🚀 CloudSEK becomes first Indian origin cybersecurity company to receive investment from US state fund
Read more
Key Takeaways:
Cloud Access Security Broker (CASB) is a cloud security control that governs access between users and cloud-based services. Placement between cloud service consumers and cloud service providers enables enforcement of security and governance policies at the access layer.
Modern enterprise applications increasingly operate on third-party platforms rather than internal infrastructure. Loss of direct ownership over application environments limits visibility and control using traditional perimeter-based security models.
A dedicated access governance layer restores oversight across external cloud services without embedding controls inside those services. Focus on regulating service access and user interaction defines CASB as a distinct cloud security category rather than a network security tool.
Cloud Access Security Broker (CASB) works by evaluating user interactions with cloud services at the moment access or activity occurs. Policy decisions are triggered using signals such as identity context, application type, and data sensitivity.
Integration with cloud platforms relies on logical control points rather than direct infrastructure ownership. Enforcement may take place during access or after activity is recorded, depending on configuration requirements.
Visibility across cloud usage is maintained through continuous analysis of behavior and data movement. Effectiveness persists even when cloud services are accessed remotely or from unmanaged devices.
Different CASB deployment models exist to provide visibility and control across varying cloud access scenarios. Selection depends on factors such as traffic flow, user location, and required enforcement depth.
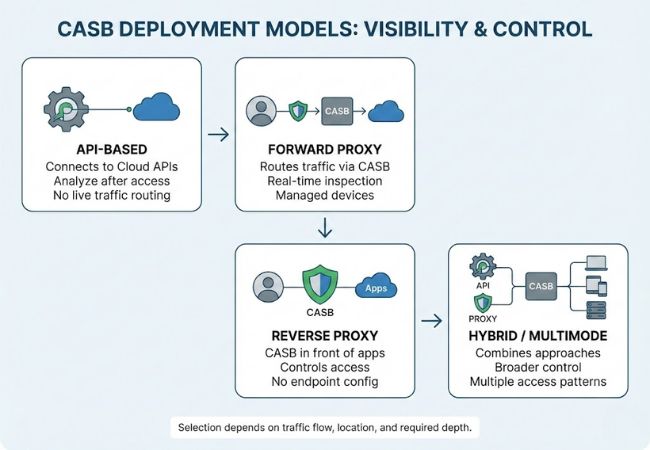
API-based deployment connects directly to cloud service APIs to analyze activity and apply policies after access occurs. Visibility into user actions, data storage, and configuration changes is achieved without routing live traffic.
Forward proxy deployment routes user traffic through the CASB before reaching cloud services. Real-time inspection and enforcement occur during access, typically requiring managed devices or network configuration.
Reverse proxy deployment places the CASB in front of cloud applications to control access without endpoint configuration. Authentication and policy checks are enforced as users connect to the service.
Hybrid deployment combines API-based and proxy-based approaches to cover multiple access patterns. Broader control is achieved across managed devices, unmanaged devices, and cloud-native integrations.
Security capabilities within a CASB are grouped into functional control areas that address visibility, governance, data handling, and risk detection across cloud services.
Application discovery identifies cloud services accessed by users, including unsanctioned or unknown applications. Usage patterns and access frequency are analyzed to map real cloud exposure.
User activity monitoring tracks actions performed within cloud applications after access is granted. Behavioral context helps identify risky or unauthorized interactions.
Data classification capabilities recognize sensitive information stored or processed in cloud services. Content awareness enables policy enforcement based on data type and risk level.
Data control mechanisms apply rules that restrict sharing, downloading, or external exposure. Policy enforcement aligns data usage with organizational governance standards.
Threat detection analyzes anomalies such as unusual login behavior or compromised accounts. Contextual signals improve identification of malicious activity within cloud environments.
Policy enforcement ensures consistent application of security rules across cloud services. Controls remain active regardless of user location or access method.
Audit logging records cloud access events and policy actions for traceability. Logged activity supports governance reviews and compliance assessments.
Cloud environments introduce security challenges that traditional enterprise controls were not designed to manage.
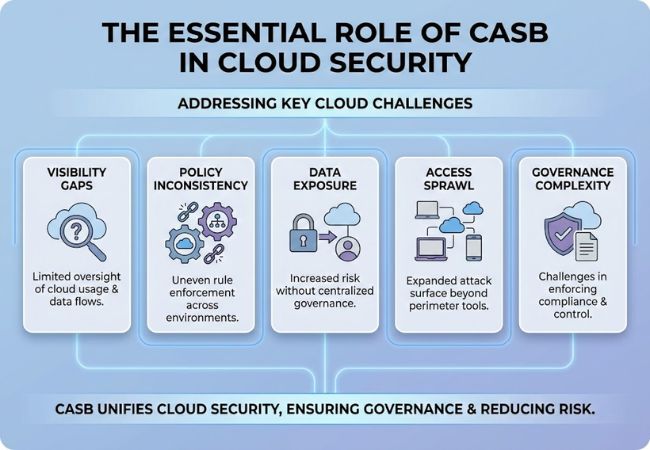
Different cloud environments expose applications and data through distinct service models, each requiring consistent access governance.
Software-as-a-Service environments deliver fully managed applications through third-party providers. User access and data interaction within these applications require external governance beyond traditional network controls.
Infrastructure-as-a-Service environments provide virtualized compute, storage, and networking resources. Access oversight focuses on how users interact with cloud-managed services rather than underlying hardware.
Platform-as-a-Service environments support application development on shared cloud platforms. Governance applies to service access and data handling without interfering with application logic.
Public cloud environments host services on shared infrastructure operated by external vendors. Centralized access control becomes necessary as services remain outside enterprise-owned boundaries.
Private cloud environments operate on dedicated infrastructure while exposing services through cloud-native interfaces. External access governance remains relevant when services are consumed beyond internal networks.
Different cloud security solutions focus on specific control layers, while CASB is designed to govern access, activity, and data usage directly within cloud services.
Selecting a CASB solution depends on how effectively it supports cloud governance, security consistency, and operational alignment.
Visibility coverage determines how clearly cloud application usage, user behavior, and data movement can be observed. Broad coverage reduces blind spots across sanctioned and unsanctioned cloud services.
Policy granularity defines how precisely access and data rules can be applied. Fine-grained controls allow enforcement based on identity, context, and service sensitivity.
Deployment flexibility reflects how easily the solution adapts to different cloud access scenarios. Support for multiple integration approaches reduces friction across environments.
Data awareness focuses on identifying and classifying sensitive information within cloud services. Contextual understanding of data enables accurate governance decisions.
Threat detection evaluates the ability to identify anomalous behavior and compromised access. Behavioral signals help surface risks that traditional controls may miss.
Integration support measures compatibility with existing identity, security, and cloud platforms. Strong integration reduces operational complexity and tooling overlap.
Operational scalability indicates how well the solution adapts to growing cloud usage. Sustainable performance and manageability prevent long-term security bottlenecks.
Cloud services have fundamentally changed where applications run and how data is accessed, reducing the effectiveness of traditional perimeter-based security controls. Governance over cloud access now requires visibility and policy enforcement beyond internal networks.
Cloud Access Security Brokers address this shift by introducing a dedicated layer focused on cloud service usage rather than infrastructure ownership. Access decisions, user behavior, and data interaction become manageable even when services operate outside enterprise boundaries.
As cloud adoption continues to expand across industries, structured control over cloud access remains a core security requirement. CASB fills this role by aligning cloud usage with security and governance expectations without disrupting how cloud services function.
A CASB solves the lack of visibility and control over how cloud services are accessed and used. Cloud activity becomes governable even when applications and data sit outside the enterprise network.
CASB is relevant for any organization that relies on cloud services to handle sensitive data. Complexity of cloud usage matters more than company size.
A CASB does not replace identity and access management systems. Authentication controls who can sign in, while CASB governs what happens inside cloud services after access is granted.
Most CASB solutions support governance across multiple cloud platforms. Centralized control prevents fragmented visibility when different providers are used together.
CASB remains necessary because Zero Trust and SASE describe security architectures rather than cloud access governance itself. Cloud service activity still requires a dedicated control layer.
