🚀 CloudSEK becomes first Indian origin cybersecurity company to receive investment from US state fund
Read more



.jpg)
CloudSEK researchers have identified ZHGUI Cryptocurrency Ltd. as a coordinated mirror exchange and TRC20-based fraud ecosystem targeting Southeast Asian retail investors, with a strong focus on Malaysia’s Mandarin-speaking population and overseas Chinese users.
While ZHGUI markets itself as a U.S.-registered, fully compliant digital-asset exchange and cites a self-submitted FinCEN MSB registration, technical evidence contradicts this narrative. Infrastructure analysis reveals a constellation of cloned domains with identical UIs, Cloudflare-fronted delivery, AWS-backed management consoles, Udesk-style verification endpoints, and a public whitepaper authored using Chinese-language WPS software in China Standard Time, which collectively indicate a China-aligned operation hidden behind U.S. regulatory theatre.
Victim acquisition follows a social-engineering and grooming-driven playbook, primarily executed through WhatsApp investment groups and finance-themed social communities. Operators posing as “investment mentors” guide users through onboarding, KYC-style data collection, and small “test deposits” that appear profitable on fabricated dashboards. Once trust is established and larger deposits are made, withdrawals are blocked under the guise of tax reviews, compliance checks, or system errors. Public reporting from Malaysian media and community testimonies confirms multi-million ringgit losses, while OSINT on chat groups and admin accounts links this activity to a structured recruitment network operating at scale across the region.
On-chain analysis of TRON addresses associated with the ZHGUI ecosystem, including an internal “RazorPay Wallet on ZHGUI Exchange”, shows large USDT (TRC20) inflows and systematic onward transfers to intermediate “ZHGUI Wallet – R” routing addresses, internal “CHAIN” wallets, and multiple deposit addresses at major centralised exchanges such as Binance, OKX, HTX, KuCoin, and Bybit. This pattern demonstrates a mature laundering pipeline: aggregation of suspected victim funds, internal layering, and off-ramping through exchange infrastructure. In light of these findings, CloudSEK assesses ZHGUI as an ongoing cross-border financial-fraud threat and recommends platform-level disruption, financial-sector alerts, CEX reporting, continuous domain and wallet monitoring, and coordinated law-enforcement engagement. CloudSEK’s threat intelligence systems are actively tracking emerging domains, social infrastructure, and wallet activity associated with ZHGUI to support early detection and regulatory action.
ZHGUI is a fraudulent online investment ecosystem masquerading as a global cryptocurrency exchange. While it presents itself as a fully licensed digital-asset trading platform with international regulatory compliance, technical and OSINT evidence shows that ZHGUI functions as a mirror-exchange scam network designed to steal user funds and personal identity information.
The operation utilises multiple cloned domains, invitation-only onboarding, fabricated trading dashboards, and social media recruitment funnels to deceive victims into depositing money while displaying fake profits. It also exploits a self-submitted U.S. FinCEN MSB registration entry - a listing that is not government-verified nor proof of legitimacy — to create a false perception of regulatory authorisation.
ZHGUI’s infrastructure, support channels, and whitepaper metadata indicate China-based operational ties. At the same time, victim reports and group-chat evidence confirm active targeting of investors in Malaysia and broader Southeast Asia, particularly Mandarin-speaking communities. The platform’s primary objective is to simulate legitimate crypto trading, block withdrawals, harvest personal/KYC data, and disappear funds, positioning ZHGUI as an organised transnational financial fraud network rather than a genuine exchange.
1. Resilient Mirror Infrastructure: Deploys 10+ cloned domains (e.g., zhguihc.com, zhguize.com) behind Cloudflare CDNs and AWS-hosted backend sockets to simulate a robust US exchange while masking origin IPs.
2. Exploited Regulatory Loopholes: Leverages a self-submitted, unverified FinCEN MSB registration (No. 31000270792163) to manufacture "compliance" without actual government oversight or background checks.
3. Digital Fingerprints of Origin: Whitepaper metadata exposes the operation's true China-based nexus, containing "WPS Presentation" software tags and creation timestamps aligned with China Standard Time (+08:00).
4. Real-Time Deception Engine: Fake trading dashboards utilise WebSocket (socket.io) connections on subdomains like rtqs.zhguiwe.com to push simulated market data and create the illusion of live liquidity.
5. Automated Laundering Pipeline: Launders victim funds via TRON (TRC20) using labelled "RazorPay" aggregation wallets (e.g., TETzN...) that route assets through internal relays before off-ramping to Binance and OKX.
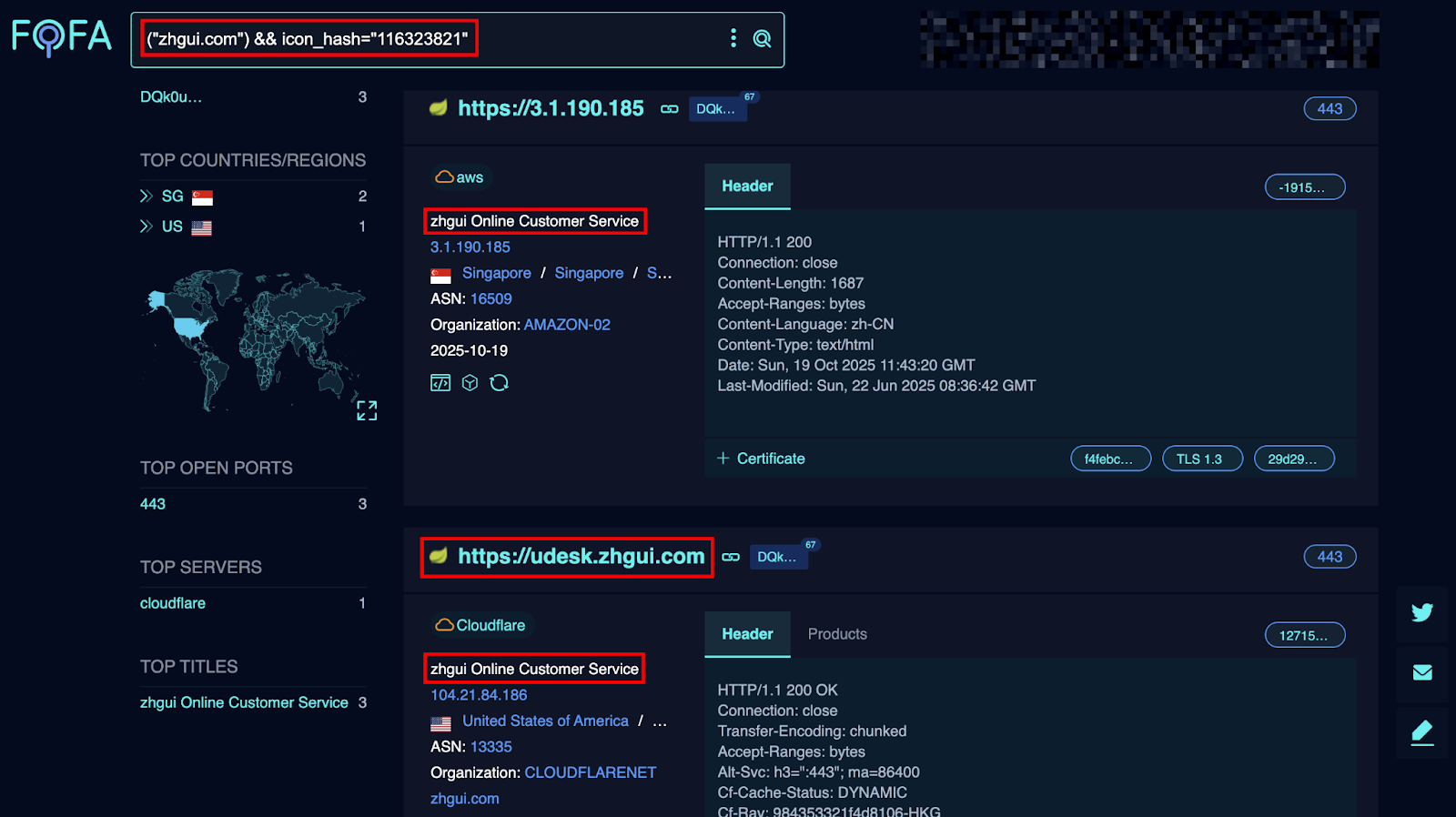
6. Weaponised Support Portals: Embeds Udesk customer service integrations (e.g., udesk.zhgui.com) to harvest sensitive PII and KYC documents under the guise of identity verification.
7. Mobile Ecosystem Infiltration: Bypassed Apple’s app review process to publish a fraudulent trading app, "ZHGUI GE" (ID: 6747241718), expanding the attack vector beyond web browsers.
8. Social Engineering Funnels: Orchestrates victim acquisition via "pig-butchering" scripts in closed WhatsApp/Telegram groups, targeting Mandarin speakers in Southeast Asia with fake "investment mentors".
9. SEO & Reputation Manipulation: Executes a "reputation laundering" campaign using paid press releases on financial sites (e.g., TechBullion) to saturate search results with fabricated narratives of institutional legitimacy.
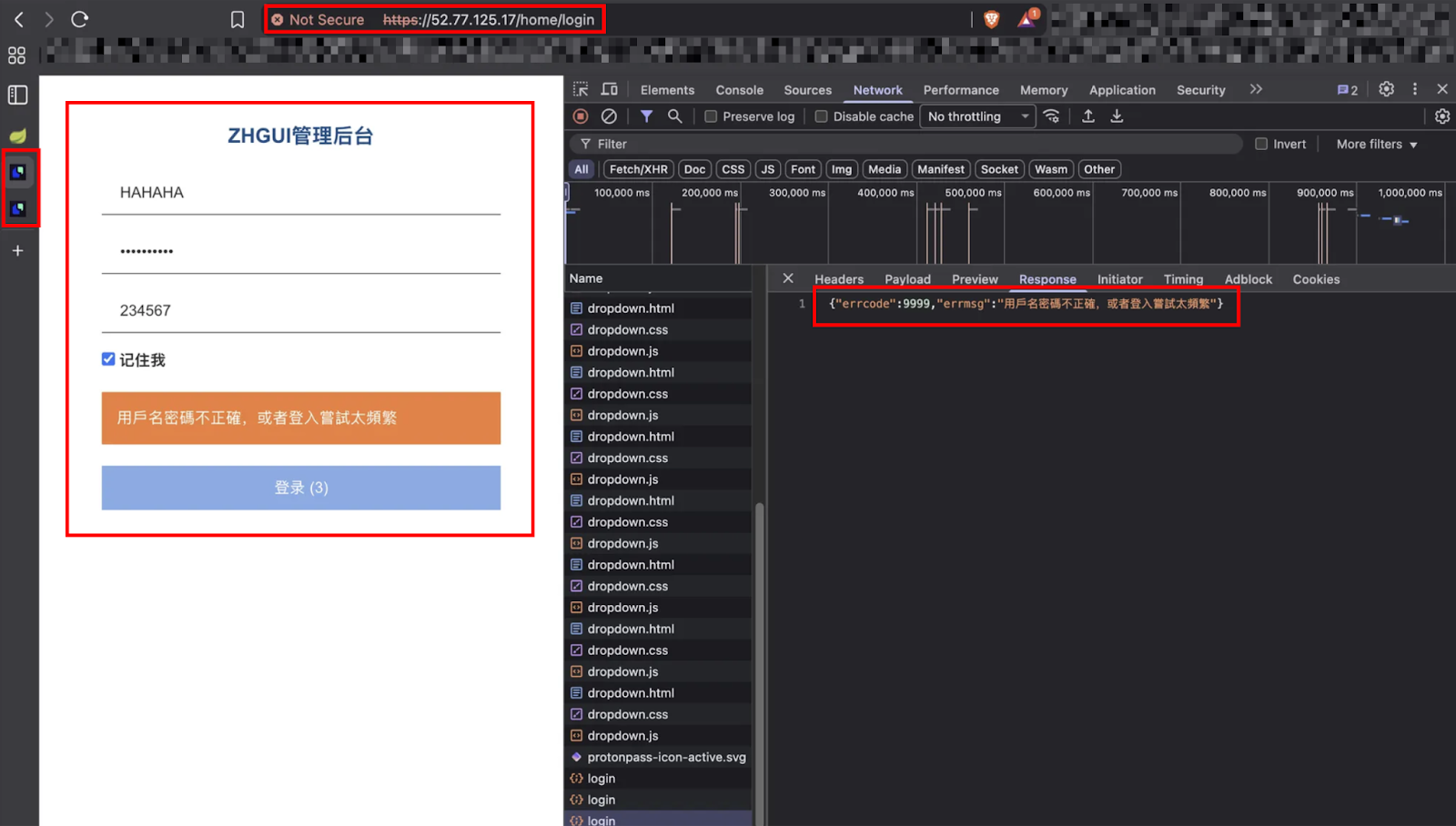
10. "Tax Review" Kill Switch: Scripts the final theft phase by blocking withdrawals under a fake "tax review" status, while backend management consoles (52.77.125.17) continue to track victim deposits.
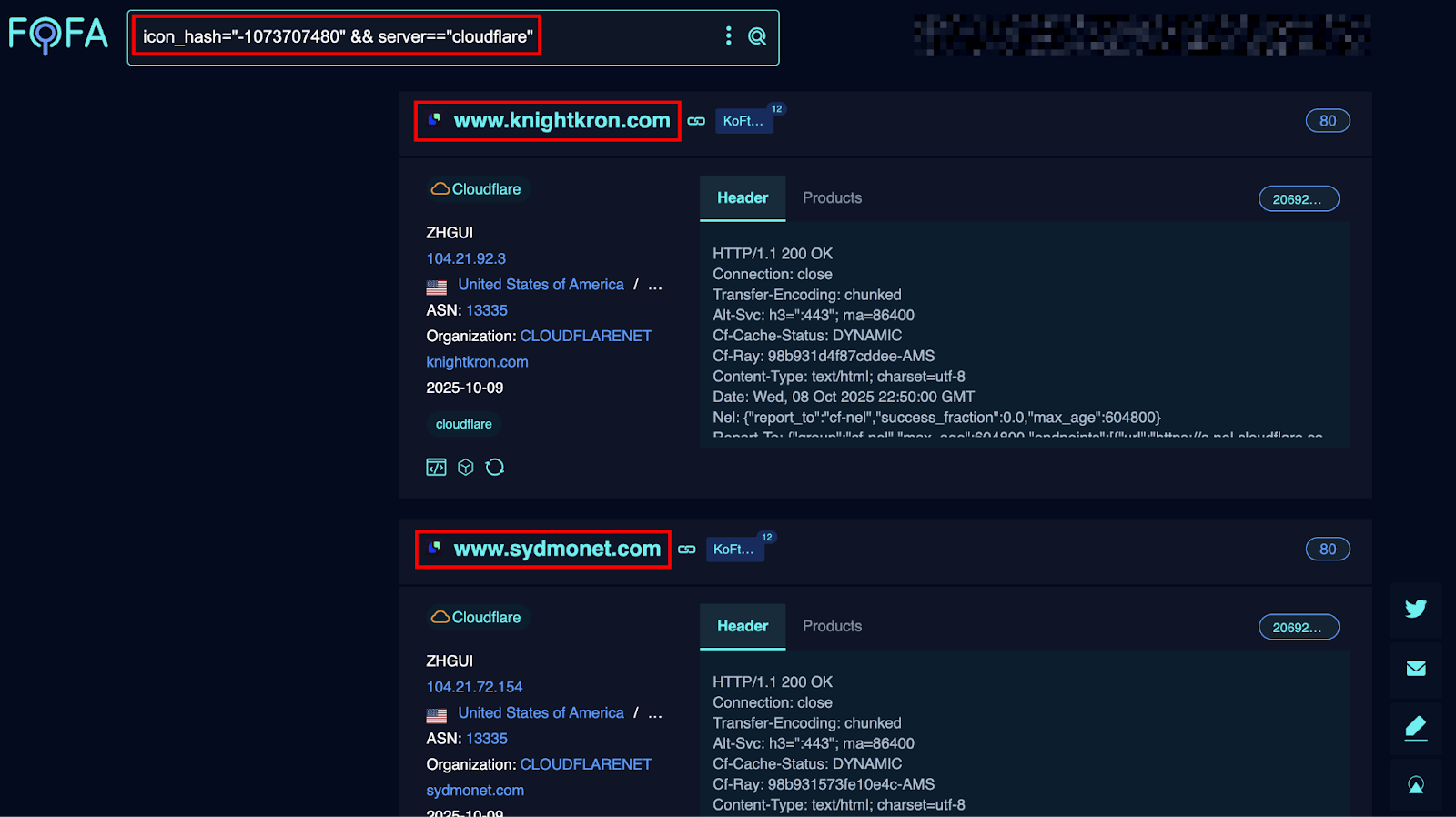
A cluster of 10+ domains was identified, all reflecting identical or nearly identical front-end structures, visual assets, and back-end script calls. These domains are active mirrors of each other and appear to redirect or replicate the scam login and investment pages.
All of the above domains serve identical login portals designed to collect user credentials, crypto wallet information, and KYC verification details. The use of Cloudflare CDN IPs suggests an attempt to obfuscate real hosting origins, while some AWS IPs indicate backend management and socket communication servers.
Additional mirror sites identified through favicon hash correlation :
##Hash Value: 1ca2e500f792fdce9128e8f26fd0a5c10b3f06f1047ce5217e5789db9b33681b##
Both domains replicate identical ZHGUI interfaces, further confirming the reuse of template-based infrastructure.
Two non-Cloudflare IPs were discovered serving as internal management consoles, potentially used by operators for backend access or administrative control:
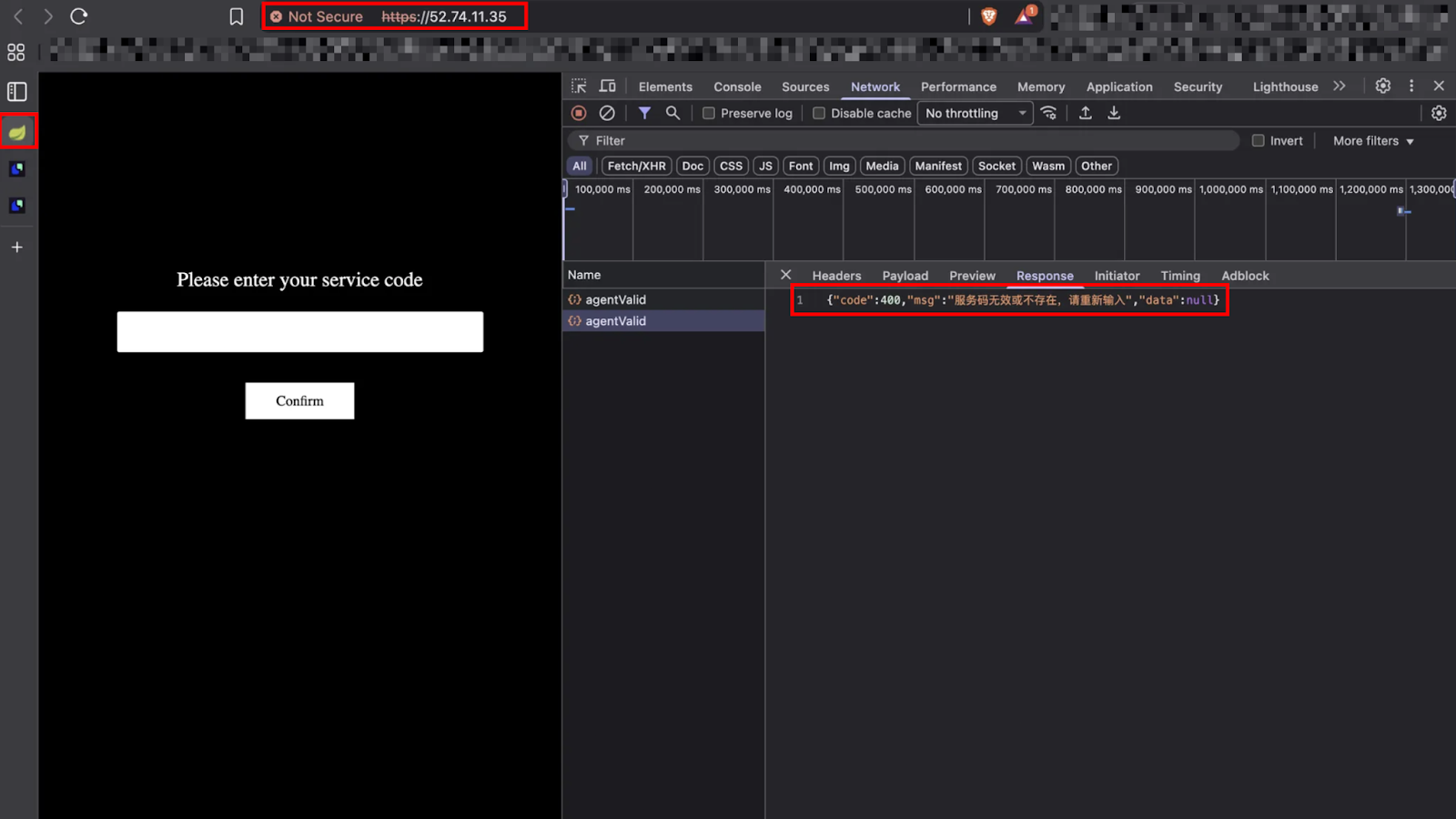
These IPs likely represent the core servers used for backend database access and credential collection.
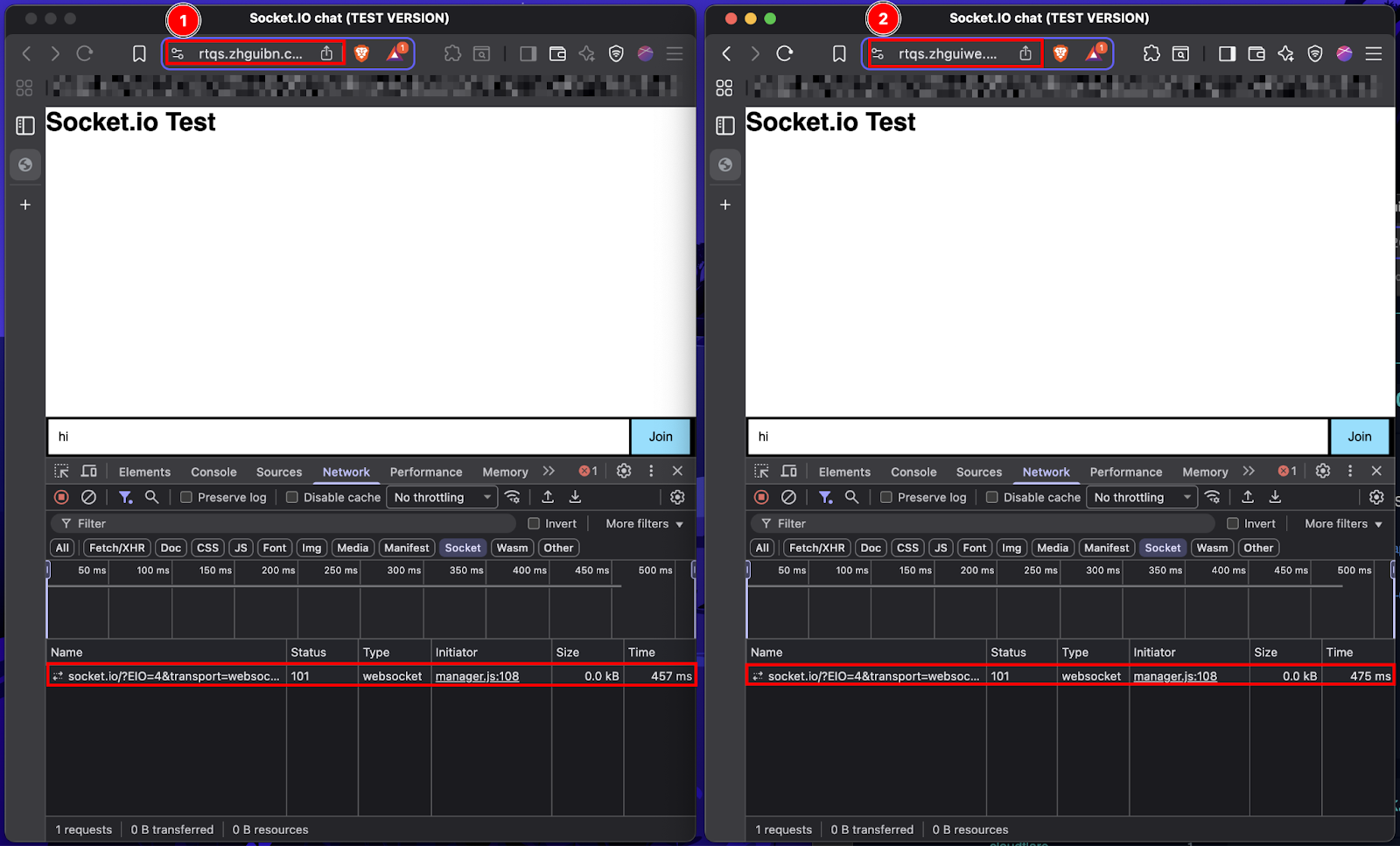
The above subdomains were identified as hosting WebSocket services likely used to update “fake trading dashboards” in real time, simulating active cryptocurrency transactions to create an illusion of authenticity for victims.
A highly suspicious URL was found embedded within the site’s JavaScript file:
##URL: https://1884145.s5.udesk.cn/im_client/?web_plugin_id=350&language=en-us&im_user_key=66666##
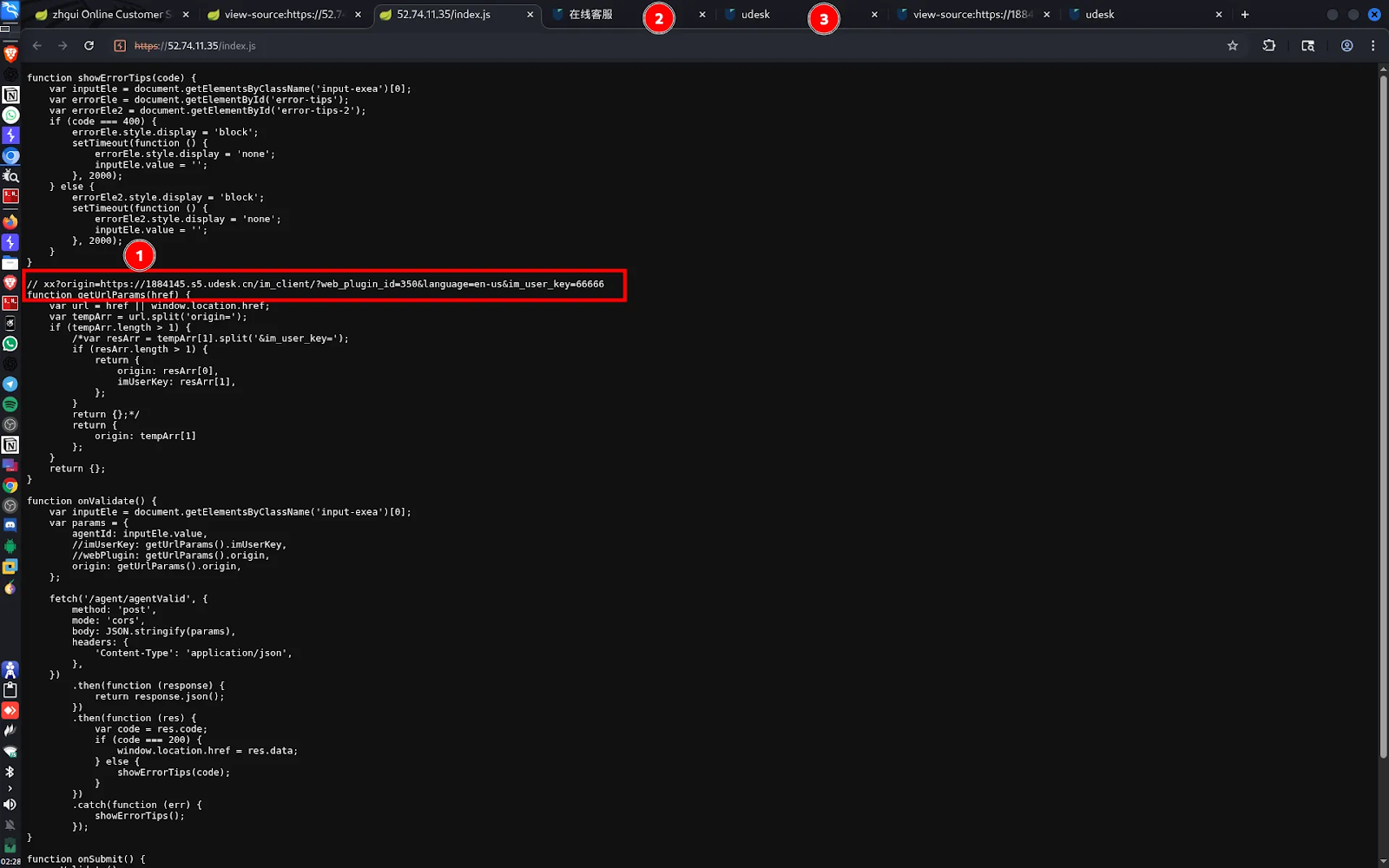
Further investigation revealed a connected endpoint:
##URL: https://1884145.udeskglobal.com/sim##
A SIM verification login page, possibly used as a fake verification or communication support portal.
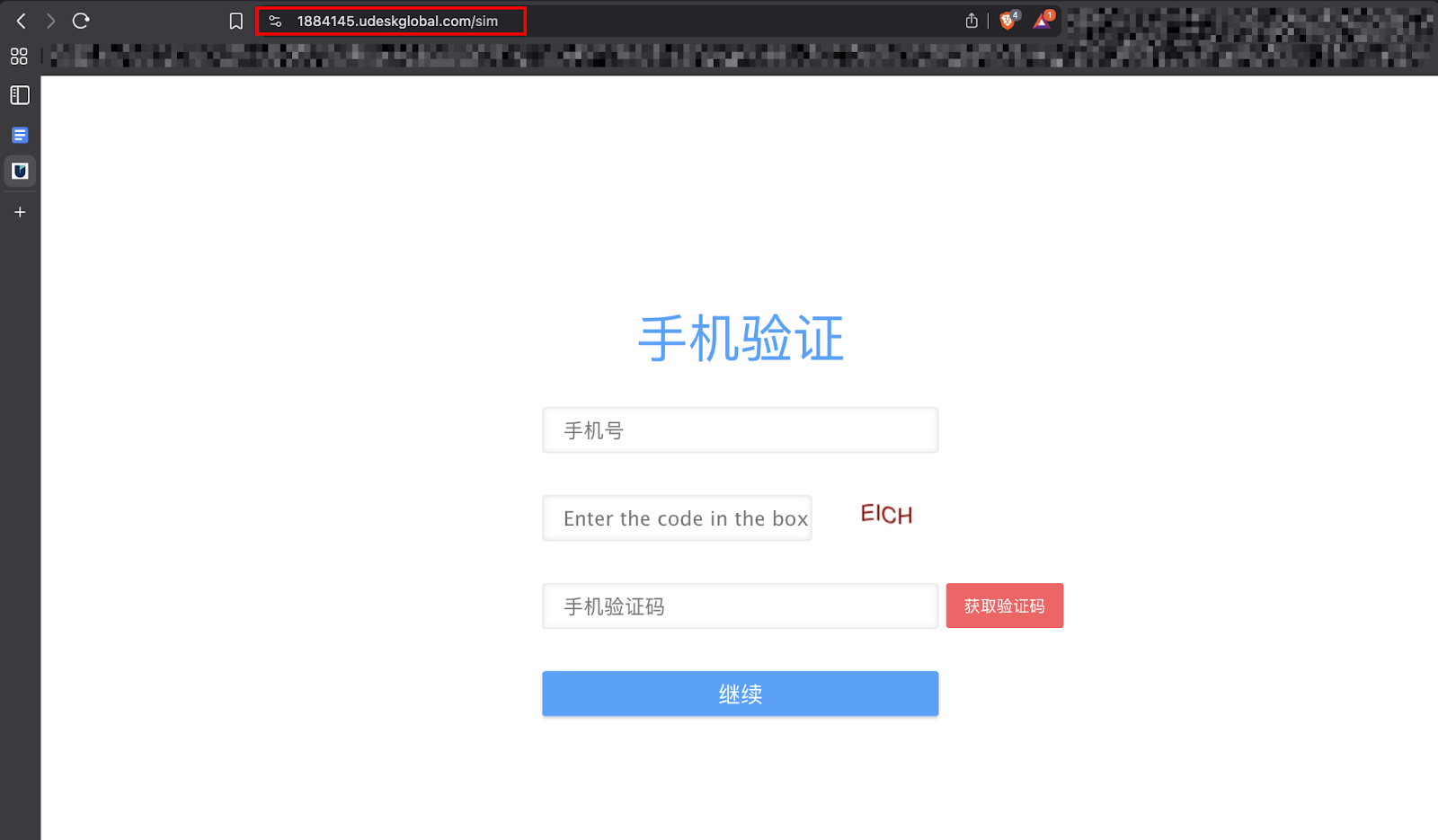
This suggests the scam operators might be leveraging Udesk-like cloned support pages to harvest user identity or KYC data under the pretence of customer service verification.
As part of controlled testing, an investigative email was sent to support@zhgui.org.
In response, the sender received an invitation code required for account creation on the ZHGUI exchange portal, confirming the active nature of the support system and validating that operational infrastructure remains online despite ongoing domain takedowns. This establishes that,
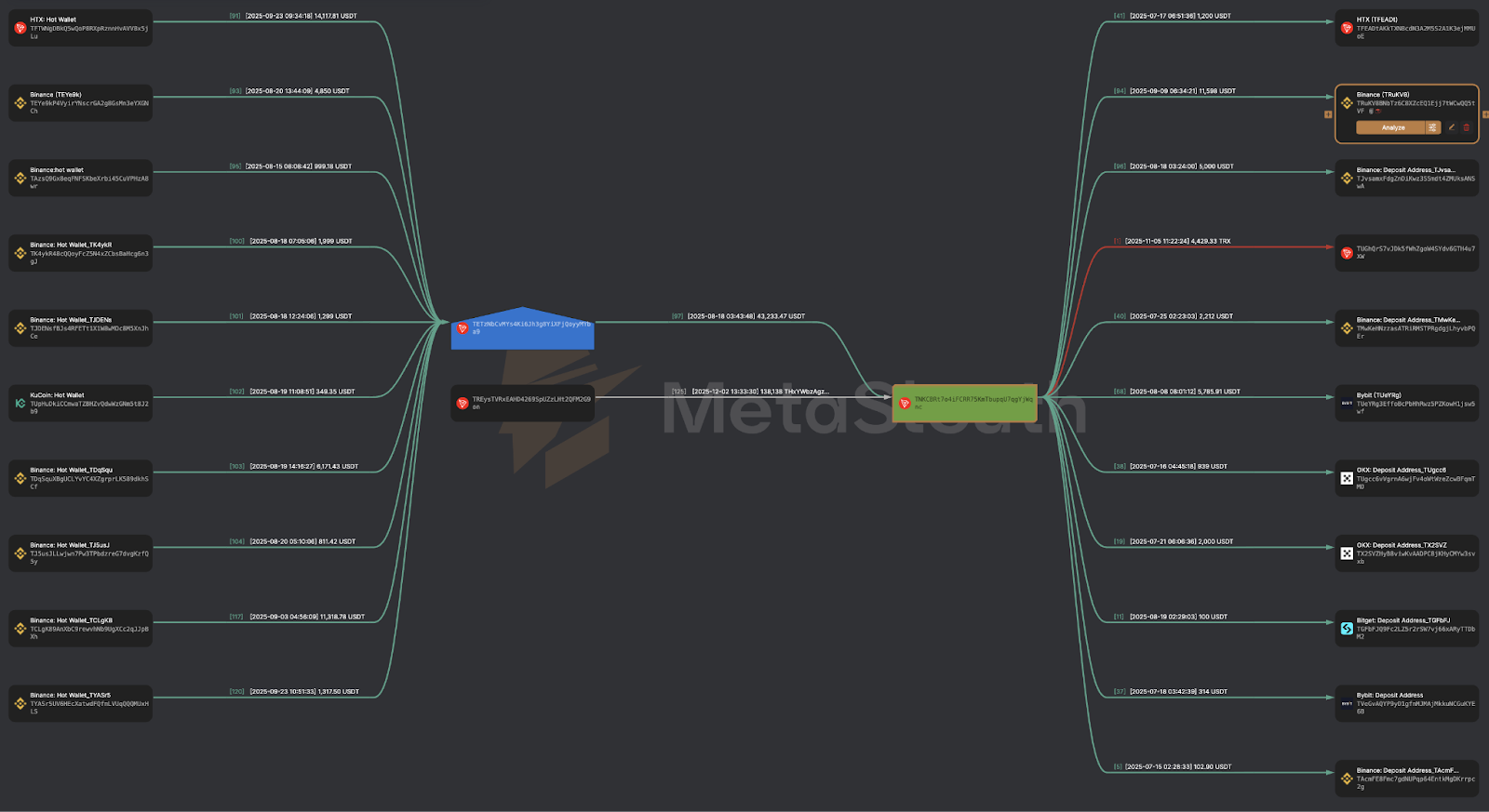
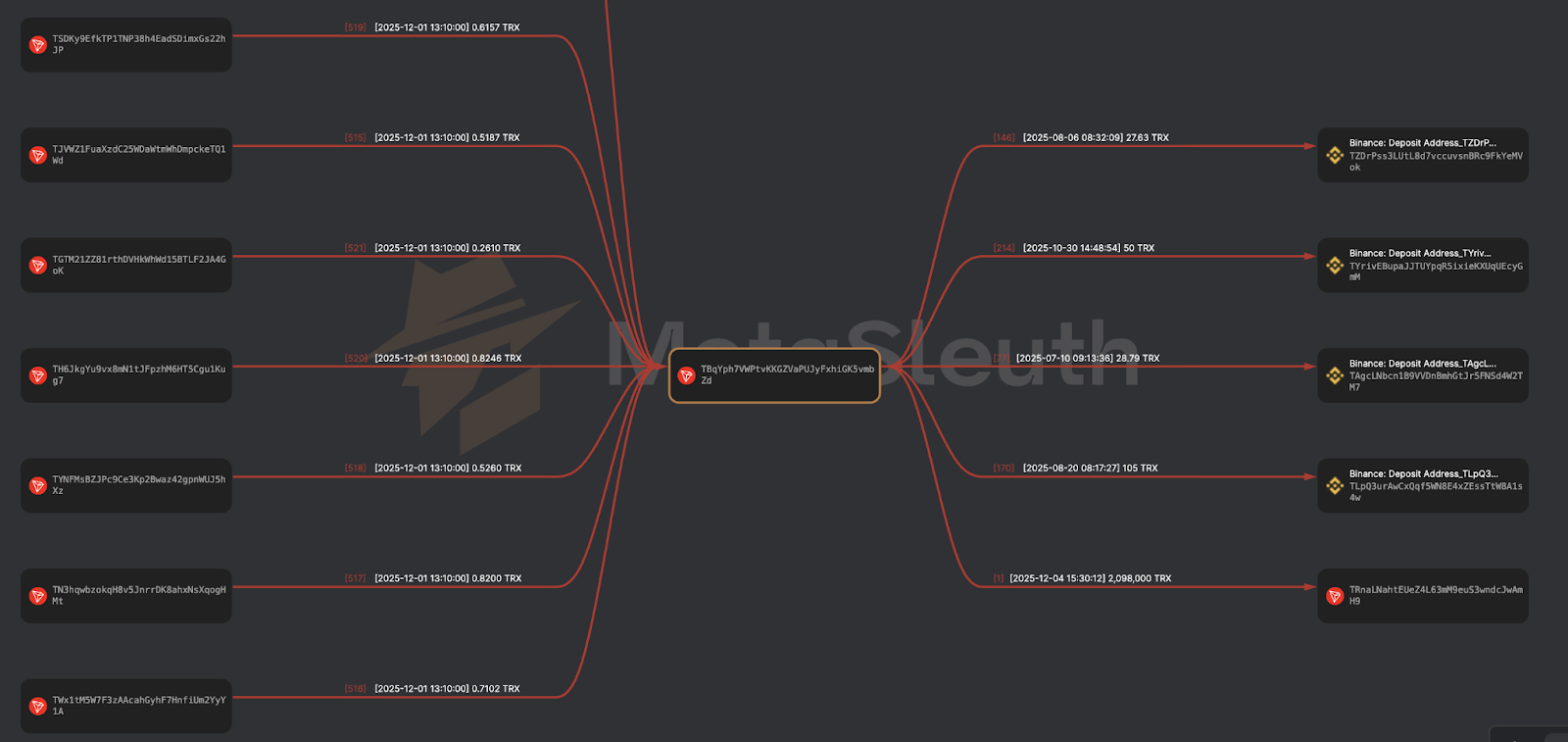
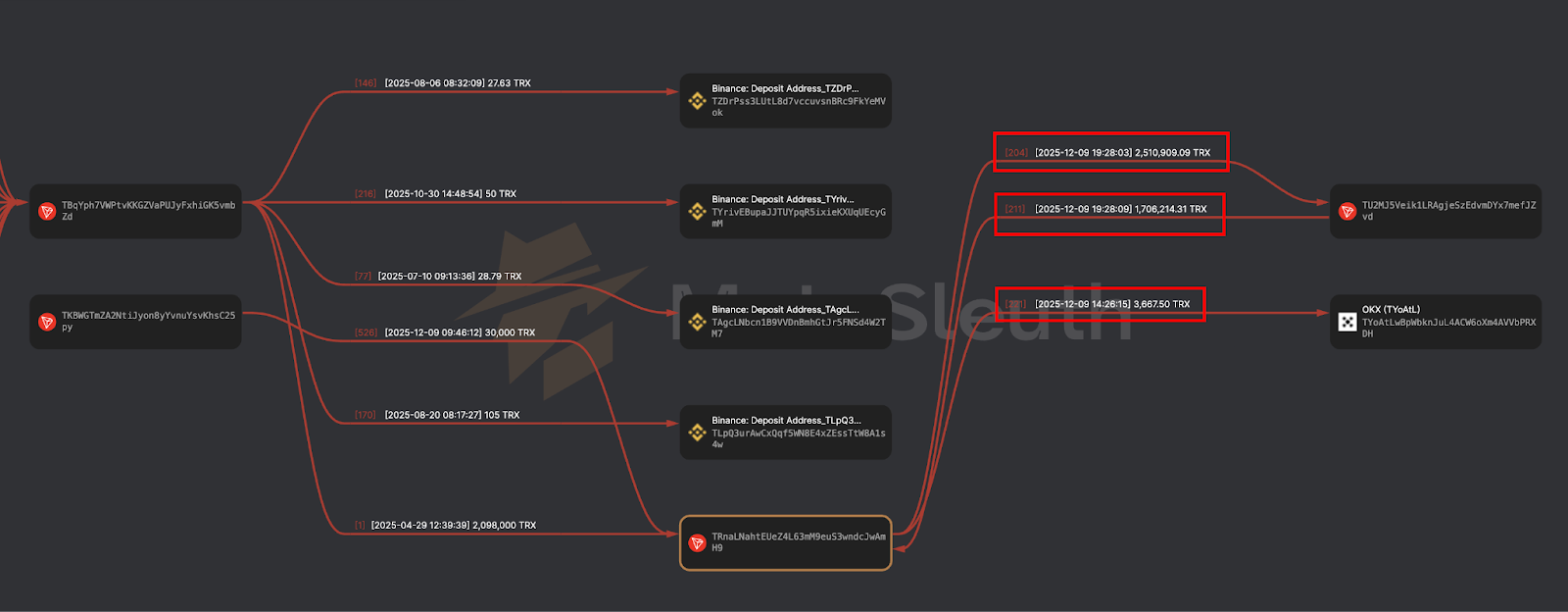
As part of the investigation, on-chain analysis was performed on the TRON address TETzNbCvMYs4Ki6Jh3g8YiXFjQoyyMYba9, internally labelled as “RazorPay Wallet on ZHGUI Exchange”. This wallet functions as an internal aggregation and routing hub for USDT (TRC-20) flows associated with ZHGUI’s merchant-style payment layer.
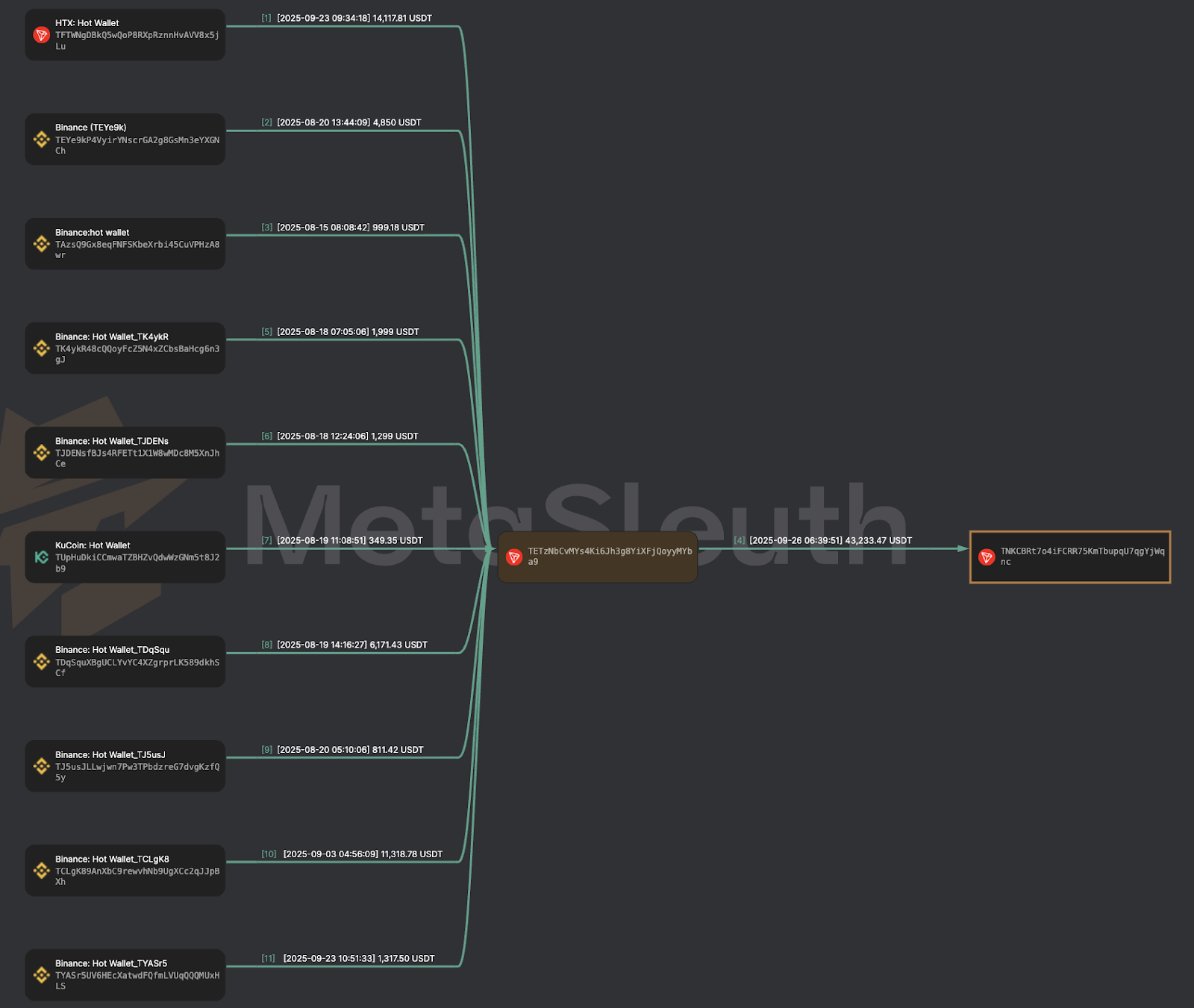
The on-chain flows centred on TETzNbCvMYs4Ki6Jh3g8YiXFjQoyyMYba9 and TNKCBRt7o4iFCRR75KmTbupqU7qgYjWqnc demonstrate that ZHGUI maintains a dedicated TRON-based treasury and laundering pipeline, which:
This behaviour is fully aligned with professional scam and money-laundering operations, characterised by structured layering, controlled aggregation, and systematic off-ramping through major exchanges. These addresses should be treated as high-risk / suspected fraud wallets and added to the IOC set for monitoring, blocking, and exchange-based investigation/escalation.
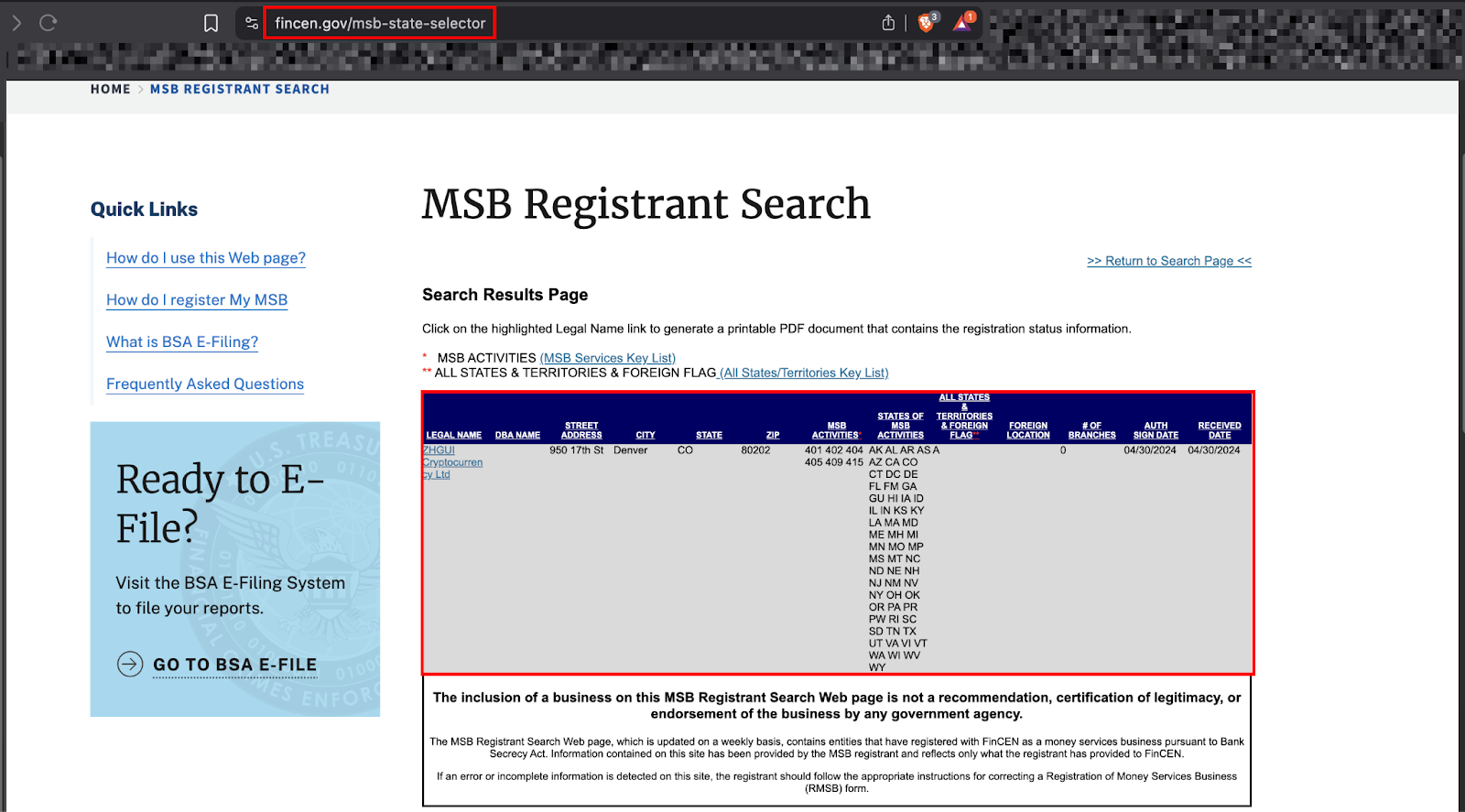
During the analysis of artefacts and documents related to the ZHGUI ecosystem, investigators recovered a white paper referencing an official Money Services Business (MSB) registration. Upon verification through the Financial Crimes Enforcement Network (FinCEN) public MSB registry, a registration entry was indeed found, registered on October 22, 2025, under the entity name ZHGUI Cryptocurrency Ltd.
However, a detailed examination of the transcript and associated notes from FinCEN’s website revealed that the listing is self-submitted, unverified and explicitly warns that inclusion on the registry does not imply authenticity or government approval.
The entity details are as follows:
##MSB Registration Number: 31000270792163
Registration Type: Initial Registration
Legal Name: ZHGUI Cryptocurrency Ltd
Street Address: 950 17th St, Denver, COLORADO, 80202
Authorised Signature Date: 04/30/2024
Received Date: 04/30/2024
MSB Activities:
Dealer in foreign exchange, Issuer of money orders, Money transmitter, Seller of money orders
States of Activities: All U.S. States and Territories
Number of Branches: 0##
This information has been strategically used to deceive users into believing ZHGUI is a legitimate, U.S.-regulated cryptocurrency exchange.
The registration, while present in the FinCEN database, was not verified or endorsed by the agency, aligning with the pattern of fraudulent legitimacy often used in crypto scam networks.
##NOTE: FinCEN explicitly states that registration data is “self-reported” and may include false or misleading claims used in scams.##
##URL: https://msb.fincen.gov/msb.registration.letter.php?ID=28612373##
A document titled “ZHGUI-Whitepaper-EN.pdf”, available publicly at their website, was analysed for embedded metadata using the exiftool utility.
##URL: https://doc.zhgui.com/ZHGUI-Whitepaper-EN.pdf##
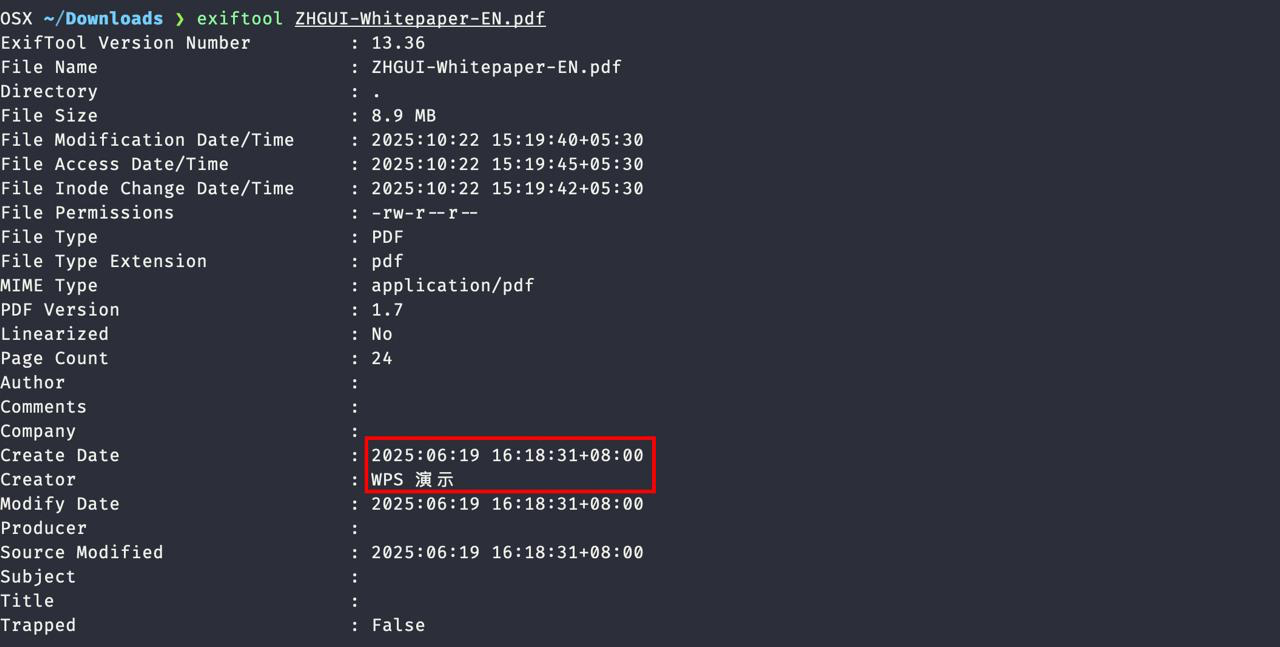
##File Size: 8.9 MB
Page Count: 24
PDF Version: 1.7
Create Date: 2025:06:19 16:18:31+08:00
Modify Date: 2025:06:19 16:18:31+08:00
Creator: WPS 演示
File Modification Date/Time: 2025:10:22 15:19:40+05:30##
Further investigation uncovered multiple verified victim cases and public reporting linking significant financial losses to the ZHGUI platform in Southeast Asia. The earliest documented case, published by China Press Malaysia on 16 October 2025, details a Malaysian investor who lost approximately 340,000 MYR (~USD 70,000) after being lured into the ZHGUI platform via online investment channels. The victim was recruited through a financial-discussion community and guided to register on the platform under the belief it was a genuine, compliant cryptocurrency exchange.
##Source: https://perak.chinapress.com.my/20251016/又是虚拟币投资圈套-华男3个月没了34万!/##

A second major case surfaced shortly after via regional financial-fraud reporting, documenting losses of approximately 3,000,000 MYR (~USD 630,000). In this instance, the victim was introduced to ZHGUI through WhatsApp investment groups, where individuals posing as financial mentors provided trade “signals,” fake performance screenshots, and personalised guidance to escalate deposits. This aligns with ZHGUI’s social-engineering strategy focused on high-touch grooming, staged profit dashboards, and trust-based onboarding funnels.
##Source: https://www.wikifx.me/en/newsdetail/202510231334676397.html##
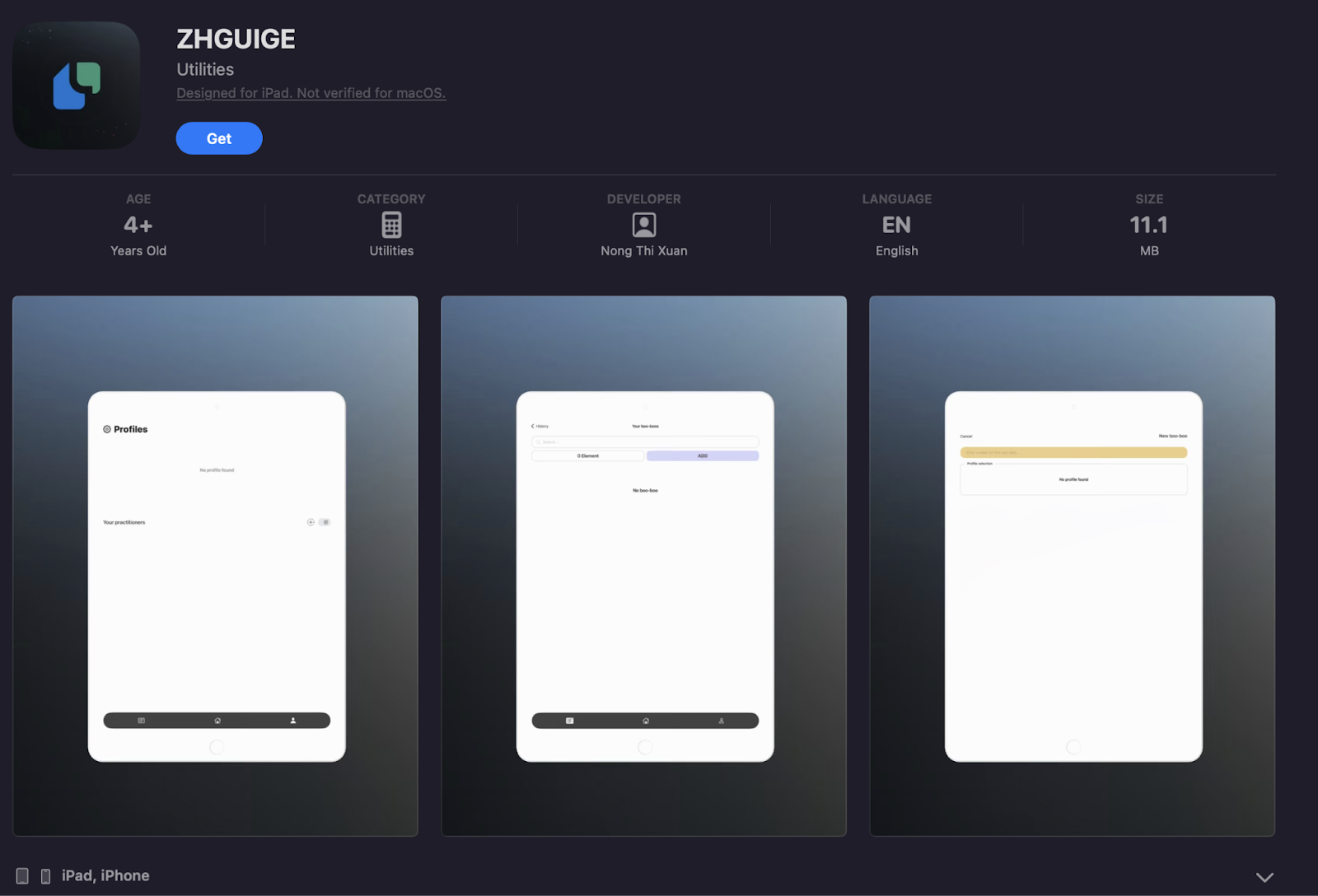
Technical validation also confirmed a ZHGUI-branded iOS application (“ZHGUI GE”) previously published on the Apple App Store. Though the app has since been removed, its existence demonstrates the actors’ effort to reinforce legitimacy and broaden distribution channels beyond web infrastructure.
##App Store: https://apps.apple.com/us/app/zhguige/id6747241718##
The combination of confirmed monetary losses, active WhatsApp-based recruitment networks, documented operator phone numbers, and historical mobile-app deployment strengthens the assessment that ZHGUI operates as a coordinated, multi-channel financial fraud network leveraging deception, fake legitimacy signals, and social-engineering tactics to target Mandarin-speaking investors across Southeast Asia.
During the investigation, CloudSEK identified a large network of news articles, blog posts, PR distributions, and paid media placements designed to artificially portray ZHGUI as a trusted, licensed, and globally recognised cryptocurrency exchange. These publications consistently promote ZHGUI using scripted narratives, exaggerated trust claims, and references to self-submitted regulatory documents such as the FinCEN MSB registration
The content across these platforms follows a uniform pattern:
Many of these articles are published on press-release distribution platforms, syndication networks, and low-editorial-review financial blogs, indicating a structured legitimacy laundering campaign intended to improve search-engine presence, mislead potential investors, and mask fraudulent behaviour under corporate-style storytelling.
The following publications were identified as part of the ZHGUI promotional network:
Counter-Evidence & Community Warnings
Amid these promotional narratives, community-driven platforms have published warnings identifying ZHGUI as a scam:
This negative commentary directly contradicts the claims made in the promotional articles and aligns with confirmed victim losses and technical evidence uncovered in our investigation.
These promotional articles were designed to legitimise the ZHGUI brand, frequently referencing the following details:
##Entity: ZHGUI Cryptocurrency Ltd
Contact Person: Irfan Saiful
Email: support@zhgui.org
Website: https://www.zhgui.org
Registered Address: Colorado, USA##
Analysis of publication patterns and metadata suggests that these articles were likely sponsored press releases distributed through automated PR networks, intended to increase visibility and credibility within search engines and social media.
The threat actors maintain multiple social media profiles masquerading as legitimate representatives of “ZHGUI Exchange”.
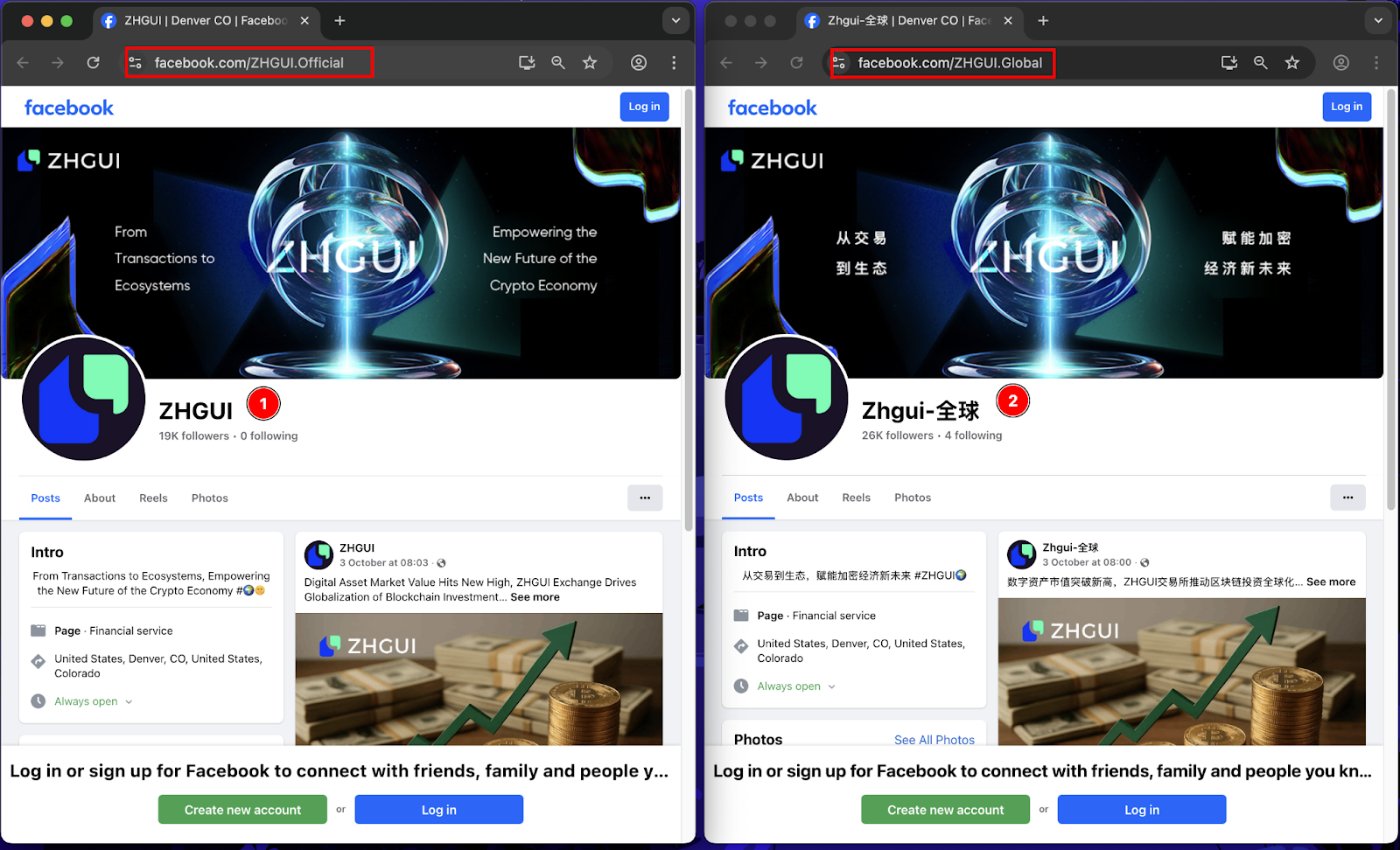
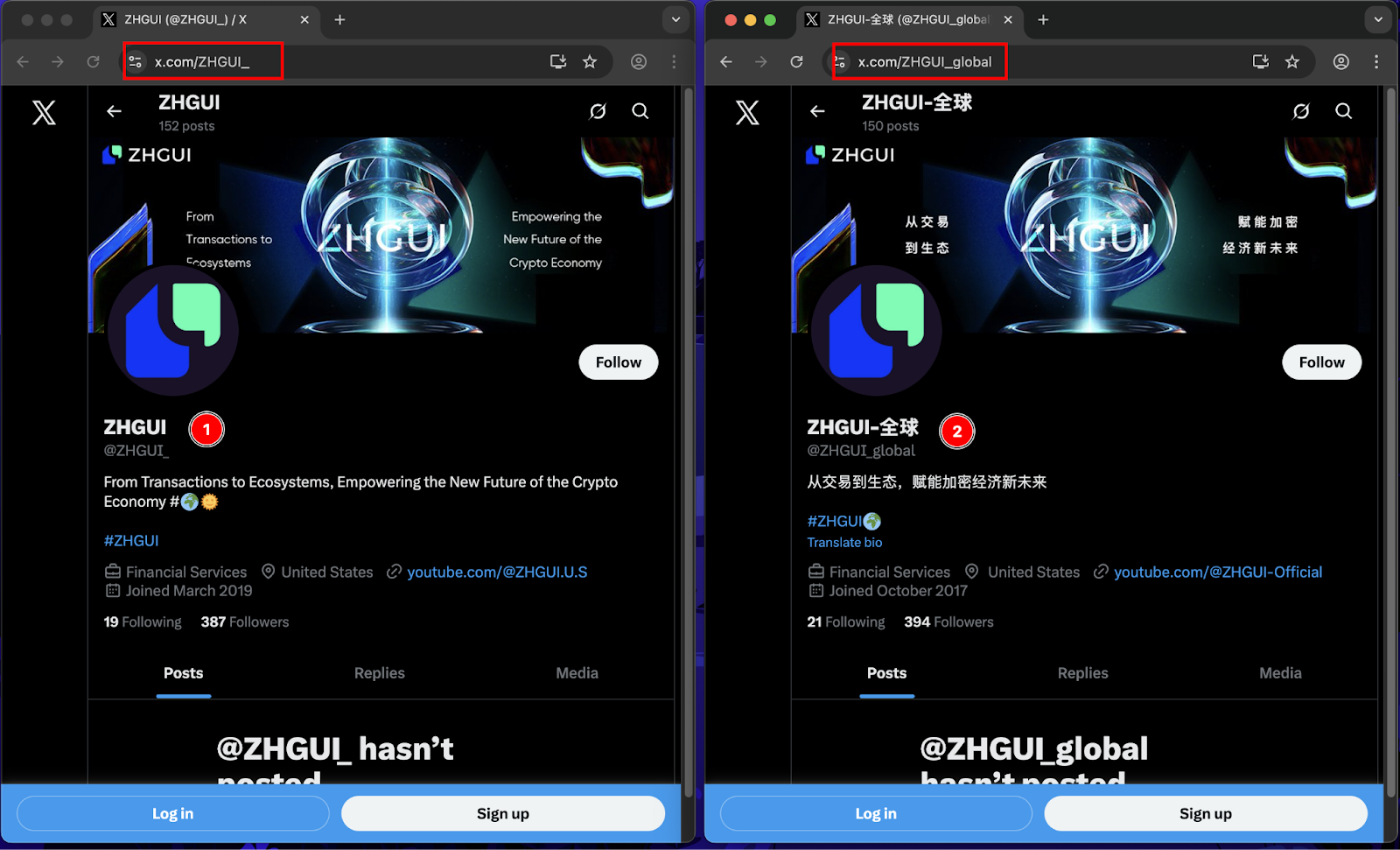
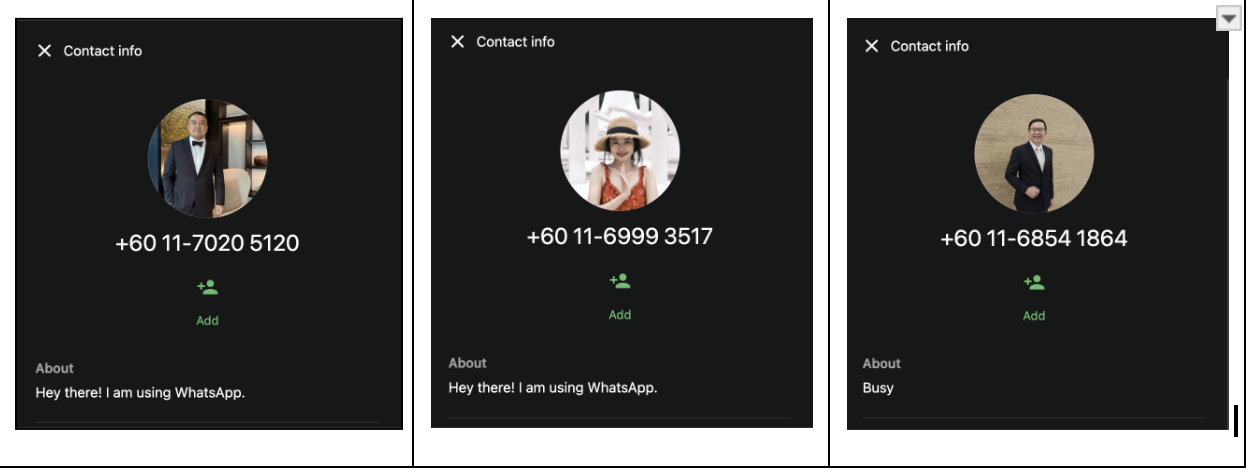
Multiple WhatsApp investment communities were identified as core recruitment hubs used to funnel victims into the platform. These groups promoted ZHGUI through curated trading narratives, fabricated success stories, and invitation-code access. OSINT review and victim-submitted screenshots revealed several Malaysia-based phone numbers associated with group administrators and onboarding handlers:
##Source: https://www.facebook.com/share/p/1KCg4dA3k9/##
WhatsApp group operators linked to ZHGUI activity:
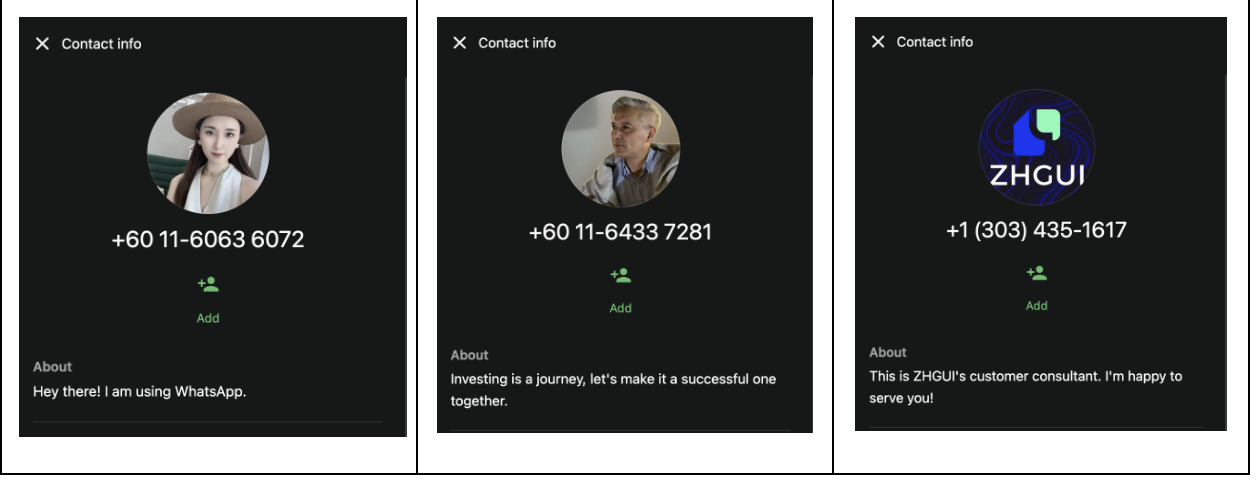
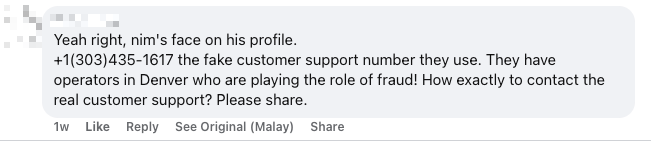
Additionally, a U.S.-based number was identified in public victim comments, cited as a fake ZHGUI customer support line allegedly operating from Denver:
##ZHGUI customer support: +1 (303) 435-1617##
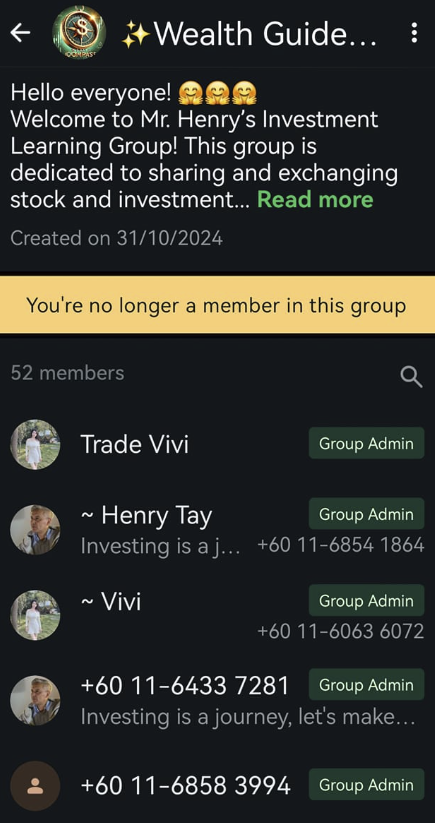
These WhatsApp funnels were observed operating in names such as A317 Strategy Intelligent Investment and Wealth Guide, and encouraging victims to use invite-only registration links while showing staged “profits” to encourage further deposits.
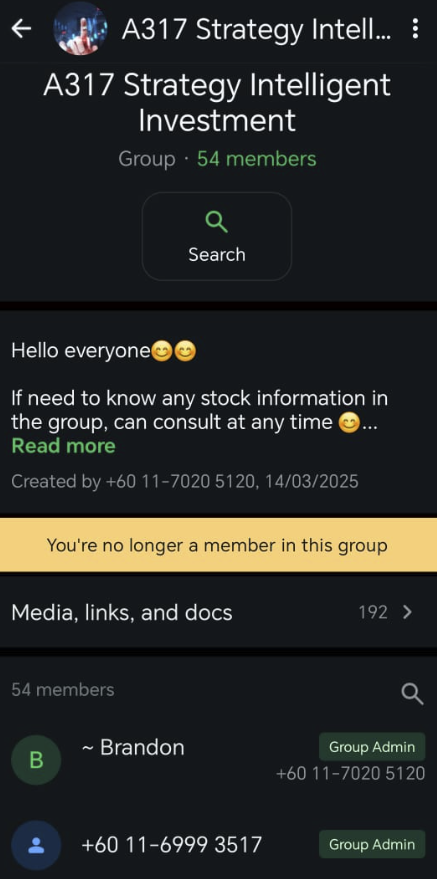
##URL: https://klse.i3investor.com/web/blog/detail/ZHGUIscam/2025-07-25-story-h499657939-ZHGUI_Exchange_Reminder_Beware_of_On_Chain_Data_Forgery_Traps_and_Stay_A##
A community blog post explicitly labels ZHGUI as a crypto scam, warning users of “On-Chain Data Forgery” and fake yield platforms.
##URL: https://www.linkedin.com/posts/ivanblinde_web3-defi-innovation-activity-7337856604559634432-IjRC##
A post by “Ivan Blinde” titled “Pioneering the Web3.0 Frontier: How ZHGUI Exchange is Leading the Charge” attempts to build credibility by presenting ZHGUI as a legitimate DeFi innovation platform. The language is promotional, AI-generated, and includes unrelated links to personal pages — an apparent attempt to boost the SEO presence of the scam.
The individual “Ivan Blinde”, who shared and promoted ZHGUI-related content, was found to have a U.S.-based phone number linked to their LinkedIn account:
This number’s activity across multiple messaging platforms suggests it may be used for direct communication or promotional coordination tied to the ZHGUI project.