🚀 CloudSEK becomes first Indian origin cybersecurity company to receive investment from US state fund
Read more
Spoofing has been part of the internet’s security landscape since networked systems first began communicating at scale. Early communication protocols such as SMTP and TCP/IP prioritized interoperability and speed, creating an environment where sender authenticity was rarely questioned.
As commercial connectivity expanded in the 1990s, forged IP packets and altered message metadata began appearing in real-world security incidents. What started as technical exploration gradually developed into a structured tactic used to bypass perimeter controls and mislead network defenses.
Rapid digital adoption in the 2000s transformed spoofing into a reliable mechanism for financial fraud and unauthorized access. Its continued presence across enterprise networks and consumer platforms reflects how deeply digital identity is embedded in modern infrastructure.
Spoofing in cyber security is a method of impersonation in which an attacker disguises the origin of digital communication to appear legitimate. Rather than exploiting software vulnerabilities directly, the attacker fabricates source information so systems interpret the interaction as trusted.
Common targets include network-layer identifiers, domain name records, and electronic messaging systems that rely on declared origin details. Altered information may resemble a familiar IP address, recognized domain, or internal system reference.
Such impersonation often acts as a gateway for broader attack strategies, enabling fraud, interception, or service disruption. Clear understanding of this concept provides the foundation for examining how specific spoofing techniques operate in technical environments.
Spoofing works by falsifying the origin details of digital communication so that systems process malicious activity as legitimate traffic.
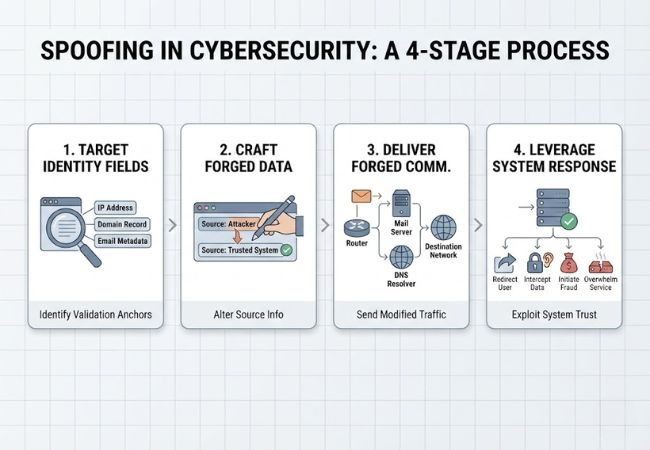
Attackers analyze which identifiers a system relies on for validation, including IP address fields, domain records, or email metadata. These elements act as trust anchors within network and application protocols.
Source information is altered directly within packet headers, DNS responses, or message structures. Precision formatting ensures the manipulated data aligns with protocol specifications and avoids immediate rejection.
Modified traffic moves through standard infrastructure such as routers, mail servers, or DNS resolvers. Normal routing behavior allows the request to reach its destination without raising structural anomalies.
Acceptance of the falsified identity enables further action, whether redirecting users, intercepting communication, initiating fraud, or overwhelming services. Exploitation succeeds not through brute force, but through the convincing presentation of legitimacy.
Spoofing appears in multiple forms depending on which communication layer or identity field is manipulated.
IP spoofing falsifies the source IP address in a network packet so traffic appears to originate from a trusted system. It is commonly used in Distributed Denial-of-Service (DDoS) attacks to hide the attacker’s true location.
CAIDA’s Spoofer data identified spoofing capability in 32 of 424 tested IP blocks in India (7.5%) and 102 of 1,645 tested IP blocks in the United States (6.2%). These figures confirm ongoing exposure at the network infrastructure level.
Email spoofing forges sender address fields so a message appears to come from a legitimate domain or executive account. Business Email Compromise schemes frequently rely on this technique to initiate fraudulent transfers.
The FBI’s IC3 2024 report recorded 21,442 Business Email Compromise complaints with $2.77 billion in reported losses. Financial impact demonstrates the scale of identity-based email fraud.
DNS spoofing, also called cache poisoning, manipulates domain resolution data to redirect users to malicious servers. Victims often remain unaware while interacting with attacker-controlled destinations.
NIST’s NVD listed CVE-2025-40778 with a CVSS score of 8.6, describing a cache-poisoning vulnerability in ISC BIND 9. Such flaws allow forged DNS records to be injected into resolver caches.
ARP spoofing links an attacker’s MAC address to a legitimate IP address within a local network. This enables interception or modification of internal traffic.
A 2025 Scientific Reports paper on the SFARP framework reported 98.3% accuracy with a 2.3% false-alarm rate (FAR) on the CICIoMT2024 dataset, which includes ARP spoofing traffic captured from an IoMT testbed.
Website spoofing creates fraudulent pages that imitate legitimate brands or services. These sites are designed to collect login credentials and payment information.
APWG recorded 892,494 phishing attacks in Q3 2025, including 351,590 unique phishing sites in July. High volume indicates continued effectiveness of cloned web infrastructure.
Caller ID spoofing falsifies phone number data to impersonate trusted institutions. Victims may be pressured into revealing confidential information or transferring funds.
The FTC received over 2.6 million Do Not Call complaints in FY 2025, with more than 258 million active registrations. Persistent complaint levels reflect ongoing telephony identity abuse.
Spoofing creates risk by enabling attackers to gain trust under a false identity before financial, operational, or data damage becomes visible.
Email spoofing and Business Email Compromise schemes manipulate invoices, executive requests, and payment instructions. Caller ID spoofing also pressures victims into fraudulent transfers by impersonating banks or government agencies.
Website spoofing and DNS spoofing redirect users to counterfeit login portals designed to harvest usernames, passwords, and Multi-Factor Authentication codes. Stolen credentials often result in account takeover across enterprise and cloud environments.
IP spoofing frequently supports Distributed Denial-of-Service (DDoS) attacks by masking traffic origin. Overwhelmed servers and degraded infrastructure performance can interrupt business operations.
ARP spoofing within local networks enables Man-in-the-Middle attacks by redirecting internal data flows. Sensitive communications may be monitored or altered without immediate detection.
Identity falsification can provide access to confidential records, intellectual property, and regulated customer information. Breaches triggered through spoofed access points may escalate into broader security incidents.
Spoofed domains, fraudulent emails, or impersonation calls erode customer confidence and brand credibility. Regulatory penalties and compliance violations may follow if identity validation controls are insufficient.
Spoofing differs from related cyber threats because it focuses on falsifying identity signals, while other attacks primarily target human behavior or user interaction.
Detection focuses on identifying inconsistencies in identity signals before attackers escalate their activity.
Email headers often reveal mismatched sender domains, irregular routing paths, or failed authentication checks. Security teams review SPF, DKIM, and DMARC validation results to identify forged sender information.
Network monitoring tools inspect packet behavior for abnormal source patterns or irregular traffic bursts. Sudden surges from inconsistent IP ranges may indicate IP spoofing or DDoS activity.
Unexpected DNS record changes or mismatched resolution responses may signal DNS spoofing attempts. DNSSEC validation and resolver logging help confirm record authenticity.
Frequent MAC-to-IP mapping changes within a local network can indicate ARP spoofing. Intrusion Detection Systems flag repeated unsolicited ARP replies or conflicting address associations.
Login attempts from unusual geographic locations or abnormal device fingerprints may reveal identity manipulation. Multi-factor authentication prompts triggered without user action often indicate credential misuse linked to spoofing.
Security Information and Event Management (SIEM) platforms correlate logs across email servers, DNS resolvers, firewalls, and authentication systems. Cross-referencing anomalies helps identify coordinated spoofing attempts that may not appear suspicious in isolation.
Effective prevention depends on strengthening identity verification across network, email, domain, and user access layers.
Sender Policy Framework (SPF), DomainKeys Identified Mail (DKIM), and Domain-based Message Authentication, Reporting & Conformance (DMARC) validate authorized email servers. Strict DMARC enforcement prevents forged domains from successfully delivering spoofed messages.
Ingress and egress filtering block packets with forged source IP addresses at network boundaries. Properly configured routers reduce exposure to IP spoofing and Distributed Denial-of-Service attacks.
DNS Security Extensions (DNSSEC) cryptographically validate DNS responses to prevent cache poisoning. Secure resolver configurations limit exposure to DNS spoofing and malicious redirection.
Dynamic ARP inspection verifies MAC-to-IP bindings within local networks. Switch-level validation prevents unauthorized address mapping and traffic interception.
Multi-Factor Authentication adds a secondary verification layer beyond passwords. Stolen credentials obtained through website spoofing or phishing campaigns become significantly less useful.
Zero Trust Architecture eliminates implicit trust within internal networks. Continuous authentication and authorization checks prevent spoofed identity signals from automatically granting access.
Spoofing continues to evolve as attackers adapt identity manipulation techniques to cloud infrastructure, artificial intelligence systems, and remote work environments.
Machine learning models now generate highly convincing phishing emails and synthetic communication patterns. Automated spoofing campaigns can mimic writing styles, internal terminology, and executive communication tone with high accuracy.
Advanced audio synthesis technology enables attackers to replicate a person’s voice during phone calls. Caller ID spoofing combined with deepfake voice cloning increases the success rate of financial fraud and executive impersonation scams.
Cloud-based applications rely heavily on API authentication and federated identity systems. Spoofed tokens or manipulated identity assertions can target misconfigured cloud services and SaaS platforms.
Attackers register lookalike domains that closely resemble legitimate brands. Website spoofing combined with HTTPS certificates makes fraudulent portals appear trustworthy to unsuspecting users.
Botnets and automated scripts allow IP spoofing and distributed denial-of-service campaigns to operate at global scale. Large-scale infrastructure increases attack speed, persistence, and evasion capabilities.
Spoofing remains one of the most persistent identity based threats in modern cyber security. Manipulating IP addresses, DNS records, email headers, and caller information allows attackers to exploit trust rather than force entry through technical vulnerabilities.
Growing reliance on cloud services, digital communication, and remote access has made identity validation more critical than ever. Strong authentication controls, DNS protection, network filtering, and Zero Trust Architecture together reduce the likelihood that falsified origin data will be accepted as legitimate.
Long term resilience depends on recognizing that digital identity is a security boundary. Organizations and individuals who strengthen verification mechanisms at every layer significantly lower their exposure to spoofing driven attacks.
Spoofing is a technique used within cyberattacks, but it is not identical to hacking itself. It focuses on impersonating trusted identities rather than directly exploiting software vulnerabilities.
Spoofing does not always require malware installation. Identity manipulation alone can redirect traffic, intercept communication, or trigger fraudulent transactions.
HTTPS encrypts communication between a user and a website. Identity impersonation can still occur if attackers create lookalike domains with valid certificates.
Email spoofing remains one of the most widespread identity based attack methods. Business Email Compromise incidents frequently depend on forged sender domains.
Spoofing attacks affect organizations of all sizes. Smaller businesses often face greater exposure due to weaker email authentication and network monitoring controls.
