🚀 CloudSEK becomes first Indian origin cybersecurity company to receive investment from US state fund
Read more
Key Takeaways:
A banking trojan is a specialized form of trojan malware created to compromise online banking sessions and steal financial information. Unlike generic trojans, its primary objective is credential theft related to banks, payment platforms, and financial services.
These threats disguise themselves as legitimate software or hide inside trusted applications to avoid detection. Once active, they operate silently in the background while collecting sensitive data, making them particularly dangerous for everyday users and businesses alike.
A banking trojan works by infecting a device, activating during banking activity, and stealing financial data in the background.
The trojan enters through phishing emails, malicious links, fake software updates, or infected mobile apps. Users unknowingly install it by interacting with seemingly legitimate files or applications.
After installation, the malware stays dormant until the user accesses a banking website or app. This reduces detection and ensures it targets high-value data only.
The trojan steals credentials using keylogging, form grabbing, or browser injection. Advanced variants manipulate banking pages directly through man-in-the-browser attacks.
Many banking trojans bypass security controls such as two-factor authentication. They do this by intercepting OTPs, session cookies, or using fake login overlays on mobile devices.
Stolen data is sent to attacker-controlled servers using encrypted communication. This allows cybercriminals to access accounts or commit financial fraud remotely.
Attackers can remotely update the trojan or change its behavior. This keeps the malware effective against new security measures and banking protections.
Banking trojans collect a wide range of digital and behavioral data that enables attackers to take over accounts and execute financial fraud.
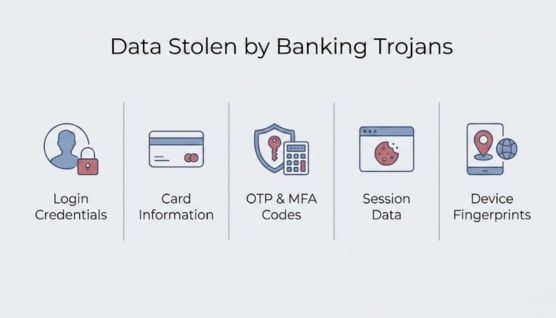
Commonly targeted data includes:
By combining these data points, attackers can impersonate legitimate users, bypass fraud detection systems, and carry out unauthorized financial activity.
Several banking trojans have been identified over the years, each using distinct techniques to steal financial data from users and organizations.
Zeus is one of the earliest banking trojans and introduced advanced browser injection methods. Many modern banking trojans are based on or inspired by its leaked source code.
TrickBot is a modular banking trojan capable of stealing credentials and downloading additional malware. It is commonly used in large-scale financial and enterprise attacks.
Emotet began as a banking trojan focused on credential theft but later evolved into a malware distribution platform. It is often used to deliver other banking trojans and ransomware.
Dridex primarily targets banking credentials through phishing emails and malicious document attachments. It focuses on corporate and high-value financial targets.
Mobile banking trojans mainly target Android devices using fake login overlays and SMS interception. These trojans are designed to steal app-based banking credentials and authentication codes.
Banking trojans target users and organizations that regularly access financial services online, especially where security awareness or controls are weak.
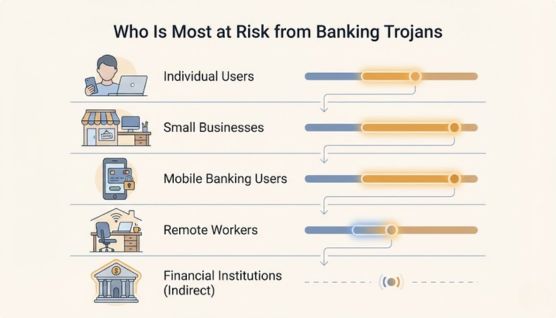
Everyday users who access online banking from personal computers or smartphones are common targets. Those who click phishing links or install unverified apps face higher risk.
Small businesses are attractive targets due to limited cybersecurity defenses. Compromised business accounts can lead to larger financial losses and data exposure.
Users who rely heavily on mobile banking apps are increasingly targeted by Android banking trojans. Malicious apps and fake overlays make mobile platforms a high-risk environment.
Remote workers often use personal devices and unsecured networks. This increases exposure to phishing-based banking trojan infections.
Banks are indirectly affected when customer accounts are compromised. Fraud losses, regulatory pressure, and reputational damage are common consequences.
Banking trojan infections are often subtle, but certain technical and behavioral indicators can signal compromise.
Unexpected transactions, failed login alerts, or changes to account settings may indicate stolen credentials. These actions often occur shortly after legitimate banking access.
Users may notice altered web pages, repeated login requests, or unexpected pop-ups during banking sessions. Mobile users may see fake screens that mimic real banking apps.
Slower system performance, high background data usage, or unexplained battery drain can indicate malicious activity. These symptoms occur as the trojan runs continuously in the background.
Antivirus warnings, disabled security tools, or blocked system updates may signal malware interference. Some banking trojans actively attempt to weaken device defenses.
Protecting against banking trojans depends on cautious behavior and basic security controls.
Do not click suspicious links or open unexpected email attachments. Most banking trojans rely on social engineering for initial access.
Keep operating systems, browsers, and apps up to date. Security patches close vulnerabilities exploited by malware.
Install trusted antivirus or mobile security software with real-time protection. These tools help detect and block banking trojans early.
Multi-factor authentication reduces risk even if credentials are stolen. Authenticator apps provide stronger protection than SMS codes.
Review transactions and alerts regularly. Early detection helps prevent significant financial loss.
Banks and organizations use layered security controls to detect fraud even when valid credentials are compromised.
Banks analyze login patterns, device behavior, and transaction anomalies. Unusual activity can trigger automatic security actions.
Real-time fraud detection systems flag suspicious transactions before they are completed. This helps reduce financial losses quickly.
Organizations deploy endpoint protection tools to detect malware on employee devices. This is especially important for remote and hybrid work environments.
Training users to recognize phishing attempts reduces infection rates. Human awareness remains a critical security layer.
Limiting access to financial systems reduces exposure. Role-based access and strong authentication help contain damage.
No, banking Trojans are malware that disguise themselves as legitimate software. Unlike viruses, they do not self-replicate but rely on user interaction.
Yes, Android devices are common targets for mobile banking trojans. These often spread through malicious apps and fake overlays.
Some advanced banking trojans can intercept OTPs or hijack active sessions. This allows attackers to bypass certain authentication methods.
Antivirus tools help, but they are not foolproof against new or modified trojans. Layered security and user awareness are also required.
Disconnect the device from the internet and contact your bank immediately. Then scan the device and change all banking credentials.
Banking trojans are designed to silently steal financial data by exploiting user trust and weak security practices.
Understanding how they work and recognizing early warning signs are critical to reducing risk. With cautious behavior and layered security controls, both individuals and organizations can significantly limit their impact.
