🚀 CloudSEK becomes first Indian origin cybersecurity company to receive investment from US state fund
Read more
A Remote Access Trojan (RAT) is a malware program that covertly grants attackers access to an infected device. It hides within legitimate-looking files, allowing remote operators to work inside the system without alerting the user.
Once active, the RAT connects to an attacker-operated command-and-control (C2) server, allowing the criminal to issue real-time instructions. Through this connection, the attacker gains access to system attributes such as files, credentials, cameras, and network resources.
RATs maintain long-term infiltration by using persistence mechanisms like registry edits, startup entries, or hidden services. Their advanced surveillance capabilities and data-exfiltration functions make them one of the most dangerous malware entities in modern cyberattacks.
A Remote Access Trojan starts working the moment a user opens an infected file or link. Once launched, the malware quietly places its files into the device so it can run without being noticed.
After settling in, it updates system settings so it can start automatically every time the device turns on. This keeps the malware active even if the user restarts or shuts down the computer.
When everything is set, the RAT opens a hidden communication line that lets the attacker interact with the device. Through this connection, the attacker can browse folders, run actions, and make changes as if they were sitting in front of the system.
RATs are dangerous because they enable attackers to operate inside a system quietly while shaping its behavior to support deeper compromise. They are commonly used during the early phases of targeted intrusions, often preceding credential theft or ransomware deployment.
Remote Access Trojans rely on both human error and system weaknesses to enter and operate inside devices.

These entry methods show how quickly a RAT can slip into an environment lacking strong digital hygiene.
RATs contain several built-in capabilities that allow attackers to interact deeply with an infected device.
Attackers can operate the device as though they had physical access. This includes launching applications, modifying system preferences, or installing hidden utilities.
A RAT can reveal files, documents, and stored information to remote operators. This unrestricted access enables targeted data collection.
Attackers can alter core settings, disable protections, or adjust mechanisms that secure the device. These changes weaken the system, making it easier to exploit further.
Once inside, a RAT lets attackers explore other connected devices. This lateral movement increases the reach of the compromise.
Attackers often use RATs to deliver additional malicious components. These may include extortion tools, file wipers, or resource miners.
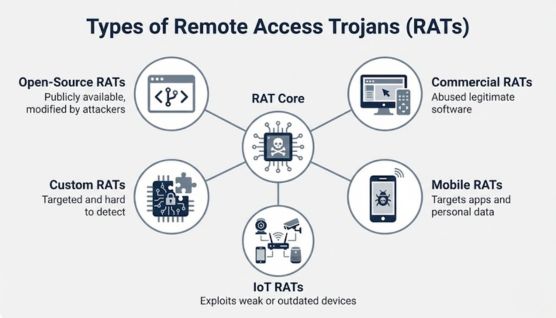
Open-Source RATs are freely available tools modified and reused by attackers. Their accessibility makes them common in widespread campaigns.
Some attackers misuse legitimate remote tools purchased or acquired illegally. These tools offer stability and strong features for long-term misuse.
Threat actors sometimes build tailored RATs for specific targets. These versions are harder to detect because they lack known patterns.
Mobile-focused variants extract app data, messages, and stored files from smartphones. They are often disguised as everyday applications.
IoT RATs target routers, smart cameras, and other connected devices. They rely on weak passwords or outdated firmware to gain access.
Many intrusion campaigns have used DarkComet because of its stability and broad functionality. Attackers appreciate its flexibility during long-term operations.
NanoCore’s modular structure lets operators expand capabilities through plugins. This design makes it effective in business-focused attacks.
njRAT spreads quickly through mass-distribution tactics. Many entry-level attackers rely on it to compromise individuals and small organizations.
PoisonIvy has played a role in several espionage operations. Its robust toolset continues to appeal to threat actors.
Remcos is a commercial tool frequently misused for unauthorized access. Many phishing campaigns rely on it to maintain long-term presence.
Recognizing a RAT infection involves paying attention to device behavior and patterns that do not match regular use.
Sudden slowdowns, unresponsive applications, or random system actions may indicate unauthorized processes. These disruptions often reflect hidden activity.
Unusual outgoing traffic or connections to unfamiliar destinations can reveal malware activity. These network patterns suggest silent communication attempts.
Security tools may flag unknown processes or irregular resource consumption. Behavioral engines help reveal suspicious activity.
System logs may show repeated access failures or unauthorized adjustments. These traces offer valuable insight into hidden interactions.
Preventing RAT infections involves improving habits, strengthening tools, and securing system access points.
Avoid interacting with unknown links or files, especially from unverified sources. Consistent training helps users recognize suspicious messages.
Reputable security software can detect unwanted behavior before it causes severe damage. These tools analyze processes to spot hidden malware.
Firewalls and traffic filters help block unwanted communication attempts. Such controls reduce the risk of remote misuse.
Keeping software updated removes weaknesses that RATs depend on. Regular updates strengthen overall device safety.
Restricting privileges and using strong authentication reduces a RAT’s ability to cause harm. These measures contain the impact of unauthorized access.
Choosing the right solution helps ensure fast detection and efficient response to RAT threats.
Effective tools provide clear insight into unexpected system behavior. Good visibility helps identify early warning signs.
Look for systems that analyze actions instead of only relying on known threat lists. This helps detect new and modified RAT variants.
Monitoring data flow reveals strange patterns created by hidden malware. This enables early identification of suspicious activity.
Instant warnings help security teams respond quickly. Rapid response prevents attackers from completing harmful actions.
Security tools should fit smoothly with existing systems. This unified approach makes overall protection more reliable.
Modern RAT campaigns rely on early infrastructure setup, underground distribution channels, and multi-stage deployment, which makes visibility beyond endpoint data essential.
CloudSEK improves RAT detection by using its XVigil platform to monitor surface, deep, and dark web sources for emerging threats. This broad intelligence collection highlights early indicators of RAT activity.
Its AI and machine learning models analyze OSINT sources, underground forums, Telegram channels, and malware logs to identify active campaigns, including DogeRAT and Arechclient2. This helps organizations see which threats are relevant to them.
The platform maps digital assets to identify weak points vulnerable to RAT misuse and provides real-time alerts when risks appear. Its threat actor tracking and fast takedown support offer a proactive method for reducing RAT-related exposure.
