🚀 CloudSEK becomes first Indian origin cybersecurity company to receive investment from US state fund
Read more
API security is the practice of protecting APIs from unauthorized access, misuse, and cyberattacks. It safeguards endpoints and data flows by enforcing authentication and authorization controls.
Different API types such as REST, Web, and Cloud APIs require tailored security measures based on their structure and usage environment. These variations affect how identity, validation, and access policies are applied.
Modern API threats include BOLA, broken authentication, bot traffic, and shadow APIs. Effective protection relies on strong design-time controls, runtime defense mechanisms, governance, and automated testing.
API security works by validating identity, filtering malicious traffic, and enforcing strict access controls to protect API interactions. It ensures that only legitimate, authorized requests reach backend services.
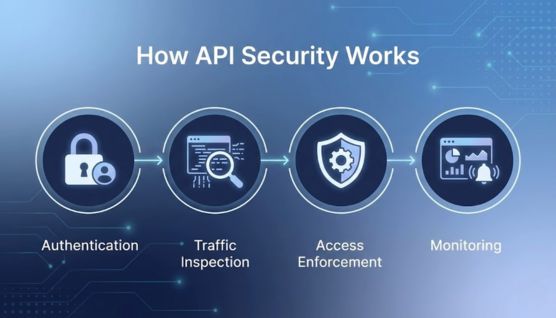
APIs confirm a requester’s identity through authentication and determine their allowed actions through authorization. OAuth 2.0, JWT, API keys, and mTLS are widely used for these controls.
Traffic inspection checks requests for malicious behavior or malformed payloads. Schema validation and input sanitization prevent injection and data manipulation attacks.
Monitoring tools track API activity to detect anomalies in real time. Runtime protection systems automatically block suspicious patterns and unauthorized usage.
A REST API is a resource-based interface that uses standard HTTP methods like GET, POST, PUT, and DELETE. It relies on stateless communication and structured data formats.
REST APIs expose resources via endpoints, allowing clients to interact with server data through predictable URL patterns. Their stateless nature makes them scalable but dependent on strict validation.
REST APIs require schema validation to prevent malformed payloads from reaching backend systems. They also depend heavily on proper authentication and authorization to protect resource access.
A Web API is a broad category of interfaces that allow software systems to communicate over the internet using HTTP, SOAP, JSON, XML, or other formats. These APIs often connect browsers, applications, and servers.
Web APIs may support multiple protocols and formats beyond REST’s constraints. This flexibility introduces more variables and increases the importance of input validation.
Web APIs require stronger filtering due to broader protocol support. They also rely on strict authentication and standardized message parsing to avoid injection and data leakage.
A Cloud API is an interface that allows applications to interact with cloud services, resources, and provider-specific functionalities. These APIs expose operations such as storage access, identity management, and compute provisioning.
Cloud APIs rely on provider-managed infrastructure and IAM policies to control access. They usually require signed requests and encrypted communication.
Cloud APIs depend on identity and permission systems to restrict access to sensitive resources. Misconfigured permissions are a common risk, making policy enforcement critical.
API security is built on identity controls, traffic protection layers, and enforcement points that regulate access and data flow.
An API gateway centralizes control by managing authentication, routing, and traffic filtering. It acts as the primary enforcement point for API access policies.
A WAF or API firewall filters malicious requests and blocks known attack patterns. It provides an additional layer of protection beyond basic gateway controls.
OAuth 2.0 manages delegated authorization, while JWT securely transmits identity information between systems. API keys identify clients, and mTLS provides mutual certificate-based authentication.
Schema validation ensures that requests match the expected structure and data types. It helps prevent injection attacks and malformed data from entering backend systems.
Rate limiting controls how many requests clients can send within a specific time. Throttling and quotas prevent abuse and keep systems stable during high-traffic periods.
API security is essential because APIs expose direct access points to data, business logic, and backend systems. As organizations expand their digital services, protecting these interfaces becomes critical to maintaining trust and preventing breaches.
APIs now power mobile apps, third-party integrations, automation tools, and internal systems. This widespread reliance increases exposure to potential misuse.
The number of APIs grows as businesses adopt microservices and cloud-native designs. Every new endpoint becomes a potential target for attackers.
APIs often provide direct access to sensitive information and critical workflows. Without proper protections, attackers can exploit weak endpoints to gain entry into core systems.
APIs face numerous threats that target logic, authentication flows, and weak configurations. Many of these threats appear in the OWASP API Security Top 10.
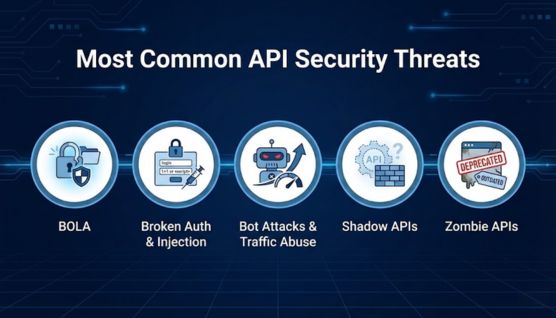
This list outlines the most critical API vulnerabilities, including issues like broken access control and insecure design. It helps developers identify and prioritize risk areas.
Broken Object Level Authorization (BOLA) allows attackers to access data they shouldn’t. Injection and broken authentication are also common causes of API breaches.
Bots can overload services, scrape sensitive data, or simulate legitimate clients. Traffic abuse leads to performance issues and security risks.
Shadow APIs are undocumented or forgotten endpoints, while zombie APIs exist long after they should be retired. Both introduce major blind spots in security programs.
APIs require layered security controls that address identity, data validation, traffic governance, and environmental risks. Each API type has unique characteristics that demand tailored protection methods.
REST APIs depend on strict schema validation to prevent malformed payloads from entering backend services. They also require strong authentication and proper resource-level authorization to block unauthorized access.
Web APIs must handle broader protocols and formats, making consistent message validation essential. They rely on robust authentication flows and standardized parsing rules to mitigate protocol-based exploits.
Cloud APIs rely heavily on identity and permission systems because they interact directly with provider-managed resources. Least-privilege IAM policies and continuous permission audits are crucial to reduce misconfiguration risks.
Centralized access rules ensure that only authorized clients and services interact with critical endpoints. Implementing least-privilege permissions across all API types minimizes unnecessary exposure.
Rate limits, quotas, and throttling prevent misuse and maintain stable performance during heavy traffic. These controls stop abusive clients and help absorb unexpected spikes.
Input validation detects harmful payloads before processing, while schema enforcement ensures every request matches expected structures. Together, they reduce the risk of injection and data corruption attacks.
TLS encryption protects all API traffic from interception and tampering. Encrypted channels ensure confidentiality and maintain data integrity across networks.
Behavior analysis tools identify anomalies and misuse patterns across API traffic. Continuous monitoring helps detect emerging threats before they escalate.
Security checks embedded in CI/CD pipelines prevent vulnerable APIs from reaching production. Automated testing ensures every new version follows consistent, secure design rules.
API security plays a central role in modern distributed systems by protecting the communication pathways between services. It ensures consistent enforcement of identity, access, and traffic controls across microservices, containers, and cloud environments.
Microservices rely heavily on APIs for internal communication, making each service boundary a potential attack surface. Consistent authentication and authorization help prevent lateral movement and unauthorized access.
Kubernetes environments depend on APIs for cluster operations and service communication. Network policies, sidecar proxies, and strong identity controls help secure these interactions.
Service meshes provide uniform security features such as encryption, identity, and traffic policies. By placing sidecar proxies next to each service, they enforce consistent rules across the entire architecture.
Hybrid and multi-cloud environments introduce multiple identity providers and networking layers. API security provides the unified governance needed to maintain visibility and enforce policies across diverse platforms.
API security tools use behavior analysis, policy enforcement, and discovery mechanisms to detect suspicious activity.
Machine learning detects anomalies by analyzing user patterns and identifying unusual behavior. These systems adapt to new threats over time.
Signature-based tools block known attack vectors, while policy-based enforcement restricts access to defined boundaries. The combination improves detection accuracy.
Discovery tools map all active, shadow, and deprecated APIs. This visibility helps organizations manage risks more effectively.
Risk assessment involves evaluating visibility, data sensitivity, and external dependencies.
Comprehensive visibility reduces blind spots across environments. Detecting shadow APIs prevents hidden vulnerabilities.
Classifying data helps determine which APIs require stronger protections. Sensitive data should always be encrypted and tightly controlled.
External APIs introduce risk through shared responsibility models. Assessing provider security and integration practices is essential.
Auditing and testing ensure APIs remain secure throughout their lifecycle.
Penetration testing identifies vulnerabilities through simulated attacks. Fuzzing sends malformed inputs to uncover logic and validation issues.
Contract tests verify that APIs behave as expected across environments. Schema validation prevents unexpected payloads from causing security issues.
Security gates automate checks during development and deployment. They ensure consistent protection across versions and releases.
API keys identify the client but do not provide strong authentication on their own. They should be combined with OAuth, JWT, or mTLS to ensure secure access control.
Shadow APIs are discovered through traffic analysis, specification checks, and automated discovery tools. Regular audits and inventory management help keep undocumented endpoints under control.
Yes, because Web APIs may support different protocols beyond REST, requiring broader validation and filtering. REST APIs depend heavily on strict schema enforcement and token-based authentication.
Broken access control, particularly BOLA, is the most frequently exploited API weakness. It often leads to exposure of sensitive data.
Yes, encryption is essential to prevent eavesdropping and ensure confidentiality. TLS should be used for all API communications, regardless of type or environment.
API security is essential for protecting modern applications, data flows, and interconnected systems. With clear visibility, strong access controls, and continuous monitoring, organizations can defend against evolving threats and maintain trustworthy digital services.
