🚀 CloudSEK becomes first Indian origin cybersecurity company to receive investment from US state fund
Read more
Modern networks no longer fail at the perimeter. Failures occur at the application layer where users authenticate, transactions execute, and attacks succeed. As organisations depend on web applications, APIs, and cloud services, Layer 7 has become the primary control point for security, availability, and performance.
This guide defines Layer 7 (the Application Layer) and explains its operational importance in modern networking and cybersecurity. It explains how Layer 7 operates within the OSI model, the protocols and applications it supports, and how it differs from lower layers. The guide examines Layer 7 attack mechanics, application-layer DDoS activity, security challenges, and the need for application-aware controls to protect availability, performance, and user experience.
Layer 7 is the application layer of the OSI model that enables end-user applications to communicate by interpreting and managing application-level requests and data. Operating closest to the user, this layer governs how applications request, structure, and deliver information between clients and servers.
Application-layer protocols operate at Layer 7. Protocols include HTTP, HTTPS, DNS, SMTP, APIs. These protocols enable web access, email exchange, authentication, and transactional workflows. Unlike lower layers that transport packets, Layer 7 interprets application logic and user intent.
As organisational reliance on web applications and APIs increases, Layer 7 has become the dominant attack surface. Gartner reports over 75% of information-security attacks target web applications that expose internet-facing application-layer interfaces. This concentration makes Layer 7 the most targeted OSI layer, where compromise results in service disruption, performance degradation, or data exposure.
Layer 7 is critical because it is the top OSI layer where application protocols are interpreted, making it the point where user interaction, application logic, performance, and security converge.
Layer 7 gives meaning to network communication by interpreting application-specific requests and responses. It governs content delivery, session handling, and transaction flows for web apps, APIs, email, and SaaS. Without Layer 7 processing, networks move data but applications fail to function reliably.
Most modern attacks target application behaviour rather than bandwidth. Application-layer DDoS, API abuse, credential stuffing, and bot traffic operate at Layer 7 and often bypass lower-layer controls. Industry reporting consistently shows a majority of incidents now involve application-layer vectors, directly impacting uptime and user experience.
The OSI (Open Systems Interconnection) model is a conceptual framework that standardises how network communication functions by dividing it into seven distinct layers, from physical transmission to user-facing applications.
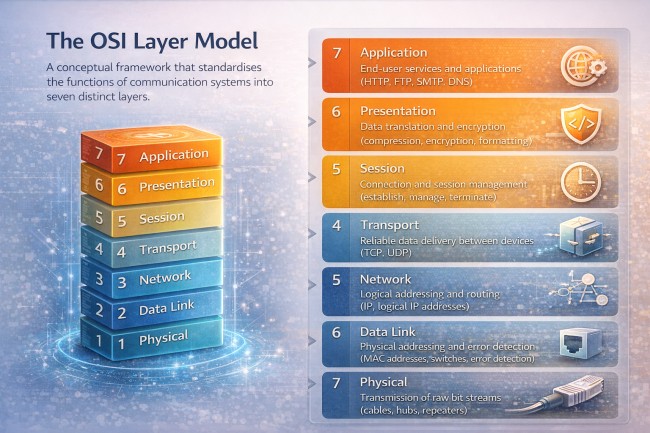
Each layer performs a specific role and builds on the layer below it, enabling interoperability, troubleshooting, and clear separation of networking responsibilities.
The physical layer handles the transmission of raw data bits over physical media. It defines hardware elements such as cables, connectors, signals, and electrical or optical specifications.
The data link layer manages node-to-node data transfer within the same network. It handles framing, MAC addressing, error detection, and controls how devices access the physical medium.
The network layer is responsible for routing data between different networks. It manages logical addressing (IP addresses) and determines the best path for data packets to reach their destination.
The transport layer ensures reliable or fast delivery of data between systems. It manages segmentation, flow control, error recovery, and session reliability using protocols such as TCP and UDP.
The session layer establishes, manages, and terminates communication sessions between applications. It controls session checkpoints, recovery, and dialogue coordination.
The presentation layer formats, encrypts, and compresses data so it can be correctly interpreted by applications. It ensures data representation, character encoding, and encryption consistency.
The application layer enables end-user interaction with network services. It supports application protocols such as HTTP, HTTPS, DNS, and SMTP, allowing users and applications to request and exchange data.
Together, the OSI model provides a structured view of how data moves from physical transmission to application-level interaction, forming the foundation for understanding networking, performance, and security across all layers.
Layer 7 enables applications to communicate by interpreting, managing, and deciding how to respond to application-level requests and data. It processes web page calls, API requests, email commands, and DNS queries by understanding request structure and intent.
According to Imperva’s 2023 DDoS Threat Landscape Report, over 70% of DDoS attacks target the application layer (Layer 7), reflecting the rise of low-volume attacks that mimic legitimate traffic.
The application layer governs how content is formatted, exchanged, and presented. It manages sessions, application state, and request handling, directly influencing backend resource consumption, where even small increases in Layer 7 traffic can disproportionately affect CPU and database performance.
Layer 7 applies protocol-specific rules for services such as HTTP, HTTPS, DNS, and SMTP. Because most business transactions rely on HTTP-based protocols, the majority of user interactions are governed at this layer.
Authentication, authorisation, and transaction handling occur at Layer 7, where credential abuse and bot-driven login attempts commonly operate. By interpreting intent and enforcing application logic, Layer 7 converts network traffic into controlled application behaviour, shaping performance, availability, and application-aware security.
Layer 7 supports the protocols and applications that enable user-facing network communication and application services. These protocols define how data is requested, exchanged, and interpreted at the application level.
Protocols such as HTTP and HTTPS enable web browsing, web applications, and API communication. They define how clients request content and how servers respond, forming the foundation of most internet-based services.
Protocols including SMTP, POP3, and IMAP support email transmission and retrieval. Layer 7 governs how messages are sent, received, stored, and accessed by users and mail servers.
Layer 7 supports file transfer mechanisms and application programming interfaces (APIs) that allow systems to exchange data and functionality. These interactions are critical for integrations, microservices, and modern application architectures.
Protocols such as DNS operate at Layer 7 to translate human-readable domain names into IP addresses, enabling applications to locate and communicate with network resources.
Cloud applications, SaaS platforms, and browser-based services rely heavily on Layer 7 to manage sessions, authentication, data exchange, and user interactions across distributed environments.
Together, these protocols and applications illustrate how Layer 7 enables meaningful communication between users and services, making it central to modern networking and application security.
Layer 7 plays a critical role in network security by providing application-aware visibility, inspection, and control that lower OSI layers cannot offer.
Layer 7 security analyses application-level requests and responses to understand user actions and intent. This makes it possible to detect threats hidden within legitimate-looking traffic, including malicious HTTP requests, API abuse, and automated bot activity. Cloudflare reports indicate that 71% of modern web attacks target application-layer vulnerabilities, underscoring the importance of Layer 7 visibility.
At this layer, security systems inspect request headers, payloads, URLs, and parameters. This deep inspection enables detection of common application-layer attacks such as SQL injection, cross-site scripting (XSS), and command injection—threats that continue to rank among the top OWASP web application risks and frequently bypass network-layer defences.
Layer 7 security also evaluates behavioural patterns rather than relying solely on traffic volume or source. This helps distinguish legitimate users from automation. Studies show that 40–50% of web traffic is bot-generated, much of it associated with scraping, credential abuse, and application-layer denial-of-service attacks that degrade availability.
Security policies are enforced at the application level based on request type, user role, and transaction context. Controls such as rate limiting, request validation, and access enforcement reduce abuse while preserving user experience.
By enabling intent-aware inspection and control, Layer 7 security protects applications from both compromise and disruption, maintaining availability and performance where lower-layer defences fall short.
Layer 7 DDoS attacks disrupt applications by exhausting application logic and backend resources rather than network bandwidth, directly impacting service availability.
These attacks target resources such as CPU, memory, threads, and database connections by sending requests that trigger expensive application operations. Traffic is crafted to mimic legitimate user behaviour—such as repeated HTTP requests, API calls, or login attempts—making detection difficult.
Unlike volumetric attacks, Layer 7 DDoS attacks often use low traffic volumes. A sustained flow of well-formed requests can significantly slow applications or cause outages by repeatedly invoking resource-intensive functions. Attackers commonly exploit application logic related to authentication, search, sessions, or dynamic content and adapt their methods over time to maintain pressure.
Because the traffic follows valid application protocols, traditional network-layer defences focused on rate or packet patterns often fail. Effective mitigation requires application-aware inspection and behavioural analysis to preserve availability and user experience.
One-line takeaway:Layer 7 security understands what the traffic is doing, while network-layer security focuses on how traffic moves—both are required for complete protection.
Layer 7 security presents critical challenges because it requires accurate interpretation of complex application behaviour at scale without disrupting availability or user experience. According to Imperva’s 2023 DDoS Threat Landscape Report, Application layer DDoS attacks increased by 82% year-on-year and around 46% of websites that came under DDoS attack were attacked again.
Most application traffic is encrypted, limiting direct inspection of requests and payloads. Gaining visibility while preserving privacy, compliance, and performance remains a core challenge for effective Layer 7 security.
Layer 7 attacks often closely resemble normal user behaviour. Accurately separating human users from automated abuse requires advanced behavioural analysis and context. Inaccurate detection increases false positives and risks blocking legitimate traffic.
Application behaviour varies widely across users and use cases. Maintaining detection accuracy without misclassifying valid requests as malicious requires continuous tuning. Poor accuracy directly impacts user experience and business operations.
Layer 7 security controls demand ongoing management. Application changes, new APIs, and evolving attack patterns require frequent policy updates, rule adjustments, and monitoring, increasing operational overhead for security teams.
Addressing these challenges requires intent-aware analysis, adaptive controls, automation, and close alignment between security and application teams to maintain protection without disrupting business-critical services.
Modern applications rely on APIs, microservices, SaaS platforms, and cloud-native architectures, all of which operate primarily at Layer 7. As application complexity increases, security and performance visibility at the application layer becomes essential for understanding behaviour, exposure, and risk.
This visibility connects Layer 7 security with broader topics such as API security, bot management, zero trust, and application performance monitoring, forming a foundation for deeper exploration in future articles.
