🚀 CloudSEK becomes first Indian origin cybersecurity company to receive investment from US state fund
Read more
Credential Leak Channels are considered the most valuable dark web Telegram sources for cybersecurity teams because they reveal compromised accounts earlier than any other group type. Their real-time exposure signals allow defenders to take immediate action before attackers weaponize the data.
As threat actors increasingly shift their operations to Telegram, the platform has become a central hub for sharing stolen information, tooling, and breach indicators. This shift has pushed security teams to monitor a wide range of underground channels to stay ahead of emerging attacks.
The speed and volume of updates inside these groups give analysts a unique advantage in identifying risks before they escalate. With a clearer understanding of how these communities operate, cybersecurity teams can strengthen their threat intelligence workflows and respond with greater precision.
Dark web Telegram groups are encrypted, semi-anonymous channels where threat actors share stolen data, malware samples, breach announcements, and fraud resources. These spaces mimic the behavior of dark web forums but operate through Telegram’s accessible and low-barrier messaging structure.
Cybercriminals use these channels to distribute logs, databases, and tools quickly. This real-time delivery makes Telegram a preferred platform for both attackers and defenders seeking visibility into evolving cybercrime activity.
As a result, cybersecurity teams track these groups to identify early indicators of compromise and gain situational awareness of emerging threats.
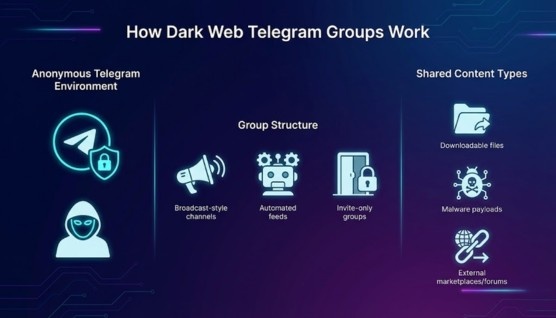
Dark web Telegram groups typically operate using broadcast-style channels, bot-automated feeds, and semi-closed communities that require invitations. Threat actors use anonymous identities, encrypted messaging, and privacy-centric settings to limit exposure.
These groups regularly share downloadable files, malware payloads, text dumps, and links to external dark web marketplaces or forums. Because content is updated rapidly, monitoring tools and careful observation are essential to maintain awareness without direct engagement.
This structure highlights why cybersecurity teams approach these groups as intelligence sources rather than communities for interaction.
Cybersecurity teams monitor dark web Telegram channels to access early insights into stolen credentials, targeted attacks, and active threat campaigns. This intelligence helps SOC analysts and CTI teams identify indicators of compromise before they appear in mainstream reporting.
These channels also reveal tactics, techniques, and procedures that threat actors use in real-world attacks. Such insights support proactive defense planning and fast escalation when new vulnerabilities or breaches surface.
By tracking these data points, organizations enhance their preparedness and understand threat trends more effectively.
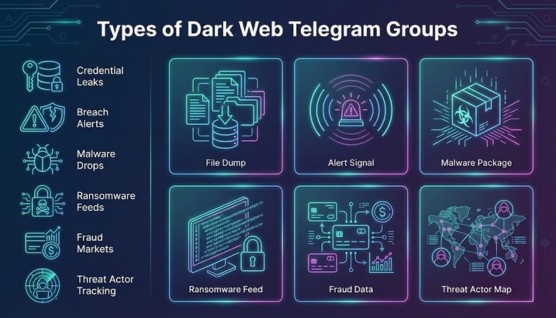
These channels share username–password combinations, authentication logs, and compromised accounts obtained from infostealers and breached databases. Cybersecurity teams monitor them to detect exposed corporate or customer credentials early.
These groups publish announcements about newly compromised platforms and leaked database previews. Analysts follow them to determine whether their organization appears in the listings.
These communities circulate malicious software including stealers, ransomware builders, and exploit kits. Security teams collect samples for sandbox testing and deeper threat modeling.
These Telegram feeds mirror or aggregate updates from active ransomware operations. Monitoring them helps CTI teams identify new victims and anticipate sector-specific targeting trends.
These groups center on financial fraud, stolen payment data, and identity bundles traded in underground circles. SOC teams watch them to anticipate fraud risks and detect exposed customer information.
These channels follow the activity, aliases, and movement of threat actors across platforms. Analysts use this insight to map relationships and understand the behavior of cybercriminal networks.
Credential leak channels release logs, compromised accounts, and authentication data sourced from infostealers and breached platforms. Analysts use this intelligence to identify exposed accounts before attackers weaponize them.
They also reveal patterns in credential harvesting operations, helping teams strengthen identity protection strategies. This early visibility supports faster internal remediation and limits downstream compromise.
Data breach channels publish claims, previews, and early indicators of newly compromised services. Security teams monitor them to determine whether organizational data appears in emerging leaks.
Announcements often surface before public disclosure, giving defenders crucial lead time. That advantage helps SOC teams accelerate triage and begin containment work sooner.
Malware-sharing groups distribute payloads, scripts, and executables used in active campaigns. These samples are collected for sandbox testing, signature development, and behavior analysis.
A continuous flow of new files helps analysts track how malware families evolve. This insight strengthens detection engines and improves defensive tuning across the security stack.
Ransomware feeds aggregate victim announcements and operational updates from active threat groups. CTI teams use this information to understand current targeting patterns across sectors.
The listings reveal geographic, industry, and organizational trends that shape attack strategy. This intelligence guides more precise risk assessments and defensive planning.
Fraud-focused channels circulate stolen payment data, identity bundles, and tools used in financial attacks. Fraud analysts rely on this intelligence to detect emerging criminal techniques.
Posts highlight new scam workflows and exploitation methods spreading across underground markets. This context supports proactive fraud prevention and customer protection measures.
SIM-swap communities discuss hijacking tactics and provide insights into telecom vulnerabilities. Security teams watch these conversations to safeguard high-risk accounts and public-facing executives.
Shared methods reveal how attackers bypass authentication controls during takeover attempts. This understanding helps organizations reinforce verification layers and reduce account compromise.
Database feeds distribute large collections of emails, hashes, and personal information obtained from breaches. Monitoring these dumps helps teams identify high-volume exposure events quickly.
The datasets also highlight industries facing sustained targeting from criminal networks. That awareness guides long-term defensive strategy and resource allocation.
Automated aggregator bots collect updates from multiple dark web points and deliver them directly into Telegram. This setup provides continuous intelligence with minimal analyst workload.
Automation reduces exposure to high-risk environments while maintaining strong visibility. Many teams pair these alerts with broader CTI pipelines for faster detection.
Phishing-kit groups share templates, cloned sites, and harvesting tools used in credential theft campaigns. Analysts follow these updates to prepare for upcoming phishing waves.
New kits often mirror current social-engineering patterns across industries. That insight helps organizations adjust filtering rules and user-awareness programs.
Crypto-focused hubs expose fraudulent wallets, malicious scripts, and drain techniques used in blockchain attacks. CTI teams track them to understand how crypto-fraud tactics evolve.
Shared evidence often reveals ways attackers bypass wallet protections or abuse smart-contract features. This intelligence supports stronger monitoring across cryptocurrency-exposed services.
Monitoring is generally allowed as long as no one engages in or encourages criminal activity. Organizations must maintain strict read-only practices and follow internal compliance guidelines.
Many channels share leaked credentials, breach fragments, malware files, and threat actor updates. Security teams use this material to identify early signs of exposure or malicious activity.
Collected insights feed into detection rules, threat-hunting workflows, and incident response planning. This accelerates visibility into emerging attacks before they escalate.
Analysts should rely on VPNs, anonymized accounts, and isolated workstations to reduce exposure. Sandboxing and non-engagement policies further minimize operational risk.
Automation helps reduce manual exposure while increasing coverage across multiple sources. When paired with human analysis, it strengthens the accuracy and speed of CTI workflows.
Cybersecurity teams gain a significant advantage when they monitor dark web Telegram groups, as these channels reveal threats earlier than most traditional intelligence sources. With consistent visibility into leaks, malware, ransomware activity, and fraud trends, defenders can respond before attacks fully unfold.
A structured monitoring strategy helps organizations use this intelligence responsibly while maintaining strong OPSEC and compliance. By integrating these insights into daily workflows, security teams improve their ability to detect risks, refine defenses, and stay ahead of rapidly evolving cybercrime tactics.
