🚀 CloudSEK becomes first Indian origin cybersecurity company to receive investment from US state fund
Read more
Key Takeaways:
Data Security Posture Management (DSPM) is a cybersecurity approach that discovers, classifies, and analyzes sensitive data across cloud and hybrid environments. It provides visibility into where critical information is stored and how exposed it may be due to misconfigurations, shadow data, or excessive privileges.
Unlike traditional security tools that focus on infrastructure, DSPM centers security on the data itself, making it easier to evaluate real risk at the asset level. It maps sensitive data, access paths, and associated controls to help organizations strengthen compliance and identify meaningful exposure points.
DSPM also connects data sensitivity with identity context, storage configuration, and policy alignment to reveal who can access information and how it moves across services. With this foundation, the next step is understanding how DSPM performs these actions across complex cloud ecosystems.
Cloud and SaaS adoption has scattered sensitive data across multiple platforms, making it difficult to track where it lives and how it is protected. This distributed footprint creates blind spots where misconfigurations, excessive permissions, and forgotten copies can introduce silent exposure risks.
Manual audits and disconnected security tools struggle to follow data across accounts, regions, and services. As a result, teams often know risks exist but lack clarity on which ones matter most or where they originate.
DSPM overcomes these challenges by linking sensitive data to the identities, applications, and cloud resources that interact with it. This context becomes the foundation for understanding how DSPM evaluates data behavior, exposure, and access conditions across cloud environments.
DSPM works by discovering sensitive data, analyzing who can access it, and monitoring exposure risks across cloud and SaaS environments.
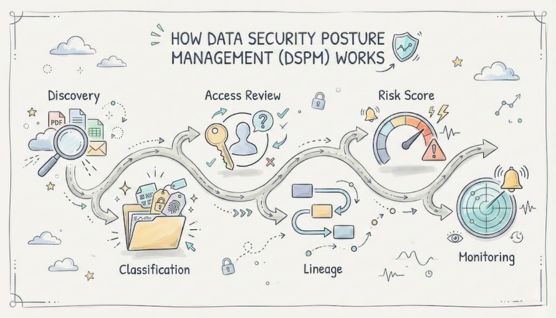
DSPM scans cloud storage, databases, data lakes, and SaaS applications to locate PII, PHI, credentials, and other sensitive assets. It also uncovers shadow data and unmanaged copies that may introduce hidden exposure risks.
Each dataset is classified based on sensitivity, business impact, and regulatory relevance. Metadata such as ownership, purpose, and retention requirements enhances prioritization.
DSPM evaluates users, roles, service accounts, and API keys to determine who can access sensitive assets. This highlights excessive privileges, unused access paths, and identity risks, reinforcing least-privilege controls.
DSPM tracks how data moves across services, pipelines, applications, and integrations. Lineage reveals unintended propagation, unsecured transfers, and downstream exposure points.
Risk scoring combines data sensitivity with access levels and configuration weaknesses to identify true exposure severity. This prioritization helps teams address the most impactful risks first.
DSPM monitors configuration drift, permission changes, encryption gaps, and unusual data behavior. Alerts identify new exposures quickly so teams can act before issues escalate.
Together, these capabilities form the functional base of DSPM and lead into the components that make a DSPM solution effective.
DSPM solutions include several essential components that work together to protect cloud data throughout its lifecycle.
A complete index of all data assets across cloud accounts and regions provides a centralized view of storage locations. This helps eliminate blind spots and reveals shadow data.
Lineage maps how data moves between systems, pipelines, backups, and integrations. Understanding these flows helps identify propagation risks and unintended exposure paths.
DSPM evaluates encryption settings, KMS usage, key rotation schedules, and unencrypted assets. These insights highlight weak cryptographic controls that could lead to compliance violations.
Exposure severity is evaluated using a scoring framework that blends sensitivity, access depth, and configuration weaknesses. This makes it easier to focus resources on the most critical vulnerabilities.
Some platforms offer automated actions such as removing public access, correcting permissions, or enforcing encryption. Automation reduces response time and eliminates manual operational load.
Strong DSPM programs measure performance using operational metrics that reflect real exposure reduction.
These metrics demonstrate DSPM’s impact on reducing exposure and improving cloud security posture.
A DSPM scan identified an object store containing over 95,000 sensitive records with publicly accessible permissions. Automated remediation removed public access within minutes and reduced the exposure window dramatically, demonstrating the value of continuous monitoring and prioritization.
DSPM identifies high-impact data risks early, reducing the likelihood of accidental exposure or unauthorized access. This proactive insight strengthens the overall security posture.
DSPM aligns sensitive data with requirements such as GDPR, HIPAA, and SOC 2. Automated evidence efforts reduce audit workloads and simplify compliance reporting.
Security teams gain visibility into which data assets, identities, and cloud resources require immediate attention. This reduces alert fatigue and improves decision-making.
DSPM reduces the time spent on manual audits, data mapping, and multi-tool correlation. Teams avoid chasing low-risk findings and maintain higher productivity.
Linking data to user roles and service accounts improves identity governance and reduces privilege creep. This enhances Zero Trust alignment.
Risk-driven prioritization and automated fixes shorten response times. Organizations can resolve issues before they escalate into incidents.
DSPM focuses on securing sensitive data, while CSPM, DLP, and data governance address different aspects of cloud security and compliance.
DSPM maps sensitive data and access risks, while CSPM analyzes cloud configurations and policy violations. Together they reveal whether misconfigurations expose sensitive assets.
DLP monitors data in motion to prevent exfiltration, while DSPM evaluates data at rest across cloud services. DSPM improves DLP accuracy with better discovery and classification.
Data governance sets policies and ownership standards, while DSPM identifies real exposure conditions. Governance defines expectations; DSPM shows whether environments meet those expectations.
DSPM uncovers unmanaged, duplicated, or forgotten data across cloud environments. This reduces hidden exposure risks.
Access governance identifies excessive permissions, unused access paths, and risky identity-to-data relationships. These insights reinforce least-privilege strategies.
DSPM maps sensitive data to frameworks like GDPR, HIPAA, and SOC 2. Automated tagging and reporting simplify audits.
Exposure prevention identifies misconfigurations such as public access, weak encryption, or insecure sharing settings. Addressing these early prevents accidental leaks.
DSPM shows which sensitive data was exposed and who interacted with it. This improves the speed and accuracy of incident investigations.
Date lifecycle oversight highlights outdated copies, unnecessary retention, and unsecured data propagation. Teams can enforce lifecycle and retention policies effectively.
Cloud-integrated DSPM solutions scan cloud services and databases to identify sensitive information and exposure conditions. They provide continuous visibility by linking sensitivity with configuration and access context.
These tools uncover sensitive data across repositories and assign sensitivity categories. Classification builds the foundation for meaningful risk evaluation.
They map access paths across users, roles, service accounts, and API keys. This helps organizations strengthen least-privilege policies.
These tools score exposure by blending sensitivity with access depth and configuration weaknesses. Prioritization directs attention to high-impact issues.
These solutions take corrective actions such as adjusting permissions or correcting misconfigurations. Automation reduces manual effort and enforces consistent policies.
They align sensitive data with major regulations and provide audit-ready evidence. This reduces the effort required for compliance assessments.
DSPM protects sensitive data such as PII, PHI, financial information, and internal business records. Its purpose is to reduce exposure caused by misconfigurations, excessive access, and unmanaged copies.
DSPM does not replace CSPM or DLP because each tool addresses a different layer of security. It enhances both by adding data-centric visibility.
Most DSPM platforms perform continuous or near-real-time scanning. This ensures that changes in data storage and permissions are detected quickly.
Security teams, cloud engineers, compliance leaders, and governance groups use DSPM insights. Each team applies these insights from different operational perspectives.
DSPM supports compliance by classifying sensitive data and mapping it to frameworks like GDPR and HIPAA. It also simplifies audits by providing accurate lineage and exposure evidence.
DSPM typically supports multi-cloud, hybrid, and SaaS environments through API integrations. This provides broad visibility across diverse data ecosystems.
DSPM provides deep visibility into how sensitive data is stored, accessed, and exposed across modern cloud environments. This allows teams to focus on the risks that matter most and respond with greater precision.
As cloud adoption expands, organizations need data-centric insight to maintain a strong security posture. DSPM provides the foundation for exposure reduction, coordinated governance, and long-term resilience.
