🚀 CloudSEK becomes first Indian origin cybersecurity company to receive investment from US state fund
Read more
Key Takeaways
Darknets are encrypted, private overlay networks built on top of the internet that require specialized software or configurations to access. They are intentionally hidden from search engines and standard browsers, which allows users and hosting services to operate with a high degree of anonymity.
Unlike the surface web, which is publicly indexed, darknets are designed to resist tracking, monitoring, and attribution. This separation is structural rather than accidental and exists to prevent identities and locations from being easily linked to online activity.
Use of these networks is often associated with illegal marketplaces and cybercrime, but activity within them is not limited to criminal purposes. Journalists, activists, and whistleblowers rely on systems such as Tor to communicate securely, bypass censorship, and protect sensitive sources.
Dark markets are online marketplaces built specifically to enable commerce without direct identity verification or traditional regulation. Their structure mirrors familiar e-commerce platforms, with product listings, search functions, and vendor storefronts organized for scale and repeat transactions.
Goods and services offered on these platforms commonly include drugs, stolen data, counterfeit documents, and cybercrime tools that cannot be traded openly. The absence of legal enforcement shifts market behavior toward reputation, speed, and operational reliability rather than branding or compliance.
Trust inside dark markets is created through vendor ratings, transaction histories, and escrow-based payment flows rather than contracts or consumer protection laws. This system allows markets to function temporarily but also makes them fragile, prone to scams, sudden shutdowns, and internal abuse.
Darknets work by separating a user’s identity from their online activity at the network level rather than at the website level. Connections are routed indirectly, which prevents observers from seeing a clear link between who is communicating and where the communication ends.
Traffic moves through multiple encrypted relays instead of traveling directly from a device to a server. No single relay has enough information to reconstruct the full path or identify both ends of the connection.
This routing model is implemented through systems such as Tor, which supports hidden services and anonymized access points. As a result, both users and services can operate without exposing IP addresses, physical locations, or hosting infrastructure.
Dark markets operate through a repeatable transaction process that replaces legal enforcement with platform controls and community-based trust signals.
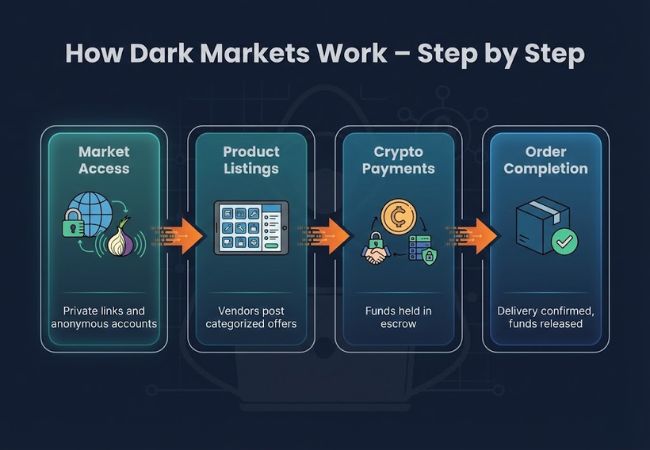
Users find marketplace addresses through private forums, mirrors, or invitation-based channels rather than public search engines. Accounts are created without personal identifiers to reduce traceability.
Vendors publish categorized listings that include pricing, delivery terms, and service details. Buyers compare options using seller reputation and transaction history rather than brand identity.
Transactions are conducted using cryptocurrencies such as Bitcoin or privacy-focused alternatives like Monero instead of banks or card networks. Payments are held in escrow until order conditions are met.
Funds are released to the vendor after the buyer confirms delivery. Disputes are resolved internally according to marketplace rules rather than consumer protection laws.
Darknets and dark markets support a wide range of activities that extend beyond a single use case. Their applications vary depending on whether the goal is private communication, information access, or anonymous commerce.
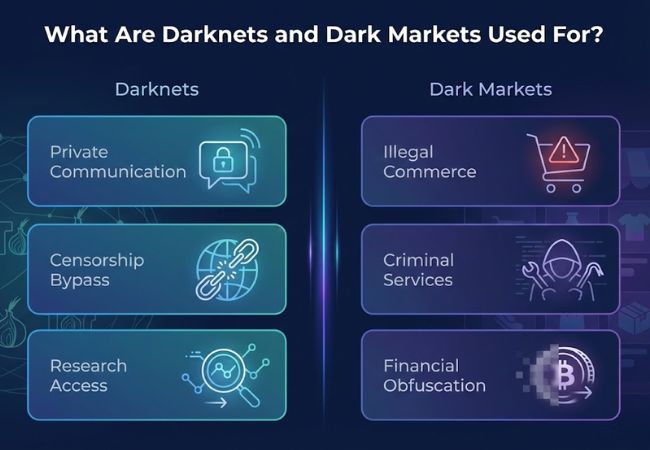
Darknets are used for secure messaging and file sharing in situations where identity exposure carries personal or political risk. Journalists, activists, and whistleblowers rely on these networks to protect sources and sensitive information.
Users in restricted regions turn to darknets to reach blocked websites and information sources. This use case focuses on access rather than anonymity for criminal purposes.
Security researchers and analysts monitor darknets to study emerging threats, malware trends, and criminal coordination. Intelligence gathered from these spaces often informs cybersecurity defenses and law enforcement investigations.
Dark markets are primarily used to trade goods that cannot be sold through regulated platforms. Drugs, stolen credentials, counterfeit documents, and prohibited digital assets dominate these marketplaces.
Many dark markets facilitate services rather than physical goods. Offerings commonly include hacking-for-hire, fraud assistance, ransomware tools, and money laundering support.
Cryptocurrency-based transactions on dark markets are used to obscure payment trails and avoid traditional financial controls. This ties dark markets closely to illicit finance and regulatory enforcement efforts.
Use of darknets and dark markets introduces multiple layers of risk that extend beyond privacy concerns. These risks affect users legally, financially, and technically, regardless of intent or experience level.
Many activities conducted on dark markets violate national and international laws. Even passive participation or accidental involvement can result in investigation, arrest, or prosecution.
Scams are common across dark markets due to the absence of enforceable contracts or consumer protections. Exit scams, fake listings, and manipulated reviews frequently lead to financial loss.
Malware, phishing schemes, and compromised downloads are widespread on darknet platforms. Users often expose their devices to surveillance tools, keyloggers, or ransomware without realizing it.
Operational mistakes can reveal identities despite anonymity tools. Poor configuration, reused credentials, or careless communication can connect darknet activity to real-world identities.
Dark markets rarely operate long-term without disruption. Sudden shutdowns, internal theft, or law enforcement seizures can cause users to lose funds held in escrow.
Darknets are continuously monitored by law enforcement and intelligence agencies. Undercover operations and blockchain analysis increasingly reduce the perceived safety of anonymous participation.
Law enforcement efforts against dark markets focus on disrupting infrastructure, identifying participants, and following financial trails rather than relying on traditional policing methods.
Authorities target marketplace operators by locating servers, exploiting configuration errors, or seizing hosting infrastructure. Coordinated international operations often result in sites being taken offline and administrators arrested.
Investigators pose as buyers, vendors, or service providers to gather intelligence from inside dark markets. Long-term infiltration helps map vendor networks, payment flows, and trust relationships.
Cryptocurrency transactions are analyzed to trace funds moving through wallets and exchanges. Even when privacy tools are used, transaction patterns can expose links between darknet activity and real-world identities.
Law enforcement frequently relies on user errors rather than technical failures. Reused usernames, poor encryption practices, or interactions outside darknet environments can reveal identities.
Exchanges, hosting providers, and payment services are regulated to limit how illicit funds are converted or moved. These controls reduce exit points for darknet profits and increase exposure risk.
Darknets exist because the modern internet does not offer privacy by default. Encrypted routing and hidden services fill that gap, enabling communication and access in situations where exposure can lead to real harm.
Commercial activity changes the nature of these networks. Once buying and selling enter the picture, anonymity becomes a tool for avoiding oversight rather than protecting speech, which is why dark markets tend to concentrate fraud, criminal services, and rapid platform collapse.
Looking at darknets and dark markets as separate layers helps clarify the conversation. The technology itself is neutral, but its outcomes depend entirely on how anonymity is applied, monitored, and abused in practice.
Accessing darknets is legal in many countries, but legality depends on jurisdiction and intent. Illegal activity conducted within these networks remains subject to prosecution.
Most known dark markets facilitate the sale of illegal goods or services. Market structure itself is not illegal, but real-world usage almost always violates existing laws.
Anonymity tools reduce exposure but do not guarantee protection. Technical mistakes, behavioral patterns, or financial tracing can still reveal identities.
Cryptocurrencies allow transactions without banks or direct identity checks. This reduces oversight while enabling global payments.
Darknets are actively monitored through infiltration, technical analysis, and financial tracking. Networks such as Tor do not prevent investigation when operational errors occur.
