🚀 CloudSEK becomes first Indian origin cybersecurity company to receive investment from US state fund
Read more
A dark web leak site is a TOR-based platform used by ransomware and cyber extortion groups to publicly expose stolen organizational or personal data. Publication is intended to pressure victims into paying ransoms by demonstrating proof of compromise.
These sites operate on anonymity networks like TOR, making attribution and takedown difficult. Leak pages typically display data samples, victim names, and timelines to legitimize threats and escalate negotiations.
Data published on leak sites often includes PII, financial records, credentials, and corporate intellectual property. Early detection, preventive controls, and structured incident response reduce financial, legal, and reputational damage caused by public exposure.
Dark web development began with U.S. military research focused on anonymous communication. This effort led to creation of the TOR network, which uses layered encryption to conceal user identities and traffic paths.
Criminal groups later exploited this anonymity to host underground marketplaces, forums, and leak sites. Ransomware operations accelerated movement from isolated data dumps to structured extortion platforms designed for public exposure.
As of 2025, the U.S. Department of Health and Human Services reported 364 healthcare hacking incidents affecting over 33 million Americans, highlighting the scale of modern data exposure. A portion of stolen information ultimately surfaces as dark web leaked data, reinforcing the role of leak sites in cybercrime infrastructure.
Dark web leak sites are curated platforms where attackers upload and showcase stolen data to pressure victims or to sell information to other criminals. These sites operate behind anonymity networks, making them difficult to detect or dismantle.
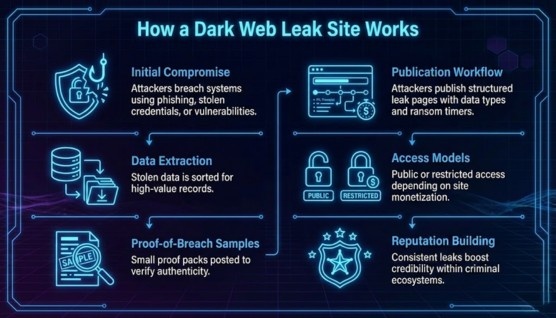
Attackers breach networks using phishing, credential theft, or vulnerabilities and exfiltrate large volumes of data. The stolen information is sorted to identify high-value records that enhance extortion pressure.
Threat actors post small “proof packs” to demonstrate the authenticity of the stolen data. These samples are deliberately chosen to alarm victims and signal credibility to criminal buyers.
Once samples are verified, attackers publish structured pages listing affected data types, ransom demands, and countdown timers. Negotiation links and communication channels are often included for pressured discussions.
Some leak sites are fully public while others require invitations or payment to view full dumps. Restricted models allow operators to monetize access and maintain selective visibility.
Consistent leaking of high-value data increases a group’s status within criminal ecosystems. Strong reputations attract affiliates and amplify the psychological impact on victims.
Cybercriminals rely on leak sites to increase negotiation leverage during extortion. Public exposure of sensitive data often forces victims to reconsider paying.
Leak sites also serve as reputation tools for threat actors seeking credibility within criminal communities. A visible track record of successful leaks helps attract affiliates and partners.
Additionally, publishing data demonstrates technical capability, which strengthens a group’s standing in the ransomware ecosystem.
Dark web leak activity shows clear geographic concentration, with certain countries appearing far more often due to infrastructure density, digital scale, and the presence of high-value organizational targets.
Observed Dark Web Leak Activity by Country:
These figures represent observed associations with dark web leak sites rather than attacker nationality or government involvement. Higher visibility often reflects large cloud footprints, dense hosting environments, and frequent targeting of regulated industries.
Organizations operating in high-exposure regions face increased likelihood of public data leaks due to attacker focus and infrastructure visibility. Countries with mature digital economies also experience higher regulatory and reputational pressure, amplifying extortion impact.
For multinational businesses, geographic exposure multiplies risk by introducing jurisdiction-specific legal obligations and enforcement timelines. This makes regional awareness critical for effective dark web monitoring and incident response planning.
Attackers publish data that maximizes leverage, financial value, and long-term harm to victims. The following categories represent the most frequently exposed datasets.
Names, addresses, IDs, and contact information enable identity theft and targeted phishing. PII remains one of the most liquid assets in cybercrime markets.
Banking documents, invoices, and payment details support fraud and money-movement schemes. Regulatory actions often follow leaks of financial data.
User passwords, admin credentials, API keys, and access tokens are commonly exposed. These enable deeper system compromise and lateral movement.
Source code, R&D files, designs, and proprietary business documents are published to damage competitive standing. Leaked IP can have long-term strategic consequences.
Emails, HR files, contracts, and incident reports create reputational harm and operational risk. Internal records often reveal sensitive context attackers exploit.
Attackers merge multiple data types (e.g., credentials + PII) to increase effectiveness in fraud campaigns. These combinations escalate downstream risk for individuals and businesses.
Dark web leaked data is used by cybercriminals for fraud, identity theft, and automated attacks. Once exposed, it can be reused repeatedly, extending exploitation far beyond the initial breach.
Exposed personal dark web leaked data enables the creation of fraudulent accounts or impersonation attempts. Victims often face prolonged recovery periods.
Stolen credentials allow attackers to infiltrate additional systems and services. This creates cascading breaches and partner-ecosystem risk.
Fraudulent transactions and invoice manipulation are common outcomes of dark web leaked financial data. Organizations also incur significant post-incident costs.
Data leaks can trigger notification obligations, fines, and investigations under laws like GDPR or HIPAA. Mishandling disclosures worsens penalties.
Incident response efforts divert resources and disrupt business continuity. Breach fallout can affect suppliers and customers.
High-profile leaks diminish customer trust and negatively affect revenue. Recovering reputation often requires substantial long-term communication efforts.
Leaked data rarely disappears once it reaches the dark web, as it is repeatedly copied, redistributed, and repackaged by different threat actors. Even if the original leak site is taken down, the data often continues circulating for months or years.
Mirror sites replicate leaked data across multiple dark web domains to ensure continued availability. These mirrors make takedowns ineffective by preserving access even when the original source is removed.
Threat actors frequently re-upload leaked data to new forums, marketplaces, or leak sites over time. This practice reintroduces old data to new audiences and keeps it relevant for ongoing abuse.
Individual records are commonly combined with other breach data to increase volume and value. Bundling makes leaked data more effective for large-scale fraud and automated attacks.
Leaked data is bought and resold multiple times across underground markets. Each resale cycle extends the lifespan of the data and increases the number of actors capable of exploiting it.
Because leaked data remains accessible for long periods, it is important to distinguish leak sites from other forms of data exposure.
Understanding these differences helps organizations choose the correct response strategy and avoid misinterpreting exposure.
A breach is unauthorized access; a leak is the public exposure that follows. Breaches can occur silently, while leaks make the incident visible.
Paste sites are transient text-sharing platforms, whereas leak sites are structured extortion hubs. Paste sites lack negotiation features or sale mechanisms.
Leak sites are designed for monetization and coercion. Breaches alone may be reconnaissance or espionage without immediate publication.
Leak sites often persist through mirror domains and require membership or TOR access. Paste sites are easy to remove and not curated.
Strong preventive controls reduce the likelihood of a breach leading to a public leak. The following areas offer high-impact resilience.
Implement MFA, least privilege, and strict role-based access. Regularly audit privileged accounts for misuse.
Prioritize patching high-risk systems and reduce exposure time through automated workflows. Attackers frequently exploit unpatched vulnerabilities.
Encrypt sensitive data at rest and in transit to reduce its value if exfiltrated. Use tokenization for high-risk fields.
Limit lateral movement with micro-segmentation and zero-trust principles. Segmented environments shrink the blast radius of a breach.
Apply secure coding practices, dependency scanning, and pipeline hardening. Vendor risk reviews strengthen supply-chain integrity.
Educate staff on phishing, impersonation, and data-handling risks. Simulated campaigns reinforce awareness.
Maintain immutable backups with regular recovery testing. This reduces leverage during ransomware negotiations.
Early detection provides critical lead time to contain incidents before public exposure escalates harm.
Effective tools must scan TOR, I2P, private forums, marketplaces, and foreign-language sources. Comprehensive coverage increases detection accuracy.
Continuous scanning identifies exposed usernames, passwords, and tokens. Rapid resets prevent secondary compromise.
Correlating leak indicators with internal logs improves prioritization. Contextual threat intelligence enhances triage quality.
Embedded decoy files and tokens reveal unauthorized access attempts. These early signals alert teams to exfiltration events.
Human validation reduces false positives and uncovers hidden context. Skilled analysis strengthens decision-making.
If your organization is listed on a dark web leak site, a structured and immediate response is critical. Follow the steps below to contain impact and meet regulatory and operational obligations.
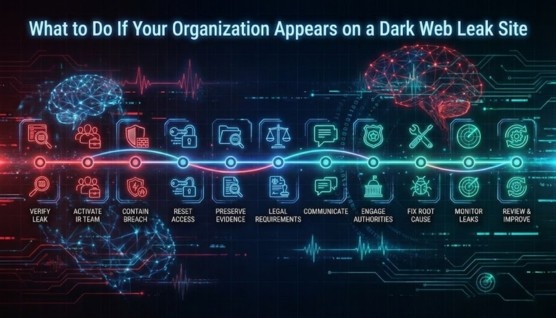
Confirm that the posted samples match your data and systems. This helps determine the real scope and prevents unnecessary escalation.
Bring together security, legal, and communications teams to coordinate response. A unified approach avoids missteps and ensures compliance.
Isolate affected systems, kill malicious sessions, and revoke suspicious access tokens. Quick containment stops further data loss.
Force password resets for impacted accounts and enforce MFA across critical systems. Privileged accounts should be prioritized first.
Collect logs, system images, and forensic artifacts for investigation. Proper preservation supports root-cause analysis and insurance claims.
Determine if the leaked data triggers regulatory or contractual notifications. Timely reporting reduces penalties and compliance risks.
Send accurate updates to customers, partners, and regulators. Transparent communication helps maintain trust and reduces speculation.
Notify law enforcement and involve your cyber insurance incident-response partners. External support enhances investigations and remediation.
Patch exploited vulnerabilities, close misconfigurations, rotate keys, and remove persistence mechanisms. Test that remediation is effective.
Track the leak site for additional data drops or escalations. Continuous monitoring helps you respond to changes quickly.
Conduct a post-incident review to understand what failed and what worked. Update policies, controls, and playbooks to prevent recurrence.
Selecting the right tool determines how quickly and accurately an organization identifies leak activity.
Robust tools include deep, multilingual coverage of leak sites, forums, and marketplaces. Broader coverage increases discovery likelihood.
Timely alerts allow teams to take immediate action. Prioritized notifications reduce noise and accelerate response.
Accurate matching detects leaked credentials, PII, and sensitive files. Fuzzy matching helps identify partial or obfuscated leaks.
Tools should integrate with SIEM, SOAR, and ticketing systems. Seamless workflows streamline incident response.
Dashboards, enrichment tools, and actor insights help validate results quickly. Strong investigative tools reduce manual effort.
Evidence exports, reporting templates, and chain-of-custody support simplify regulatory obligations. These capabilities save time during audits.
Monitoring tools reduce risk by enabling early, actionable insights and improving the response timeline.
Quick identification of leaks limits exploitation time. Faster awareness improves containment results.
Context-rich intelligence helps analysts focus on real threats. This improves remediation depth and speed.
Monitoring tools provide documentation needed for regulatory deadlines. Proper records reduce legal exposure.
Insights reveal recurring weaknesses and influence security investment. Long-term patterns help reduce incident frequency.
Automation and enriched data decrease manual workload. Efficiency gains reduce operational costs.
Visiting the dark web is not illegal, but accessing stolen data may violate privacy or data protection laws. Organizations should rely on authorized monitoring tools.
Data may appear within hours or weeks depending on the attacker’s timeline. Some groups leak samples immediately to increase pressure.
Yes, but not always quickly due to anonymity networks. Some sites reappear under new domains after takedowns.
Most major groups do, but some rely solely on encryption and negotiation. Leak sites have become the industry norm for extortion.
Yes, but consumer-grade monitoring tools are safer than manual browsing. Manual access exposes users to risk.
Dark web leak sites have become a powerful tool in ransomware and extortion campaigns. Understanding how they work helps organizations prepare, detect, and respond more effectively.
With strong preventive measures and reliable monitoring tools, businesses can reduce exposure and protect sensitive data in an increasingly hostile threat landscape.
