Executive Summary CloudSEK analyzed a dataset that appears to be a credible leak of Charming Kitten (APT35) operational materials, containing Persian-language internal documents, personnel rosters, tooling details, and campaign reports. It documents coordinated teams for penetration, malware development, social engineering, and infrastructure compromise, including rapid exploitation of CVE-2024-1709 and mass router DNS manipulation. Victims include government, legal, academic, aviation, energy, and financial sectors across the Middle East, but the regions of interest include the US and Asia as well. The systematic operations enable long-term persistence, Active Directory domination, and extensive exfiltration. Tradecraft shows custom RATs, EDR evasion, supply-chain pivots, and sophisticated phishing infrastructure. The disclosure highlights Iran’s organized regional espionage capability and acute supply-chain and national security risk from IRGC-affiliated nation-state actors.
Analysis Background Charming Kitten, also known as APT35, Magic Hound, and Phosphorus, is a cyber-espionage group believed to be operating out of Iran. In late 2024, they were found to deploy a C++ variant of a known malware called BellaCiao. In October 2025, CloudSEK ’s TRIAD found and analyzed a github repository that allegedly contained leaked internal operational documents from Charming Kitten, an IRGC-affiliated APT group. The leaked documents are in Farsi, so consumption of the information from this leak was challenging for the wider community.
To make it easier for English speakers, we’ve assessed the legitimacy of the leak, the APT group’s organizational structure, and their operational details from the leak.
Note: This blog will be updated when more information becomes available, as the threat actor has stated that they plan to leak more information in the coming days.
Is this leak even legitimate? High Confidence Indicators Persian language internal documentation (100+ files) Iranian calendar usage (Jalali dates: 1402, 1403) Operational hours align with Tehran timezone Target selection aligns with Iranian intelligence priorities Infrastructure matches known APT35 patterns Tradecraft consistent with Charming Kitten TTPs Personnel names (Persian naming conventions)Known APT35/Charming Kitten Overlaps Social engineering focus (phishing campaigns)Credential harvesting priorityMiddle East targeting (Jordan, UAE, Saudi Arabia)Long-term persistence over rapid smash-and-grabTool development custom RATs and utilities
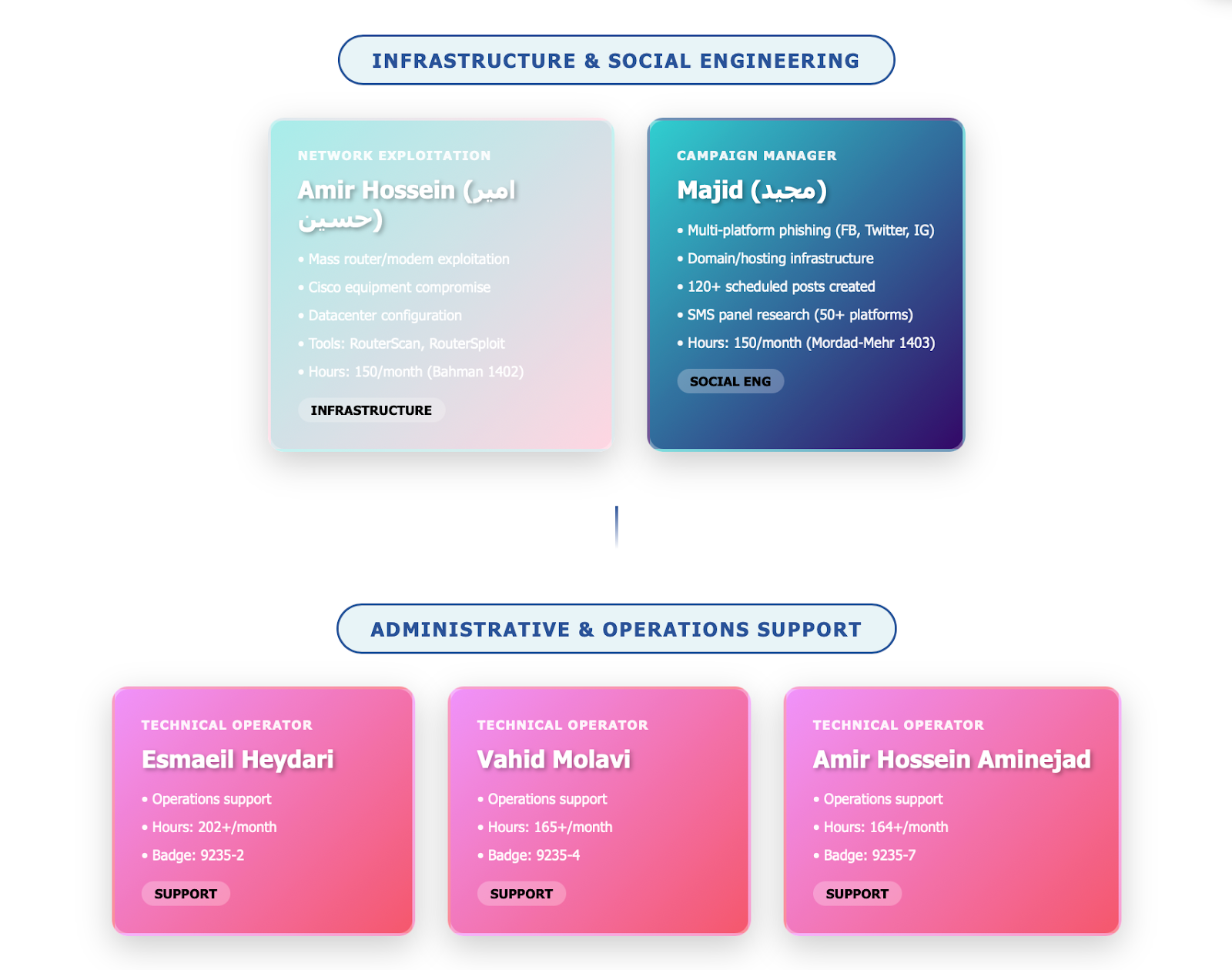
Organization Structure - APT35 a.k.a. Charming Kitten Operational Staff 1. Mehdi Sharifi (مهدي شريفي) Role : Office Manager / Administrative Head (رئیس دفتر)Department : Administrative Contracts (اداری قراردادي)Evidence : Timesheet records Work Pattern : Regular office hours with overtimeBadge Number : 9235-12. Esmaeil Heydari (اسماعيل حيدري) Role : Operator / Technical Operator (اپراتور)Department : Administrative ContractsEvidence : Timesheet records Work Pattern : 202+ hours monthly, significant overtimeBadge Number : 9235-2Notes : High workload indicator suggests senior technical role
3. Vahid Molavi (وحيد مولوي) Role : Operator / Technical Operator (اپراتور)Department : Administrative ContractsEvidence : Timesheet recordsWork Pattern : 165+ hours monthly with leave daysBadge Number : 9235-4 (Note: Badge #3 not present in documents)
4. Amir Hossein Aminejad (امیر حسین امین نژاد) Role : Operator / Technical Operator (اپراتور)Department : Administrative ContractsEvidence : Timesheet recordsWork Pattern : 164+ hours monthly, multiple authorized leavesBadge Number : 9235-7Technical Operations Team 5. Ali (علی) Role : Penetration Tester / Offensive Security OperatorPrimary Focus : SQL Injection campaigns, Israeli targetsEvidence : Monthly report (02120dcf3b263702028a0441881d339ee4ff8e15)Work Period : Bahman 1402 (Jan-Feb 2024)Total Hours : 44 hours monthlySpecializations : SQL injection exploitation (SQLMap) Mass scanning operations Israeli infrastructure targeting Modem exploitation (GoAhead devices) DNS server manipulation Key Projects : simania.co.il exploitation bonimonline.co.il compromise Mass modem attack campaign (580+ devices) CVE research and exploitation Proficiency : SQLMap, Burp Suite Intruder, Censys, Acunetix
6. Mohammad (محمد) Role : Penetration Tester / Web Application Security SpecialistEvidence : Monthly report (4037e9382a99fdd96fe93eb0fd4380eea695bd3a)Work Period : Dey 1402 (Dec 2023-Jan 2024)Total Hours : 55 hours monthlySpecializations : Web application exploitation CMS vulnerability research Auto-deface tool development Israeli website targeting Key Projects : exite.co.il target campaign souz.co.il exploitation tuvastory target operations Reverse IP reconnaissance Exploit automation development Proficiency : Custom exploit development, waybackurls, Bing dorking, BreachForums OSINT
7. Hossein (حسین) / HSN Role : Malware Developer / Red Team OperatorEvidence : Daily reports (HSN2 folder, 1403-05-27 through 1403-06-06)Work Period : Mordad-Shahrivar 1403 (Jul-Sep 2024)Total Hours : 26+ hours documented (partial reporting)Specializations : Custom malware development (RTM Project) Active Directory exploitation Share folder enumeration tools Windows Server infrastructure setup Loader development Key Projects : RTM Project : Remote Administration Tool Share folder enumerator for AD environments Binary rewrite capabilities System information harvesting Shell access functionality Custom switch-based execution Technical Environment : Active Directory test lab setup Windows Server 2012 R2 Domain controller configuration Multi-machine VM environment Challenges Documented : Complex function architecture in RTM AD user visibility issues Integration of multiple modules
8. Majid (مجید) / MJD Role : Social Engineering Campaign Manager / Infrastructure SpecialistEvidence : Extensive daily reports (MJD folder, 1403-05-27 through 1403-07-24)Work Period : Mordad-Mehr 1403 (Jul-Oct 2024)Total Hours : 150+ hours monthly (180 attendance, 150 operational)Specializations : Social media campaign management Phishing infrastructure development Domain/hosting acquisition Payment system setup (cryptocurrency) Content creation and scheduling SMS panel research and acquisition E-commerce template design VPN/anonymity infrastructure Key Projects : Campaign Project : Multi-platform phishing operations Facebook Ads (kaelajnz account) Twitter/X campaigns Instagram operations Google Ads setup Microsoft Ads (multiple accounts) Telegram channels (UAE-targeted) Infrastructure Development : aecars.store e-commerce site Domain purchases (sunrapid.com, lydston.com variants) Cloudflare + Namecheap hosting Business email setup VPN services acquisition OSINT Operations : IASA educational organization reconnaissance Target profiling and documentation Support Functions : SMS panel evaluation (50+ platforms) Document forgery coordination SIM card acquisition (multiple countries) Payment method research (PayPal, Wise, cryptocurrency) Proficiency : Web development (HTML/CSS, Photoshop, Dreamweaver) Social media management (Meta Business Suite, scheduling) Hosting/DNS (cPanel, Cloudflare, Namecheap) AI tools (video generation, content creation) Cryptocurrency wallets (Atomic Wallet, MetaMask) Operational Challenges : Microsoft account suspensions (phone verification) Facebook account restrictions (sanctioned card detection) Skype account bans Number verification difficulties (4-6 SIMs per platform) Notable Activities : Prepared 120+ scheduled social media posts Created multiple e-commerce templates Coordinated with "exchange" (sarrafi) for payments Managed attendance tracking system setup Created motion graphics and promotional videos
9. Amir Hossein (امیر حسین) Role : Infrastructure Penetration Specialist / Network Engineer Evidence : Monthly report (e8ed42d00168744e408dd53c795008c76ee788e6)Work Period : Bahman 1402 (Jan-Feb 2024)Total Hours : 150 hours monthlySpecializations : Mass exploitation campaigns Network equipment targeting (routers, modems) Infrastructure mapping and documentation Datacenter configuration Vulnerability scanning and exploitation Key Projects : Modem Mass Exploitation : GoAhead device targeting TP-LINK, ASUS, D-Link campaigns pfSense equipment reconnaissance Cisco Equipment Compromise : Cisco RV (Small Business) exploitation Multiple CVE utilization Network Configuration : Tebyan datacenter setup Starlink equipment testing Infrastructure Projects : IP-LAND server deployment Next Cloud system design Planka project management setup Proficiency : Nmap, Nuclei RouterScan, RouterSploit (auto-exploiters) Fofa search engine NetGear exploitation Documentation Responsibilities : SQLi vulnerability management reports 3-month management reports System architecture documentation
Unknown/Unattributed Operators 10. Unnamed Operator(s) - ConnectWise Campaign Role : Rapid Response Exploitation TeamWork Period : Esfand 1402 (Feb-Mar 2024)Specializations : Zero-day/N-day rapid exploitation Multi-country scanning operations Real-time vulnerability weaponization Key Achievement : Day-1 exploitation of CVE-2024-1709 (within 24 hours of disclosure)Geographic Coverage : Israel, Saudi Arabia, Turkey, Jordan, UAE, Azerbaijan11. Unnamed Operator(s) - Jordan Ministry of Justice Role : Web Application Penetration TesterEvidence : services.moj.gov.jo reportSpecializations : Telerik exploitation (CVE-2019-18935, CVE-2017-11317) ASP.NET application security Anti-AV payload development DLL obfuscation techniques
12. Unnamed Operator(s) - Qistas Operation Role : Advanced Persistent Threat Operator / Data Exfiltration SpecialistEvidence : Winter 1403 performance report (Final)Specializations : Active Directory domination Supply chain attacks Long-term persistence (months/years) Massive data exfiltration (74GB+ documented) EDR bypass (Sophos, Trend Micro) Backup infrastructure compromise (Acronis Cloud) Key Achievement : Complete domain compromise with ongoing access
13. Unnamed Operator(s) - WISE University Role : Legacy System Exploitation SpecialistEvidence : wise.edu.jo initial access reportSpecializations : PHP CGI exploitation (CVE-2012-1823) Database compromise Adminer tool deployment
14. Unnamed Operator(s) - IBLaw Operation Role : Corporate Network Penetration SpecialistEvidence : IBLaw Winter 1403 reportSpecializations : Exchange Server compromise Domain controller exploitation Legal industry targeting Client data exfiltration
Management & Support Personnel 15. "Management" / "Modiriyat" (مدیریت) Role : Operational Leadership / Project CoordinatorEvidence : Mentioned throughout daily reports (meetings, approvals, task assignments)Responsibilities : Task assignment and prioritization Budget approval (cryptocurrency transfers) Strategic planning Personnel coordination Report review Interaction Pattern : Regular status meetings (20-40 minutes documented) Approval authority for expenditures Technical guidance provider Campaign strategy decisions
16. "Exchange" / "Sarrafi" (صرافی) Role : Financial Facilitator / Cryptocurrency HandlerEvidence : Repeatedly mentioned in Majid's reportsResponsibilities : Cryptocurrency transactions Foreign payment processing SIM card purchases Document forgery coordination VPN/service payments Entities Referenced : Gigo Pay (support contact) Binance/Novin Verify (document services) Paynans (payment services) Note : May be external contractor rather than direct team member
17. "Technical Manager" (مدیر فنی) Role : Senior Technical AdvisorEvidence : Mentioned in Ali's modem exploitation reportResponsibilities : Technical guidance on exploitation techniques Tool selection (Censys, etc.) Methodology assistance Specific Example : Assisted with GoAhead device discovery and exploitation strategyOperational Timeline Bahman 1402 (Jan-Feb 2024) :
SQL injection campaigns on Israeli targets (simania.co.il, bonimonline.co.il) Mass network device exploitation (GoAhead devices, TP-Link) DNS server manipulation (580+ modems) Esfand 1402 (Feb-Mar 2024) :
ConnectWise CVE-2024-1709 exploitation Rapid response to vulnerability disclosure (within 24 hours) Multi-country scanning campaigns Mehr-Aban 1403 (Sep-Nov 2024) :
Social engineering campaign infrastructure development Domain purchases and template creation SMS panel research and acquisition Payment system setup (cryptocurrency, document forgery) Dey 1403 (Dec 2024-Jan 2025) :
Active Directory exploitation focus EDR evasion development Supply chain attack execution (Qistas partner penetration) Continuous data exfiltration (74GB+ from single target) Capability Development Immediate exploitation of CVE-2024-1709 (day-1 response) Continuous EDR/AV bypass research Custom RATs, automation scripts, data organization systems Geopolitical Context Iranian Intelligence Interests :
Regional legal/judicial systems Government decision-making processes US agency operations in Middle East (USAID, OPIC) Defense contractor relationships Energy sector intelligence Financial systems (money transfer, banking) Targeting & Victimology Geographic Focus Primary : Jordan, UAE, Saudi Arabia, Israel Secondary : Turkey, Oman, Qatar, Azerbaijan Tertiary : USA, Singapore, India
Sector Targeting Legal/Judicial : Ministry of Justice (Jordan) Qistas legal services IBLaw firm Court systems Education : WISE University (Islamic studies) IASA educational organization Financial Services : Swiss Exchange money transfer Banking infrastructure (via legal firm clients) Government : Multiple government network penetrations Civil service databases Critical Infrastructure : National Water Company (Saudi Arabia) Aviation systems (Air Arabia) Energy sector (via legal clients) Exfiltrated Data Types Personal Identifiable Information (PII) :
11,164+ student records (WISE University) Thousands of judges/lawyers (Qistas database) Employee personnel files National ID numbers (Jordan, Palestine) Passport scans (multiple countries) Credentials :
Domain administrator passwords Database credentials (MySQL, Oracle) Email account access VPN credentials Camera system logins Classified/Sensitive Documents :
Saudi Council of Ministers decisions Jordan Civil Aviation Commission files USAID project documentation Legal contracts with defense contractors Aviation regulatory communications Operational Intelligence :
CCTV footage (24/7 surveillance) VoIP call recordings (2023-2024) Email correspondence archives Business strategy documents Client lists and contracts Campaign Operations (Social Engineering) Phishing Infrastructure Platforms Targeted :
Facebook Ads (kaelajnz account) Twitter/X advertising Instagram (@kaelajnz) Google Ads Microsoft Ads Telegram channels (UAE-focused) LinkedIn campaigns Operational Challenges :
Microsoft account suspensions (phone verification issues) Facebook account restrictions (sanctioned card detection) Twitter payment integration issues Number verification difficulties (4-6 SIM cards purchased per platform) Supporting Infrastructure :
SMS panels researched (50+ platforms evaluated) for smishing eSIM services (tested via sms-activate) Document forgery services (Binance, Novin Verify, Gigo Pay, Paynans) Skype number purchases (UAE) Attendance tracking system (Tick Box panel) Template Development :
Helios template (e-commerce) Molla Store template AECars automotive template 120+ scheduled social media posts prepared Operational Infrastructure VPN Services : Namecheap VPN, RegXA VPSVPS: Tebyan datacenterStarlink integration Hosting : Cloudflare + Namecheap hostingEmail : Business email accounts via NamecheapCustom Tooling RTM Project : Remote Access Trojan development Active Directory integration Share folder enumeration System information harvesting Shell capability Binary execution with switches Automated Scanners : Nuclei templates for CVE-2024-1709 RouterScan/RouterSploit auto-exploiters WordPress vulnerability scanners (WPScan) Data Organization : Planka (Project Management) NextCloud (File Sharing) Documentation systems Technical Tradecraft Analysis Attack Methodologies A. Reconnaissance Tools & Techniques :
Search engines: Shodan, Censys, ZoomEye, Fofa, Hunter, Odin Subdomain enumeration via reverse IP lookups Infrastructure mapping using Nmap, Nuclei B. Initial Access Vulnerability Exploitation(including but not limited to) : CVE-2024-1708/1709 (ConnectWise) CVE-2019-18935 (Telerik Deserialization) CVE-2017-11317 (Telerik File Upload) CVE-2012-1823 (PHP CGI RCE) CVE-2017-3506 (Oracle WebLogic) Credential Harvesting : Database password extraction Browser credential theft Active Directory enumeration C. Persistence Web shell deployment (Adminer, custom PHP) Domain admin account creation Backup system compromise (Acronis, Oracle) VPN infrastructure (Namecheap VPN services) File upload portals on compromised domains D. Defense Evasion Anti-EDR :
Obfuscated DLL payloads DLL hijacking strategies Bypass of: SentinelOne Sophos Trend Micro CrowdStrike (lab testing) Operational Security :
VPN rotation (European IPs) Infrastructure compartmentalization Encrypted document storage (VeraCrypt) Virtual machine snapshots for rapid deployment E. Lateral Movement Active Directory exploitation Share folder enumeration Credential dumping Supply chain pivoting (partner networks) F. Data Exfiltration Methods :
Database dumps via Adminer Cloud backup access (Acronis portals) CCTV footage downloads Email archive extraction (Exchange) VoIP call recording theft Data Staging :
Organized by client/project Encrypted archives Categorized file types (Office, Audio, Config, Database)
Conclusion This dataset represents one of the most comprehensive APT35/Charming Kitten operational disclosures to date. The threat actor demonstrates:
Strategic patience : Multi-year access maintenanceTechnical sophistication : Custom tool development, EDR evasion, supply chain attacksOperational breadth : Simultaneous campaigns across 6+ countriesHigh-value targeting : Government, legal, critical infrastructure sectorsData-centric mission : Systematic exfiltration prioritizing intelligence valueThe compromise of entities like Qistas (legal services) and IBLaw provides Iran with unprecedented visibility into:
Regional judicial proceedings US government operations in Middle East Defense contractor relationships Government decision-making processes Critical infrastructure planning This shows that elements within one’s supply chain are increasingly being used to obtain information about organizations of interest. This represents an ongoing, active, and moderately successful espionage campaign with considerable implications for Middle Eastern regional security, US interests, and international legal proceedings.
References