🚀 CloudSEK becomes first Indian origin cybersecurity company to receive investment from US state fund
Read more
Data security management is the practice of protecting an organization’s data throughout its entire lifecycle, including creation, storage, use, sharing, and deletion. It ensures that data is safeguarded from unauthorized access, exposure, alteration, or loss.
This practice relies on a combination of policies, procedures, and technical controls such as access management, encryption, and monitoring. Together, these measures maintain the confidentiality, integrity, and availability of data.
DSM also involves governance and human oversight, not just technology. By aligning tools, processes, and employee responsibilities, organizations reduce risks from cyber threats, human error, and insider misuse while supporting compliance and trust.
Organizations depend on data to operate efficiently, serve customers, and maintain competitive advantage. When data is exposed, altered, or lost, it can disrupt operations, undermine decision-making, and damage long-term business stability.
Poor data security can lead to financial losses, legal penalties, and reputational harm. As data breaches continue to increase in scale and impact, strong data security management has become essential for protecting both business continuity and customer confidence.
Data Security Management works by applying different security controls as data moves through creation, storage, use, sharing, and disposal. At each stage, policies and technical measures are adjusted to address the specific risks introduced during that phase.
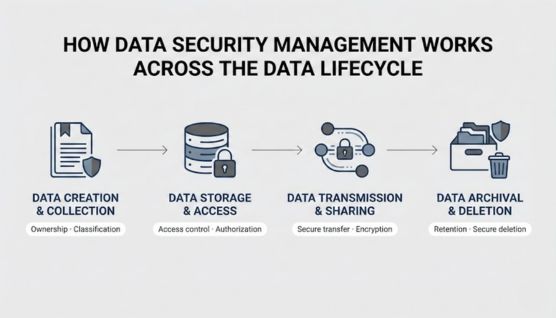
Security starts when data is created or collected by assigning ownership and determining its sensitivity level. This ensures appropriate controls are applied before the data is widely accessed or stored.
Stored data is protected through access controls that restrict who can view, modify, or delete it. Authentication and authorization mechanisms help prevent unauthorized or excessive access.
When data is transmitted or shared, security measures protect it from interception and misuse. Secure transfer methods and encryption help maintain confidentiality during movement.
Archived data must remain protected even when it is no longer actively used. Secure deletion processes ensure outdated or unnecessary data is permanently removed and cannot be recovered.
As data moves through its lifecycle, it appears in different forms and carries varying levels of risk. Data Security Management accounts for these differences by applying protection based on how data is structured, shared, and regulated.
Structured data is typically stored in databases and business systems where accuracy and consistency are essential. Security efforts focus on controlling access and preventing unauthorized changes that could impact operations.
Unstructured data spreads across emails, documents, and shared files, making it harder to track and secure. Because it moves frequently between users and systems, visibility and usage controls become critical.
Sensitive data poses the highest risk when exposed due to legal, financial, or privacy implications. Protecting this data requires stricter controls to meet regulatory standards and organizational risk policies.
Data security management relies on distinct control areas that protect data in different ways. Each component addresses a specific risk within the overall security framework.

Managing data security is about keeping controls effective over time as data usage, teams, and risks change. This requires regular oversight rather than new tools or repeated setup.
Every critical data set should have a clearly defined owner. Ownership ensures accountability for decisions, exceptions, and security issues.
Teams must maintain awareness of how data is being accessed and shared across the organization. Consistent visibility prevents security gaps from going unnoticed.
Management involves reviewing whether existing controls are still working as intended. Regular oversight helps identify weaknesses before they become incidents.
Data security requires coordination between IT, security, legal, and business teams. Clear communication reduces delays when decisions or actions are needed.
As risks and business needs evolve, data security controls must be adjusted. Small, timely changes help maintain protection without disrupting operations.
Data Security Management focuses on protecting data itself wherever it exists, while cybersecurity focuses on protecting the systems, networks, and infrastructure that store and transmit data.
Even with strong policies and tools in place, organizations often face practical challenges when managing data security. These issues usually stem from complexity, visibility gaps, and human factors rather than a lack of technology.
Many organizations struggle to identify where all their data is stored and how it is used. Without full visibility, applying consistent security controls becomes difficult.
Data environments continue to expand across cloud platforms, applications, and devices. This complexity makes it harder to enforce uniform security policies everywhere.
Security policies may exist but are not always applied consistently across systems and teams. Gaps in enforcement can create weak points that attackers or insiders exploit.
Employees can unintentionally expose data through mistakes or unsafe practices. Insider misuse, whether accidental or intentional, remains one of the hardest risks to manage.
Threats change faster than many security programs can adapt. Organizations that fail to update controls regularly may fall behind emerging risks.
Implementing data security management requires a structured approach that aligns people, processes, and technology. Rather than relying on isolated tools, organizations must build security into how data is handled across the business.
Implementation starts with understanding what data exists and where the highest risks lie. This assessment helps prioritize security efforts based on potential impact.
Clear policies establish how data should be accessed, stored, and shared. These rules provide consistency and guide both technical controls and employee behavior.
Technical controls such as access restrictions and encryption are deployed to enforce policies. These controls ensure data protection is applied consistently across systems.
Employees play a critical role in data security and must understand their responsibilities. Training reduces mistakes that often lead to data exposure.
Ongoing monitoring helps verify that controls are working as intended. Continuous improvement ensures data security adapts to new risks and changes.
CloudSEK approaches Data Security Management by focusing on preventing data exposure before it becomes a security incident. Its Digital Risk Protection platform helps organizations identify external threats that can lead to data leaks or unauthorized access.
The platform continuously monitors the open web, dark web, cloud assets, and public code repositories to detect exposed credentials, sensitive data, and vulnerable systems. By mapping an organization’s external attack surface and supply chain, CloudSEK helps reduce the risk of data being accessed through overlooked entry points.
In addition to prevention, CloudSEK supports response and compliance by providing threat intelligence and takedown assistance for phishing sites and malicious domains. This proactive, risk-driven approach helps organizations manage data security more effectively across their digital ecosystem.
