🚀 CloudSEK becomes first Indian origin cybersecurity company to receive investment from US state fund
Read more
Key Takeaways:
Cyberthreat Intelligence is the practice of collecting and analyzing threat data to understand attacker behavior, motivations, and capabilities. It turns unstructured information such as TTPs, IOCs, and infrastructure telemetry into insights that guide security decisions.
The goal of CTI is to help organizations anticipate threats instead of reacting after damage occurs. It achieves this by contextualizing activities across threat actors, campaigns, and attack surfaces.
Security teams use CTI to strengthen detections, enhance incident response, and improve long term risk planning. CTI becomes more valuable when it is aligned with frameworks like MITRE ATT&CK because this allows analysts to map adversary techniques with precision.
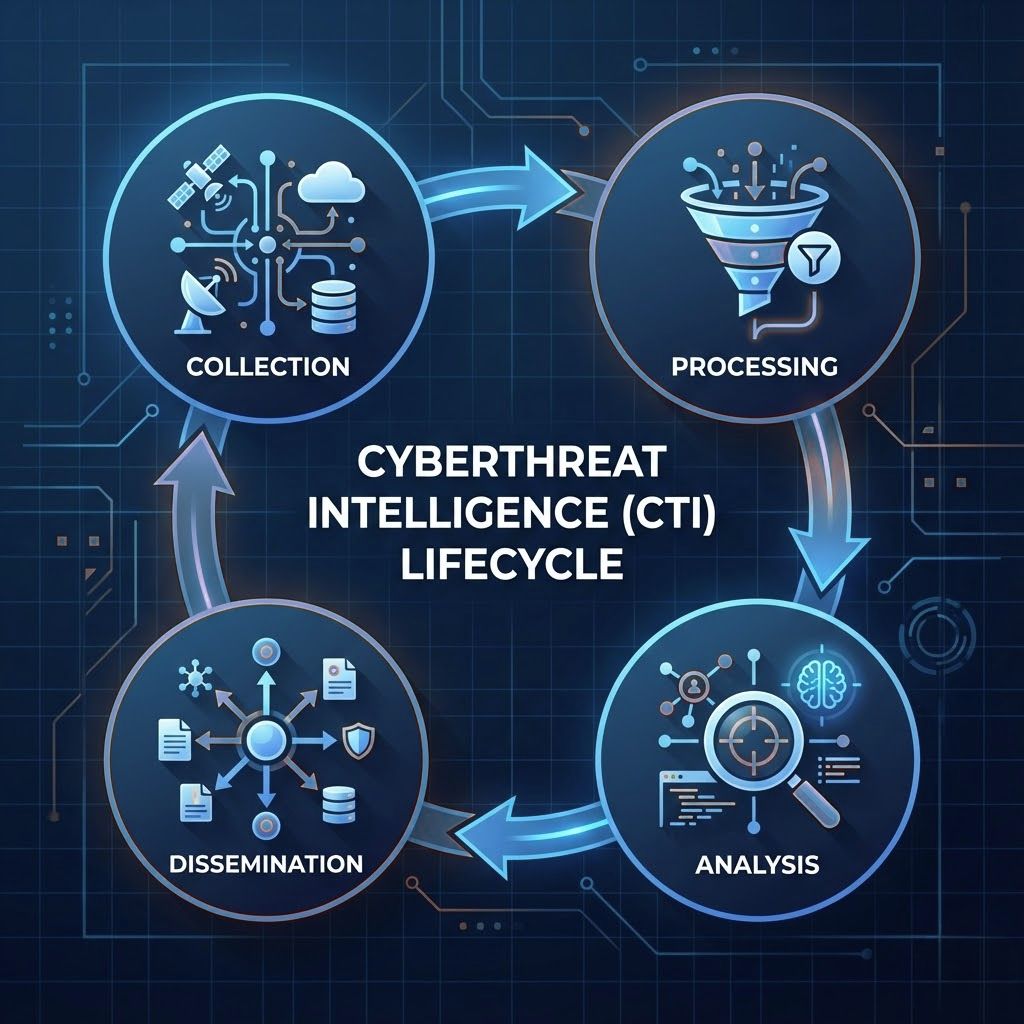
CTI works by following the intelligence lifecycle which includes collection, processing, analysis, and dissemination. Each stage refines raw information into relevant intelligence for different operational layers.
Collection begins across sources such as OSINT, dark web forums, malware sandboxes, and internal infrastructure logs. This diverse data union helps teams identify attacker movements that may remain unnoticed in isolated systems.
During analysis, threat patterns are correlated with known TTPs and mapped to adversary profiles to uncover intent. The final intelligence is shared with leadership, SOC analysts, and IR teams so the insights can be operationalized within SIEM and SOAR environments.
Cyberthreat Intelligence is categorized into four types, each providing a distinct level of context and visibility. These categories allow organizations to apply intelligence in strategic planning as well as real time defense.
Strategic CTI provides executive level awareness of geopolitical risks, sector trends, and long term threat developments. It guides leadership in shaping security policies and investment decisions.
Tactical CTI focuses on adversary tactics, techniques, and procedures used during active operations. It equips SOC teams with behavioral patterns they can convert into detection logic.
Operational CTI reveals details about ongoing or emerging threat campaigns that directly target an organization or industry. It supports IR teams by highlighting attacker tools, timelines, and objectives.
Technical CTI delivers granular indicators such as malicious hashes, domains, and file signatures. It enables rapid blocking of threats at control points such as firewalls and SIEM rules.
Strategic CTI focuses on long-term risks that shape security governance and investment decisions. It evaluates geopolitical conditions, threat actor motives, and industry-specific trends to help leadership anticipate future challenges.
Risk themes identify broader forces that may influence attacker motivations or operational shifts. These insights help executives align security priorities with evolving external conditions.
Industry trends highlight attack patterns targeting similar sectors or technologies. Leadership uses these insights to predict which business units may require additional protective measures.
Policy insights assess regulatory developments and compliance pressures that affect enterprise security planning. This ensures strategic decisions support both resilience and governance requirements.
Tactical CTI analyzes the behaviors and techniques attackers use during operations. It gives SOC teams the information needed to refine detections and strengthen monitoring systems.
Adversary TTP analysis maps observed behaviors to ATT&CK techniques. SOC analysts use these mappings to enhance visibility across the attack chain.
Detection logic translates behavioral insights into signatures and alert rules that improve SIEM performance. This process reduces false positives and strengthens detection depth.
Defense focus highlights which assets or processes require additional attention based on attacker behavior. It enables SOC leaders to prioritize workflow adjustments that strengthen readiness.
Operational CTI offers information about active campaigns that may directly target the organization or its sector. It bridges the gap between broad strategic awareness and technical indicators needed during investigations.
Campaign data identifies threat actor groups, their active tools, and their operational preferences. It helps responders anticipate how attacks may unfold within their environment.
Activity timeline analysis reveals how quickly adversaries execute different stages of an attack. This gives responders context on when to expect escalation or lateral movement.
Threat intent analysis explains why attackers are pursuing a particular target or industry. It helps teams calibrate their response strategies based on adversary objectives.
Technical CTI provides the shortest-lived yet most actionable intelligence for frontline defenders. It offers detailed indicators that feed directly into detection and prevention systems.
IOC analysis collects hashes, IPs, domains, and URLs associated with malicious activity. These indicators enhance SIEM, EDR, and firewall detection accuracy.
Malware artifact analysis examines code fragments and behavioral signatures to identify malicious files. These insights help analysts recognize new or modified malware strains.
Infrastructure signals reveal command and control servers, distribution points, and hosting environments used for attacks. This information helps teams disrupt adversary communication channels.
The four CTI types differ in purpose, audience, data depth, and time sensitivity. Understanding these differences helps organizations apply intelligence effectively across strategic decision making and operational defense.
The four CTI types strengthen security by offering complementary layers of insight that address both strategic and operational needs.
Attack Forecasting: Strategic and tactical CTI provide long-term clarity on industry risks and adversary behaviors.
Threat Containment: Operational and technical CTI enhance rapid response by revealing active threats and actionable indicators.
Organizations use CTI to enrich alerts, uncover hidden threats, and reduce investigation time within their SOC workflows.
Alert Precision: Tactical and technical CTI improve SIEM quality by adding behavioral patterns and verified indicators.
Investigation Depth: Operational CTI provides campaign context that helps responders understand attacker goals and escalation paths.
A strong CTI solution should combine accurate intelligence, wide data coverage, and seamless integration into existing security tools.
The solution should source intelligence from diverse repositories, including malware labs, dark web communities, and network telemetry.
It should provide enriched insights that explain attacker motives, infrastructure relationships, and emerging patterns.
The platform must integrate with SIEM, SOAR, EDR, and threat hunting tools to make intelligence immediately actionable.
It should generate clear reports for executives and operational teams using ATT&CK mappings and contextual narratives.
Technical CTI is the most actionable because it provides specific indicators that can be blocked immediately.
Executives and CISOs use strategic CTI to guide long-term planning and investment decisions.
Threat data is raw information, while CTI contextualizes it into insights that support decision-making.
Yes, operational CTI provides campaign intelligence that accelerates investigation and containment.
Tactical and operational intelligence reveal adversary behaviors that hunters use to uncover hidden activity.
CloudSEK is an AI-powered threat intelligence platform that delivers real-time visibility across digital assets, external infrastructure, and adversary ecosystems. Its Unified Intelligence engine correlates dark web activity, attack surface insights, and infrastructure anomalies to predict threats before they materialize.
CloudSEK provides contextual intelligence that links exposed assets with attacker movements to show how threat actors may exploit vulnerabilities. This helps organizations prioritize risks that align with adversary intent rather than relying on isolated alerts.
The platform integrates seamlessly with SOC environments so security teams can deploy enriched intelligence into SIEM, SOAR, and EDR systems. CloudSEK enhances operational readiness by delivering continuous monitoring and actionable insights across evolving threat landscapes.
