🚀 CloudSEK becomes first Indian origin cybersecurity company to receive investment from US state fund
Read more
As organisations increasingly rely on digital information to operate, comply, and compete, protecting that information requires more than isolated security controls. Information security risks now span people, processes, technology, and third-party ecosystems, making a structured and auditable approach essential.
This article explains what an Information Security Management System (ISMS) is and why organisations implement it as a core part of information security governance. It explores the purpose and structure of an ISMS, its key components, and the role of risk management in protecting information assets. The article also examines best practices for ISMS implementation, how ISO 27001 relates to and strengthens an ISMS, and why continuous improvement is critical for sustaining compliance, security maturity, and organisational trust over time.
An ISMS is a formal, structured framework used to design, implement, operate, monitor, and continuously improve information security within an organisation.
The system provides a consistent and documented approach to managing information security risks. It ensures protection efforts are repeatable, measurable, and aligned with business objectives rather than dependent on ad hoc controls.
Information security management defines what must be protected and why. An ISMS defines how protection is implemented, maintained, and improved through documented policies, controls, and governance mechanisms.
An ISMS formalises security through:
This structure supports accountability, audit readiness, and regulatory compliance.
An ISMS operates as a continuous cycle. Risks are reassessed, controls are reviewed, and improvements are made based on incidents, audits, and organisational change. This ensures protection remains effective as threats, technologies, and business needs evolve.
Together, these elements allow an ISMS to translate security intent into sustained, organisation-wide practice.
An ISMS is composed of structured components that work together to manage information security risks in a consistent, auditable, and repeatable manner.
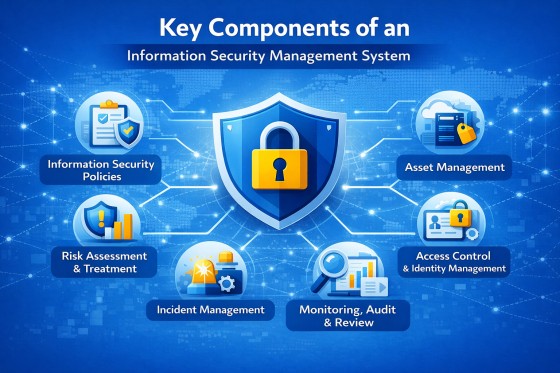
Policies define the organisation’s security objectives, principles, and expectations. They establish management intent and provide direction for how information must be protected across the business.
Risk assessment identifies threats, vulnerabilities, and potential impact to information. Risk treatment defines how risks are mitigated, accepted, transferred, or avoided through appropriate controls.
Information assets are identified, classified, and assigned ownership. Asset management ensures protection efforts are proportional to the value and sensitivity of information.
Controls ensure that only authorised users and systems can access information. This includes user provisioning, authentication, authorisation, and periodic access reviews.
Processes are defined to detect, report, respond to, and recover from information security incidents. Incident management limits impact and supports rapid restoration of normal operations.
Controls and processes are continuously monitored and periodically audited. Reviews assess effectiveness, identify gaps, and provide evidence for compliance and improvement.
Together, these components ensure the ISMS operates as a living system that maintains protection, supports accountability, and adapts to organisational and risk changes over time.
Implementing an ISMS requires a structured, risk-based approach that aligns information security with business objectives and operates as a continuous program.
Senior management defines the ISMS direction, approves policies, and assigns clear ownership. Leadership involvement ensures authority, resources, and accountability across the organisation.
The scope identifies which information, systems, processes, and locations are covered. Alignment with business objectives and risk appetite ensures the ISMS remains practical and relevant.
Controls are selected based on assessed risks rather than generic checklists. This approach ensures resources focus on protecting the most critical information assets.
Clear documentation defines how security is implemented and maintained. Consistent records support repeatability, accountability, and audit readiness.
The ISMS is embedded into existing business and IT workflows, such as change management, procurement, and incident response, to avoid operational friction.
Metrics, reviews, and internal audits are used to evaluate whether controls function as intended and achieve defined objectives.
Regular reviews assess performance, address gaps, and confirm continued suitability. Audits provide independent assurance and improvement input.
Findings from incidents, audits, and changes in risk drive ongoing enhancement. Continuous improvement ensures the ISMS evolves with threats, technology, and organisational change.
These practices ensure the ISMS remains effective, auditable, and aligned with business needs over time.
Organisations implement an ISMS to manage information security risk in a structured, auditable, and business-aligned manner.
An ISMS provides a consistent framework to identify, assess, and treat information security risks based on business impact. This ensures controls are proportionate, documented, and focused on protecting critical information assets.
Many regulations require formal governance, documented controls, and ongoing risk management. An ISMS helps organisations meet data protection, privacy, and industry obligations in a systematic and defensible way.
By standardising policies, evidence, and review processes, an ISMS enables organisations to demonstrate control effectiveness during internal audits, external assessments, and certifications such as ISO 27001.
An ISMS supports the availability and integrity of information during disruptions while reinforcing confidence among customers, partners, regulators, and stakeholders through consistent and accountable security practices.
Risk management is the core mechanism through which an ISMS identifies, evaluates, treats, and monitors threats to information, ensuring controls remain aligned with organisational risk tolerance and business impact.
Risk management within an ISMS begins with risk identification and analysis, where potential threats, vulnerabilities, and impacts are systematically catalogued.
Statistical evidence underscores the importance of a structured risk management approach. Around 80 % of organisations reported a significant increase in security incidents over the past year, yet fewer than half felt adequately prepared to manage emerging threats, highlighting widespread risk exposure and the need for formal risk processes.
Once risks are understood, they are prioritised based on impact and likelihood, enabling risk treatment decisions such as mitigation, transfer, acceptance, or avoidance. Effective risk treatment ensures that security efforts focus on risks that could most severely compromise information confidentiality, integrity, or availability.
Continuous monitoring and review are essential, as risk profiles evolve with new threats, technologies, and business changes. A strong risk management process helps organisations adapt their ISMS over time, maintain compliance with regulatory requirements, and make informed decisions that balance security with operational needs.
ISO 27001 is the internationally recognised standard that defines the requirements for establishing, implementing, maintaining, and continually improving an Information Security Management System (ISMS).
ISO 27001 provides a consistent, auditable framework that organisations use to demonstrate a structured and measurable approach to information security. Certification to ISO 27001 is globally recognised and often expected by customers, partners, and regulators as proof of effective information risk management.
An ISMS aligned with ISO 27001:
Organisations certified to ISO 27001 gain measurable benefits:
An ISMS built around ISO 27001 ensures that information security is not an ad hoc activity but part of a disciplined, measured, and continuously improving management system that organisations can benchmark, certify, and govern with confidence.
An Information Security Management System is not a one-time implementation but a continuous improvement journey.
As business operations, technologies, regulatory expectations, and threat landscapes evolve, the ISMS must be regularly reviewed and adjusted. Ongoing risk assessments, internal audits, management reviews, and corrective actions ensure controls remain effective and aligned with organisational objectives.
Treating the ISMS as a living system helps organisations maintain compliance, improve security maturity, and sustain long-term resilience and stakeholder trust.
