🚀 CloudSEK becomes first Indian origin cybersecurity company to receive investment from US state fund
Read more
Cyber Threat Intelligence (CTI) is the process of collecting, analyzing, and interpreting information about existing and potential cyber threats. It focuses on understanding threat actors, their motivations, and the methods they use to target systems and data.
Unlike raw security data, CTI adds context and meaning to threat information so it can guide informed decisions. This intelligence helps organizations anticipate attacks, reduce uncertainty, and respond more effectively to evolving cyber risks.
CTI operates across multiple levels, including strategic, tactical, operational, and technical intelligence. Together, these levels support proactive defense by turning fragmented threat signals into actionable insights that strengthen an organization’s overall security posture.
Cyber Threat Intelligence is important because cyber attacks are no longer random or generic. Modern threats are intentional, adaptive, and designed to bypass traditional security controls.
Without CTI, organizations lack visibility into who is targeting them and why those attacks matter. This leads to reactive security decisions based on alerts instead of informed risk understanding.
CTI provides the necessary awareness to recognize emerging threats before they cause significant damage. By improving situational awareness, it helps organizations make better security decisions and reduce overall exposure to cyber risk.
Cyber Threat Intelligence works through a defined flow that turns raw threat information into intelligence that supports security decisions. Each stage has a specific purpose and prepares the information for the next step.
Cyber Threat Intelligence is divided into four types that reflect what kind of decisions the intelligence supports and how it is used. These types range from high-level risk awareness to technical indicators used directly in security systems.
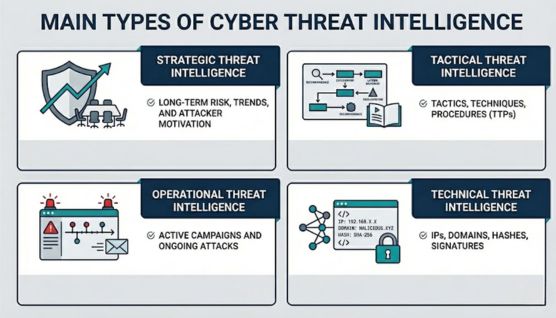
Strategic threat intelligence used for long-term cyber risk, threat trends, and attacker motivations. It is used by executives and leadership teams to guide security strategy, policy, and investment decisions.
Tactical threat intelligence focuses on how attackers operate, including their tactics, techniques, and procedures (TTPs). Security teams use it to improve detection logic, defensive controls, and threat awareness.
Operational threat intelligence provides context about active or emerging attacks and threat campaigns. It supports incident response by helping teams understand what is happening now and what may happen next.
Technical threat intelligence consists of concrete indicators such as malicious IP addresses, domains, file hashes, and signatures. These indicators are consumed by security tools to detect, block, or investigate threats.
Cyber Threat Intelligence is not used the same way by everyone. It becomes useful only when it is applied to real decisions, whether that decision is triaging an alert, stopping an active attack, or deciding where to invest in security.
For security operations teams, CTI helps answer a simple question: does this alert actually matter? By linking alerts to known threat actors, campaigns, or behaviors, analysts can quickly separate routine noise from activity that deserves immediate attention.
During an incident, CTI provides clarity when time is limited. It helps responders understand how the attacker is likely operating, what tools they may already have access to, and what moves typically come next, allowing containment and recovery to happen with fewer assumptions.
Threat hunters use CTI as a starting point rather than a confirmation tool. Instead of waiting for alerts, intelligence points them toward specific behaviors, techniques, or environments where attackers are known to hide before detection systems catch up.
At the leadership level, CTI is less about technical detail and more about risk direction. It helps decision-makers see which threats are growing, which business assets are most exposed, and where security efforts will have the greatest impact over time.
Threat data refers to raw security information collected from systems and external sources, while threat intelligence is the analyzed and contextualized output derived from that data.
Threat intelligence is derived from multiple sources that provide visibility into different aspects of the threat landscape. Combining these sources helps organizations build a more accurate and reliable understanding of cyber threats.
Internal sources include data generated within an organization’s own environment, such as security logs, incident reports, network traffic, and endpoint telemetry. These sources are valuable because they reflect threats that are directly relevant to the organization.
Open-source intelligence comes from publicly available information, including security blogs, research publications, forums, and vulnerability databases. OSINT helps organizations stay aware of widely known threats, exploits, and attacker techniques.
Information-sharing communities, such as industry-specific groups and ISACs, allow organizations to exchange threat intelligence with peers. These sources are useful for understanding threats targeting a specific sector or region.
Dark web and closed-source intelligence focuses on monitoring underground forums, marketplaces, and restricted channels. This type of source helps identify early indicators of planned attacks, data leaks, or emerging criminal activity.
Cyber Threat Intelligence helps organizations make security decisions based on understanding rather than assumptions. Its value comes from reducing uncertainty and improving how threats are identified, prioritized, and handled.
Cyber Threat Intelligence is valuable, but it is difficult to execute effectively without the right processes and expertise. Many organizations struggle to turn large volumes of threat information into intelligence that actually supports decisions.
Threat intelligence tools and services support the collection, analysis, management, and use of threat information across security operations. They help organizations turn intelligence into actions that improve detection, response, and risk awareness.
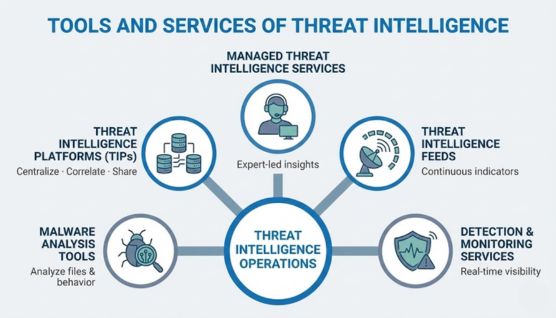
Threat intelligence platforms centralize intelligence from multiple sources into a single system. They support tasks such as correlation, enrichment, prioritization, and sharing of intelligence across security teams.
Threat intelligence feeds provide continuous updates about indicators, attacker activity, and emerging threats. These feeds supply timely inputs that can be used for monitoring, enrichment, and early warning.
Malware analysis tools are used to examine suspicious files, links, and behaviors to understand how threats operate. They help security teams validate indicators and uncover attacker techniques and capabilities.
Some intelligence is delivered through security services that monitor systems, networks, or endpoints directly. These services combine real-time telemetry with threat intelligence to identify malicious activity as it occurs.
Managed threat intelligence services provide analyst-driven insights without requiring internal expertise. They deliver curated intelligence, alerts, and assessments tailored to an organization’s risk profile and environment.
Successful cyber threat intelligence implementation requires clear objectives, relevant data, and consistent integration into security operations. Without structure and alignment, threat intelligence efforts often produce information but little value.
Start by identifying what decisions the intelligence should support, such as risk prioritization or incident response. Clear objectives prevent unnecessary data collection and keep intelligence aligned with business needs.
Not all threats are equally important to every organization. Intelligence efforts should prioritize threats based on industry, geography, assets, and known adversaries.
Relying on a single source limits visibility. Combining internal data with external intelligence improves accuracy and reduces blind spots.
Raw information must be reviewed, correlated, and interpreted by skilled analysts. This step is essential to transform data into intelligence that explains impact and intent.
Threat intelligence should feed directly into security monitoring, incident response, and risk management processes. Intelligence that is not operationalized quickly loses relevance.
CTI programs should be regularly reviewed to assess accuracy, usefulness, and timeliness. Feedback from security teams helps refine intelligence priorities over time.
CloudSEK runs a Cyber Threat Intelligence program focused on finding external risks before they turn into incidents. Using XVigil and BeVigil, it monitors the surface, deep, and dark web to detect data leaks, malicious domains, and exposed assets linked to an organization.
The intelligence highlights which parts of the attack surface are actively being targeted and how those threats are developing. This helps security teams understand attacker intent and prioritize real risks instead of reacting to isolated alerts.
The platforms continuously map global threat activity to an organization’s infrastructure and applications, then deliver focused intelligence that teams can act on quickly. In parallel, CloudSEK contributes to the security ecosystem through CTI researcher internships and collaboration with CERT-In to build practical threat analysis skills.
