🚀 CloudSEK becomes first Indian origin cybersecurity company to receive investment from US state fund
Read more
A VPN tunnel is a secure connection that sends your internet data through a protected path instead of the open internet. It creates a private link between your device and a VPN server, keeping your activity hidden from outsiders.
This secure tunnel protects data using encryption, which turns readable information into coded data. Even if data packets are intercepted on the public internet, they remain unreadable without the decryption key.
The term “tunnel” is used because your data travels safely inside this protected route while the public internet exists outside it. As a result, your IP address, browsing activity, and online communication stay private and secure.
A VPN tunnel works by continuously controlling how your internet traffic is packaged, protected, and sent across the public internet. While active, it forces all data to follow a secure route through a VPN server instead of a direct connection.
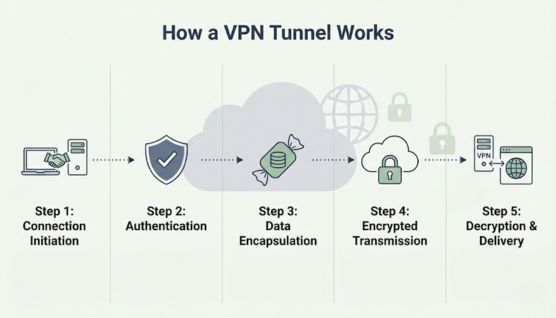
A VPN tunnel depends on several technologies that each handle a specific security or networking task. Instead of controlling the flow of data, these technologies define how protection, access, and transport are enforced.
Encryption is responsible for protecting data content from being read or altered. It ensures confidentiality by making intercepted traffic useless without the correct decryption key.
Authentication controls who is allowed to use the VPN tunnel. By verifying users and devices, it prevents unauthorized traffic from entering the secure connection.
Tunneling protocols define the rules for packaging and moving data across networks. They determine how stable, fast, and compatible the VPN tunnel will be across different devices and environments.
VPN tunneling types are determined by the protocol a virtual private network uses to move data between devices and servers. Each protocol solves a different problem, such as speed limitations, mobile stability, or network restrictions.
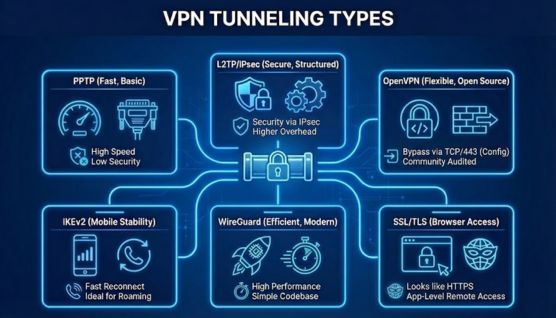
Because no single protocol fits every situation, VPN tunneling evolved over time to address changing security and performance needs.
PPTP represents the earliest approach to VPN tunneling and focuses on fast data transfer. Its simple design allows broad compatibility with older systems.
As security threats advanced, weaknesses in PPTP became difficult to ignore. Modern privacy requirements rarely align with its limited protection capabilities.
To improve security, L2TP introduced a structured tunneling method paired with IPsec encryption. This combination added authentication and data integrity checks missing from older protocols.
The added protection increases processing overhead. Networks that value standardized security controls often accept this trade-off.
OpenVPN addressed flexibility and transparency by using open-source architecture. Public code review strengthened trust and long-term security reliability.
Support for multiple transport methods allows OpenVPN to function across restricted networks. Environments with firewalls or public Wi-Fi commonly rely on it.
Mobile connectivity introduced new challenges, particularly frequent network changes. IKEv2 was designed to maintain tunnel stability during these transitions.
Fast reconnection improves reliability on smartphones and tablets. Operating systems often include native support due to this advantage.
As performance demands increased, WireGuard focused on efficiency and simplicity. A smaller codebase reduced complexity and potential attack surfaces.
Modern cryptographic design delivers high speeds without sacrificing security. Performance-focused deployments increasingly adopt WireGuard.
Some environments block traditional VPN protocols entirely. SSL/TLS tunneling works around this limitation by using the same transport model as HTTPS traffic.
Browser-based access becomes possible without full-device tunneling. Remote system access remains the primary use case.
VPN split tunneling is a feature that controls which traffic passes through the encrypted tunnel of a virtual private network and which traffic connects directly to the internet. This setup allows sensitive data to remain protected while less critical traffic bypasses the VPN.
The tunnel creates two simultaneous paths for data transmission. One encrypted path carries sensitive activity such as online banking or work applications, while a direct path handles general browsing, gaming, or streaming.
Split tunneling improves connection speed and preserves access to local resources like printers or internal networks. Reduced protection applies to traffic routed outside the VPN tunnel, making careful traffic selection necessary.
A VPN tunnel plays a critical role in protecting data and identity while using the internet.
VPN tunneling and encryption work together but serve different roles in securing internet communication. One controls how data travels, while the other controls how data is protected.
VPN tunnels are most commonly used in situations where internet connections are not fully trusted. They help protect data when people work, travel, or connect through shared networks.
People working from home often use VPN tunnels to reach internal company systems securely. This keeps work data protected even when the connection runs through a home or public network.
Businesses use VPN tunnels to link offices, servers, and remote staff over long distances. These tunnels allow private communication without exposing internal systems to the open internet.
Public Wi-Fi in places like cafés, airports, or hotels carries higher security risks. VPN tunnels protect logins, messages, and browsing activity from being intercepted on these networks.
Phones and laptops frequently switch between Wi-Fi and mobile data while traveling. VPN tunnels keep connections protected during these network changes and reduce exposure to attacks.
Some networks limit access to specific services or websites. VPN tunnels allow secure access to approved resources while keeping traffic protected from local network monitoring.
You can check whether a VPN tunnel is working by comparing your IP address before and after connecting to the VPN. If the IP address changes and matches the VPN server location, traffic is passing through the tunnel.
VPN tunneling is legal in most countries and commonly used for privacy and security. Some regions restrict or regulate VPN usage, so local laws should always be checked.
A VPN tunnel can slightly reduce speed because data is encrypted and routed through a VPN server. The impact depends on the protocol used, server distance, and network quality.
Strong VPN tunnels are very difficult to compromise when modern protocols and encryption are used. Weak configurations or outdated software increase security risks.
No, different VPN services support different tunneling protocols with varying performance and security levels. Many providers allow users to switch between protocols based on their needs.
A VPN tunnel plays a central role in keeping internet communication private and secure in everyday use. By understanding how VPN tunneling works, the available types, and configurations like split tunneling, users can make better decisions about protecting their data.
Whether used for remote work, public Wi-Fi, or personal privacy, VPN tunnels provide control over how traffic moves across the internet. Choosing the right tunneling method and setup helps balance security, speed, and usability in real-world situations.
