🚀 CloudSEK becomes first Indian origin cybersecurity company to receive investment from US state fund
Read more
AsyncRAT is a .NET-based remote access trojan that enables attackers to remotely control infected Windows systems, including executing commands, accessing files, and monitoring user activity. It first appeared publicly in 2019 as an open-source remote administration tool, a release that later allowed threat actors to adapt and reuse its code in real intrusion campaigns.
Since then, AsyncRAT has become a common post-compromise foothold rather than a one-off payload, frequently deployed after phishing-based initial access. Its design makes it effective for maintaining persistence and expanding attacker control once a system is breached.
Its current relevance is reflected in U.S. government reporting: a July 25, 2024 joint cybersecurity advisory identified AsyncRAT as one of 18 open-source or dual-use tools actively used and customized by North Korean threat actors. That classification places AsyncRAT in the context of nation-state operations, signaling that its detection should be treated as a high-confidence indicator of serious intrusion activity.
AsyncRAT is a remote access trojan designed to provide attackers with persistent, interactive control over compromised Windows systems. The malware allows remote command execution, file manipulation, and user activity monitoring after initial access has been established.
Built on the .NET framework, AsyncRAT is easy to modify, recompile, and redistribute across campaigns. Open availability of the codebase significantly lowered the barrier for reuse, which led to widespread adoption in phishing-led intrusions and post-exploitation activity.
In real-world attacks, AsyncRAT is commonly deployed as a long-term access mechanism rather than a one-time payload. This role aligns it with post-compromise operations, where its presence often indicates objectives such as credential theft, lateral movement, or secondary malware delivery.
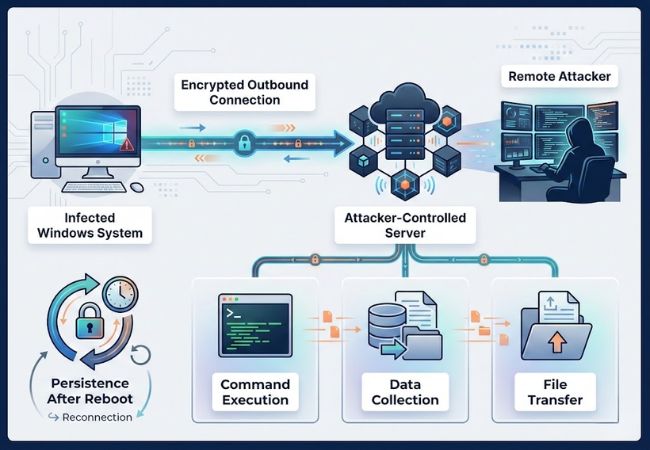
AsyncRAT works by establishing an outbound connection from an infected Windows system to attacker-controlled infrastructure. This connection allows attackers to issue remote commands and receive responses without requiring user interaction.
An asynchronous communication design enables multiple actions to run at the same time, including command execution, data collection, and file transfer. Parallel task handling helps maintain responsiveness while minimizing visible system impact.
Encrypted network traffic is commonly used to reduce inspection and avoid basic detection controls. Persistence mechanisms ensure the malware reconnects after reboots, allowing long-term access once a system is compromised.
AsyncRAT provides attackers with multiple post-compromise capabilities that support remote control, information theft, and persistent access.
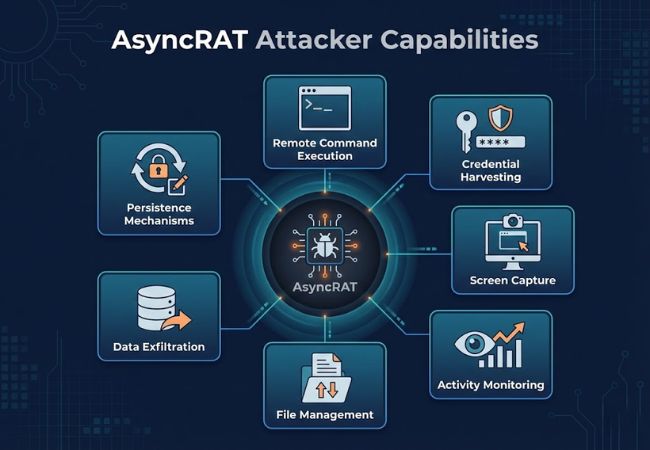
This capability allows attackers to execute system commands on the infected host. Remote execution enables configuration changes and deployment of additional malicious payloads.
Credential harvesting focuses on extracting authentication data from browsers, applications, and user input. Stolen credentials often enable privilege escalation and access to additional systems.
Screen capture provides visual insight into user activity by recording on-screen content. Captured data is commonly used to identify sensitive information or operational workflows.
Activity monitoring allows attackers to observe user behavior and system interaction over time. This capability supports reconnaissance and timing of follow-on actions.
File management enables remote uploading, downloading, and modification of files. These actions support data theft and preparation for further malicious activity.
Data exfiltration focuses on transferring stolen information out of the infected environment. Sensitive files and collected credentials are commonly targeted.
Persistence mechanisms allow AsyncRAT to remain active after system restarts or user logouts. Startup execution methods and registry modifications are commonly used to maintain access.
Social engineering remains the dominant infection vector, with AsyncRAT delivered through user-initiated execution instead of direct exploitation of system vulnerabilities.
Phishing emails are the most common infection method used to deliver AsyncRAT. Messages often impersonate legitimate organizations and pressure recipients to open attachments or click links.
Malicious attachments typically include executable files, compressed archives, or weaponized documents. Opening these files triggers the initial execution stage that installs the malware.
Social engineering lures rely on urgency, curiosity, or trust to prompt user action. Fake invoices, delivery notices, or account alerts are frequently used themes.
Loader-based delivery involves a small initial payload that retrieves AsyncRAT from a remote server. This technique helps evade basic detection and reduces the malware footprint during early stages.
Multi-stage infection chains separate initial access from final payload execution. Each stage performs a limited role, which complicates analysis and delays detection.
Command and control infrastructure in AsyncRAT enables remote tasking, data exchange, and sustained attacker control after a system is compromised.
Infected systems initiate outbound connections to attacker-controlled servers rather than waiting for inbound access. This design helps bypass common firewall and perimeter filtering rules.
Traffic exchanged between the host and control servers is commonly encrypted to hide commands and responses. Reduced payload visibility limits the effectiveness of basic network inspection.
Standard application-layer protocols such as TCP or HTTP are frequently used to carry command traffic. Familiar protocol usage allows malicious communication to blend into legitimate network activity.
Domains or IP addresses used for command and control often change over time. Infrastructure rotation increases resilience and complicates static blocking efforts.
Automatic reconnection behavior allows communication to resume after network loss or system restarts. Persistent retry logic maintains access without user interaction.
Commands delivered through the control channel are queued and processed asynchronously on the host. Asynchronous execution allows multiple instructions to run efficiently without degrading stability.
Collected information such as credentials, screenshots, and system metadata is transmitted back through the same control pathway. Centralized communication preserves attacker visibility while reducing operational complexity.
Risk exposure associated with AsyncRAT comes from its ability to remain active over long periods while quietly enabling multiple forms of abuse within compromised environments.
Collected files, screenshots, and captured input can be removed from systems without raising immediate alarms. Loss of sensitive internal data often occurs before defenders detect the intrusion.
Access to stored credentials and authentication material allows attackers to impersonate users. Compromised accounts are frequently reused to expand access beyond the initial system.
Control over one endpoint can be leveraged to explore connected systems and shared resources. Poor segmentation increases the likelihood of wider compromise.
Established access makes it easier to introduce additional malicious tools at later stages. Follow-on activity often includes ransomware deployment or deeper surveillance tooling.
Security incidents linked to remote access malware commonly result in downtime, investigation costs, and compliance concerns. Long dwell time amplifies operational and reputational damage.
Detection of AsyncRAT relies on correlating endpoint behavior with network communication rather than identifying a single static indicator.
Background processes executing commands outside expected user behavior often signal remote access activity. These executions usually persist longer than legitimate tasks and lack a clear business purpose.
Unexpected registry changes or startup execution paths indicate attempts to maintain long-term access. Persistence becomes more suspicious when paired with abnormal process behavior.
Repeated outbound connections to unfamiliar external destinations commonly reflect command-and-control activity. Regular timing or beacon-like behavior increases confidence even when traffic is encrypted.
Process creation, configuration changes, and memory activity reveal how the malware operates over time. Linking these signals helps separate real compromise from isolated noise.
Endpoint Detection and Response platforms are effective when execution, persistence, and communication events are tied together. Behavioral analysis reduces reliance on indicators that change across campaigns.
Reducing risk from AsyncRAT requires limiting initial access opportunities while shortening the time attackers can maintain control if a compromise occurs.
Strong email filtering reduces exposure to malicious attachments and links used in phishing campaigns. Attachment sandboxing and executable blocking are especially effective against RAT delivery.
System hardening limits the techniques malware can abuse after execution. Disabling unnecessary services and enforcing application control reduces post-compromise options.
Least-privilege access prevents malware from operating with elevated permissions. Restricting administrative rights limits lateral movement and system-level changes.
Regular patching reduces weaknesses that attackers may exploit after initial access. Updated systems also improve the effectiveness of endpoint security tools.
Security awareness training lowers the success rate of social engineering attacks. Users who recognize phishing attempts reduce the likelihood of initial execution.
Ongoing monitoring shortens dwell time by identifying abnormal behavior early. Faster detection limits data exposure and follow-on activity.
AsyncRAT continues to be a relevant threat due to its ability to provide persistent access and support a wide range of post-compromise activity. Its use across phishing-driven intrusions and more advanced operations shows how even older tools remain effective when paired with modern delivery techniques.
Effective defense depends on early detection, strong access controls, and continuous monitoring rather than reliance on single indicators. Treating AsyncRAT alerts as signals of deeper attacker intent helps organizations respond faster and reduce long-term impact.
