🚀 CloudSEK becomes first Indian origin cybersecurity company to receive investment from US state fund
Read more
Internet of Medical Things (IoMT) Security is the protection of connected medical devices and the clinical data they exchange. It ensures these devices cannot be accessed, altered, or disrupted by cyber threats.
IoMT security keeps patient information private and preserves the integrity of every device involved in diagnosis, monitoring, and treatment. It creates a safe environment where medical teams can rely on accurate data and uninterrupted device performance.
Modern hospitals depend on thousands of devices communicating across networks, cloud platforms, and wireless channels. IoMT security supports this ecosystem by maintaining trust, stability, and safety across all points of care.
IoMT spans everything from home wearables to high-end diagnostic equipment, each carrying different cybersecurity expectations.
Wearables include ECG patches, glucose monitors, smartwatches, and RPM sensors. They rely on Bluetooth, Wi-Fi, and mobile apps, which makes secure cloud APIs and authentication essential.
Infusion pumps, ventilators, anesthesia machines, and cardiac monitors connect through HL7 v2 or proprietary protocols. They often run continuously in ICUs and med-surg units, limiting downtime for updates.
MRI, CT, ultrasound, and X-ray systems depend on DICOM and integrate with PACS and RIS. Because they generate massive image payloads, encrypted transport and segmentation are crucial.
Pacemakers, neurostimulators, and insulin pumps communicate via RF or NFC. Their limited patchability and long design life make them some of the highest-risk IoMT assets.
Clinical OT includes lab analyzers, robotic surgery systems, and medication-dispensing cabinets. Many operate on Windows CE, VxWorks, or other legacy platforms that lack modern security controls.
IoMT devices directly influence clinical decisions, making their security essential for safe patient care.
An attacker manipulating a pacemaker’s telemetry or infusion pump dosage can cause real physical danger. Even subtle data tampering can lead clinicians to take incorrect actions during treatment.
Compromised PACS servers can delay radiology workflows across an entire ER. ICU monitors experiencing wireless packet loss can cause false alarms or missed alerts during critical care.
IoMT devices handle PHI regulated under HIPAA, state privacy rules, and FDA cybersecurity expectations. Breaches often trigger costly investigations, fines, or operational shutdowns.
Attackers frequently pivot from a single weak IoMT device into high-value systems like EHR servers. Flat VLAN architectures and unsegmented clinical devices increase this risk dramatically.
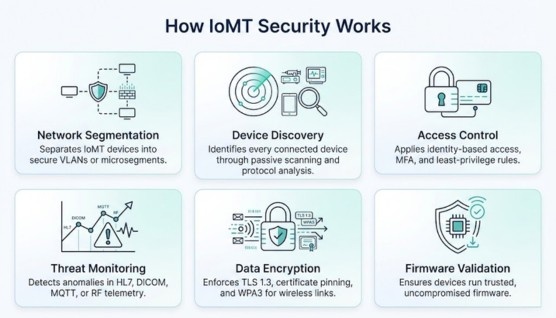
IoMT security brings together device-level protections, secure communication, and network policies.
Attackers exploit outdated software, weak wireless signals, misconfigured networks, and insufficient authentication.
Legacy firmware on infusion pumps or imaging consoles allows attackers to execute malicious code. Many devices cannot be patched, making them persistent entry points.
RF interception, Bluetooth replay, and Wi-Fi downgrades expose wearable and implantable devices. Weak or outdated encryption increases these risks significantly.
Unsegmented devices let attackers pivot into PACS, EHR, or administrative systems using SMB, RDP, or HL7 vulnerabilities. This significantly expands the blast radius of an attack.
Attackers clone device IDs to impersonate monitors or pumps, enabling man-in-the-middle attacks. This can feed false vitals or disrupt clinical dashboards.
Targeting devices tied to imaging, laboratory, or surgical workflows creates widespread operational paralysis. Even unencrypted downtime can delay diagnostics and care delivery.
Attackers use device cloning, RF replay, downlink command manipulation, and cryptographic downgrade techniques to compromise IoMT devices ranging from cardiac wearables to implantables.
They also deploy AI-augmented malware that targets device firmware and evades SOC detection to gain deeper control over clinical systems.
Healthcare has unique operational constraints that make traditional security approaches impractical.
Devices often remain in use for decades, outlasting vendor support. Older platforms like Windows CE and VxWorks lack patches for emerging threats.
Hospitals may run 10,000+ devices, many discovered only when incidents occur. Without full inventory, segmentation and monitoring become incomplete.
Critical devices cannot be rebooted during patient care. Security fixes must align with uninterrupted ICU and OR operations.
Manufacturers ship devices with inconsistent authentication, encryption, and update practices. This complicates unified policies across departments.
HL7 v2, DICOM, CoAP, and other older standards were not built for modern security. This leaves gaps in message integrity and session authentication.
AI-driven diagnostics and monitoring introduce a new layer of exposure, especially when IoMT devices feed clinical models.
Attackers manipulate vitals or sensor data to skew machine-learning predictions. A poisoned AI sepsis model may delay lifesaving intervention.
Altering training data or inference pathways can push diagnostic systems toward inaccurate classifications. This impacts radiology AI tools that rely on PACS images.
Slow, subtle IoMT data tampering can cause AI predictions to drift over time. Clinicians may notice inconsistencies too late.
If PACS or EHR systems storing training datasets are compromised, the resulting AI models inherit silent vulnerabilities.
Hospitals increasingly rely on cloud-connected and edge-processing devices, expanding the attack surface.
Compromised cloud admin keys can expose entire IoMT fleets. Least-privilege identity access and key rotation reduce these risks.
FHIR APIs allow seamless interoperability but require strong TLS 1.3 enforcement and token validation. Poor API security creates large-scale PHI disclosure risk.
Edge devices bridging IoMT and cloud networks can be exploited if not properly hardened. Attackers may manipulate MQTT or CoAP traffic flowing through them.
Unencrypted or weakly signed telemetry can be intercepted or altered in transit. Certificate pinning and zero-trust service authentication prevent misuse.
Zero Trust adapts well to IoMT environments because devices cannot be implicitly trusted.
Every device, infusion pump, MRI console, wearable needs a cryptographic identity. Authentication replaces traditional IP-based trust models.
Zero Trust microsegments restrict device-to-device communication, preventing lateral movement. Even compromised devices stay contained.
Clinicians get temporary, role-based access to configure devices. This minimizes persistent privileges that attackers can hijack.
Device posture scoring evaluates firmware, certificates, and behavior in real time. Access is continuously revalidated to reflect current risk levels.
Healthcare cybersecurity is governed by international standards, federal mandates, and manufacturer requirements.
Requires administrative, physical, and technical safeguards for PHI. IoMT devices must meet strict encryption, logging, and access obligations. Know more about HIPAA.
FDA pre-market and post-market guidance requires SBOMs, secure development, patch processes, and vulnerability disclosure.
FDA RTA 2023 enforces cybersecurity completeness before market approval.
Provides a structured approach for identifying, protecting, detecting, responding, and recovering. Useful for hospital cybersecurity maturity. Know more about NIST CSF.
Hospitals can strengthen their security posture through structured short-term and long-term efforts.
Manufacturers play a decisive role in securing IoMT throughout the device lifecycle.
Encrypted communications, authenticated commands, and hardened firmware reduce vulnerabilities from day one.
Consistent patch schedules protect devices from emerging threats. Clear vendor SLAs help hospitals plan maintenance safely.
Coordinated vulnerability disclosure accelerates risk mitigation. The FDA and EU MDR expect manufacturers to provide transparent, timely updates.
A strong incident response workflow protects patient care while containing threats. It ensures that every action taken supports clinical safety and restores device integrity.
Identify which IoMT devices are affected and determine the level of patient impact based on clinical dependency. Prioritize life-support and high-risk systems first to prevent delays in urgent care.
Use microsegmentation or controlled physical disconnects to contain compromised devices without interrupting essential workflows. This prevents attackers from moving laterally into PACS, EHR, or other critical systems.
Analyze HL7 logs, DICOM imaging flows, and device telemetry to understand how the compromise occurred. This helps teams pinpoint root causes and detect whether additional systems were affected.
Apply patches, restore firmware, or replace unsafe devices to remove the threat and return equipment to trusted operation. Verify each device’s configuration and security posture before reconnecting it to clinical networks.
Notify clinical leaders, compliance teams, manufacturers, and regulators to ensure coordinated response and reporting. Clear communication keeps patient care teams informed and meets regulatory requirements such as HIPAA or FDA post-market expectations.
IoMT security strengthens the hospital’s cybersecurity foundation by reducing exposure across clinical and IT environments. It ensures that medical devices no longer act as weak entry points into critical systems.
Segmented IoMT devices stop attackers from moving into EHR, PACS, and administrative networks. This reduces the blast radius of any breach and protects high-value clinical workflows.
IoMT telemetry gives SOC and SIEM platforms deeper insight into device behavior and unusual activity. These signals improve alert accuracy and help analysts detect threats earlier.
Securing IoMT environments minimizes device outages and keeps clinical operations running smoothly. This reduces downtime across departments and supports continuous patient care.
A strong IoMT security solution offers visibility, integration, and device-level protection across complex hospital networks. It should enhance clinical safety while simplifying security operations.
Continuous device discovery and classification ensure teams know exactly what is connected at all times. This removes blind spots and enables better segmentation.
Support for SIEM, SOAR, EDR, firewalls, and Zero Trust systems creates a unified security ecosystem. This allows IoMT data to flow directly into existing monitoring and response workflows.
Automated integrity checks detect tampered or outdated firmware before it becomes a threat. Patch management workflows help teams maintain devices without disrupting patient care.
Built-in reporting aligned with HIPAA, NIST CSF, FDA, IEC, and EU MDR simplifies audits. These tools help hospitals demonstrate adherence to regulatory requirements.
A scalable platform supports thousands of devices across multi-site hospitals. This ensures security coverage grows as the IoMT environment expands.
Yes. Most IoMT devices run outdated software and can’t be patched frequently.
It’s possible but extremely rare. Strong encryption and access controls reduce the risk.
Hospitals often lack a full inventory of connected devices. Unseen devices create blind spots.
No. Modern IoMT solutions use passive monitoring that does not interfere with patient care.
No. HIPAA only protects PHI; technical device security requires FDA, NIST, and IEC controls.
Yes. Zero Trust reduces lateral movement and verifies device identity at all times.
As soon as vendors release updates, if clinically safe. Unpatchable devices must be segmented.
It shows the software components inside a device, helping teams find vulnerabilities quickly.
IoMT security has become essential as hospitals rely on thousands of connected devices that support critical patient care. Protecting these devices ensures safe treatment, stable operations, and trustworthy clinical data across the entire healthcare system.
Stronger visibility, better segmentation, and modern security practices allow healthcare teams to manage growing cyber risks without disrupting care. As IoMT ecosystems expand, consistent security governance will remain the key to resilience and patient safety.
