Overview
The cybersecurity landscape is constantly evolving, with threats becoming more sophisticated and harder to detect. Organizations need robust, proactive solutions to stay ahead of potential risks. The CloudSEK Threat Intelligence Splunk app on Splunkbase is our latest integration offering that addresses this need by providing a comprehensive approach to threat detection, prevention, and response.
This integration combines CloudSEK's ability to gather and analyze threat data from across the digital landscape with Splunk's powerful data processing and correlation capabilities. The result is a solution that enables organizations to:
- Identify potential threats early in their lifecycle
- Correlate external threat intelligence with internal security data
- Respond more quickly and effectively to security incidents
This article explores the key features of the CloudSEK-Splunk integration, presents practical use cases, and offers guidance on implementation. Whether you're a security analyst looking to enhance your current security posture or a CISO trying to build a more resilient cybersecurity strategy, this integration provides valuable tools for navigating today's complex threat environment.
Key Components of the Integration
The two advanced cybersecurity solutions are combined together in this app, each bringing its own unique strengths:
- CloudSEK’s AI-Driven Risk Management and Threat Intelligence
- Utilizes 21+ specialized monitors through XVigil (Digital Risk Protection) and BeVigil Enterprise (External Attack Surface Management).
- Provides deep, contextualized threat insights across diverse digital landscapes.
- Offers early detection of emerging threats and vulnerabilities.
- Splunk's Advanced SIEM Capabilities
- Delivers industry-leading data ingestion, correlation, and analysis.
- Enables rapid threat detection and response
- Presents comprehensive security information through a unified interface
By integrating these technologies, organizations can:
- Correlate external threat intelligence with internal log data for more accurate threat detection
- Automate response workflows based on high-fidelity threat indicators
- Gain a more comprehensive view of their security posture across multiple digital domains
The 360-Degree Threat Protection Model
The CloudSEK x Splunk integration offers comprehensive protection across some of the key security domains:
- Web and Application Security: Real-time vulnerability detection in web applications, APIs, and mobile apps.
- Infrastructure and Network Security: Continuous monitoring of network, cloud, and DNS infrastructure for threats.
- Dark Web and Social Media Intelligence: Early warning system for planned attacks or data leaks.
- Code and Data Leak Prevention: Detection of sensitive data exposure in public repositories, open buckets, and cloud storage.
- Fraud and Impersonation Prevention: Rapid detection of phishing campaigns and brand impersonation attempts.
- Vulnerability and Exploit Intelligence: Real-time tracking of new CVEs and compromised assets.
- Banking and Financial Security: Monitoring for leaked financial information (credit/debit cards) and potential fraud attempts.
Let’s look at some of the use cases
Scenario 1
A sophisticated fraud ring launches a coordinated impersonation attack against BigBank, a major financial institution, utilizing multiple channels to maximize their chances of success.
Attack Vectors Detected
- Fake mobile apps impersonating BigBank's official banking app.
- Phishing websites mimicking BigBank's login portal.
- Social media accounts impersonating BigBank's customer service.
- Fraudulent call centre operations claiming to be BigBank support.
Integration in Action
- CloudSEK XVigil Alerts:
- Fake Mobile Apps Monitor identifies 3 counterfeit Android apps and 2 iOS apps in various third-party app stores and download sites, all impersonating BigBank's official app.
- The Fake URLs and Phishing Monitor detects a network of 25+ phishing domains using slight variations of BigBank's official domain, all hosting convincing replicas of the bank's login page.
- Fake Social Media Handles Monitor flags 12 Twitter accounts and 8 Facebook pages impersonating BigBank's official customer service channels.
- Fake Call Center Monitor identifies a cluster of new VoIP or phone numbers that suddenly appeared in online advertisements and social media posts, claiming to be BigBank's official customer support lines.
- Splunk's correlation and analysis:
- Observes a 200% increase in customer reports of suspicious calls, emails, and text messages in the last 48 hours. This correlation suggests a potential phishing scam targeting BigBank customers.
- Detects an unusual pattern of password reset requests and new device registrations across genuine customer accounts.
- Identifies a spike in failed login attempts on the real BigBank platform, suggesting credential stuffing using harvested information.
- CloudSEK-Splunk Integration projected response:
- Generates a high-priority fraud alert correlating all detected impersonation attempts across channels.
- Triggers a coordinated response playbook:
- Automatically submits takedown requests for fake apps to respective app stores.
- It initiates rapid domain blacklisting of phishing URLs across major ISPs and corporate networks.
- Reports impersonating social media accounts for immediate suspension.
- Temporarily elevates authentication requirements for high-risk actions (e.g., large transfers, adding new payees) on genuine BigBank platforms.
- Deploys targeted warning messages on BigBank's official app, website, and social media channels, alerting customers about the impersonation attempts and to stay vigilant against potential frauds.
Scenario 2
CloudSEK’s BeVigil Enterprise Helps a Retail Company Prevent Customer Data Leakage from Their Cloud Environment.
Vulnerabilities Detected
- Cloud Storage Misconfiguration: BeVigil discovers a publicly accessible Amazon S3 bucket containing sensitive customer information, including personal identification data and transaction records.
- API Vulnerability: An API endpoint used for retrieving customer orders is misconfigured, allowing unauthorised access without proper authentication controls (CVSS Score: 9.1 - Critical).
Integration in Action
- CloudSEK BeVigil Alerts:
- Flags the S3 Bucket: Identifies the publicly accessible S3 bucket as a critical misconfiguration exposing confidential customer data.
- Historical Vulnerability Insight: Reveals that the misconfiguration has been exploitable for the past 45 days, potentially impacting thousands of customers.
- API Vulnerability Detection: Highlights the insecure API endpoint lacking authentication, classifying it as a high-severity vulnerability due to the risk of unauthorized data access.
- Splunk’s Correlation and Analysis:
- Anomalous API Traffic: Detects a sudden spike in API requests originating from suspicious IP addresses, indicating potential exploitation attempts of the vulnerable endpoint.
- Threat Intelligence Correlation: Associates these IP addresses with known malicious actors and patterns identified by CloudSEK's threat intelligence, suggesting a coordinated attack.
- Data Exfiltration Indicators: Monitors unusual download activities from the S3 bucket, signaling possible data exfiltration efforts.
- CloudSEK-Splunk Integration’s Response:
- Comprehensive Security Alert: Generates a critical alert combining detailed information on the cloud misconfigurations and observed malicious activities.
- Triggers a coordinated response playbook:
- Restricts S3 Bucket Access: Immediately revokes public access permissions and applies proper access control lists (ACLs) to secure the bucket.
- Secures API Endpoint: Disables the vulnerable API and implements robust authentication mechanisms, such as OAuth 2.0.
- Initiates Security Audit: Notifies the security team and cloud administrators to conduct a thorough review of all cloud storage permissions and API configurations.
- Remediation Guidance:
- Credential Rotation: Advises rotating all access keys and credentials associated with the compromised services.
- Data Encryption: Recommends implementing server-side encryption for sensitive data stored in S3 buckets.
- Enhanced Monitoring: Suggests setting up advanced logging and continuous monitoring for cloud resources to detect future anomalies.
- Customer Impact Report: Generates a detailed list of potentially affected customers for proactive notification, allowing the company to comply with regulatory requirements and maintain customer trust.
Getting Started with CloudSEK Threat Intelligence for Splunk
Ready to enhance your security posture with CloudSEK and Splunk? Here's how to get started:
- Prerequisites
- Ensure you have a Splunk Enterprise or Splunk Cloud instance (version 9.0 or later recommended).
- You'll need a valid CloudSEK API token from your account. If you don't have one, contact your Customer Success Manager, or if you’d like to test our product out, reach out to CloudSEK for a 14-day free trial.
- Installation
- Log in to your Splunk instance as an admin or a user with a system role like ‘splunk-system-upgrader’, etc.
-
Navigate to "Apps" and click on the "Find More Apps" option.
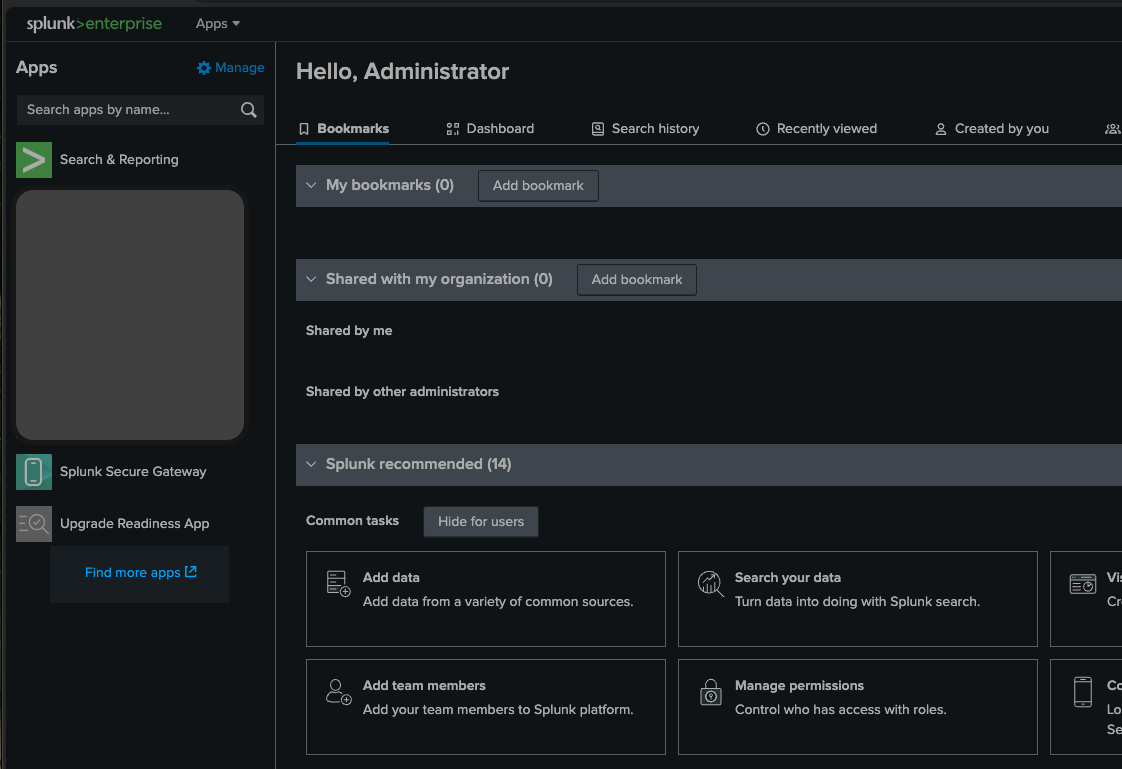
-
Search for "CloudSEK" and then click "Install" on the "CloudSEK Threat Intelligence" app card. Proceed with the installation by following the on-screen prompts.
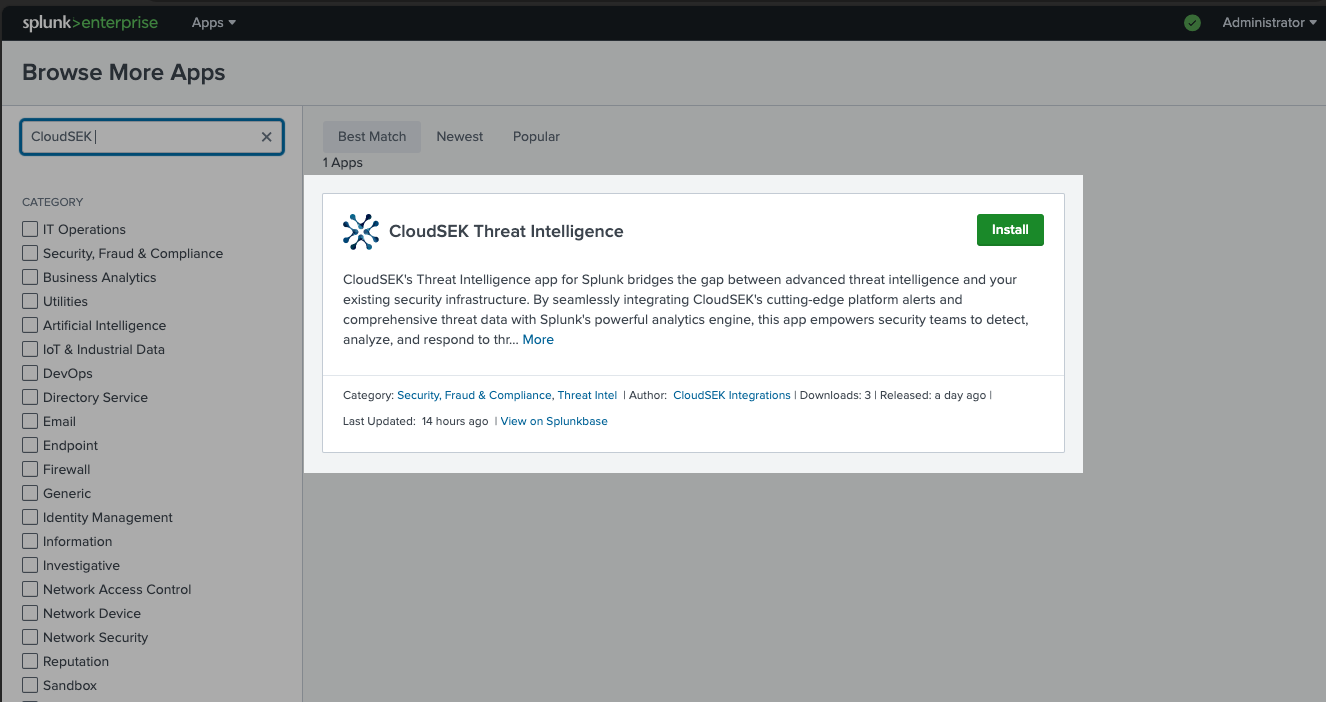
-
Alternatively, download the app from Splunkbase and install it manually.
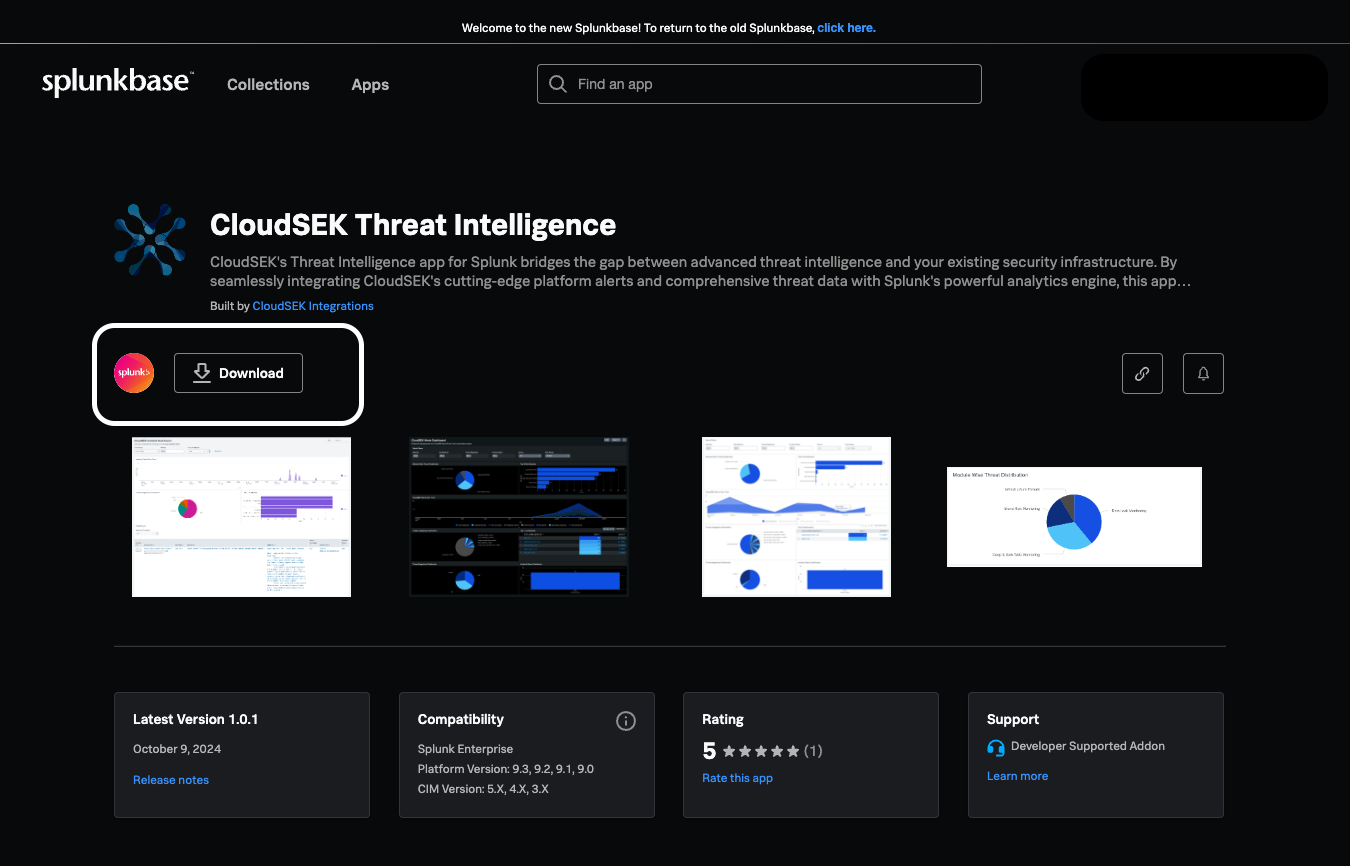
- Configuration
- Once installed, go to the CloudSEK Threat Intelligence app in your Splunk instance.
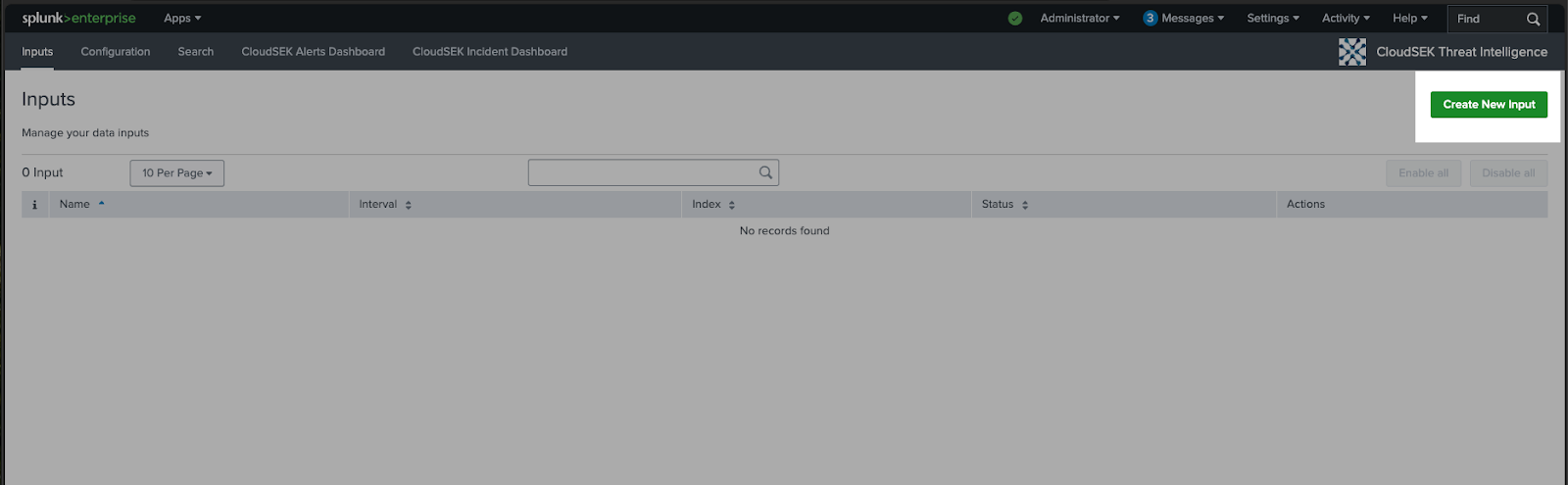
- Navigate to the "Inputs" page.
-
Click on the "Create New Input" button.
-
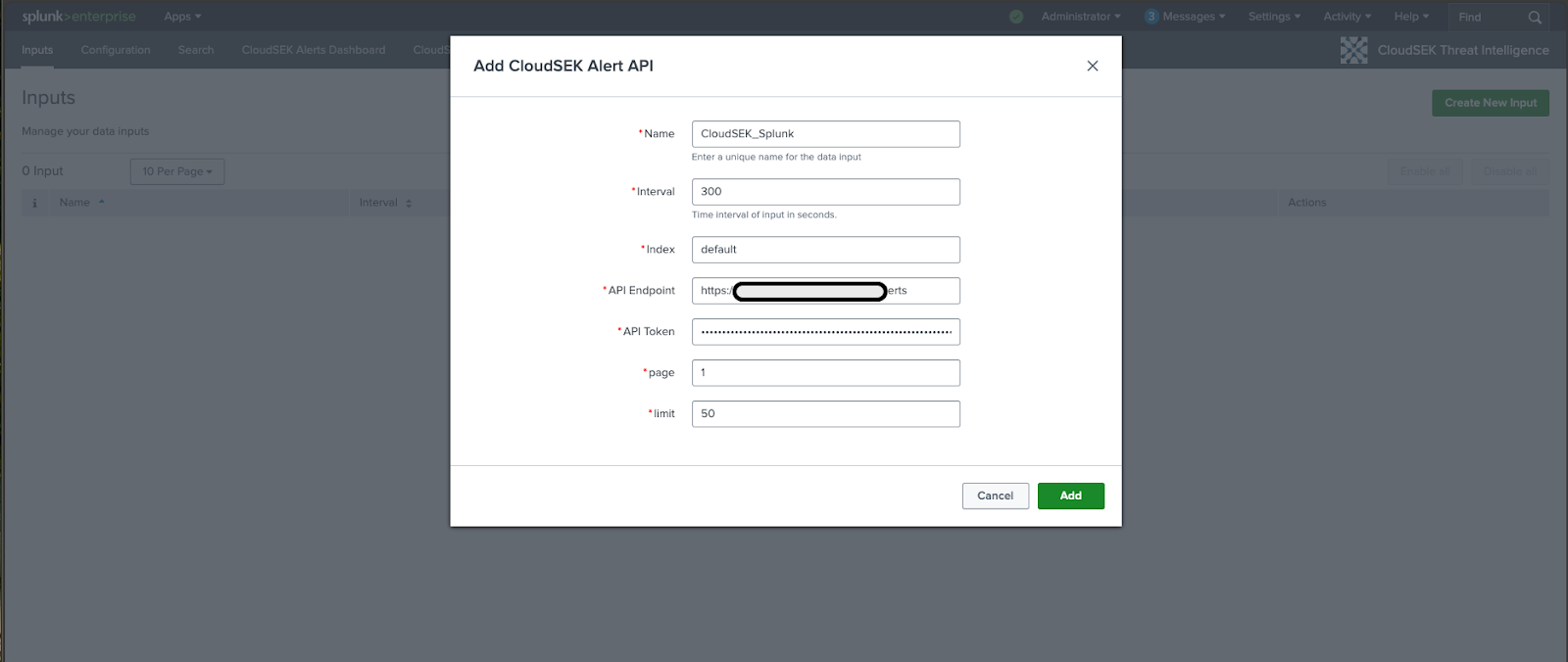
Enter a name for the input, add your CloudSEK API token and configure any additional settings as needed.
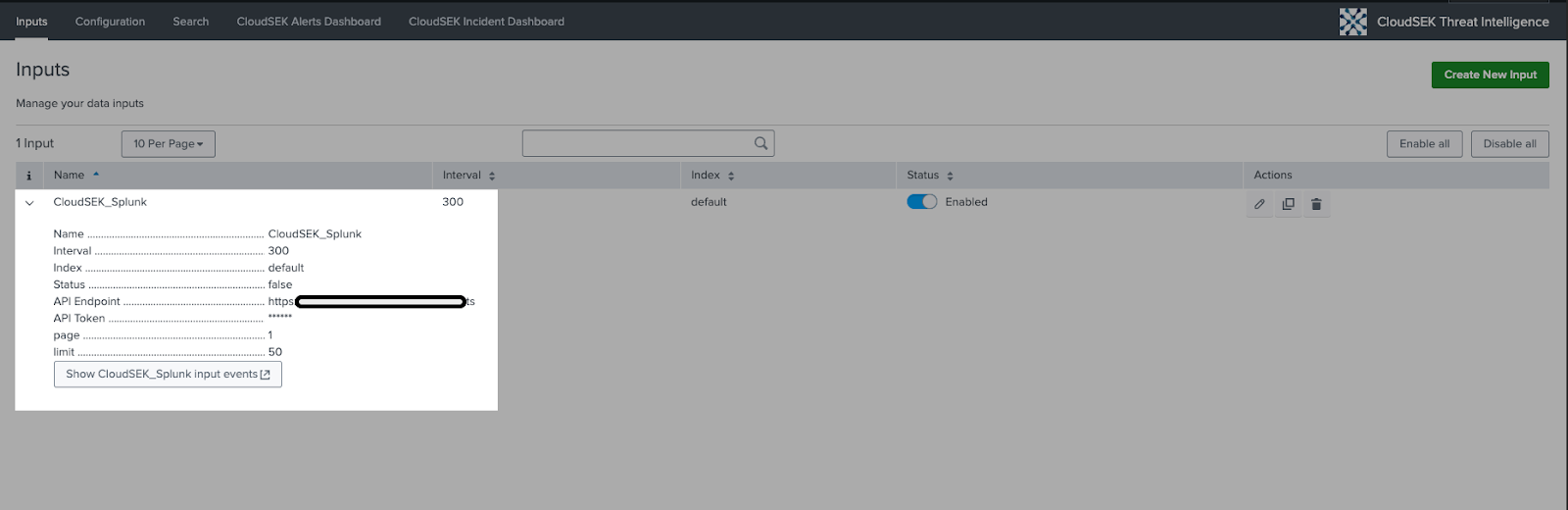
- Data Ingestion
- The app will start ingesting threat intelligence data from CloudSEK automatically.
- You can adjust the data collection interval in the app's configuration.
- Explore Dashboards
- Set Up Alerts
- Configure custom alerts on Splunk based on CloudSEK's threat intelligence to automate your response to potential threats.
- Integration with Existing Data
Remember, the power of this integration lies in customizing it to your organization's specific needs.
Conclusion
Implementing the CloudSEK-Splunk integration requires careful planning and ongoing management, but it provides a robust foundation for a modern, adaptive cybersecurity strategy. As organizations continue to face increasingly complex digital threats, solutions that combine broad threat intelligence with powerful analytics will be essential for maintaining strong security postures.
For those considering this integration, the next steps include:
- Assessing your current security infrastructure and identifying integration points
- Developing an implementation roadmap with clear milestones and success metrics
- Ensuring your team has the necessary training to leverage the full capabilities of the integrated solution
By taking these steps, organizations can position themselves to more effectively protect their digital assets and adapt to emerging security challenges.



