🚀 CloudSEK becomes first Indian origin cybersecurity company to receive investment from US state fund
Read more
Many major breaches fail not because attackers break encryption, but because they quietly reuse credentials that already exist inside systems. Once a single machine is compromised, stolen credentials often allow attackers to move freely across the network.
One of the most common tools behind this stage of an attack is Mimikatz, which targets how Windows handles authentication after users log in. Its techniques help attackers turn limited access into full control without triggering obvious alarms.
This behavior is part of normal authentication workflows, traditional defenses frequently fail to stop credential reuse. This makes Mimikatz-related techniques a recurring factor in ransomware incidents and internal network compromise.
Mimikatz is an open-source tool used to extract authentication data from Windows systems after a user has logged in. It operates at a stage where credentials are already present in memory as part of normal system operation.
The tool can retrieve plaintext passwords, NTLM hashes, and Kerberos tickets associated with active sessions. These credentials can be reused to access other machines without interacting with login screens or authentication prompts.
Mimikatz remains effective because it relies on standard Windows credential handling rather than exploiting a software vulnerability. As a result, its techniques continue to appear in ransomware attacks and internal network compromises.
Benjamin Delpy released Mimikatz publicly in 2011 to demonstrate how Windows exposes authentication credentials in memory after a system is compromised. The tool was created to highlight design weaknesses in credential handling, not to exploit a specific software vulnerability.
Over time, Mimikatz evolved beyond its original scope and became a reference implementation for credential dumping. U.S. government threat models classify this behavior as OS Credential Dumping (T1003), a technique used to steal passwords and hashes from memory for lateral movement, as documented by CISA.
A joint FBI–CISA advisory updated in June 2025 confirms that ransomware groups, including Play (Playcrypt), actively use Mimikatz to obtain domain administrator credentials during intrusions. The advisory reports approximately 900 affected organizations as of May 2025, underscoring the continued operational relevance of the tool.
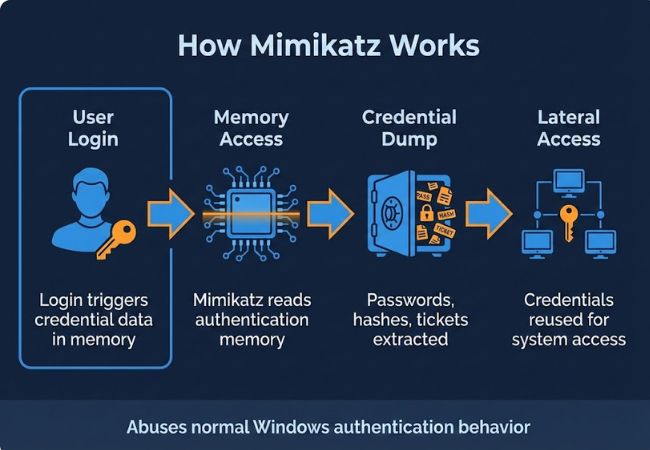
Mimikatz works after a user successfully logs in, when Windows loads authentication data into memory to manage active sessions. This data exists so the operating system can authenticate users and services without repeatedly asking for credentials.
During execution, Mimikatz reads the memory of Windows security processes responsible for authentication and session management. These processes hold credential artifacts such as plaintext passwords, NTLM hashes, and Kerberos tickets tied to logged-in accounts.
The extracted credentials can then be reused to authenticate to other systems as legitimate users. Since this behavior relies on standard Windows authentication workflows rather than exploitation, the technique remains effective across versions and patches.
Mimikatz extracts different forms of authentication data that Windows loads into memory to support active user sessions and service authentication.
In certain configurations, Windows temporarily stores plaintext passwords in memory after a user logs in. Mimikatz can recover these passwords when they are present, allowing direct reuse without additional processing.
NTLM hashes are cryptographic representations of user passwords used for Windows authentication. Mimikatz extracts these hashes from memory, enabling pass-the-hash attacks without revealing the original password.
Kerberos tickets are used to authenticate users and services within Active Directory environments. Mimikatz can dump these tickets from memory, allowing attackers to reuse them to access network resources.
Alongside tickets, Kerberos relies on encryption keys derived from user credentials. Mimikatz can extract these keys, which can be used to request new tickets or impersonate users within a domain.
Windows stores cached domain credentials to allow logins when a domain controller is unavailable. Mimikatz can retrieve these cached credentials, extending access even in disconnected or segmented environments.
Mimikatz is used almost exclusively to enable credential theft and reuse techniques that allow attackers to authenticate as legitimate users after a system is compromised.
Mimikatz blends into normal Windows authentication activity, making malicious behavior difficult to separate from legitimate system operations.
Credential access occurs through Windows security processes that routinely handle authentication tasks. Activity originating from these processes often appears expected in enterprise environments.
Most operations occur directly in system memory rather than through executable files written to disk. Reduced disk interaction limits visibility for controls focused on file scanning.
Extracted credentials are already trusted by the operating system and associated services. Authentication attempts using these credentials appear legitimate to access control mechanisms.
Attackers regularly modify or recompile Mimikatz to avoid static detection. Signature-based defenses struggle to maintain coverage as variants change.
Security administrators perform actions that closely resemble credential access and inspection. Behavioral overlap complicates reliable differentiation between authorized and malicious use.
Reducing the impact of Mimikatz requires limiting credential exposure, restricting privilege, and monitoring authentication behavior across endpoints and domains.
Protect sensitive authentication material by enabling features that isolate credentials from user-mode access. Controls such as protected LSASS and modern credential protection reduce what can be read from memory.
Limit administrative access and reduce where high-privilege accounts can sign in. Fewer privileged sessions mean fewer valuable credentials loaded into memory.
Disable legacy authentication mechanisms and enforce stronger protocols across the environment. Consistent use of modern authentication reduces opportunities for credential reuse.
Monitor access to authentication-related processes and memory with behavior-based detection. Alerts tied to abnormal process access provide visibility into credential dumping attempts.
Separate systems and restrict lateral movement paths through network and identity segmentation. Segmentation limits how far stolen credentials can be reused.
The legality of Mimikatz depends entirely on authorization, purpose, and the environment in which it is used.
Use is generally permitted on systems owned by the user or where explicit permission has been granted. Penetration tests, red-team exercises, and internal security assessments fall into this category.
Running Mimikatz on systems without permission constitutes unauthorized access in most jurisdictions. Extracting credentials from third-party systems can violate computer misuse and cybercrime laws.
Security researchers may study or test Mimikatz in controlled lab environments. Such use focuses on understanding credential exposure rather than accessing live production systems.
Many organizations restrict the use of credential-dumping tools regardless of intent. Internal policies often require approvals, logging, and scope limitations before any use.
Legitimate use of Mimikatz occurs in controlled scenarios where credential exposure needs to be assessed, validated, or demonstrated with proper authorization.
Authorized penetration tests use Mimikatz to confirm whether credentials can be extracted after compromise. Findings help organizations understand real post-exploitation risk rather than theoretical exposure.
Red team exercises apply Mimikatz to simulate attacker behavior during lateral movement and privilege escalation. Results measure detection capability and response readiness under realistic conditions.
Security assessments use credential dumping to evaluate configuration weaknesses in authentication and privilege management. Evidence gathered supports remediation of high-risk access paths.
Isolated lab environments use Mimikatz for education and skill development. Hands-on testing builds familiarity with credential theft mechanics without touching production systems.
During investigations, controlled execution may validate whether credential dumping occurred on affected hosts. Confirmation helps scope compromise and prioritize credential resets.
Mimikatz highlights a fundamental security challenge: credentials remain one of the most valuable assets inside Windows environments after compromise. Its continued use shows that many attacks succeed by reusing trusted authentication data rather than exploiting new vulnerabilities.
Reducing risk depends on limiting credential exposure, controlling privilege, and detecting abnormal authentication behavior early. Addressing these areas lowers the impact of Mimikatz-style techniques and strengthens overall post-compromise resilience.
