🚀 CloudSEK becomes first Indian origin cybersecurity company to receive investment from US state fund
Read more
Key Takeaways:
Each browser was examined by looking at how it’s built, how often it’s updated, and how well it handles modern privacy expectations. That perspective helped clarify which tools remain dependable in 2026 and which ones have fallen behind.
Testing involved running the browsers in real conditions, opening hidden services, and observing how they respond to scripts, tracking attempts, and fingerprinting techniques. This approach made it easier to understand the difference between theoretical security and actual performance.
To round out the review, launch histories, project documentation, and public development activity were checked for accuracy. These details ensured that every recommendation reflects tools that are still being maintained and can be trusted today.
Tor Browser was introduced in 2008 as part of an effort to bring the privacy-protecting Tor network into a user-friendly application. It grew from a research program into the most widely trusted tool for anonymous browsing.
People use Tor Browser when they need consistent protection while navigating hidden services or avoiding monitoring on public networks. Its layered routing structure helps keep browsing activity private without requiring complex technical skills.
What makes Tor Browser stand out is its long development history, active maintenance, and strong global community support. For users who want a stable and proven anonymity solution, it remains the strongest overall choice.
Mullvad Browser was released in April 2023 through a partnership between Mullvad VPN and the Tor Project to create a privacy-focused browser without mandatory Tor routing. It was designed for users who want strong anonymity on the open web.
Its goal is to remove identifying traits that allow websites to build a fingerprint of your device. This makes it useful for people who browse regularly but still want strict privacy protections.
The browser resets identity information each session and blocks silent tracking behavior by default. For users seeking a blend of simplicity and privacy, Mullvad Browser delivers consistent and reliable protection.
I2P began in 2003 as a project focused on creating a fully decentralized anonymity network separate from the public internet. It was built to support private communication across independent nodes.
The network is ideal for users who want to access internal forums, email services, and peer-to-peer platforms unreachable from the surface web. Its use case fits people who value closed-network anonymity instead of traditional browsing.
I2P’s garlic routing separates encrypted data into multiple paths, making tracking extremely difficult. Its decentralized design offers a unique privacy environment not dependent on external infrastructure.
Freenet was introduced in 2000 as a research project aimed at building a censorship-resistant information network. It later evolved into a global system for anonymous publishing and distributed storage.
Users rely on Freenet when they need to share documents or host forums without revealing their identity. It suits people looking for long-term information persistence rather than fast browsing.
Its distributed architecture encrypts and splits data into fragments stored across volunteer nodes. This makes Freenet especially strong for private communication and anonymous content hosting.
Tails was launched in June 2009 as a live operating system designed to leave no traces on the device it runs on. It was created for users who need a controlled and temporary privacy environment.
People turn to Tails when they require a secure workspace that disappears after shutdown. It is especially useful for journalists, travelers, and researchers who cannot trust the host machine.
Tails routes all activity through secure channels and includes built-in anonymity tools. Its portability and self-contained design make it one of the safest solutions for short-term anonymous sessions.
Whonix was introduced in 2012 as a distribution designed to separate network traffic from user activity. It operates as a two-virtual-machine system that protects identity through compartmentalization.
Users rely on Whonix when they need protections that go beyond browser-level anonymity. It suits people who work with sensitive material and require control over every layer of the environment.
The system ensures all traffic moves through secure channels, even if the user workspace is compromised. Its strong isolation framework makes it one of the most resilient privacy setups available.
Qubes OS was introduced in 2012 as a security-first operating system built around the idea of isolating tasks into separate virtual environments. It grew from the need to protect users even when one activity, application, or browser window becomes compromised.
People choose Qubes OS when they want clear separation between everyday browsing, private communication, and high-risk research. This design makes it especially appealing to journalists, security professionals, and users who handle sensitive information.
Its strength comes from the way it uses individual “qubes” to confine risk and prevent one issue from spreading across the system. When paired with Whonix or Tor Browser inside dedicated compartments, it becomes a powerful setup for long-term, stable anonymity.
Brave released its Private Window with Tor in the late 2010s to give users a simple way to access hidden sites. It was created for people who want occasional anonymity without using a separate browser.
Users choose Brave’s Tor mode when they want quick private sessions wrapped inside a familiar interface. This makes it appealing for beginners or casual privacy-seekers.
While not as strict as dedicated anonymity tools, the Tor window blocks trackers and masks IP information effectively. Its balance of accessibility and privacy makes it useful for lighter anonymous browsing.
Onion Browser launched for iOS as a way to bring Tor-based privacy to Apple devices where native Tor Browser cannot run. It offers a lightweight approach to hidden-site browsing on mobile.
iOS users depend on Onion Browser when they need quick, private access without desktop tools. It fits people who browse anonymously while traveling or using public networks.
The app includes safety modes that restrict risky scripts and limit exposure on untrusted pages. Its simplicity and mobile compatibility make it a practical Tor solution for iPhone users.
Orbot was released in 2008 as a Tor-powered proxy designed for mobile devices. It later became a key tool for routing Android app traffic through privacy-focused channels.
Users rely on Orbot with Tor Browser when they need secure mobile access to hidden sites or private communication. It works well for people in restrictive regions or on monitored networks.
The combination allows apps and browsers to run through anonymizing routes without exposing identity details. Its flexibility and mobile-first design make it the strongest anonymity setup for Android devices.
A dark web browser is a specialized tool built to access hidden websites that operate on networks like the Tor network rather than the mainstream internet. It creates a private browsing environment by routing traffic through encrypted paths that help conceal your identity.
These browsers rely on multi-layered encryption, often referred to as onion routing, to move your data through volunteer-run nodes. This layered design makes it difficult for websites, internet providers, or outside observers to trace where a request originated.
Unlike regular browsers, dark web browsers are engineered to limit fingerprinting, block invasive scripts, and safely load .onion domains that aren’t accessible through standard search engines. Their purpose is to give users a controlled and anonymous way to explore hidden services without exposing personal information or system details.
Browsing the dark or deep web in 2026 is safer than in previous years, but only when you understand the risks that come with hidden networks. Many unsafe experiences happen because users rely on the wrong tools or interact with unknown sites without caution.
Security in 2026 is shaped by more advanced tracking attempts, smarter phishing scams, and scam marketplaces that mimic legitimate hidden communities. These threats make it important to rely on updated privacy tools rather than outdated browsers or casual browsing habits.
Safe exploration is possible when users stick to verified resources, avoid downloads, and treat every unknown page with skepticism. The dark and deep web still hold genuine research forums and privacy-focused spaces, but navigating them responsibly is what keeps the experience secure.
Choosing a dark web browser requires focusing on features that keep your identity protected and reduce the chances of data exposure.
The strongest safety on .onion sites comes from browsers built specifically for anonymity rather than general privacy.
Tor Browser is the safest overall choice because it handles routing, isolation, and fingerprint protection automatically. It gives consistent anonymity without requiring any advanced setup.
Tails is safest for short, high-risk sessions since it runs as a temporary system that erases everything when it shuts down. Its clean environment avoids leaving traces on the device.
Whonix offers the safest long-term protection thanks to its two-VM structure that separates network activity from the user environment. This division keeps identity secure even if one layer is compromised.
A VPN is helpful when you want to hide the fact that you’re connecting to Tor from your internet provider. It also provides an extra layer of protection in countries or networks that block or closely monitor Tor traffic.
For most users, Tor alone is enough because the network already masks your identity by routing your traffic through multiple encrypted relays. Using a VPN on top of Tor doesn’t automatically make you more anonymous.
There are situations where a VPN can introduce unnecessary risk, especially if the provider keeps logs or handles traffic poorly. In those cases, the extra layer becomes a weakness instead of a benefit.
Using the wrong browser exposes you to risks that hidden services often exploit to identify or target visitors.
A weak browser may reveal your IP address through small connection leaks that occur in the background. These leaks give hidden sites a direct link to your real location.
Poorly configured browsers reveal device traits that make your setup unique. That uniqueness gives trackers a persistent reference point across different pages.
Some browsers load active scripts that hidden services use to test for weaknesses. One unsafe script can deliver malware or extract system-level details.
Browsers without strong isolation create traffic patterns that observers can match with your real activity. This correlation turns anonymous browsing into something traceable.
Outdated browsers miss critical updates that fix vulnerabilities exploited on hidden networks. These flaws give attackers easy opportunities to compromise your system.
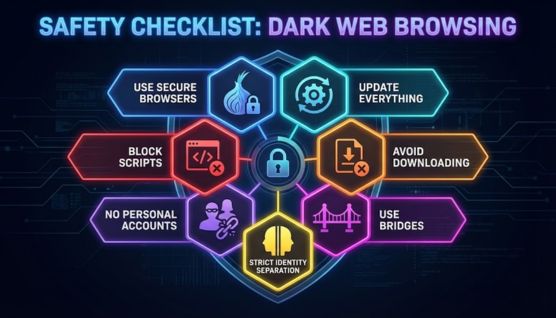
Rely on browsers built specifically for anonymity rather than general privacy. This ensures that routing, isolation, and fingerprint controls work the way hidden networks expect.
Outdated software exposes you to exploits that circulate heavily on hidden services. Keeping tools updated closes gaps attackers depend on.
Scripts are a common method for identifying or exploiting visitors on hidden sites. Turning them off removes one of the fastest paths to exposure.
Files from unknown hidden pages frequently contain malware or tracking payloads. Skipping downloads protects you from threats you cannot evaluate safely.
Any login tied to your real identity breaks anonymity immediately. Keeping personal and anonymous activity separate protects your privacy.
Bridges help bypass networks that restrict Tor or monitor entry nodes. They add a quiet layer of protection when connecting from hostile regions.
Do not reuse usernames, writing patterns, or browsing habits from your regular life. Maintaining clear boundaries prevents hidden sites from connecting your anonymous presence to your real profile.
Choosing the right dark or deep web browser in 2026 comes down to understanding your threat level and the type of anonymity you need. Some tools offer simple protection for everyday browsing, while others are designed for high-risk environments where even small mistakes matter.
Tor Browser remains the most reliable option for most users, while Tails and Whonix offer deeper protection for sensitive work. Tools like Mullvad Browser, I2P, and Qubes OS fill in the gaps for people who need privacy outside of .onion sites or want compartmentalized environments.
No matter which path you choose, the key is staying informed, keeping your tools updated, and using the dark web with caution and purpose. Consistent, careful habits will protect you far more than any single piece of software.
