🚀 CloudSEK becomes first Indian origin cybersecurity company to receive investment from US state fund
Read more
Email security protects communication and user accounts through email-based cyber attacks such as phishing, malware, spoofing, and other deceptive tactics designed to exploit trust. These attacks take many forms, from credential-stealing links to malicious attachments and impersonation attempts that target everyday communication flows.
Recent studies show that more than 90% of successful cyber incidents begin with email interaction, and attackers continue to shift toward more targeted and mobile-driven tactics like smishing and quishing. This combination of volume and precision keeps email at the center of modern cyber risk.
Strong authentication, careful handling of unfamiliar messages, and reliable threat detection form the foundation of safer email use. With the right controls in place, organizations can limit exposure to these attacks and maintain a more secure communication environment.
Email security is the practice of protecting email accounts, communication channels, and sensitive data from unauthorized access or misuse. It protects individuals and organizations from cyber threats such as phishing, malware, ransomware, spoofing, and Business Email Compromise.
Because email is a primary target for attackers, strong email security is crucial for preventing data exposure and maintaining organizational trust. It achieves this through filtering technologies, authentication standards like DMARC, DKIM, and SPF, and AI-driven detection that work together to block malicious content before it reaches users.
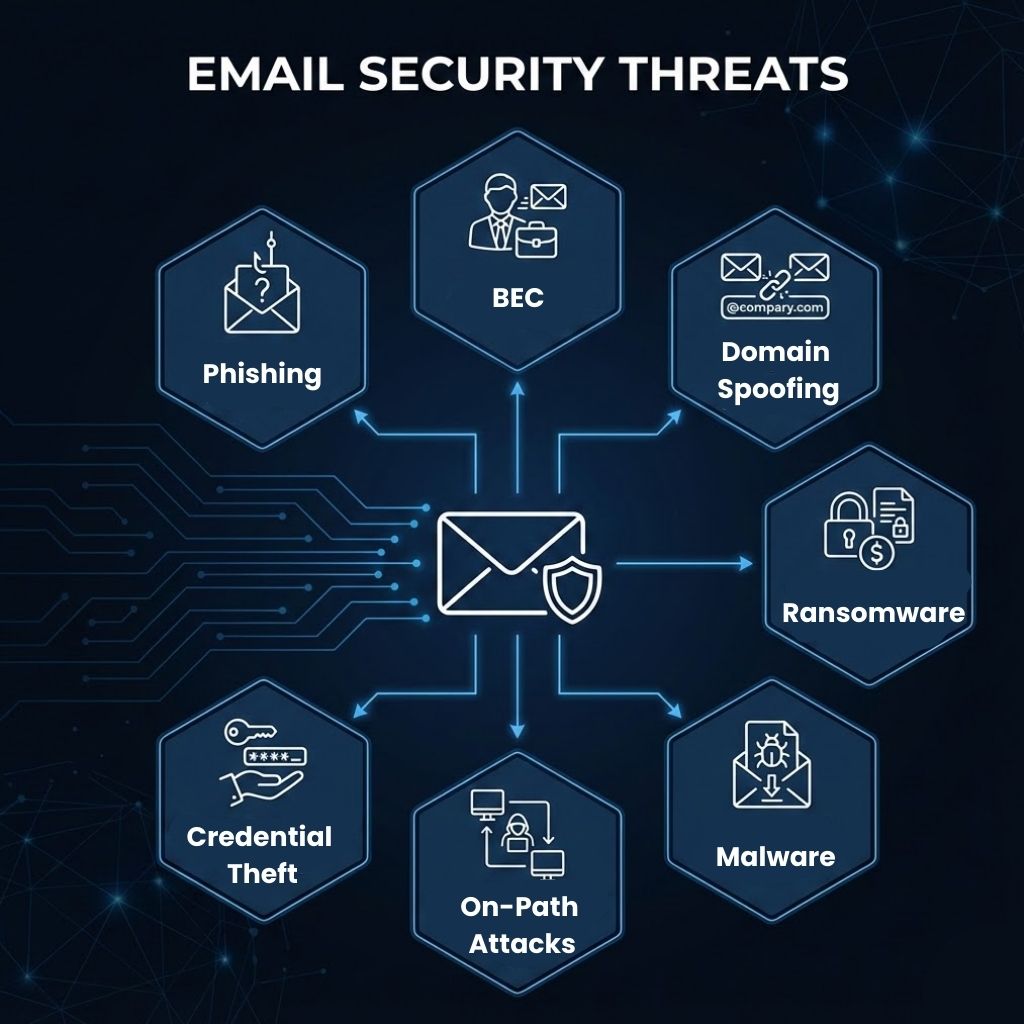
Phishing uses deceptive messages to manipulate users into sharing credentials or personal data through crafted links or forms. These attacks exploit user trust and rely on subtle messaging cues rather than technical exploits.
BEC involves carefully planned social engineering where attackers infiltrate communication threads to redirect payments or alter financial instructions. Instead of broad impersonation, these campaigns rely on timing, conversation familiarity, and transaction-level manipulation.
Domain spoofing focuses on forging email headers at the domain level to misrepresent the origin of a message. This technique enables attackers to blend into legitimate communication flows without altering content or behavior.
Ransomware emails distribute malicious code concealed within attachments or embedded links that trigger encryption once activated. These payloads aim to disrupt operations by locking critical systems and demanding payment for restoration.
Malware-based attacks deliver trojans, spyware, or keyloggers designed to extract data packets, monitor activity, or create persistence inside local area networks (LANs). These campaigns prioritize long-term access rather than immediate disruption.
On-path attackers position themselves between users and mail servers to intercept or manipulate email traffic in real time. By monitoring unsecured Wi-Fi or LAN segments, they can read, reroute, or subtly alter information without detection.
Credential harvesting directs victims to login portals that imitate legitimate services to collect passwords and session tokens. Once attackers gain mailbox access, they can escalate privileges, observe internal communication, or spread additional attacks.
Phishing is an attempt to trick users into giving up credentials or sensitive information through messages that look genuine. The technique has expanded far beyond email and now follows users across different communication channels.
Several variations of phishing are common today and each uses a different approach:
All of these methods work because they exploit attention and trust. Users react to familiar branding or urgent requests, and attackers build their messages around that behavior.
Effective protection focuses on recognizing unusual activity and strengthening identity checks. Email authentication, adaptive filtering, mobile-aware monitoring, and steady user awareness help reduce the chances of these attacks succeeding.
Email attachments are a common way for attackers to hide malicious code inside familiar file formats. Users open these files expecting routine documents, which makes the attack easy to trigger.
Attackers often use invoices, reports, and forms to make the file look legitimate. Once opened, the attachment can install ransomware, spyware, or other harmful payloads without showing any obvious signs.
Key patterns seen in attachment-based attacks include:
Limiting script permissions, scanning attachments before delivery, and using sandboxing tools help reduce the chances of these files causing damage.
Spam consists of unsolicited mass emails that fill inboxes with irrelevant or deceptive content. Attackers use spam to distribute unsafe links or misleading prompts at a large scale.
Some messages contain hidden malware inside attachments or redirect users to pages designed to capture login details. These campaigns rely on volume, hoping that even a small number of users will click without questioning the source.
Effective spam protection depends on strong filtering and consistent reputation checks for suspicious senders. Users should be cautious with unsolicited messages that ask for clicks, downloads, or personal information.
Account Takeover occurs when attackers gain unauthorized access to a user’s mailbox by using stolen or guessed credentials. Once inside, they can read messages, reset passwords, and impersonate the account owner.
These attacks often begin with credential harvesting, password reuse, or brute-force attempts targeting weak accounts. Attackers usually stay quiet at first, monitoring communication to understand internal processes before acting.
Preventing ATO requires strong authentication and monitoring for unusual login behavior. Users should avoid password reuse and report unexpected alerts or unfamiliar account activity.
AI in email security refers to machine-learning systems that strengthen detection by examining how emails are written, structured, and delivered.
SEGs filter inbound and outbound messages to block malicious URLs, suspicious attachments, and high-risk senders. They act as the first inspection layer before emails reach user inboxes.
These services protect sensitive messages by converting them into unreadable formats for unauthorized recipients. They help secure communication during transfer and storage.
DLP monitors outgoing email to stop sensitive information from being sent to the wrong recipients. It enforces internal policies and prevents accidental or intentional data exposure.
API-driven tools analyze messages directly inside the mailbox instead of relying on inline filtering. This allows deeper visibility into user activity and better detection of post-delivery threats.
Threat intelligence services enrich email scanning with insights on new malicious domains, active phishing campaigns, and emerging attack patterns. This helps identify threats that traditional filters may miss.
DMARC, DKIM, and SPF verify that messages come from legitimate domains. These protocols reduce spoofing and protect organizations from impersonation attempts.
Cloud-based solutions offer scalable protection that adapts to changing message volumes and evolving threats. They integrate smoothly with modern email platforms without requiring hardware.
AI models analyze writing style, sender patterns, and unusual behavior to identify complex phishing attempts. This helps detect attacks that do not rely on known signatures.
Zero-trust approaches validate sender identity, device posture, and message intent before allowing interaction. This reduces the risk of unauthorized access and credential misuse.
These solutions analyze messages after they enter the inbox and remove harmful content if detected later. They are especially effective against delayed or stealthy attacks.
Mobile-aware tools look for threats delivered through QR codes, text messages, and mobile redirects. They help organizations secure email interactions that occur outside the desktop environment.
Some solutions extend email security to file sharing, attachments, and workspace communication. This ensures consistent protection across all channels where users exchange information.

A strong, unique password prevents attackers from guessing or reusing credentials obtained from breaches. It should be long, unpredictable, and not shared across multiple accounts.
MFA adds a second verification step, reducing the risk of account takeover even if a password is compromised. It blocks most unauthorized login attempts by requiring identity confirmation.
Encryption protects message content from being read if intercepted during transmission. It helps secure sensitive communication and keeps private data out of unauthorized hands.
Many attacks begin with files that hide malicious code inside familiar formats. Scanning attachments before opening them reduces the chance of ransomware or spyware reaching your device.
Strong filtering reduces exposure to fraudulent links, suspicious messages, and high-volume spam. It helps keep harmful content out of the inbox and lowers user risk.
DLP policies prevent sensitive information from leaving the organization through mistakes or intentional misuse. These controls detect risky content and block it before it is sent.
Unusual logins, new forwarding rules, or unexpected sent messages can indicate early compromise. Checking activity regularly helps catch suspicious behavior quickly.
Email clients, apps, and operating systems need frequent updates to patch exploitable weaknesses. Updated tools reduce the chances of attackers using known vulnerabilities.
Unexpected requests for information or links that feel out of place should be treated carefully. Verifying the sender and checking URLs can prevent credential theft.
Avoid logging into email accounts on public or unsecured Wi-Fi. Using a VPN adds encrypted protection to your connection and reduces interception risks.
Yes. Small businesses are often targeted because attackers expect lighter defenses, so reliable email security helps protect their communication and accounts.
AI tools detect unusual patterns and emerging threats faster than fixed rule-based filters. They offer stronger protection against evolving phishing techniques.
They prevent most forms of domain impersonation when configured correctly. These standards are strongest when paired with real-time threat monitoring.
In many cases, yes. Cloud-based tools provide better scalability, faster detection, and easier management compared to traditional on-premise gateways.
CloudSEK is one of the best email security tools because it identifies threats before they reach the inbox. Its intelligence-driven approach focuses on spotting phishing setups, spoofed domains, and impersonation signals early in the attack cycle.
CloudSEK strengthens email protection by monitoring attacker infrastructure, new domain registrations, and behavioral patterns that indicate preparation for phishing or account takeover. This gives security teams visibility into risks that traditional filters and gateways often miss.
By combining real-time threat intelligence with continuous monitoring, CloudSEK provides a proactive layer of defense that helps organizations stay ahead of emerging email threats. Its focus on early detection makes it a strong choice for preventing phishing, spoofing, and identity-based attacks.
