🚀 CloudSEK becomes first Indian origin cybersecurity company to receive investment from US state fund
Read more
Key Takeaways:
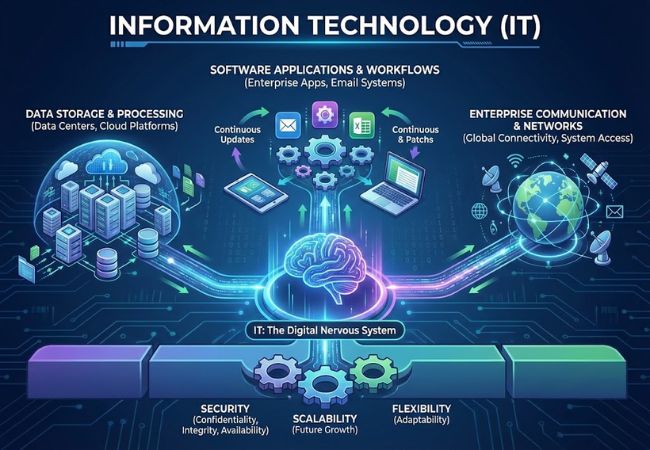
Information Technology is the function that manages digital data, software applications, and enterprise networks used in business environments. It enables organizations to store information, run applications, and support communication across digital systems.
Enterprise offices, data centers, and cloud environments rely on IT to handle data processing, system access, and internal workflows. Servers, databases, enterprise applications, email systems, and cloud platforms form the operational base of these environments.
Security, scalability, and flexibility shape how IT systems operate in practice. Regular updates, patches, and system changes are expected, with the primary goal of protecting data confidentiality, integrity, and availability rather than controlling physical processes.
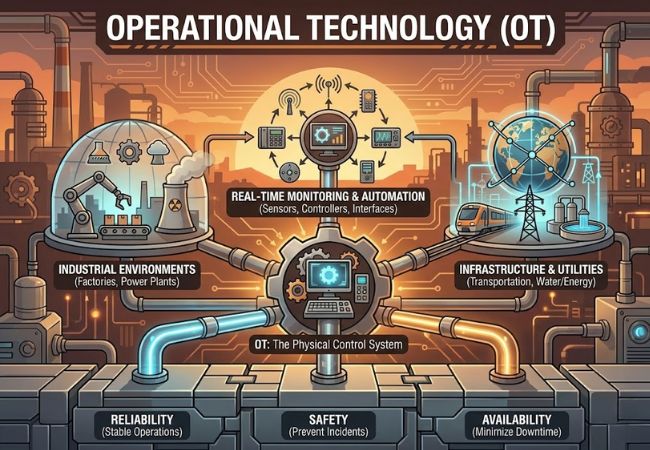
Operational Technology is the technology used to monitor, control, and automate physical equipment and industrial processes. It governs how machines, production lines, utilities, and infrastructure operate in real time.
Industrial environments such as factories, power plants, transportation systems, and utilities depend on OT to keep operations stable and predictable. Systems like industrial control systems, sensors, controllers, and operator interfaces work together to manage physical outcomes rather than digital information.
Reliability and safety define how OT systems are designed and maintained. Changes are introduced cautiously, downtime is tightly controlled, and system availability is prioritized because failures can lead to production loss, equipment damage, or safety incidents.
IT and OT systems differ in what they operate on, where they are deployed, and how directly they influence physical outcomes.
IT systems handle digital information such as business data, applications, and user access across enterprise operations. OT systems control machines, production processes, and equipment that shape physical activity in industrial environments.
Corporate offices, data centers, and cloud platforms form the core environment for IT systems, where conditions remain predictable and digitally managed. Industrial sites such as factories, plants, and infrastructure facilities define OT environments, where systems interact continuously with physical variables.
IT system failures commonly result in service interruptions, workflow delays, or temporary data inaccessibility. OT system failures often interrupt production, damage equipment, or introduce safety and operational risk.
Software updates and configuration changes occur regularly within IT environments as part of routine maintenance. OT environments emphasize stability, limiting changes and requiring careful coordination before any system modification.
The key differences between IT and OT systems become clear when comparing their purpose, risk tolerance, lifecycle, and operational priorities side by side.
Cybersecurity differs between IT and OT because each protects a different type of asset and faces a different type of risk.
IT cybersecurity concentrates on securing digital assets such as data, applications, and user access. Breaches primarily threaten confidentiality, system integrity, and business continuity.
OT cybersecurity centers on keeping physical operations stable and safe during normal and abnormal conditions. Security failures can affect machines, production output, infrastructure reliability, or human safety.
IT environments allow rapid response actions such as system isolation, patch deployment, or service shutdowns. OT environments require measured responses, since abrupt security actions can interrupt physical processes.
IT security commonly relies on frequent updates, endpoint protection, and identity controls. OT security emphasizes network segmentation, continuous monitoring, and minimal system interference.
The difference between IT and OT matters today because digital systems and physical operations are increasingly connected, making mistakes more costly and risks harder to contain.
Modern organizations rely on uninterrupted operations, where failures no longer stay isolated within a single system. Confusing IT practices with OT requirements can introduce disruptions that affect production, infrastructure, or public safety.
Expanded connectivity has increased the attack surface for both digital and industrial environments. Security incidents that once resulted only in data loss can now trigger physical damage or operational shutdowns.
Operational interruptions now carry financial, regulatory, and reputational consequences at the same time. Clear separation between IT and OT responsibilities helps organizations manage risk without slowing innovation.
Automation, remote monitoring, and data-driven operations continue to blur traditional boundaries. Understanding how IT and OT differ allows organizations to integrate systems without sacrificing reliability or safety.
IT/OT convergence refers to the integration of enterprise IT systems with operational OT systems to share data, improve visibility, and coordinate decision-making across digital and physical operations.
Operational data generated by machines and industrial systems is increasingly shared with business platforms for analysis and reporting. This visibility allows organizations to track performance, identify inefficiencies, and respond faster to operational changes.
Connected IT and OT environments enable better coordination between planning systems and production systems. Real-time insights help reduce downtime, optimize resources, and align operations with business goals.
Industrial connectivity, cloud platforms, and advanced analytics have accelerated convergence across sectors. Technologies such as industrial IoT, automation platforms, and remote monitoring tools make integration more practical and scalable.
Greater connectivity also increases exposure to cyber and operational risk. Convergence requires careful governance to ensure digital access does not compromise system stability, safety, or reliability.
Many industries rely on a combination of IT and OT systems to manage digital operations while maintaining control over physical processes.
Production planning, inventory management, and analytics run on IT systems, while assembly lines, robots, and control systems operate through OT. Coordination between both domains keeps production efficient without compromising safety.
IT systems manage patient records, scheduling, diagnostics data, and administrative workflows across healthcare organizations. OT systems operate medical devices, imaging equipment, and facility systems where reliability and precision affect patient safety.
IT systems support billing, forecasting, and grid analytics across energy providers. OT systems manage power generation, transmission, and distribution where stability and uptime are critical.
Logistics platforms, scheduling systems, and passenger services depend on IT infrastructure. OT systems control signaling, vehicle operations, and traffic management across rail, air, and road networks.
Exploration data, operational planning, and compliance reporting rely on IT systems. Drilling operations, pipelines, and refining processes depend on OT for continuous and safe operation.
IT supports monitoring, reporting, and administrative functions across public infrastructure. OT systems control water treatment, waste management, and essential services where failures affect public safety.
The difference between IT and OT comes down to managing digital information versus controlling physical operations. Each domain operates under distinct priorities shaped by risk, reliability, and environment.
As connectivity expands across industries, digital systems and operational systems increasingly intersect. This shift makes it essential to recognize where IT practices apply and where operational constraints must take precedence.
Effective integration depends on respecting the unique role of each domain rather than blending them without control. Organizations that align digital efficiency with operational safety are better equipped to reduce risk and sustain long-term reliability.
OT is not part of IT and operates as a separate technology domain with different priorities. IT manages digital information and systems, while OT controls physical processes and equipment.
Many IT security actions can interrupt operations when applied to industrial systems. OT environments require security controls that preserve system stability, safety, and continuous operation.
OT systems were traditionally isolated from external networks. Increased connectivity has changed this, but access remains tightly controlled due to operational risk.
Both IT and OT face cyber risks, but OT incidents often have greater physical and safety consequences. A single attack can disrupt production, infrastructure, or essential services.
IT and OT remain distinct domains with different responsibilities. Integration is increasing, but separation is still necessary to protect reliability and operational safety.
