🚀 CloudSEK becomes first Indian origin cybersecurity company to receive investment from US state fund
Read more
SafePay ransomware is a malware strain that encrypts data, steals sensitive files, and uses both to pressure victims into paying large ransoms. It carries out these actions by entering networks without authorization and taking control of critical systems.
Attackers behind SafePay rely on stolen credentials and weak remote access points to move through an environment quietly. Once inside, they disable protections, remove backups, and prepare the system for full-scale encryption and data theft.
The impact of these attacks is visible in public records, including a July 2025 breach filing on the Maine Attorney General’s portal that reported 42,521 affected individuals linked to an incident claimed by SafePay. This level of exposure shows how quickly a single intrusion can escalate into a significant operational and regulatory event.
SafePay is a ransomware operation controlled by one organized group that handles every step of the intrusion. The attackers carry out access, movement, data theft, and encryption as a single coordinated workflow.
Silent progression through a network is a core part of the operation, and each stage is arranged to prepare the environment for maximum disruption. The encryption engine locks systems quickly, and the key design prevents easy recovery without solid backups.
Victims are chosen based on the impact that interruptions or data exposure would create. Organizations that depend on remote access and interconnected systems face the greatest risk because SafePay aims for environments where pressure produces fast leverage.
SafePay infections follow a controlled access-to-control sequence that allows attackers to remain unnoticed until full system dominance is achieved.
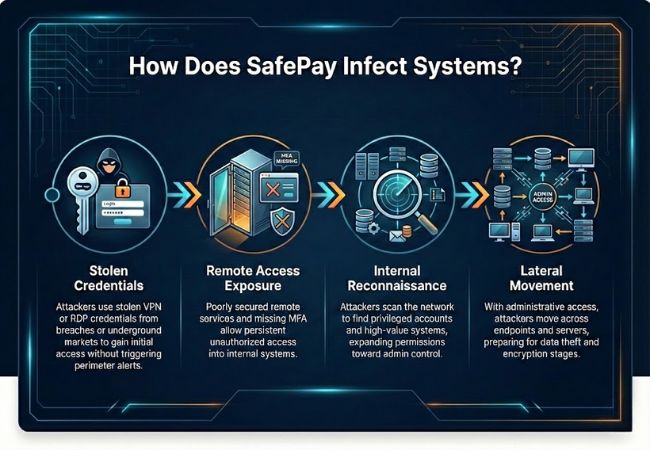
SafePay uses a controlled sequence that ensures leverage is secured before victims are aware an attack is underway.
Attackers first identify sensitive files stored on servers, backups, and shared storage systems. Priority is given to data tied to operations, finances, or regulatory exposure.
Selected files are compressed and transferred outside the network using common file-handling tools and standard protocols. Completing exfiltration before encryption guarantees pressure even if systems are later restored.
Encryption begins only after recovery options and security controls are neutralized. Files are locked using a hybrid cryptographic method that prevents access without attacker-held keys.
Ransom instructions are distributed after encryption is complete across affected systems. At that stage, victims face both operational shutdown and the risk of stolen data being leaked.
SafePay avoids early detection by weakening visibility and response long before encryption begins.
Antivirus, EDR, and monitoring services are deliberately stopped during the early stages of access. Removing these controls allows later activity to proceed without generating alerts.
Backup services and Volume Shadow Copies are deleted once attackers gain sufficient privileges. This step ensures that restoration options are removed before encryption is triggered.
Security-related configurations and policies are altered to reduce logging and defensive enforcement. These changes often persist until after the attack completes, complicating investigation.
Built-in operating system utilities are used for execution and movement across systems. Normal administrative tools help activity blend into routine system behavior.
Previously compromised credentials are reused to maintain access without raising suspicion. Legitimate accounts allow attackers to operate without introducing new authentication anomalies.
Preparation activity is concentrated during low-visibility periods such as nights or weekends. Encryption is delayed until defenders are least likely to respond quickly.
Logs related to execution, access, and system changes are reduced or cleared. Limited forensic data slows incident response and post-incident analysis.
SafePay infections leave behind technical and behavioral signals that appear before and after encryption, allowing defenders to identify an intrusion if monitoring is in place.
SafePay targets organizations where access, data value, and operational dependence combine to create strong leverage during an extortion attempt.
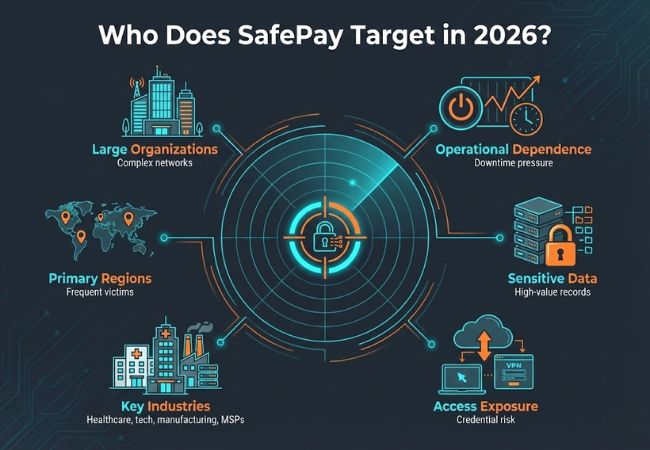
Mid-sized and large organizations are preferred because complex networks slow detection and response. Broader infrastructure also increases the chance of finding valuable data and privileged access.
Businesses that rely heavily on continuous system availability face higher risk. Downtime in these environments quickly translates into financial loss and urgency.
Targets often store regulated, proprietary, or customer data that carries legal or reputational consequences if exposed. Stolen information increases pressure even if systems can be restored.
Organizations with widespread VPN, RDP, or cloud-admin access are frequently affected. Stolen credentials in these environments allow attackers to move quietly and maintain control.
Healthcare, technology, manufacturing, and managed service providers appear often in reported incidents. These sectors combine sensitive data with time-critical operations.
Most confirmed victims are located in North America and Western Europe. Higher ransom tolerance and regulatory exposure influence this distribution.
Early detection depends on spotting behavior that signals preparation rather than waiting for encryption to begin.
Unusual VPN or RDP logins from new locations, devices, or time windows often appear before deeper activity. Valid credentials are used, but access patterns differ from normal behavior.
Sudden elevation of user privileges or unexpected use of administrative accounts can indicate internal expansion. These changes usually happen shortly after initial access.
Endpoint protection, monitoring agents, or backup services may stop without a clear operational reason. Such interruptions often signal attempts to weaken detection and recovery.
Network scanning, account enumeration, and system discovery activity can appear during the preparation phase. This behavior is typically low-noise but persistent.
Large volumes of files may be compressed or staged in short timeframes. This activity often precedes outbound data transfer.
Unusual data movement to unfamiliar external servers or cloud storage endpoints can indicate exfiltration. Transfers commonly occur during low-activity periods.
Protection against SafePay depends on limiting initial access, reducing internal movement, and preserving recovery options before an attack reaches the encryption stage.
VPN, RDP, and administrative portals should be restricted and protected with multi-factor authentication. Stolen credentials lose value when additional verification is required.
User permissions should follow least-privilege principles across systems and services. Reducing standing administrative access limits lateral movement after initial entry.
Endpoint detection tools should monitor command execution, credential use, and service tampering. Behavioral visibility allows defenders to identify preparation activity before encryption begins.
Backups must be isolated, immutable, and regularly tested for recovery. Offline or write-protected backups prevent attackers from removing restoration options.
Critical systems should be separated from general user environments. Segmentation limits the spread of an intrusion even when one system is compromised.
Continuous review of authentication logs, privilege changes, and data movement is essential. Early signals often appear hours or days before ransomware execution.
Choosing a ransomware protection tool requires focusing on visibility, control, and recovery rather than relying on signature-based prevention alone.
The tool should detect suspicious behavior such as credential misuse, service tampering, and abnormal command execution. Early-stage activity matters more than identifying the ransomware payload itself.
Strong visibility into VPN, RDP, and privileged account usage is essential. Abnormal login patterns often provide the earliest warning of a SafePay-style intrusion.
Automated containment features should allow infected endpoints to be isolated immediately. Fast isolation can stop lateral movement before data theft or encryption occurs.
The platform should work alongside immutable or offline backups without interfering with recovery workflows. Protection loses value if restoration paths can still be sabotaged.
Detailed telemetry, logging, and timeline reconstruction are critical for understanding how access was gained. Clear forensic data shortens response time and improves future hardening.
Deployment, maintenance, and alerting should align with the organization’s size and security maturity. Overly complex tools often fail due to misconfiguration rather than capability gaps.
SafePay ransomware shows how modern attacks combine access abuse, data theft, and encryption into a single, controlled operation designed to maximize pressure. The damage comes not only from locked systems, but from the exposure risk created long before encryption begins.
Organizations that focus on early detection, access discipline, and recovery readiness are better positioned to limit impact. Understanding how SafePay operates makes it easier to spot warning signs and disrupt attacks before they reach the point of extortion.
