion trigger repeated retries.
OpenVPN suits users who want a proven option with strong security and flexible configuration on desktops, phones, and routers. Mature tooling and broad support make it dependable, while higher CPU overhead than WireGuard can limit top end speed on weaker devices.
IKEv2 IPsec is a modern VPN option built for stable connections, especially on mobile devices that move between networks. The IKEv2 control channel negotiates keys and maintains the session, and MOBIKE support helps the tunnel survive WiFi to cellular switches with quick reconnection.
IPsec encrypts the data path once the session is established. Some networks still filter IPsec, so reliability can drop in tightly controlled environments.
IKEv2 IPsec is ideal for travel, commuting, and always on mobile protection where fast reconnect matters more than deep customization. Strong security and smooth roaming are the big benefits, while firewall filtering is the main friction point.
WireGuard is a modern VPN protocol built with a small codebase and an emphasis on speed and straightforward security design. WireGuard commonly uses ChaCha20 Poly1305 and a streamlined handshake built around the Noise framework, which keeps overhead low and auditing simpler.
Many implementations run efficiently and can feel snappier than older protocols on phones and routers. Feature sets stay intentionally lean, so advanced enterprise controls may need supporting tooling around the tunnel.
WireGuard fits everyday privacy, streaming, gaming, and mobile use where performance is the priority. Excellent throughput and low latency stand out, while fewer legacy features can be limiting in specialized corporate setups.
SSTP is a VPN protocol that tunnels through TLS and typically uses TCP port 443 to blend with normal HTTPS traffic. That design makes SSTP useful in networks where common VPN ports are blocked by firewalls or deep packet inspection.
A TLS handshake establishes the secure session first, then VPN traffic flows inside the encrypted channel. Windows offers strong native support, but TCP tunneling can slow down on unstable connections because retransmissions add overhead.
SSTP works best for Windows users who need reliable access from restrictive workplaces, campuses, or hotel networks. Firewall compatibility is the win, while platform limits and TCP performance quirks are the main constraints.
SoftEther is a VPN platform that supports multiple VPN methods rather than being a single protocol only. SoftEther can provide an SSL VPN mode and also offer compatibility layers for L2TP IPsec and OpenVPN, which helps mixed device environments.
Administrators can choose the connection method that best matches the user device and network restrictions. Flexibility increases operational complexity, so secure deployment depends on disciplined configuration and access policies.
SoftEther suits corporate environments that need broad compatibility across endpoints and remote access scenarios. Multi method support is the advantage, while admin overhead and configuration discipline are the price of that flexibility.
An SSL TLS VPN provides encrypted remote access using the same TLS security model used by HTTPS. Many deployments use a clientless portal in a browser or a lightweight client, often running over port 443 for high compatibility.
The gateway terminates TLS and then proxies approved applications or creates a limited tunnel depending on configuration. Full device wide tunneling is not guaranteed, so access scope can be narrower than a traditional VPN client.
SSL TLS VPNs are common for business portals, internal web apps, and controlled remote work access. Easy rollout and strong firewall compatibility help, while limited network reach and vendor dependent behavior can be drawbacks.
The right VPN protocol depends on what matters most for your connection, such as security strength, speed, device type, or network conditions.
VPN protocols directly affect security, speed, and connection reliability, making protocol choice a practical decision rather than a technical detail. Modern protocols deliver stronger protection while maintaining performance across common networks.
Legacy options may still offer compatibility, but they no longer meet current privacy expectations. Network type, device behavior, and usage context determine whether a protocol performs well or creates limitations.
Selecting a protocol aligned with real usage keeps connections stable without weakening security. A well-matched protocol ensures consistent protection for browsing, streaming, remote work, and travel.
A VPN is the service that protects your internet connection, while a VPN protocol is the technology that controls encryption, tunneling, and data transfer. The protocol determines how secure and fast the VPN connection behaves.
WireGuard, OpenVPN, and IKEv2/IPsec are considered the most secure options. They use modern encryption and strong authentication methods suitable for current threat models.
WireGuard is usually the fastest due to its lightweight design and low processing overhead. Performance can still vary depending on device hardware and network quality.
PPTP is no longer considered secure due to outdated encryption and known vulnerabilities. It should only be used for legacy compatibility in low-risk situations.
Different protocols perform better under different conditions such as mobile networks, firewalls, or high-speed connections. Offering multiple protocols allows users to adapt to changing environments.
IKEv2/IPsec performs well on mobile devices because it reconnects quickly when networks change. WireGuard also handles mobile usage efficiently.
Yes, protocols influence speed, latency, and packet handling, all of which affect streaming performance. Faster protocols with lower overhead usually provide smoother playback.
No, some networks block VPN traffic at the protocol level. SSTP and SSL-based VPNs often work better because they run over HTTPS traffic.
OpenVPN remains widely used due to its strong security, flexibility, and broad compatibility. It is especially valuable in environments requiring fine-grained control.
Automatic selection works well for most users, but manual changes can help in specific cases like slow speeds or blocked connections. Switching protocols can resolve performance or access issues without changing the VPN service.
