🚀 CloudSEK has raised $19M Series B1 Round – Powering the Future of Predictive Cybersecurity
Read more




As Canadian citizens increasingly rely on digital services for transportation, taxation, parcel delivery, and travel, threat actors continue to exploit this dependency by deploying highly convincing impersonation campaigns that mimic trusted government bodies and national brands. CloudSEK discovered multiple interconnected fraud clusters that abuse traffic ticket enforcement themes, tax refund narratives, airline booking portals, and postal delivery alerts to harvest personal and financial information at scale.
A significant portion of the activity is aligned with the “PayTool” phishing ecosystem, a known fraud framework that specializes in traffic violation and fine payment scams targeting Canadians through SMS-based social engineering.
In parallel, additional infrastructure was observed impersonating Canada Revenue Agency (CRA), Air Canada, and Canada Post, indicating a broader fraud operation that reuses common design patterns. Furthermore, the investigation uncovered threat actors actively commercializing these campaigns on underground forums by selling specialized phishing kits designed to mimic official government services and banking portals.
Victims are primarily seen lured using sms messages and malicious advertisements. Messages utilize high pressure tactics alleging unpaid fines, delivery failures, or booking errors to impersonate authoritative bodies like PayBC, CRA, Canada Post, and Air Canada. The use of URL shorteners or typosquatted domains adds a layer of perceived legitimacy.
Upon clicking, victims are not immediately asked for data. Instead, they are taken through a “fake validation” phase. This stage typically requests inputs such as ticket numbers, booking references, or account identifiers. However, these fields accept virtually any value and perform no real verification. Their sole purpose is to create an illusion of authenticity and to psychologically prime the victim by making the interaction appear official and procedural.
After this trust-building step, the site transitions to a fraudulent payment gateway. These pages closely mimic legitimate payment processors but in reality, they are engineered to harvest personally identifiable information (PII) and financial data.
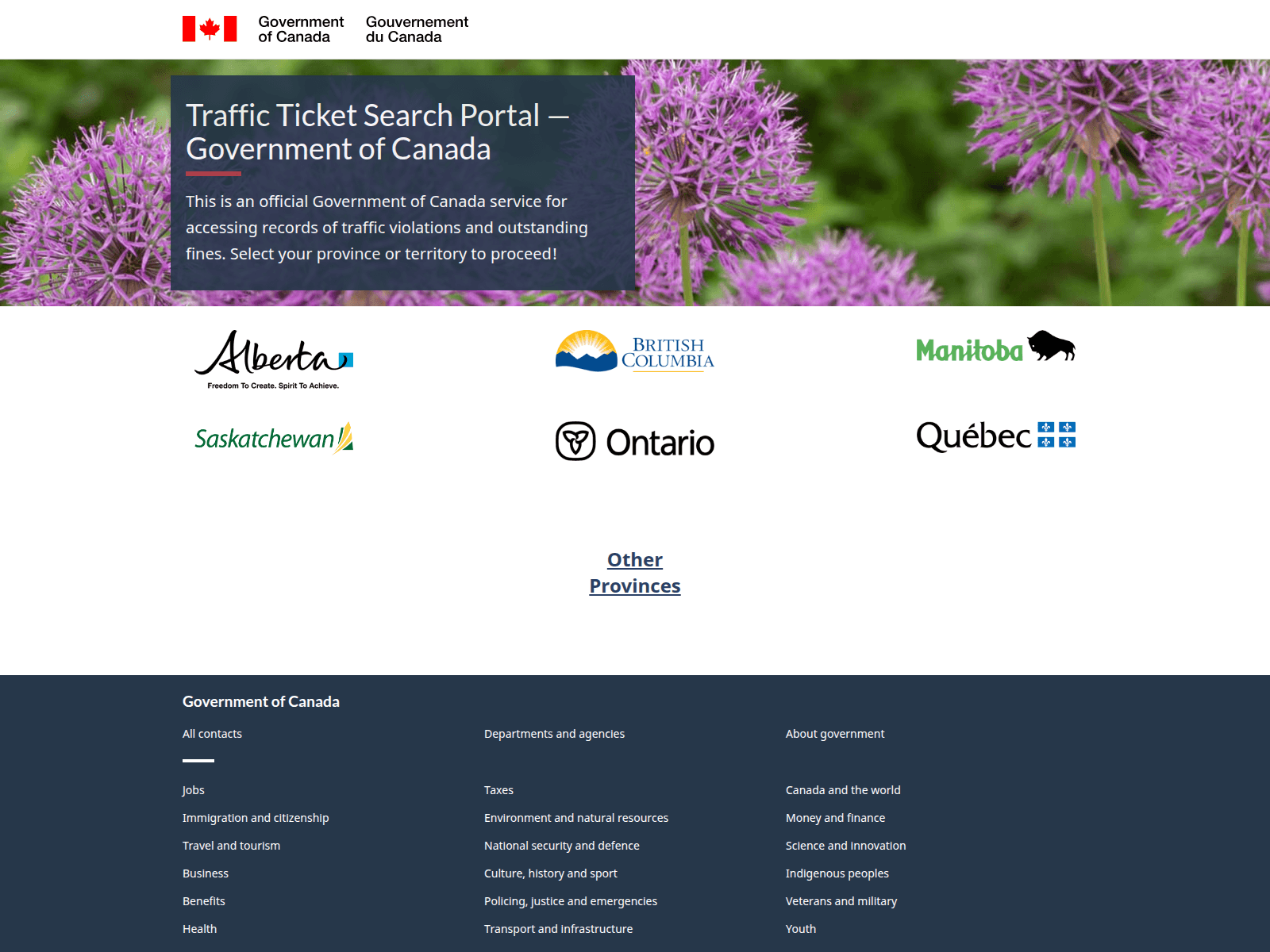
The core theme observed across multiple clusters in this campaign is the impersonation of Canadian government traffic enforcement and fine payment services. This activity strongly aligns with the previously documented “PayTool” ecosystem, which focuses on provincial traffic fines and parking violations, while also expanding into a broader federal-style “Traffic Ticket Search Portal” model that aggregates multiple provinces under a single interface.
Unlike simple single-page phishing sites, this infrastructure is designed to simulate a centralized government service. Victims are presented with what appears to be an official “Government of Canada” portal where they can select their province (Alberta, British Columbia, Ontario, Quebec, Manitoba, Saskatchewan, etc.) to search for outstanding traffic violations. This mirrors how legitimate Canadian federal services provide entry points to provincial systems, significantly strengthening the illusion of authenticity.
On analysis we found over 70 websites which were resolving to ip address 198[.]23[.]156[.]130 impersonating the legitimate canada.ca The inclusion of provincial logos and a “Traffic Ticket Search Portal – Government of Canada” banner establishes institutional trust before any data is requested.
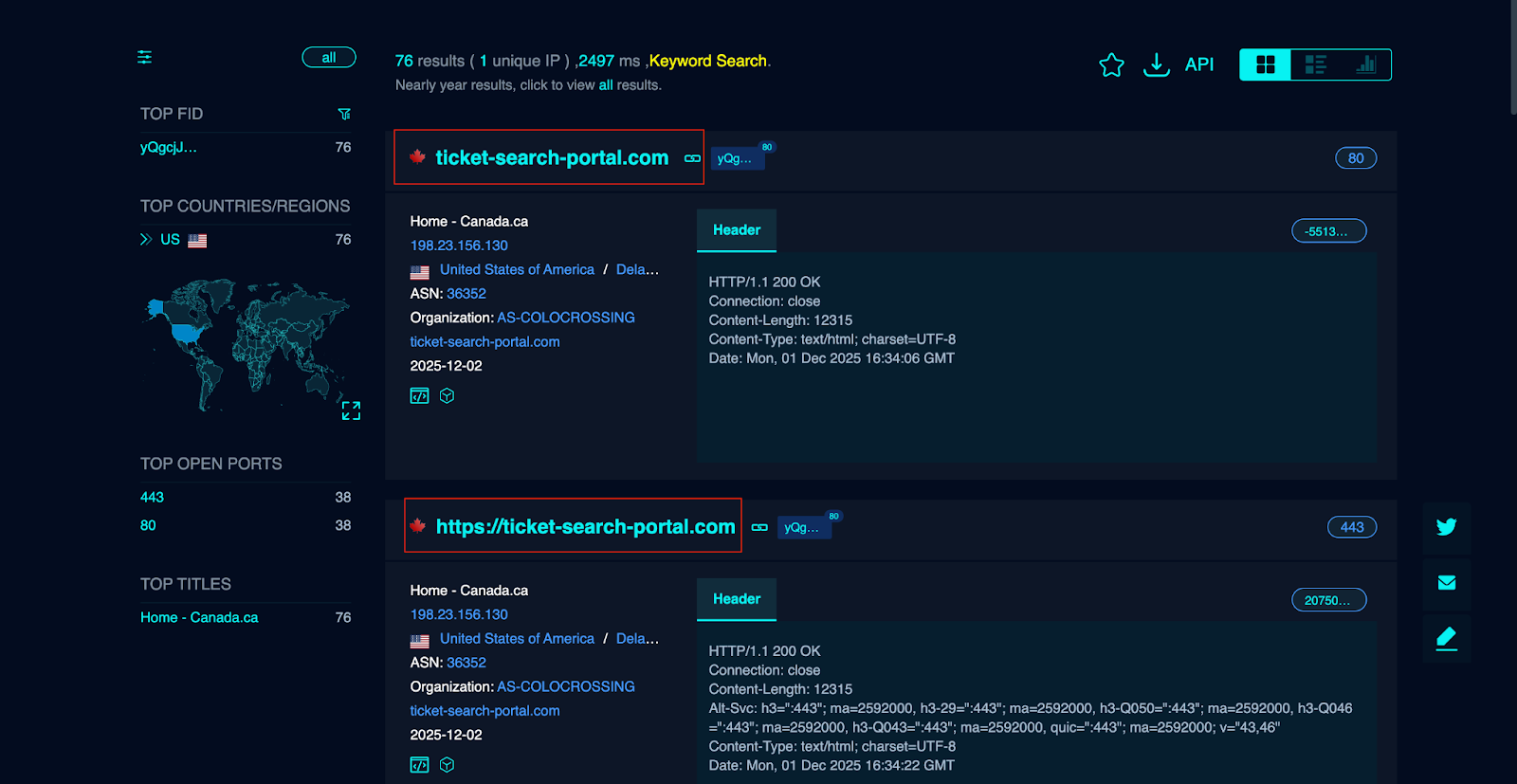
From an operational perspective, this structure serves three major purposes:
This workflow mirrors legitimate provincial traffic enforcement portals such as PayBC and ServiceOntario, making it consistent with known PayTool attack patterns.
The domains associated with this cluster exhibit highly systematic naming conventions centered around:
These naming patterns indicate automation and bulk generation rather than organic domain creation. The repetition of terms reinforces the legitimacy narrative by matching keywords users expect when dealing with official traffic violation services.
This activity is a direct conceptual extension of the PayTool group which traditionally impersonates provincial fine payment portals (PayBC, ServiceOntario, parking payment pages). This campaign expands that model by introducing a federal-style entry layer, simulating Canada.ca infrastructure before handing users off to province-themed portals.
The actual payment phishing kits (where the financial theft occurs) are hosted on a distinct infrastructure block. Passive DNS analysis reveals a high concentration of activity on the 45.156.87.0/24 subnet, specifically targeting Canadian provincial services.
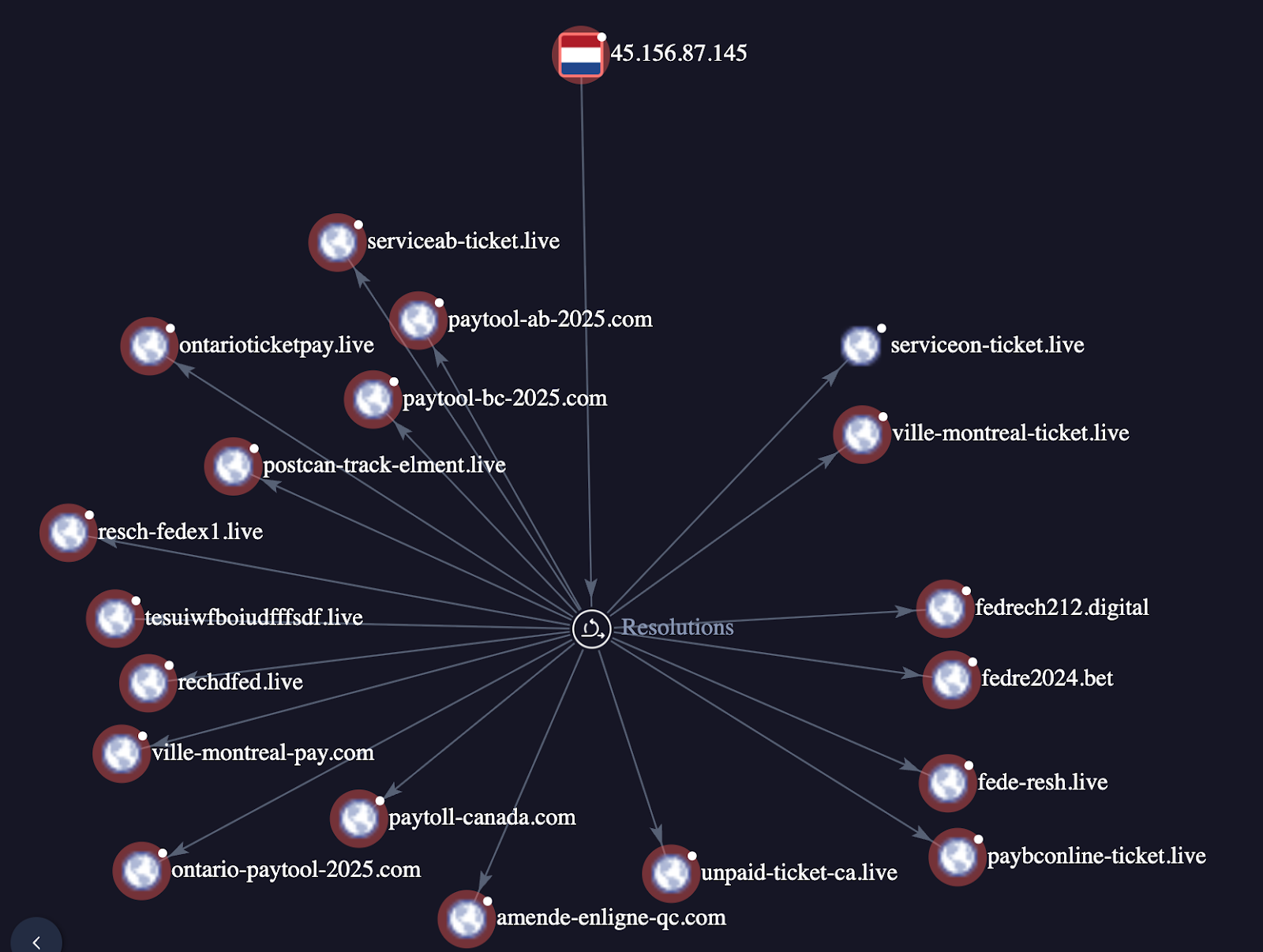
The infrastructure allows for simultaneous targeting across different jurisdictions using the same hosting provider. Based on domain relation data, we discovered multiple phishing domains of different provinces:
Beyond the direct government impersonations, the relation data for 162[.]243[.]100[.]252 and the 45.156.87.x subnet exposes a "long tail" of generic infraction domains, such as parking-portal[.]live and overdueticketinfraction[.]info.
This indicates that the PayTool threat actor maintains a pool of generic, fallback domains. When specific provincial domains (like paybc-portal) are inevitably flagged or blacklisted by browser vendors, the actor can immediately rotate traffic to these generic "infraction" sites to maintain campaign continuity.
Further analysis of the infrastructure revealed a subset of domains mimicking Canada Post. While these specific domains were inactive during the investigation, passive DNS data and reputation signals strongly suggest a campaign focused on parcel delivery scams.
The naming conventions heavily utilize keywords associated with "failed delivery" narratives:
Although the domains were offline, their clustering around the same hosting provider aligns with the broader "PayTool" and ticket-fraud infrastructure. This indicates a consistent pattern of brand trust exploitation using disposable domains to cast a wide net for victims.
Air Canada Impersonation & Typosquatting
A distinct branch of this campaign targets the travel sector through Air Canada impersonation. Unlike the ticket and postal scams, which rely heavily on SMS (Smishing), this cluster appears driven by SEO poisoning and typosquatting.
Observed domain patterns include:
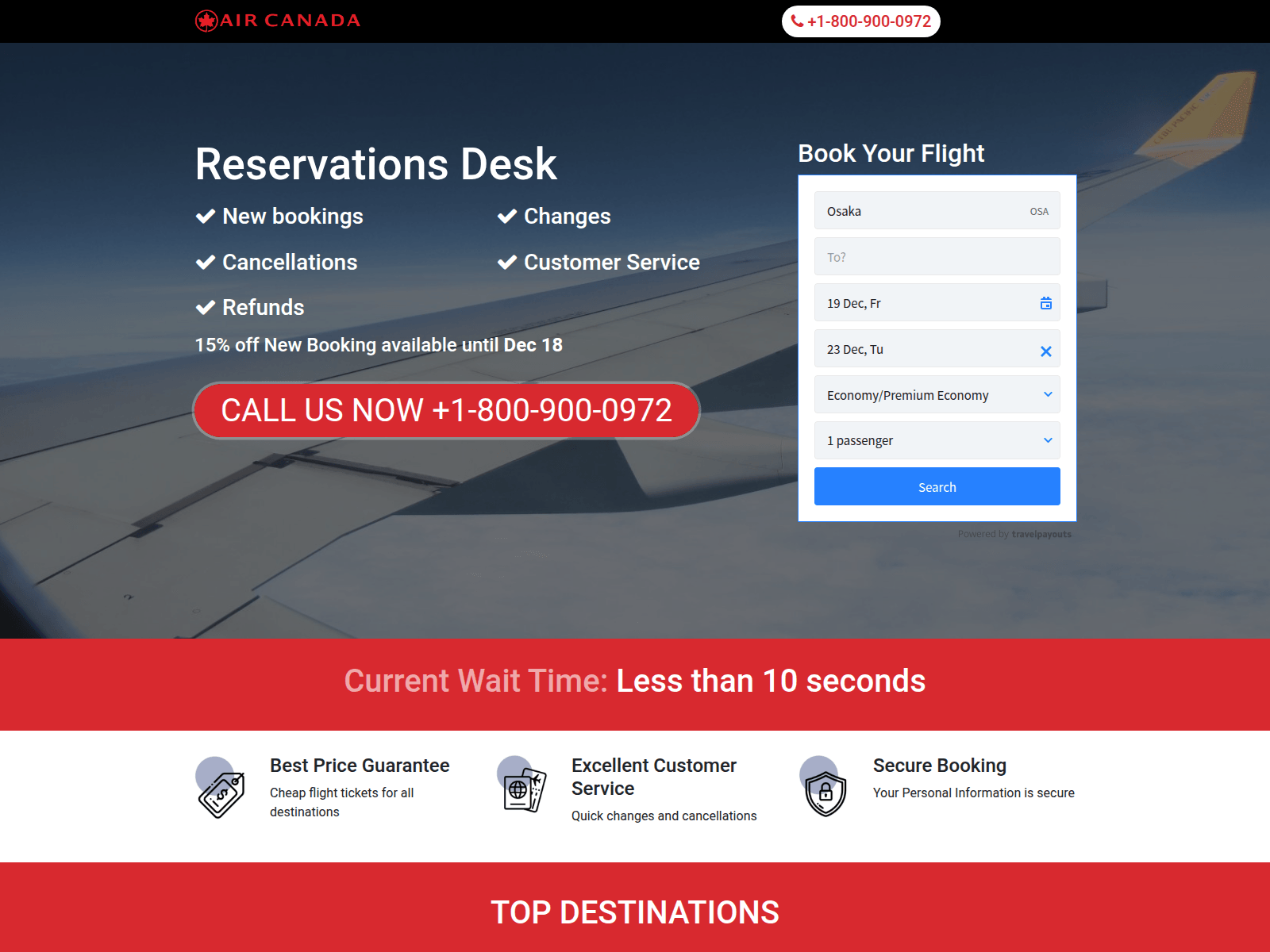
The objective is to intercept users who mistype the legitimate domain or click malicious search engine ads. Furthermore, FOFA queries identified multiple servers hosting these domains using:
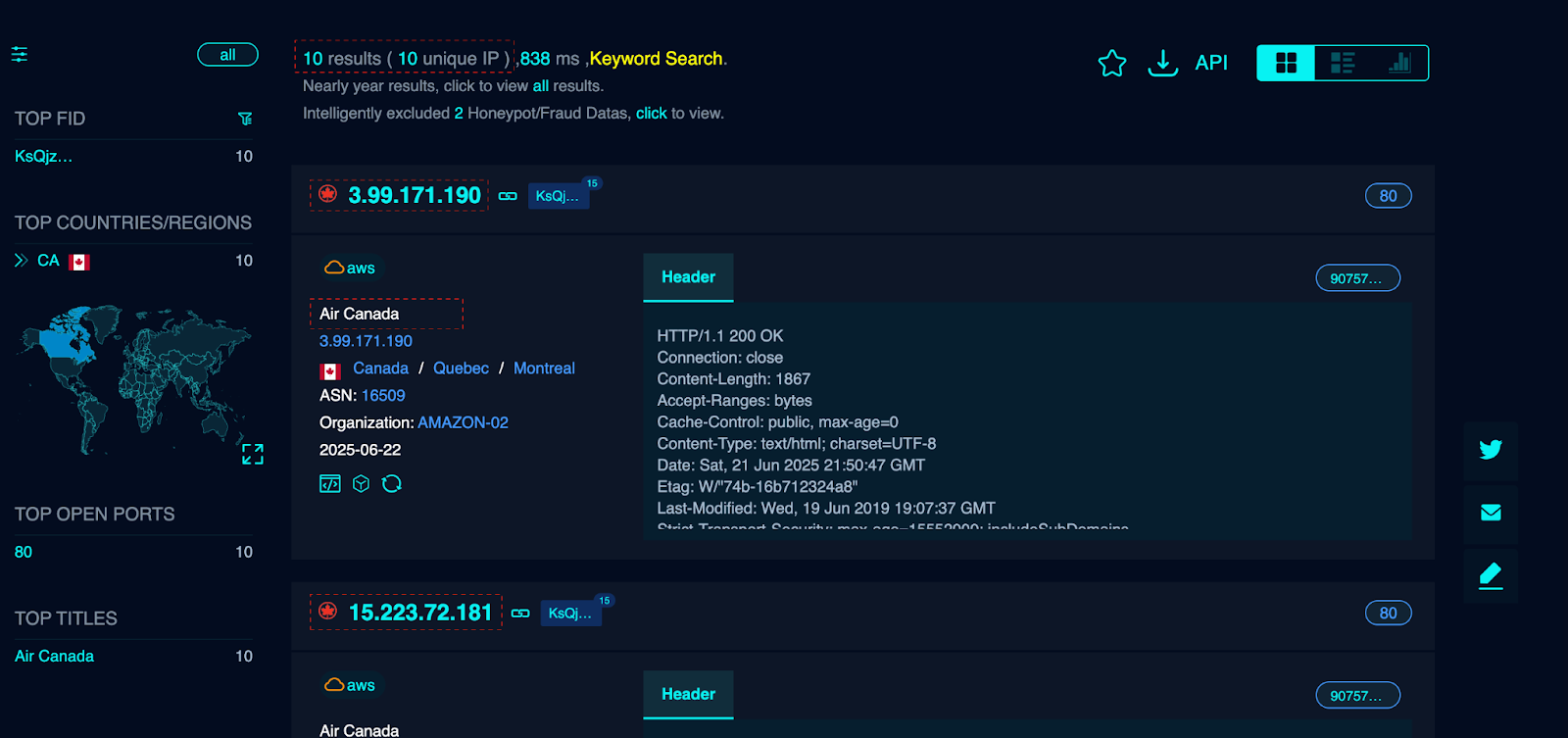
This confirms the deliberate cloning of legitimate branding assets rather than superficial imitation. The attackers likely leverage airline fraud because:
This expansion demonstrates that the threat actors are not limited to government service impersonation; they are effectively diversifying their targets to exploit commercial sectors where financial urgency is common.
Relationship With Underground Forums Activity
Intelligence gathered from various dark web cybercrime forums confirms that the proliferation of these localized campaigns is being driven by a "Phishing-as-a-Service" (PhaaS) model. Our analysis identified a threat actor operating under the alias 'theghostorder01', actively selling a specialized phishing kit designed to mimic the Ontario Driver's License Renewal process on multiple dark web forums.
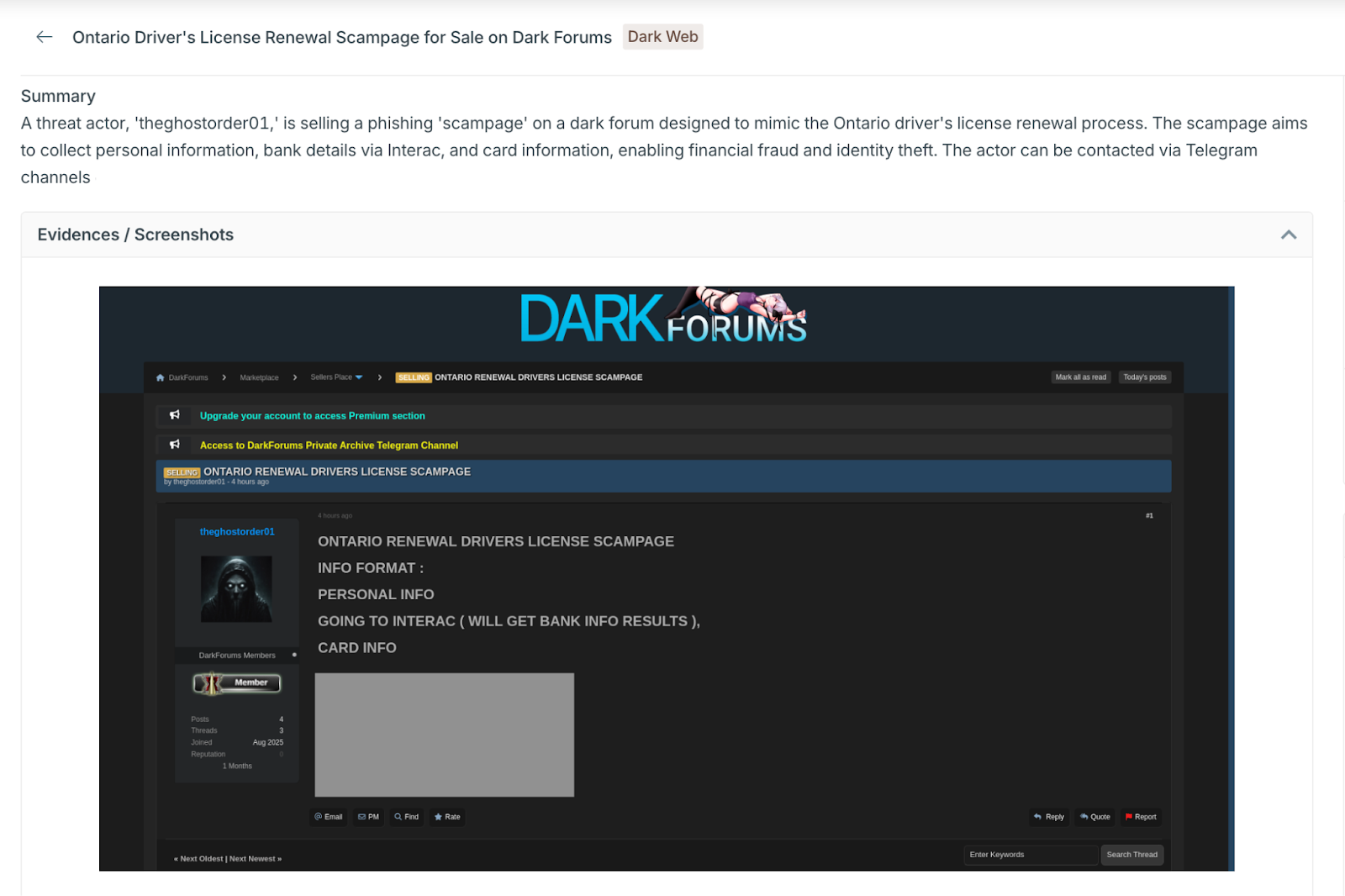
The advertisement highlights the kit's capability to harvest high-value data points, including:

The actor facilitates sales and support via different telegram channels. To validate these claims, one of our sources engaged with the threat actor. During the interaction, the seller was unable to demonstrate any server-side data handling or hosted infrastructure. Also when questioned about how victim data would be captured and delivered, the actor provided vague responses, stating that results would be sent via email or messaging platforms.
While the handling of the exfiltrated data is the responsibility of the buyer in most cases, the barrier of setting up the backend infrastructure has lowered significantly. Threat actors can now use Gen AI tools to rapidly script backend logic to process victim data. Additionally instead of a complex server-side database the victim data can be fetched via API and pushed directly to the bots and messaging platforms in real-time, a functionality that requires minimal technical skill to implement.
This investigation highlights a significant evolution in phishing campaigns targeting the Canadian demographic. Moving beyond generic "tax refund" lures, threat actors are now leveraging highly localized and context-aware themes ranging from PayBC speeding fines and ServiceOntario renewals to Air Canada booking modifications.
The discovery of phishing kit developers on the dark web confirms that this is a commoditized operation, ensuring a steady supply of fresh domains and updated templates.
As these attacks rely heavily on urgency (unpaid fines) and trust (government branding), organizations and users must remain vigilant against domains utilizing irregular TLDs (e.g., .live, .info) and verify links directly through official provincial portals.
45.156.87.145
45.156.87.131
45.156.87.143
45.156.87.213
198.23.156.130
162.243.100.252
192.109.138.183
209.141.50.110
3.99.171.190
15.223.72.181
35.183.85.238
3.97.15.116
35.183.132.238
35.182.194.55
3.96.139.96
15.156.206.92
3.97.9.55
99.79.60.130