🚀 CloudSEK becomes first Indian origin cybersecurity company to receive investment from US state fund
Read more
Key Takeaways:
An Adversary-in-the-Middle (AitM) attack represents a class of cyber threats focused on abusing authenticated user identity rather than compromising network infrastructure. Modern authentication systems make session trust a primary target, which places AitM attacks firmly in the identity-threat landscape.
AitM attacks align closely with cloud-first environments where browsers, identity providers, and token-based access control dominate authentication design. Single Sign-On platforms and web applications are especially exposed due to their reliance on persistent login sessions.
Operation within legitimate authentication flows separates AitM attacks from older interception techniques. Conceptual clarity at this level makes it easier to distinguish AitM attacks from traditional Man-in-the-Middle attacks, which target data transmission instead of identity trust.
Both attacks involve interception, but Adversary-in-the-Middle (AitM) attack and Man-in-the-Middle (MitM) attack differ in their attack surface, execution context, and impact on modern authentication systems.
An Adversary-in-the-Middle (AitM) attack works by placing a hidden intermediary inside the authentication flow so active user sessions can be hijacked without disrupting the login process.
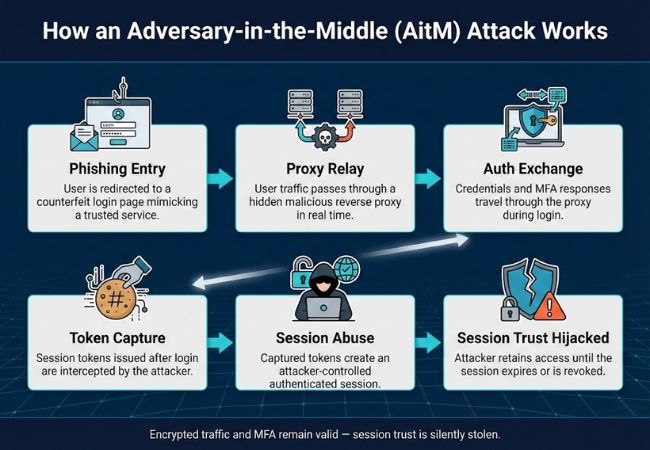
Attack execution begins by luring a user to a counterfeit login page designed to mirror a legitimate service. Visual familiarity and expected sign-in behavior encourage users to authenticate normally.
Traffic between the user and the real application is forwarded through a malicious reverse proxy in real time. Encrypted communication remains intact, which prevents visible warnings or broken functionality.
Login credentials and MFA responses traverse the proxy during authentication. Session cookies or access tokens issued after verification become exposed at this stage.
Captured session artifacts represent authenticated trust rather than raw credentials. Possession of these tokens allows attackers to impersonate users without repeating authentication.
Stolen tokens are reused to establish an independent authenticated session controlled by the attacker. Access continues until the session expires or is explicitly revoked.
Application trust remains bound to the stolen session until expiration or manual revocation. Encrypted transport and MFA validation stay intact while control over the session silently shifts to the attacker.
MFA bypass in AitM scenarios occurs after authentication succeeds, when session trust is reused without continuous identity verification.
Token targeting in AitM attacks centers on session artifacts that represent authenticated trust rather than credentials used during login.
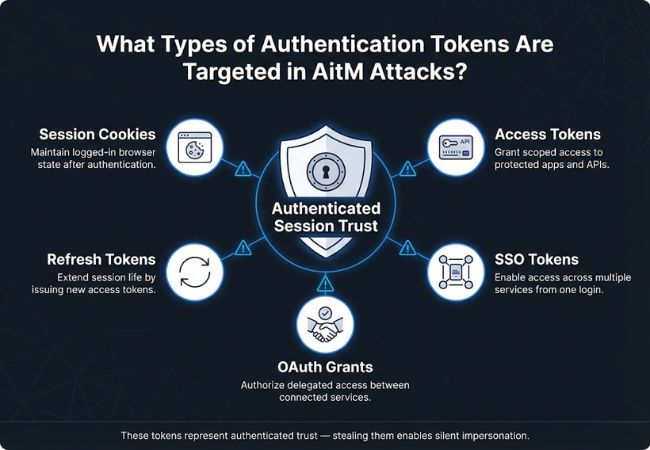
Session cookies maintain a logged-in state within a browser after authentication succeeds. Control of these cookies allows attackers to impersonate users instantly without triggering reauthentication.
Access tokens grant scoped permissions to applications and APIs on behalf of a user. Theft enables direct interaction with protected resources using the victim’s identity and privileges.
Refresh tokens extend session duration by issuing new access tokens without user involvement. Compromise increases persistence and allows attackers to maintain access long after initial login.
Single Sign-On tokens enable access to multiple applications through a single authentication event. Abuse creates broad lateral access across services tied to the same identity provider.
OAuth grants authorize delegated access between services once user consent is established. Misuse allows attackers to operate across connected applications without repeated identity checks.
Risk exposure from AitM attacks stems from abuse of legitimate session trust rather than exploitation of technical vulnerabilities.
Session token theft allows attackers to assume full control of user accounts without triggering authentication challenges. Legitimate access makes malicious activity difficult to distinguish from normal behavior.
Compromised sessions can be used to access administrative features or sensitive roles granted to the victim. Elevated permissions increase the scope and severity of the breach.
Single authenticated sessions often provide access to multiple connected applications and services. Attackers leverage inherited trust to move across environments without additional authentication.
Authorized access enables direct interaction with confidential data, internal systems, and cloud resources. Traditional data access controls often fail because requests appear legitimate.
Refresh tokens and long-lived sessions allow attackers to maintain access beyond the initial compromise. Extended persistence increases dwell time and the likelihood of secondary attacks.
Unauthorized access to regulated systems can result in violations of data protection and security compliance requirements. Audit trails often show valid user activity, complicating incident reporting and investigations.
Post-authentication abuse reduces the effectiveness of traditional security alerts and monitoring tools. Delayed detection increases attacker dwell time and amplifies overall damage.
Defense against AitM attacks requires controls that protect session trust before, during, and after authentication rather than relying on credentials alone.
Phishing-resistant authentication methods prevent credential and token replay even when login pages are impersonated. Hardware-backed and cryptographic authentication remove the attacker’s ability to reuse captured sessions.
Binding sessions to a specific device, browser, or cryptographic context limits token portability. Stolen session artifacts lose value when replayed from a different environment.
Context-aware access policies evaluate device posture, location, and risk signals before granting or maintaining access. Suspicious session context can trigger reauthentication or access denial.
Post-login session behavior monitoring detects anomalies that occur after authentication succeeds. Unusual access patterns, location changes, or API usage can indicate session abuse.
Short-lived access tokens reduce the window of opportunity for attackers. Frequent token rotation limits persistence even when session artifacts are compromised.
Centralized identity monitoring provides insight into authentication events across applications and services. Correlating session activity improves detection of lateral movement and abuse.
AitM attacks undermine security models that rely on identity as the primary control point rather than network-based trust boundaries.
Zero Trust architectures treat identity as the new perimeter for access decisions. AitM attacks exploit this shift by abusing trusted sessions instead of breaching infrastructure.
Cloud applications often inherit authentication decisions from identity providers without continuous revalidation. Compromised sessions remain trusted across services once access is granted.
Modern cloud platforms depend heavily on browser sessions and token-based access. Control over session artifacts enables attackers to bypass perimeter controls entirely.
Single identities frequently span multiple services, environments, and privilege levels. AitM attacks exploit this sprawl to expand impact without additional authentication events.
Zero Trust implementations that focus only on login hardening leave post-authentication activity insufficiently protected. Session abuse occurs after trust is already established.
Cloud environments amplify the impact of session compromise due to centralized identity and shared access models. A single stolen session can expose wide portions of an organization’s digital surface.
Adversary-in-the-Middle attacks highlight a shift in how account compromise occurs, moving away from password theft toward abuse of authenticated session trust. Encryption and traditional MFA remain important but are no longer sufficient on their own.
Modern authentication systems place significant trust in session tokens issued after login. Once that trust is transferred, attackers can operate with legitimate access unless additional controls are in place.
Reducing exposure to AitM attacks requires treating session integrity as a core security concern rather than a secondary control. Identity security strategies must extend beyond login validation to protect access throughout the entire session lifecycle.
Traditional phishing aims to steal credentials for later reuse, while AitM attacks intercept live authentication sessions in real time. Access is gained immediately after login by abusing session trust rather than stored passwords.
HTTPS encrypts data in transit but does not prevent attackers from relaying traffic through a malicious intermediary. Encrypted sessions remain vulnerable when authentication trust is established through a compromised proxy.
Standard MFA protects the login event but does not secure the session after authentication succeeds. Session replay remains possible unless authentication is phishing-resistant and bound to the user’s device or context.
Post-authentication monitoring can reveal anomalies such as unusual access patterns or context changes. Detection depends on visibility into session behavior rather than login failures.
Cloud-based users and organizations relying on SSO and browser-based authentication face higher exposure. A single compromised identity can provide access across multiple applications and services.
