🚀 CloudSEK becomes first Indian origin cybersecurity company to receive investment from US state fund
Read more
Key Takeaways:
Endpoint Detection and Response (EDR) is a category of endpoint security used to manage security incidents on endpoint devices such as laptops, servers, and workstations. EDR is applied when suspicious or malicious activity must be investigated and controlled, rather than simply blocked.
The primary role of EDR is to give security teams centralized visibility and control over endpoint-related incidents. This capability turns endpoint security into an active process focused on investigation, response, and recovery.
EDR exists to help organizations limit the impact of endpoint attacks by improving how incidents are detected, analyzed, and handled once they occur.
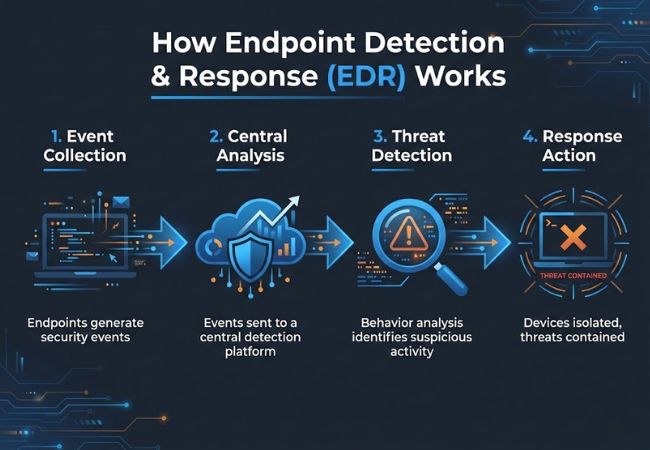
Endpoint Detection and Response works by collecting security event data generated by endpoint operating systems, applications, and user activity. These events are sent to a centralized platform where they can be reviewed and investigated together.
Analytical systems examine how events relate to one another over time to determine whether activity represents a security incident. Context from historical activity and known threat patterns helps separate normal behavior from malicious behavior.
Response actions are executed directly on affected endpoints to contain or remove threats. Common actions include isolating devices, stopping malicious processes, and preserving evidence for investigation.
An Endpoint Detection and Response solution is composed of multiple system components that collectively support endpoint visibility, investigation, and response.
Endpoint agents are installed on endpoint devices to collect security-relevant events generated by the operating system and applications. Collected data includes process activity, file operations, memory usage, and network behavior.
Data collection mechanisms ensure endpoint events are captured consistently and transmitted for centralized analysis. Reliable data flow is essential for maintaining visibility across all protected endpoints.
The management console provides a centralized interface for viewing alerts, conducting investigations, and managing response actions. Security teams rely on this interface to analyze incidents across multiple endpoints.
The detection engine evaluates endpoint data to identify activity associated with potential security incidents. Detection logic relies on behavioral indicators rather than static signatures.
Analytics engines correlate events over time to provide context and reduce false positives. Analytical processing helps security teams understand attack patterns and incident scope.
Threat intelligence components enrich endpoint data with known indicators, attacker techniques, and contextual metadata. Enrichment improves confidence in detections and prioritization of incidents.
Response controls enable direct action on affected endpoints to contain or remediate threats. Actions may include device isolation, process termination, artifact removal, and evidence preservation.
Endpoint Detection and Response is designed to surface malicious activity on endpoints that traditional prevention tools often fail to identify.
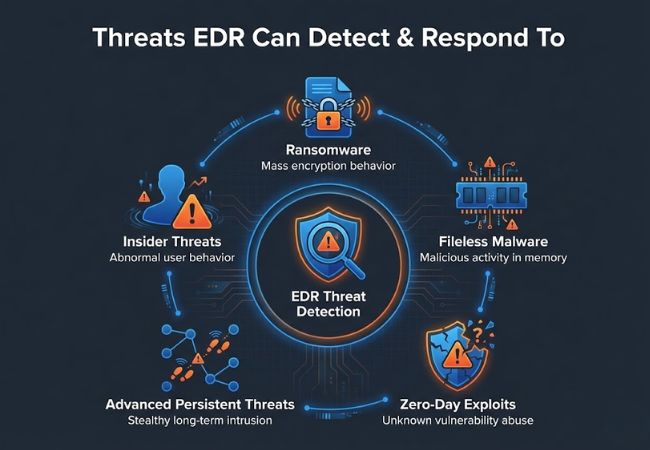
Ransomware attacks are identified through behaviors such as mass file encryption, abnormal process execution, and unauthorized privilege escalation. Early detection helps contain encryption activity before widespread damage occurs.
Fileless malware operates in memory and abuses legitimate system tools rather than writing files to disk. EDR detects these attacks by analyzing abnormal process behavior, scripting activity, and command execution patterns.
Zero-day exploits take advantage of previously unknown vulnerabilities and lack identifiable signatures. Behavioral detection enables EDR to identify exploit activity based on execution patterns rather than known indicators.
Advanced persistent threats rely on stealth, persistence, and lateral movement to remain undetected over long periods. Long-term activity correlation allows EDR to surface low-frequency behaviors that indicate sustained compromise.
Insider threats involve misuse of legitimate access by authorized users or compromised accounts. EDR highlights suspicious access patterns, privilege abuse, and unusual data movement that deviates from normal behavior.
Endpoint Detection and Response and traditional antivirus tools differ primarily in how threats are identified, analyzed, and handled after detection.
Traditional antivirus relies on signature-based detection to block known malware before execution. EDR identifies suspicious activity based on behavioral patterns observed on endpoints, including unknown or emerging threats.
Antivirus provides limited visibility focused on individual files or processes. EDR offers broader visibility into endpoint activity, allowing security teams to review timelines, relationships, and historical context.
Antivirus tools typically quarantine or delete detected files automatically. EDR supports investigation and controlled response actions, enabling containment, remediation, and forensic analysis.
Antivirus is effective against common and well-known malware. EDR is designed to handle advanced threats such as ransomware, fileless attacks, zero-day exploits, and persistent intrusions.
Antivirus operates largely without human involvement once deployed. EDR is actively used by security teams as part of incident response and SOC workflows.
Endpoint Detection and Response is often evaluated alongside other security technologies, each serving a distinct role within modern security architectures.
Endpoint Detection and Response solutions has become essential as organizations face increasingly complex attacks that bypass traditional prevention-focused security controls.
Remote work, cloud adoption, and unmanaged devices have significantly increased the number of endpoints exposed to threats. Each endpoint represents a potential entry point that requires continuous security oversight.
Modern attacks rely on techniques such as fileless execution, credential abuse, and lateral movement to avoid detection. EDR addresses these techniques by focusing on activity patterns rather than known malware signatures.
Attackers often remain undetected inside environments for extended periods, increasing potential damage. EDR helps shorten dwell time by enabling earlier detection and faster investigation.
Effective incident response depends on accurate data and rapid action at the endpoint level. EDR provides the visibility and control required to investigate incidents and contain threats efficiently.
Security incidents increasingly carry regulatory, financial, and reputational consequences. EDR supports compliance and risk management efforts by improving detection accuracy and response accountability.
Organizations typically adopt Endpoint Detection and Response when endpoint-related risks can no longer be effectively managed through prevention-only security tools.
Growth in laptops, servers, and remote devices increases the number of potential attack entry points. EDR becomes necessary when endpoint volume makes manual monitoring impractical.
Industries frequently targeted by ransomware, espionage, or data theft face higher attack pressure. EDR helps manage this exposure by enabling faster detection and response at the endpoint level.
Lack of insight into endpoint activity delays detection and investigation of security incidents. EDR addresses this gap by providing centralized visibility across endpoint environments.
Organizations developing or formalizing incident response processes benefit from endpoint-level control and evidence collection. EDR supports response readiness by enabling investigation and containment actions from a single platform.
Regulatory frameworks often require timely detection, investigation, and reporting of security incidents. EDR helps meet these requirements by improving monitoring, response consistency, and auditability.
Selecting an Endpoint Detection and Response solution requires evaluating capabilities that directly affect visibility, investigation quality, and response effectiveness.
Accurate detection reduces false positives while ensuring advanced threats are not missed. Behavioral detection quality directly affects analyst workload and response speed.
Effective EDR solutions support direct containment and remediation actions at the endpoint level. Response depth determines how quickly threats can be neutralized without external tools.
Strong investigation features provide timelines, process trees, and contextual event data. These capabilities help security teams understand attack progression and scope.
Endpoint agents must operate with minimal impact on system performance. Excessive resource usage can disrupt business operations and user productivity.
EDR platforms should integrate with existing security tools and workflows. Compatibility with SOC processes improves operational efficiency and response coordination.
Scalability determines how well an EDR solution performs as endpoint counts grow. Large or distributed environments require consistent performance across all devices.
Endpoint Detection and Response has become a foundational capability for managing endpoint security incidents in modern environments. By focusing on detection, investigation, and response at the endpoint level, EDR addresses threats that prevention-focused tools alone cannot handle.
As endpoint attack techniques continue to evolve, organizations rely on EDR to maintain visibility, reduce incident impact, and support effective response operations. Implementing EDR strengthens an organization’s ability to manage endpoint risk with precision and control.
The main purpose of EDR is to detect, investigate, and respond to security incidents on endpoint devices. It is used when malicious or suspicious activity has already bypassed preventive controls.
EDR is not a replacement for antivirus software. Antivirus focuses on preventing known threats, while EDR focuses on detecting and responding to active or post-compromise threats.
Yes, small and mid-sized businesses can use EDR to gain visibility into endpoint threats and improve incident response. Many EDR solutions are designed to support organizations without large security teams.
EDR does not require a dedicated security team, but it is most effective when actively monitored. Organizations without in-house expertise often use managed detection and response services alongside EDR.
EDR supports incident investigations by providing detailed endpoint event data, activity timelines, and response controls. This information helps identify how an attack occurred and what actions are needed to contain it.
