🚀 CloudSEK becomes first Indian origin cybersecurity company to receive investment from US state fund
Read more
Key Takeaways:
Healthcare is targeted more than any other sector because attackers can monetize patient records and exploit outdated clinical systems that lack modern security controls. The combination of legacy infrastructure and critical service availability makes healthcare highly vulnerable to extortion-driven attacks.
Manufacturing attracts cybercriminals due to interconnected OT–IT environments that create hidden vulnerabilities across production lines. Attackers exploit these gaps to disrupt operations and supply chains, knowing that downtime creates strong leverage for ransom demands.
Financial services face continuous targeting because they store high-value identity data and process sensitive monetary transactions across digital platforms. Criminals use credential theft, phishing, and malware to bypass defenses and exploit the expanding landscape of online banking and fintech services.
Industries are targeted based on data value, operational urgency, and the ease of exploiting vulnerabilities.
Healthcare remains a prime target due to its sensitive patient data and operational urgency. Attackers exploit outdated medical systems and fragmented networks.
Threats:
Mitigation Approach:
Healthcare systems can reduce risk by segmenting networks and securing legacy systems. Regular patching and multi-factor authentication further strengthen overall resilience.
Manufacturers face rising attacks because production halts create high leverage. Their OT/IT convergence exposes many weak access points.
Threats:
Mitigation Approach:
Manufacturers benefit from isolating operational technology and securing vendor access. Continuous monitoring of industrial systems also reduces hidden vulnerabilities.
Financial institutions handle money and identity data, making them lucrative targets. Attackers seek direct monetary gain through fraud and account takeovers.
Threats:
Mitigation Approach:
Financial firms strengthen protection by enforcing strong authentication and real-time fraud detection. Behavioral analytics further helps identify suspicious activity quickly.
Retailers face high attack volumes due to constant online transactions. Cybercriminals exploit checkout systems and customer accounts.
Threats:
Mitigation Approach:
Retailers can enhance security with bot management, strong authentication, and secure payment gateways. Regular audits of third-party integrations also reduce exposure.
Tech companies store intellectual property and support massive user ecosystems. Attackers aim to infiltrate their platforms for wider exploitation.
Threats:
Mitigation Approach:
Tech firms improve safety by tightening API controls and securing build environments. Access governance and key rotation also limit unauthorized entry.
Government agencies manage essential citizen services and sensitive databases. Attackers target them to cause disruption and extract strategic information.
Threats:
Mitigation Approach:
Upgrading legacy infrastructure and enforcing strict identity controls enhances protection. Agencies benefit from continuous monitoring to detect early intrusion attempts.
Energy systems power national infrastructure, making them high-impact targets. Attackers focus on causing operational instability and long downtime.
Threats:
Mitigation Approach:
Energy operators strengthen defenses by isolating critical systems and monitoring for unusual activity. Partnering with threat-intelligence services also improves early detection.
Schools and universities face rising attacks due to limited budgets and large user networks. Research institutions are additionally targeted for intellectual property.
Threats:
Mitigation Approach:
Educational institutions can improve safety through MFA adoption and awareness training. Strengthening access controls for remote learning platforms also lowers risk.
Transportation providers rely on real-time digital coordination, making disruptions costly. Attackers exploit system interconnectivity to maximize impact.
Threats:
Mitigation Approach:
Organizations safeguard operations by segmenting network layers and monitoring supply-chain dependencies. Automated alerts help detect anomalies in routing systems.
SMBs and service firms lack advanced cybersecurity resources, making them frequent targets. Attackers exploit weak authentication and outdated tools.
Threats:
Mitigation Approach:
Small businesses benefit from adopting low-cost security layers like MFA and endpoint protection. Regular backups and staff training further reduce breach impact.
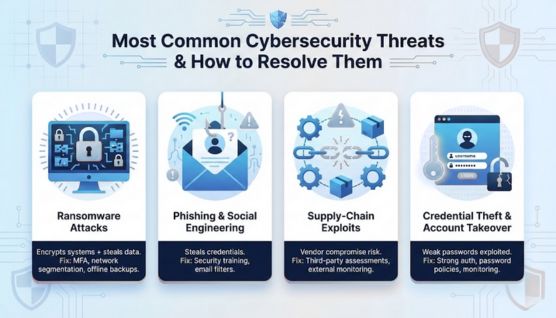
Ransomware encrypts systems and steals data to pressure victims into paying. Organizations can reduce risk by enforcing MFA, segmenting networks, and maintaining offline backups.
Phishing remains the easiest way for attackers to steal credentials. Training programs and email security filters significantly lower success rates.
Attackers compromise vendors to access larger targets. Regular third-party assessments and continuous external attack surface monitoring reduce this exposure.
Weak or reused passwords make breaches easier. Strong authentication, password policies, and monitoring tools help prevent unauthorized access.
Modern organizations must strengthen cybersecurity posture through layered, proactive defense strategies.
Healthcare experienced the highest number of breaches due to its valuable data and aging infrastructure. Attackers exploited these weaknesses for ransomware and extortion.
Manufacturing operations cannot afford downtime, giving attackers leverage. OT systems are also harder to secure, creating easy entry points.
They store money, identity data, and payment information. This makes them high-reward environments for credential theft and fraud.
Yes, SMBs are frequently targeted because they lack dedicated security teams. Their slower response times increase attacker success.
Human error is still a major cause of breaches. Training and awareness programs drastically reduce this risk.
CloudSEK provides continuous AI-driven threat intelligence by monitoring an organization’s external digital footprint across surface, deep, and dark web sources. This real-time detection helps identify data leaks, exposed credentials, brand impersonation, and targeted threats earlier.
Its external attack surface monitoring (EASM) platform automatically maps internet-facing assets such as domains, APIs, cloud instances, and shadow IT. CloudSEK then flags misconfigurations or vulnerabilities before attackers can exploit them for initial access.
When risks are discovered, CloudSEK delivers contextual alerts with clear remediation actions based on severity and exploitability. This reduces investigation time and strengthens incident response by enabling faster, more accurate decision-making.
