🚀 CloudSEK becomes first Indian origin cybersecurity company to receive investment from US state fund
Read more
Cloud environments now run the majority of modern applications, data platforms, and digital services—often exposed to the internet and managed through APIs rather than physical networks. This shift has fundamentally changed how risk is created and exploited.
According to IBM’s Cost of a Data Breach Report, cloud-related breaches are among the most expensive to remediate, largely driven by misconfigurations and identity misuse rather than infrastructure failure.
Cloud security is the discipline of protecting cloud-based data, applications, workloads, identities, and configurations across public, private, and hybrid cloud environments.
It secures internet-facing, API-driven, and continuously changing resources where perimeter-based controls no longer function.
Gartner reports 99% of cloud security incidents originate from customer misconfigurations, and more than 60–80% of cloud attacks target APIs, making cloud security a configuration- and identity-centric problem. Operates in dynamic environments where access is identity-centric, infrastructure scales automatically, and configuration changes occur continuously.
Security controls enforce protection at the identity, configuration, and runtime layers to reduce misconfigurations, unauthorised access, and workload compromise. Cloud providers protect the underlying infrastructure, while organisations protect identities, permissions, data, and configurations. This model establishes cloud security as a continuous, risk-based practice that maintains visibility, control, and resilience as cloud environments evolve.
Cloud security is important because cloud environments fundamentally change how risk is introduced, exploited, and scaled. The following factors make cloud security a critical control layer rather than an optional enhancement:
Cloud security works by continuously monitoring cloud environments, analyzing risk in real time, and enforcing controls automatically as resources, identities, and configurations change. It replaces static perimeter defenses with adaptive, cloud-native protection.
Step 1: Discover and inventory cloud assets
Cloud security platforms continuously identify cloud resources across accounts, regions, and services. This includes workloads, storage, identities, APIs, and configurations, creating a real-time inventory that reflects how the environment actually operates.
Step 2: Monitor configurations and posture
Security controls evaluate cloud configurations against security best practices and compliance baselines. Misconfigurations, insecure defaults, and configuration drift are detected as soon as changes occur.
Step 3: Analyze identity and access behavior
User roles, service accounts, API keys, and permissions are assessed against least-privilege principles. Abnormal access patterns, excessive permissions, and risky identity behavior are flagged for investigation.
Step 4: Inspect workload and runtime activity
Cloud security monitors how workloads behave during execution. Suspicious activity, such as unexpected network connections, privilege escalation, or anomalous process behavior, signals potential compromise.
Step 5: Enforce policies and detect risk
Detected risks are evaluated using policy logic, behavioral analysis, and contextual signals. This allows cloud security to prioritize real threats rather than static rule violations.
Step 6: Automate response and remediation
When risk is confirmed, cloud security can automatically remediate issues by restricting access, correcting configurations, isolating workloads, or alerting security teams to prevent escalation.
Step 7: Integrate with security operations
All findings and actions are fed into SIEM, SOAR, and incident response workflows. This ensures cloud threats are managed as part of a unified security strategy rather than in isolation.
A common real-world cloud security failure occurs when a storage service or database is deployed with overly permissive access settings. High-profile incidents show that cloud data breaches are more often caused by misconfigurations than by zero-day exploits or malware.
For example- The Capital One breach in 2019 exposed data from over 100 million customers due to a misconfigured IAM role and firewall rule in AWS, not a flaw in the cloud provider’s infrastructure.
Attackers continuously scan cloud environments for exposed resources such as public storage buckets, unsecured APIs, and over-privileged identities. According to Microsoft’s 2022 cloud threat research, internet-exposed cloud assets are often discovered by automated scanners within minutes of misconfiguration, enabling rapid data access before defenders detect the exposure.
Misconfiguration-driven breaches have occurred repeatedly at scale. In 2017, Accenture exposed sensitive internal data through unsecured cloud storage, while Facebook disclosed in 2019 that hundreds of millions of user records were exposed due to improperly secured cloud databases. In each case, the cloud provider remained secure—the failure occurred on the customer side of the shared responsibility model.
Cloud environments face unique threats because they are dynamic, identity-driven, and exposed through APIs and internet-facing services. Attackers exploit these characteristics to bypass traditional controls and expand access rapidly.
Threat 1- Misconfigurations and insecure defaults
Misconfigurations remain the most consistent source of cloud exposure. According to Orca Security’s State of Cloud Security Report, 81% of organizations have at least one public‑facing cloud asset (e.g., with open ports), typically due to misconfigurations or neglected security settings rather than active exploitation.
Threat 2- Identity compromise and privilege abuse
Stolen credentials, leaked access keys, and excessive permissions allow attackers to authenticate as legitimate users or services. Once inside, privilege escalation enables access to sensitive resources and control planes.
Threat 3- Data exposure and accidental leakage
Cloud data leaks are frequently accidental. IBM’s Report that misconfigured cloud environments are among the top three causes of data exposure, with incidents taking significantly longer to detect due to the absence of clear attack signals.
Threat 4- API abuse and insecure integrations
Cloud platforms are fundamentally API-driven. The Salt Labs State of API Security Report (Q1 2023) found a 400% increase in unique API attackers over a recent six‑month period, based on empirical customer data. This reflects a rapid rise in attacker activity against APIs.
These threats persist because cloud environments change continuously, making constant visibility, strong identity controls, and automated detection essential.
Cloud security protects the full set of assets that operate inside cloud environments, where access is identity-based, configurations change continuously, and control planes are exposed through APIs. Protection extends beyond infrastructure to include identities, data, and operational behavior.
Cloud security is built on a set of core components that work together to protect dynamic, internet-accessible environments. Each component addresses a specific failure point common in cloud deployments.
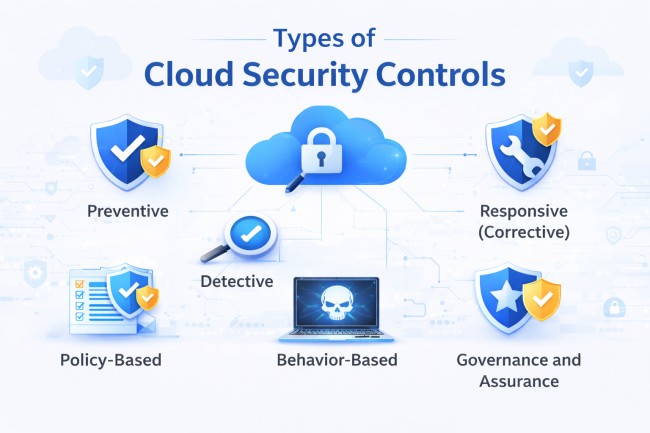
Cloud security controls operate across the lifecycle of risk—before exposure, during activity, and after detection. Each control type addresses a specific failure mode and is most effective when layered together.
Cloud security and traditional IT security differ fundamentally in architecture, control points, and risk dynamics. Cloud security is designed for elastic, identity-driven environments, while traditional IT security assumes static infrastructure and defined network boundaries.
These challenges make cloud security a continuous risk management function, requiring real-time visibility, identity governance, and automated enforcement to operate securely at cloud scale.
Cloud security is a foundational pillar of modern security strategies because it protects the environments where applications, data, and identities now operate by default. As organizations adopt cloud-first and multi-cloud models, security enforcement must shift from static infrastructure controls to continuous, identity- and configuration-driven protection.
In Zero Trust architectures, cloud security enforces the principle of never trust, always verify. Identities, workloads, and services are continuously evaluated based on behavior, permissions, and context rather than network location, reducing the risk of implicit trust and lateral movement.
Cloud security also plays a critical role in DevSecOps and CI/CD pipelines. By embedding security controls into infrastructure-as-code, deployment workflows, and runtime monitoring, organizations detect misconfigurations and vulnerabilities early without slowing development velocity.
Finally, cloud security integrates with SOC, SIEM, and SOAR platforms to support centralized detection and response. Telemetry from cloud environments enriches threat detection, enables automated remediation, and ensures cloud risk is managed as part of a unified enterprise security strategy rather than in isolation.
