🚀 CloudSEK becomes first Indian origin cybersecurity company to receive investment from US state fund
Read more
Modern cyber threats are engineered to resemble legitimate files, emails, and scripts, activating only after evading perimeter controls. This attack pattern succeeds because more than 90% of cyberattacks originate from email-based vectors, while signature-based antivirus fails to detect zero-day and previously unknown malware.
Sandboxing eliminates this visibility gap by executing suspicious files in isolated environments and analysing real runtime behaviour before deployment on production systems. Behaviour-based execution exposes malicious activity, shortens dwell time, and blocks threats prior to operational impact.
Here we examines how sandboxing works, why it is essential for detecting unknown threats, the sandboxing types used in current security operations, practical enterprise use cases, and how sandbox-driven intelligence strengthens early detection and response across security workflows.
Sandboxing is a cybersecurity technique that executes untrusted files or code within a controlled, isolated environment before they reach production systems, enabling direct visibility into runtime behaviour without operational risk. This execution-based approach exposes malicious activity that static inspection fails to detect.
This capability is critical because modern malware actively bypasses signature-based detection. PatentPC research shows that more than 60% of malware samples use evasion techniques such as delayed execution, obfuscation, and environment awareness. Forced execution in a monitored environment neutralises these techniques and reveals behaviours including privilege escalation, command-and-control communication, and payload deployment.
Controlled execution acts as an enforcement decision point. Behavioural evidence determines whether content is allowed, blocked, or contained, improving detection accuracy in environments where nearly one-third of breaches involve malware that initially appears benign.
Sandboxing delivers four core benefits that strengthen threat prevention and operational resilience:
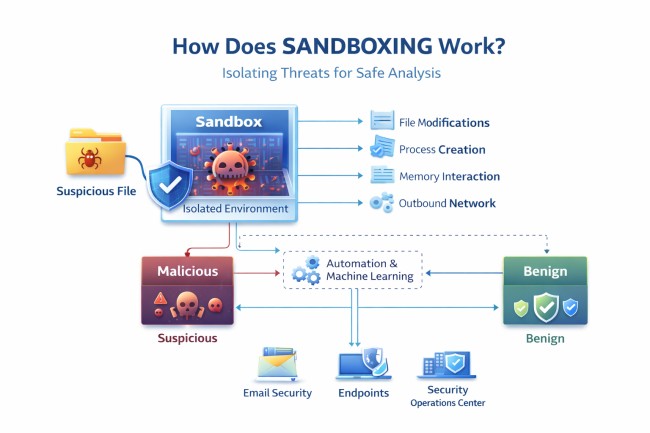
Sandboxing operates by executing suspicious files or code within a controlled environment that replicates a production operating system. The file executes as intended, while all activity remains confined to an isolated execution space.
During execution, the sandbox records behavioural indicators including file modifications, process creation, memory interaction, and outbound network communication. These indicators are analysed to classify behaviour as malicious or benign.
Isolation from production systems and internal networks ensures any harmful activity remains contained. This containment enables security controls to block threats before lateral movement or propagation occurs.
Modern sandbox platforms apply automation and machine learning to produce rapid verdicts and actionable intelligence, supporting real-time decisions across email security, endpoints, and SOC workflows.
A sandbox environment is an isolated, controlled execution space used to run and observe untrusted files, code, or links without affecting live systems.
Sandboxing tests commonly:
By isolating and observing these elements, sandboxing exposes concealed threats that traditional security controls often fail to detect.
Sandboxing types differ by analysis depth, execution realism, and deployment model, each balancing speed, visibility, and operational scale.
Sandboxing is applied across multiple layers of modern cybersecurity architecture to stop threats before they cause damage. It enhances both automated detection systems and manual investigation workflows.
Sandboxing is used by cybersecurity professionals across operational, defensive, and investigative roles to identify threats before they execute in live environments. Each group relies on sandboxing for targeted outcomes.

Industry: Financial Services
Attack Vector: Email attachment (Excel file)
Scenario
A financial services company received a seemingly legitimate Excel attachment as part of routine client communication. The file passed traditional antivirus checks and raised no initial alerts.
Detection
Before delivery, the secure email gateway automatically routed the attachment to a cloud-based sandbox. Within seconds of execution, the file launched PowerShell, modified registry entries, and attempted an outbound connection to a known command-and-control server.
Response
The sandbox generated a malicious verdict in under a minute, triggering automated blocking, alerting the Security Operations Center (SOC), and stopping further distribution across the network.
Outcome
The threat contained pre-execution, with no user interaction, no endpoint compromise, and no downtime. Sandbox telemetry captured the full attack chain and was later used to strengthen internal detection rules against similar threats.
The correlation between sandboxing and threat intelligence lies in signal generation and signal meaning, a relationship central to modern threat intelligence programs. Sandboxing produces high-fidelity behavioral evidence, while threat intelligence interprets that evidence to reveal broader attacker intent and activity.
When sandboxing executes suspicious files in isolation, it captures how a threat behaves, including execution flow, dropped artifacts, command-and-control attempts, persistence mechanisms, and lateral movement indicators. On their own, these observations describe a single event rather than the full threat context.
Threat intelligence adds that missing context by correlating sandbox-derived behaviors across multiple samples, timelines, and environments. This correlation exposes shared infrastructure, reused techniques, and recurring attack patterns, allowing security teams to move from isolated detections to campaign-level understanding and predictive defense, as explained in What Is Threat Intelligence.
