🚀 CloudSEK becomes first Indian origin cybersecurity company to receive investment from US state fund
Read more
A virtual firewall is a software-based security system that monitors and controls network traffic within virtual or cloud environments. It performs the same core function as a traditional firewall but does not rely on physical hardware.
Instead of being deployed as a standalone device, a virtual firewall runs inside virtual machines or alongside cloud workloads. It inspects incoming and outgoing traffic and allows or blocks connections based on defined security rules.
Virtual firewalls are commonly used in cloud and virtualized systems where networks change frequently. They help protect applications and data even as workloads scale, move, or are dynamically created.
A virtual firewall functions by gaining visibility into network traffic flowing between systems. Each connection request is evaluated before it is allowed to proceed.
Based on predefined security rules, the firewall determines whether traffic should be permitted, blocked, or flagged for review. This decision-making process happens continuously to maintain protection as environments change.
Virtual firewalls are deployed wherever digital systems communicate without passing through physical network devices. Their placement depends on the type of environment being protected.
In cloud platforms, applications are frequently created, scaled, and updated. Virtual firewalls operate close to these workloads, enforcing traffic controls without introducing hardware dependencies.
Within virtualized data centers, multiple systems share the same internal network. Virtual firewalls regulate communication between these systems to prevent unrestricted access.
In hybrid setups that combine cloud and on-premises infrastructure, virtual firewalls help apply consistent security policies across both environments.
Virtual firewalls inspect traffic based on how systems communicate rather than only where traffic enters or exits the network.
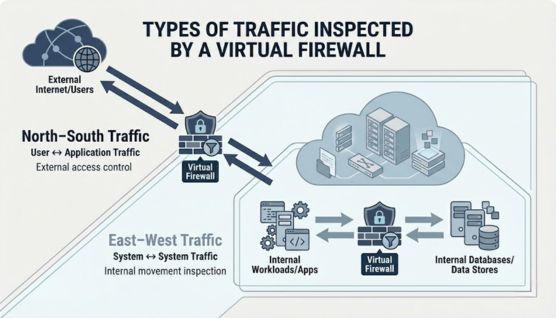
North–south traffic refers to data moving between users and applications, such as access from the internet. Monitoring this traffic helps control entry points and limit external exposure.
East–west traffic occurs when systems within the same environment communicate with each other. Inspecting this traffic helps detect and restrict unauthorized internal movement.
Virtual firewalls and hardware firewalls serve the same purpose but operate in very different ways. The key difference lies in how they are deployed, managed, and scaled.
In cloud environments, systems rarely stay in one place. Applications scale, move, and connect in ways that make fixed network boundaries unreliable as a security control.
Cloud workloads shift as demand changes or systems update. When security depends on a fixed position in the network, gaps appear as soon as those workloads move.
Much of the activity in cloud environments happens between internal systems. Without controls inside the environment, this traffic remains largely unchecked.
Security issues do not always enter from the outside. Once inside, unrestricted internal connections allow problems to spread faster than expected.
Cloud infrastructure grows and shrinks continuously. Security must scale at the same pace, without introducing delays or manual overhead.
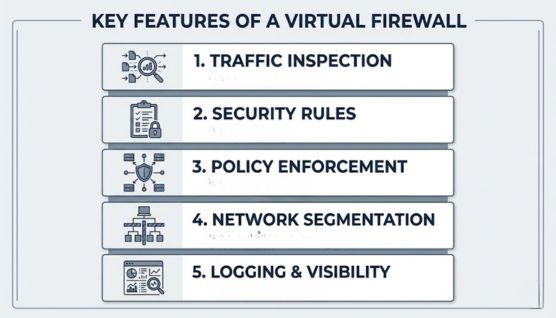
A virtual firewall inspects network traffic moving between virtual machines, applications, and cloud services. Connection attributes such as source, destination, protocol, and behavior are evaluated to identify legitimate or suspicious activity.
Network access is controlled through predefined security rules that define allowed and blocked connections. Rule updates can be applied quickly to reflect changes in workloads or network architecture.
Security policies remain enforced across all workloads regardless of where they are deployed. Controls stay intact during scaling, migration, or infrastructure changes.
Communication between systems is restricted based on role, application purpose, or trust level. Limiting internal access reduces exposure and restricts lateral movement.
Traffic activity and enforcement actions are recorded for ongoing monitoring and review. Log data supports auditing, troubleshooting, and incident investigation.
Virtual firewalls are typically used when organizations need precise control over how systems communicate in complex, software-driven environments. These use cases focus on day-to-day operational needs rather than general security benefits.
Virtual firewalls are often used to control which services can reach specific applications. This helps ensure only approved systems or users can access sensitive workloads.
Teams use virtual firewalls to separate development, testing, and production environments. This prevents accidental access across environments that serve different purposes.
In modern architectures, applications frequently communicate with each other through APIs or internal services. Virtual firewalls help regulate these connections and restrict unnecessary communication paths.
Service providers use virtual firewalls to isolate customer environments running on shared infrastructure. This keeps each tenant’s traffic separate and prevents cross-environment impact.
Virtual firewalls fit naturally into environments where systems are no longer fixed or predictable. By placing control closer to workloads instead of relying only on network edges, they help manage how applications and services interact as infrastructure changes.
As cloud and hybrid setups continue to grow, controlling internal traffic becomes just as important as blocking external threats. Virtual firewalls provide a practical way to maintain visibility and control in environments where traditional boundaries no longer define security.
