🚀 CloudSEK becomes first Indian origin cybersecurity company to receive investment from US state fund
Read more
Key Takeaways:
A security threat assessment evaluates potential threats, weaknesses, and likely impacts across an organization’s assets. It helps teams implement targeted defenses before attackers exploit vulnerabilities.
A threat assessment identifies critical assets, analyzes exposures, and scores risks to guide remediation priority. This ensures teams address the highest-impact weaknesses first.
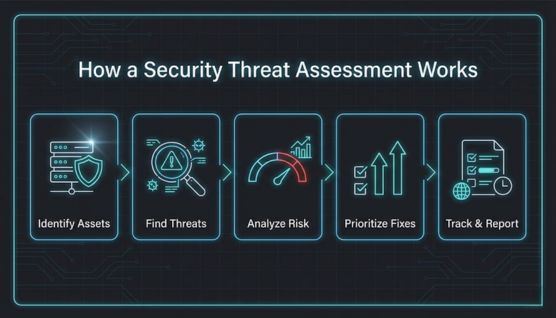
Teams determine which systems, data, facilities, and services require the highest level of protection. Prioritizing these assets directs the assessment toward areas of greatest organizational impact.
Security teams identify weaknesses through credentialed scanning, audits, and threat intelligence feeds. This process reveals exploitable paths across networks, applications, identities, APIs, and physical environments.
Likelihood scoring considers attacker capability, exposure, and existing controls. Impact is measured by business disruption, financial loss, compliance implications, and safety effects.
Risk scoring models rank issues based on severity and business relevance. This ensures limited resources are allocated efficiently to reduce exposure quickly.
Findings are compiled into a formal risk report with recommended actions, scores, and timelines. Teams use this documentation to verify remediation progress and meet compliance requirements.
A threat assessment includes several components that form a structured and repeatable evaluation process. Each component builds a complete picture of risk across systems, users, and infrastructure.
Analysts identify who or what could cause harm, including insiders, cybercriminals, hacktivists, supply-chain vendors, and nation-state groups. This shapes the threat model and informs defensive strategies.
Teams evaluate configuration weaknesses, software flaws, identity gaps, and third-party risks. Vulnerabilities are mapped to CVEs and CVSS scores to prioritize severity.
Likelihood is assessed by attacker capability, exploit availability, exposure, and security control maturity. Higher likelihood threats receive elevated priority in treatment plans.
Impact considers financial loss, safety risks, operational disruption, and damage to brand trust. High-impact threats shape executive-level decision-making.
Current safeguards (firewalls, MFA, PAM, SIEM monitoring, API security tools, and Zero Trust controls) are evaluated for effectiveness. Gaps indicate where stronger protections are required.
Threat intelligence aligns assessments with real-world adversary techniques and campaigns. Frameworks such as MITRE ATT&CK help categorize attack behaviors and intent.
The assessment produces a structured findings report, risk scores, and a remediation roadmap. Deliverables typically include: prioritized findings, CVE/CVSS summaries, remediation timelines, an executive overview, and technical appendices with scan results.
Threat assessments consider a full spectrum of cyber, human, environmental, and infrastructure threats.
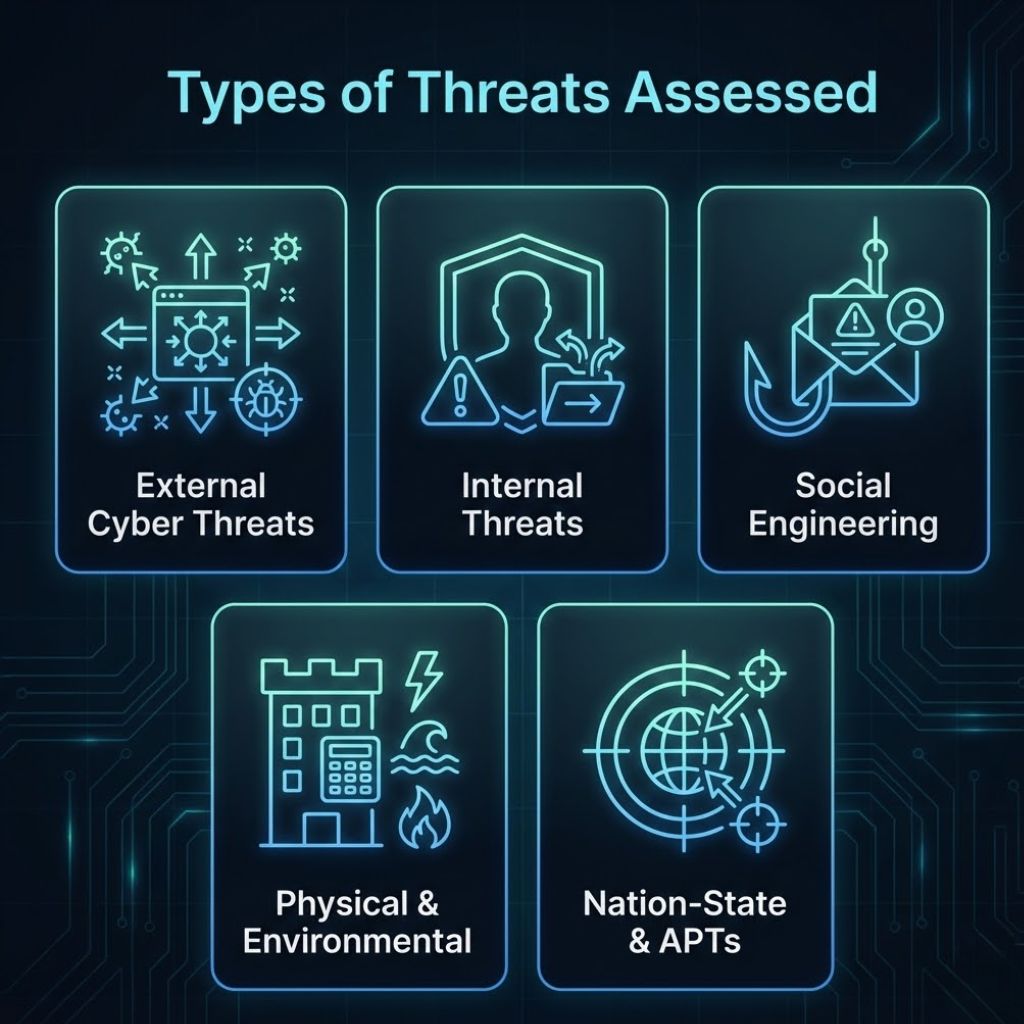
These include malware, viruses, ransomware, supply-chain attacks, DDoS attacks, and exploitation of software vulnerabilities. They often originate from cybercriminal groups, botnets, or automated exploitation tools.
Employees, contractors, or partners may misuse credentials or unintentionally expose systems. Internal threats are uniquely dangerous because they involve legitimate access paths.
Phishing, spear-phishing, impersonation, and business email compromise target human error. These techniques trick users into granting access or revealing sensitive data.
Physical breaches, theft, natural disasters, and facility failures disrupt operations and damage systems. These threats can undermine cybersecurity even without digital compromise.
Advanced persistent threats use stealthy, long-term campaigns for espionage or disruption. These adversaries require heightened monitoring, Zero Trust controls, and strong segmentation.
A network threat assessment evaluates misconfigurations, exposed services, identity paths, and abnormal traffic patterns to detect weaknesses in network infrastructure.
Credentialed vulnerability scans (Nessus, Qualys, OpenVAS) identify unpatched systems and insecure services. These scans often uncover direct entry points attackers could exploit.
Analysts review firewall rules, IAM configurations, authentication policies, and privilege assignments. Misconfigurations and excessive permissions remain leading causes of breaches.
Network flow data (NetFlow, IDS/IPS logs) is analyzed to detect lateral movement, beaconing, or suspicious patterns. SIEM tools correlate events to uncover stealthy intrusions.
Evaluation focuses on how easily attackers can move between systems once inside the network. Proper segmentation blocks lateral movement and limits blast radius.
Assessments include cloud posture checks, API exposure, SaaS misconfiguration, and identity drift. OT/ICS and IoT devices are also evaluated where applicable.
Threat assessments are necessary during major infrastructure changes, compliance cycles, or after potential security incidents.
Assessment helps determine root causes and prevent recurrence. It validates whether controls were bypassed or misconfigured.
New systems introduce new attack surfaces. Assessments ensure cloud, hybrid, or on-prem redesigns maintain strong controls.
Industries such as healthcare, finance, and retail require periodic assessments to meet standards like HIPAA, PCI DSS, and NIST. These assessments provide audit-ready documentation.
Mergers, acquisitions, and new product launches require risk validation. Assessments reveal inherited vulnerabilities and vendor risks.
Threat assessments strengthen resilience and improve the effectiveness of security investments.
Assessment frequency depends on organizational risk profile, compliance requirements, and system complexity.
Assessments rely on collaboration between internal security teams, external specialists, and business stakeholders.
CISOs, SOC analysts, and security engineers lead the assessment lifecycle. They coordinate technical findings and remediation efforts.
These analysts map attacker techniques, campaigns, and vulnerabilities. Their insights align assessments with real-world adversary behavior.
External firms and auditors offer independent evaluation and compliance validation. They uncover blind spots internal teams may miss.
Risk managers, legal teams, and business owners ensure recommendations support operational requirements. Their input shapes timelines and priorities.
Small-scope assessments take 3–7 days, mid-size projects take 2–4 weeks, and enterprise or multi-site assessments can span 6+ weeks or become continuous. Costs range from a few thousand dollars for scoped scans to significantly higher investments for comprehensive enterprise assessments.
A threat assessment identifies threats and vulnerabilities, while a risk assessment quantifies their likelihood and impact to prioritize treatment.
Threat assessments provide intelligence, prioritization, and context that strengthen detection and containment.
Assessment insights integrate adversary tactics (TTPs) into incident response plans. This improves preparedness and response precision.
Impact ratings determine which alerts or incidents require immediate focus. High-severity paths are contained first to reduce damage.
Assessments define normal system behavior, helping SIEM and analytics tools detect anomalies faster. Lower dwell time reduces attacker impact.
Assessments provide valuable insight but cannot eliminate all risk.
Point-in-time assessments become outdated as systems evolve. Continuous monitoring fills this gap by providing ongoing visibility.
Quality depends on accurate scans, logs, and intelligence feeds. Poor data reduces assessment reliability.
Limited budgets, time, or staff can delay remediation. Cultural resistance may also reduce corrective action effectiveness.
Threat assessments identify risks broadly, whereas penetration testing actively attempts to exploit them.
Penetration testing validates exploitability and control effectiveness. Threat assessments identify threats without performing exploitation.
Pen tests produce proof-of-exploit evidence. Threat assessments deliver prioritized findings and risk insights.
Assessments guide where penetration testing should focus. Using both enhances overall maturity and resilience.
Tools and frameworks help standardize assessments, strengthen accuracy, and ensure repeatability.
NIST CSF, ISO 27001, CIS Controls, and MITRE ATT&CK offer structured guidance. These frameworks align assessments with industry benchmarks.
SIEM, EDR/XDR, IDS/IPS, IAM (MFA, SSO, PAM), vulnerability scanners, API security tools, and threat intelligence platforms are essential. They collect data, detect anomalies, and validate exposure.
CVSS and custom scoring matrices help quantify severity and prioritize remediation. Scores guide resource allocation and reporting.
Threat assessments differ by industry context, risk level, and regulatory obligations.
Financial companies face heavy fraud, DDoS, and account takeover threats. Assessments include transaction monitoring and strict compliance checks.
Healthcare systems prioritize patient safety and PHI protection. HIPAA requires continuous evaluation of security risks.
Retailers assess POS systems, web apps, and supply-chain partners. PCI DSS mandates regular security assessments.
These sectors face nation-state and ICS/OT threats. Assessments focus on resilience, redundancy, and Zero Trust strategies.
Tools include SIEM platforms, vulnerability scanners, EDR/XDR solutions, IAM tools, and threat intelligence systems.
Depending on scope and complexity, assessments range from several days to several weeks.
Yes, many standards like PCI DSS, HIPAA, NIST, and ISO 27001 require periodic assessments.
Reports include threat findings, vulnerability summaries, CVE/CVSS ratings, and recommended remediation steps.
Yes, but many rely on third parties for independent validation and compliance needs.
A security threat assessment helps organizations identify their risks and understand where systems and operations are most vulnerable. By revealing exposures early, it enables stronger defensive strategies and meaningful risk reduction.
Consistent assessments promote long-term resilience by guiding teams on prioritization and continuous improvement. This structured approach empowers organizations to make informed decisions and maintain a proactive, mature security posture.
